Original title: "What Is a Stealth Address? Vitalik’s Solution for Privacy on Ethereum》
Original Author: Kenny
Original compilation: ChinaDeFi

Original compilation: ChinaDeFi
Vitalik Buterin, the co-founder of Ethereum, published an article some time ago, which mainly discussed how to add privacy to the Ethereum network through so-called "stealth addresses". In it, he explains how stealth addresses work and the technology's potential to increase user privacy on the Ethereum network. In this article, the author tries to explain how stealth addresses work using an example: Alice wants to send 1.2 ETH to Bob.
Why do we need stealth addresses?
It is a common misconception that many people think that public blockchains like Ethereum and Bitcoin are private. We should clearly know that public blockchains are not private. Public blockchains do provide some sense of privacy through "pseudonyms" in the form of wallet addresses. But we only need to think of the wallet address as an account, as long as someone matches this account with someone in real life, then everything this person does will be exposed in the sun.
Every interaction of the wallet address on the chain, including transactions, interactions with decentralized applications, purchase of NFT, etc., these data will be recorded and stored in a public way, and anyone who can connect to the Internet can freely Check. Websites like Etherscan make it very easy for people to view this information. Applications like Dune Analytics make it easy for people to analyze this information.
Without privacy protection, this information can be easily used by others without consent. Using the public blockchain, it is possible to see the user's purchase location, subscription and other content, and those who are interested may use this information to carry out some criminal activities. Given this, on-chain privacy solutions are fast becoming the solution to protect Web3 users around the world. Recently Vitalik Buterin has thought more deeply about this topic and offers a solution for the Ethereum ecosystem through so-called stealth addresses.
Generate keys to create stealth addresses
Stealth addresses must be generated by two participants: in the example below Bob is the receiver and Alice is the sender.
Bob generates:
A spending key (Spending Key), known only to Bob, will be used to generate addresses later;
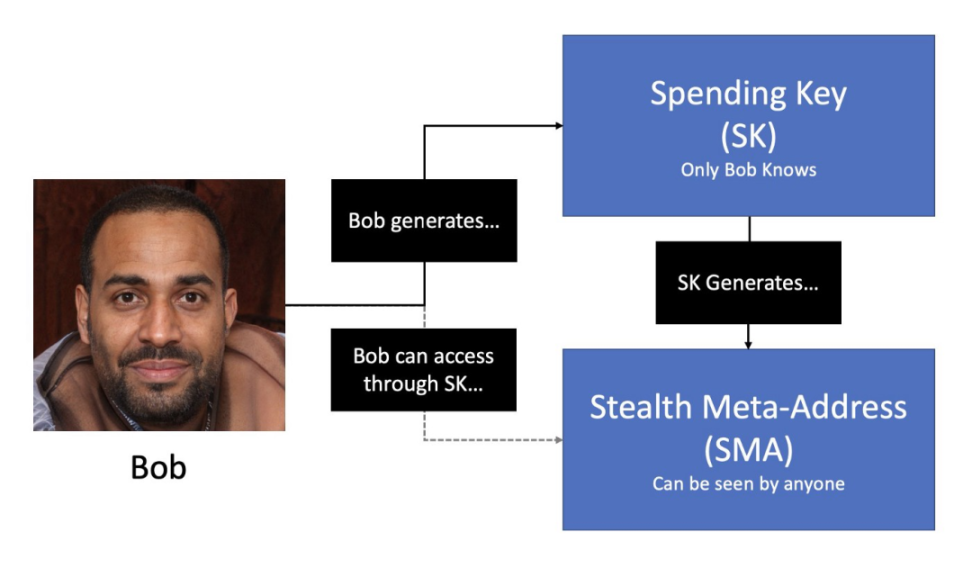
A Stealth Meta-Address, which is a public address that anyone can see, but it is also a master address that can be used to derive an unlimited number of Stealth addresses with partners like Alice.
In order to obtain the invisible meta-address unique to Bob and Alice, Alice also needs to generate two keys:
A temporary private key, known only to Alice;
A corresponding ephemeral public key acts like a stealth meta-address.
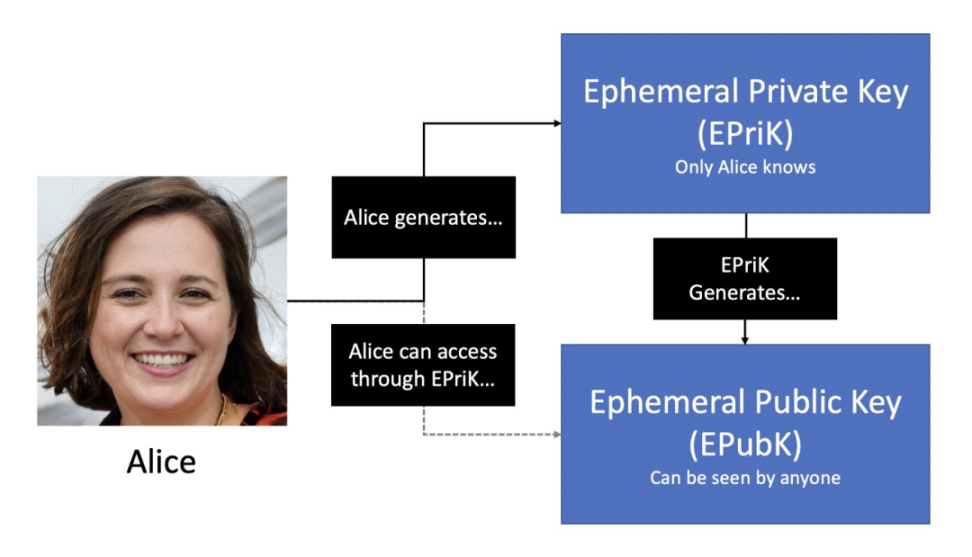
The temporary public key is generated by the temporary private key, which is similar to the generation of Ethereum addresses by mnemonics. The ephemeral public key can be posted to the public ledger where anyone can view it. The ephemeral key pair is used only once, so Alice must generate a new ephemeral key pair if she wants to transact with someone else.
To sum it up:
Bob generates a spending key (private) and uses this key to generate a stealth meta address (public).
Alice generates an ephemeral private key (private) and uses this key to generate an ephemeral public key (public).
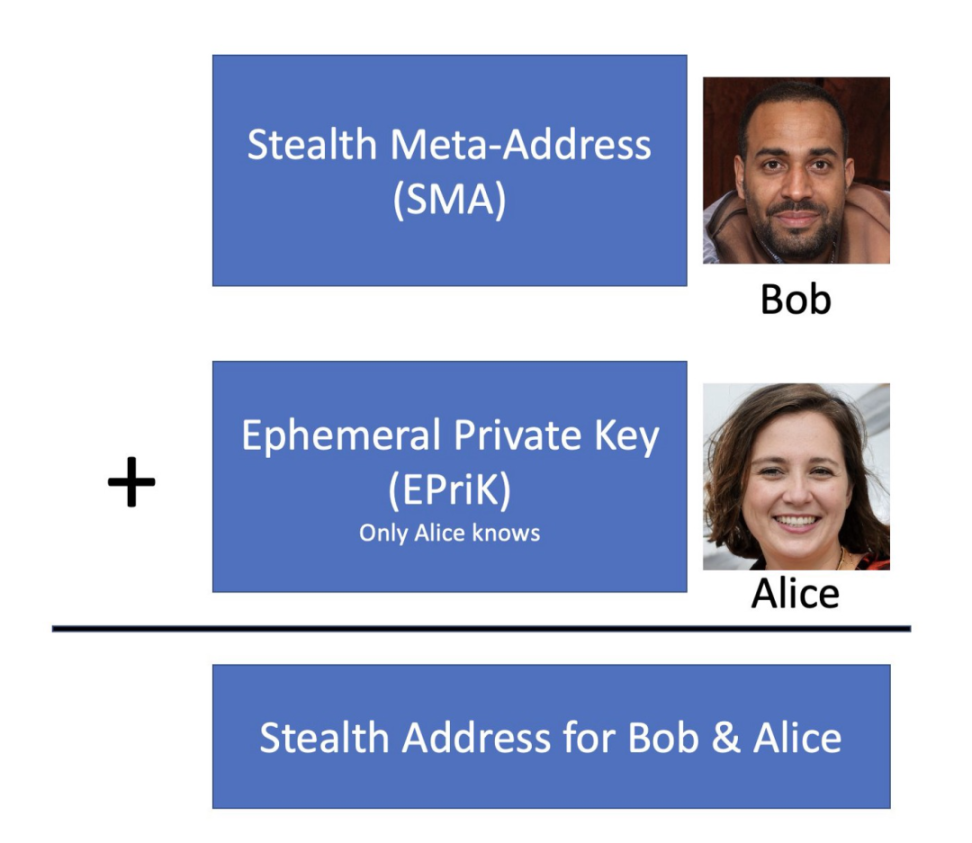
The next step in wanting to generate the final stealth address is for Bob and Alice to share their respective public keys. Bob provides Alice with his own invisible meta-address (public) that anyone can view. Alice then combines the stealth meta-address provided by Bob with the ephemeral private key she created. This combination creates a stealth address. Alice can send 1.2 ETH to the stealth address.
Visit Stealth Address
In order for Bob to be able to find the stealth address where Alice sent him 1.2 ETH, he must also create the stealth address created by Alice, but there is a problem that this step needs to combine Alice’s temporary private key and Bob’s stealth meta-address , the problem is that Bob does not know Alice's ephemeral private key because the ephemeral private key is private.
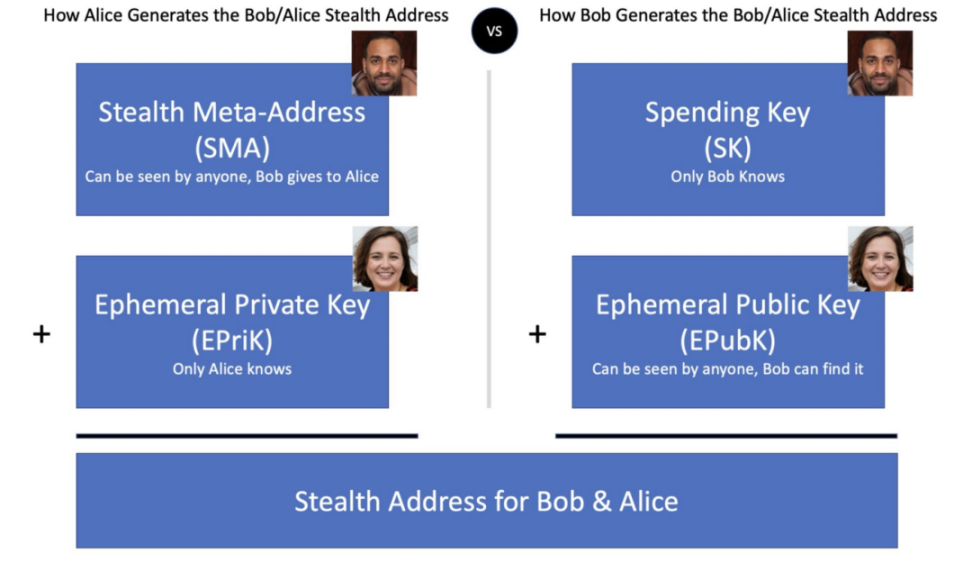
Using cryptography concepts, Bob has another option: he can use different private/public key combinations to create the same stealth address (and use his own spending key to control the cryptocurrency inside the stealth address). Bob can combine his spending key with Alice's ephemeral public key to create a stealth address.
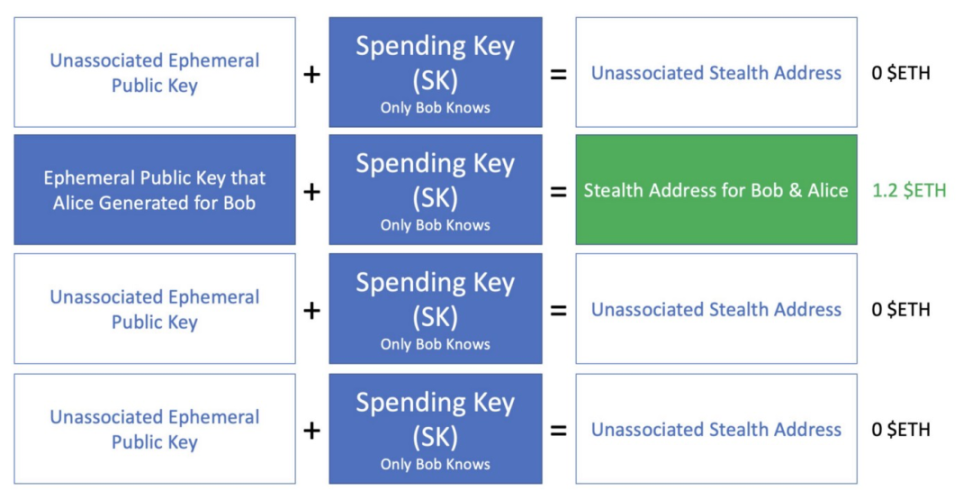
In fact, Bob does not need to manually match all the temporary public keys to find the correct one. This process will be automatically completed by the computer, which will greatly reduce the time and energy invested.
Summarize
Summarize