Are you willing to disclose your wallet address and let everyone know how much money you have? Are you willing to let everyone know your investment preferences and every expenditure? I think many people are unwilling. To achieve the privacy protection of these data, a privacy protocol is required.
There have always been digital currencies with privacy as the selling point in the market, including DASH, XMR, Zcash, Grin, Rose (Oasis Network), FRA (Findora), PHA (Phala network), SCRT (Secret Network), etc. Ten years of development in the encryption industry For several years now, the privacy sector has had its place.
If the privacy track is further subdivided, it can be divided into four categories: privacy computing network, privacy transaction protocol, privacy application, and privacy currency. Among them, the development of privacy coins is the earliest. Tornado in privacy applications is currently widely used, and privacy transaction protocols and privacy computing networks are currently the most concerned.
first level title
secondary title
1. CoinJion
CoinJoin: CoinJoin is a currency mixing mechanism that takes tokens from different senders and combines them into one transaction. The third party packages the tokens and sends them to the receiver. On the client side, each recipient gets his/her tokens in a never-spent address. This is used to reduce the likelihood of a particular transaction being traced.
DASH coin is a typical case of using CoinJion technology to realize private transactions. DASH coin was born in 2014, not for the sole purpose of privacy, but for private transactions as an option for users. Users can choose to use the PrivateSend function for private transactions, or choose normal transactions.
secondary title
2. Stealth address + ring signature
Stealth addresses: Creating a stealth address means creating a new address every time you receive cryptocurrency. It ensures that external parties cannot link the paid address to the permanent wallet address.
Ring signature: Blockchain transactions require digital signatures to verify that the signer is the sender. Because each user's signature is unique, it is not difficult to trace back to the transaction with the signer when the user signs. The ring signature strategy is to combine signatures with the signatures of other ring members: the more ring members sign, the harder it is to directly link signers to their transactions.
Monero XMR uses the combination mode of hidden address + ring signature to realize privacy protection. Monero is not about selective privacy, but total privacy. Monero provides each wallet owner with a new private view key, recipient address, and a private spend key. Moreover, XMR mining can be completed with a general computer CPU and does not require a professional mining machine, which makes XMR more decentralized to a certain extent.
secondary title
3. Mimblewimble
The word Mimblewimble comes from the spell "Confusion Curse" in "Harry Potter". There are two main projects, Grin and Beam, that use this privacy protocol. The technologies used by Mimblewimble include Confidential Transaction, CoinJoin and Cut-through.
The Mimblewimble protocol is a solution that finds Tradeoff between anonymity and scalability. This is a design scheme that provides cryptocurrency privacy for public ledgers based on the output model. It does not involve a consensus layer, so it can be used on almost any consensus rules .
secondary title
4. Zero-knowledge proof class
Zero-Knowledge Proof (Zero-Knowledge Proof) means that the prover can convince the verifier that a statement is correct/true without providing the verifier with information beyond the validity of the statement itself.
Zero-knowledge proofs were first theorized by Goldwasser, Micali, and Rackoff in 1989. At present, zero-knowledge proof is mainly used in two aspects in the blockchain industry: privacy protection and scalability. This paper mainly introduces the application of zero-knowledge proof in protecting privacy.
Zero-knowledge proof is used for privacy protection. It was first practiced on Zcash. Later, many projects such as Aztec, Manta Network, and StarkWare gradually adopted the zero-knowledge proof mechanism, and evolved many new technologies.
Introduce the zero-knowledge proof mechanism through the example of "Alibaba and the Forty Thieves":
Alibaba is the prover, and Thief is the verifier. The thief caught Ali Baba and asked him to speak the spell to open the cave where the treasure was hidden, or he would kill him. If Ali Baba utters the spell directly, he may be killed because of the loss of use value; if Ali Baba insists on not speaking, the robber will think that he does not know the spell and will kill him. Ali Baba thought of a way and asked the robber to be within an arrow's reach of him. If Ali Baba couldn't open the stone door of the cave or escape by chanting a spell, the robber could shoot him to death with a bow and arrow.
In this way, Ali Baba is able to prove that he does know the spell while being far enough away from the robber that he cannot hear what the spell is. In this process, Alibaba (the prover) does not directly reveal what the spell is, but it can convince the thief (verifier) that a certain assertion (Alibaba has the spell) is true.
zk-SNARK
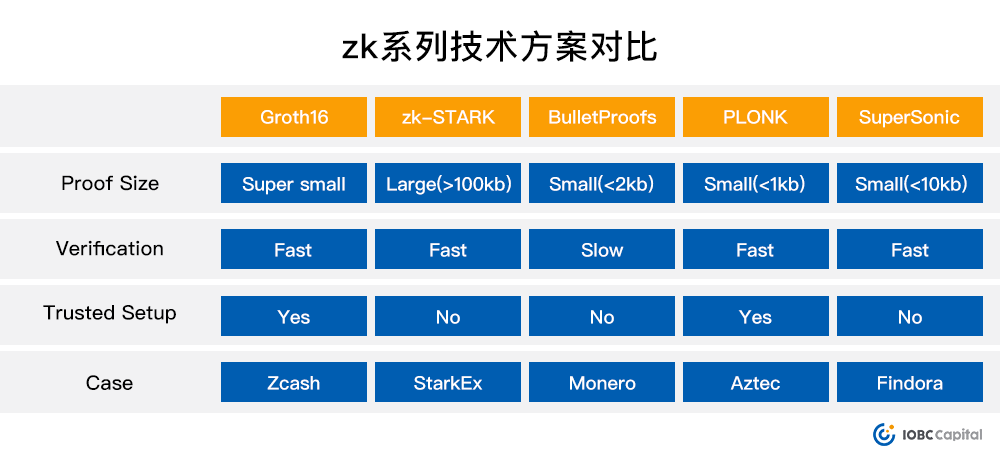
The full name of zk-SNARK is" Zero-Knowledge Succinct Non-Interactive Argument of Knowledge", the Chinese name is "Zero-Knowledge Concise Non-Interactive Knowledge Argument". zk-SNARK was proposed by Ben-Sasson et al. of the Israel Institute of Technology in the Zerocash paper in 2014. It is currently the most widely used zero-knowledge proof privacy technology. Well-known projects that directly deploy the zk-SNARK algorithm include Zcash, Loopring, etc. . It allows people to prove that they have specific information without revealing the content of the information.
zk-SNARK is a technology that transforms the zero-knowledge proof mechanism into a computer programming language. The basic logic is as follows:
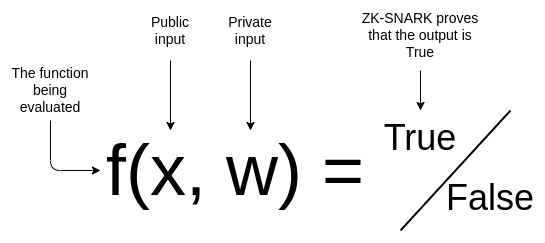
What kind of privacy does zk-SNARK specifically implement? zk-SNARK achieves complete privacy, not only hiding the addresses of both parties to the transaction and the amount of the transaction, but even the nodes do not know the content of the transaction. But the disadvantage of zk-SNARK is that it requires a trusted initial setup (trusted setup). No matter how this setup is set, there are some potential security risks after all.
On the basis of zk-SNARK, in order to improve privacy while also taking into account the optimization of transaction capacity and transaction cost, Bulletproofs, zk-STARK, Sonic, PLONK, Supersonic and other new zero-knowledge proofs were derived later.
Bulletproofs
Compared with zk-SNARK, Bulletproofs do not require trusted initial settings, but verifying Bulletproofs is more time-consuming than verifying zk-SNARK proofs. Bulletproofs are applied in the XMR project to increase the transaction size of XMR and reduce its verification time by 80% .
zk-STARK
The full English of zk-STARK is Zero-Knowledge Scalable Transparent Argument of Knowledge, "Zero-Knowledge Scalable Transparent Argument of Knowledge". zk-STARK was developed by StarkWare, which uses novel cryptographic proofs and modern tapes to enforce the integrity and privacy of calculations on the blockchain. StarkEx uses zk-STARK technology. zk-STARKs allow blockchains to offload computations to a single off-chain STARK prover, and then use on-chain STARK validators to verify the integrity of those computations.
Compared with zk-SNARK, zk-STARK is considered to be a faster and lower-cost technical implementation, because its calculation amount increases, but the communication amount between the prover and the verifier remains the same, so zk-STARK The overall data volume is much smaller than the data volume in the zk-SNARK proof. And zk-STARKs do not require an initial trusted setup, as they rely on simpler cryptography through collision-resistant hash functions. Overall, zk-SNARKs have made significant progress in refinement and adoption, while zk-STARKs fill many of the shortcomings of zk-SNARK proofs (faster, cheaper, and do not require an initial trusted setup) and are considered the An improved version of the protocol, but zk-STARK adopts off-chain calculation and on-chain verification, which seems to be inferior to zk-SNARK in terms of security.
Sonic
Sarah Meiklejohn of the University of London, Markulf Kohlweiss of the University of Edinburgh, and Sean Bowe of Zcash proposed a zero-knowledge proof protocol called Sonic. any possibility.
The emergence of Sonic has taken a big step forward in the evolution of zero-knowledge proofs. However, the speed of Sonic is reduced, because compared with non-universal SNARK, Sonic’s proof construction time increases by about 2 orders of magnitude, so there are currently no well-known privacy projects that adopt Sonic technology solutions.
PLONK
PLONK is an efficient and universal zk-SNARK jointly developed by CTO Zachary Williamson of the Aztec protocol and chief scientist Ariel Gabizon (Protocol Labs and former Zcash). Ariel Gabizon and Zac Williamson developed PLONK during a chance meeting at the Binary District workshop in London.
This is a brand-new efficient universal zk-SNARK. PLONK only needs one trusted setting, which can be reused by all programs. This technology has also been forwarded by Vitalik. How fast is PLONK? On fully standard hardware, PLONK is able to go through a circuit with over 1 million gates in 23 seconds. There are no server farms or HPC clusters here—this data comes from Microsoft Surface tablets.
Taking Aztec as an example, briefly describe the working principle of Aztec, a privacy protocol based on PLONK:
First, Aztec needs a trusted initial setup - Ignition CRS. At the beginning, Aztec randomly called 200 participants around the world to obtain Ignition CRS. Each of these 200 participants creates randomness - the basis for Aztec's proof-of-security. (This is equivalent to 200 people shuffling the cards. As long as not all 200 people collude, as long as one of them is an honest participant, the randomness of the cards can be guaranteed, which is the security of the system.)
Then, Aztec's regular privacy transactions can be understood as a UTXO (as shown below). Similar to how Bitcoin works, but with the difference that Aztec requires encryption for transactions. Therefore, Ethereum will verify whether this UTXO is correct - that is, check 60+40 =75+25.
How to check it? First check that the input note = output note; in order to prevent surround attacks (for example: 10 = 11+ -1), and set the Range Proof (range proof), so Aztec instead deploys the proof of set membership - the transaction needs to obtain the Aztec cryptographic engine (ACE) approval, users need to demonstrate that they form output annotations from Codex. After this series, the correctness of UTXO can be successfully verified.
The privacy that Aztec wants to achieve includes three aspects: one is data privacy, Aztec can encrypt and hide the transaction amount; the other is user privacy, people watching the network can no longer determine the ID of the sender and recipient; the third is code privacy , the smart contract code of the dApp using the Aztec SDK can also be private. The first of which has been achieved, the latter two have not yet been achieved.
SuperSonic
SuperSonic technology combines Sonic and DARK proofs. It is a short proof that does not require trusted settings. Under the premise of 1 million logic gates, the proof size can be compressed to 10-20 KB, and there is even room for optimization. This technology is first applied in financial companies. Chain on Findora.
The comparison of zero-knowledge proof series technical solutions in terms of verification proof size, verification speed, whether trusted settings are required, and application cases is as follows:
secondary title
Future Trends of Privacy Technology
At the current stage, the utilization rate of private transactions is still low, and it is expected to increase with technological changes
There are three main reasons for the low usage rate of private transactions: First, the technical threshold is too high, and the early private transactions are not friendly to most ordinary users. Although privacy coins such as Zcash and XMR have existed for many years, most of them Most ordinary people have never really used them; the second is that the demand for private transactions has not been popularized. Before talking about private transactions, everyone subconsciously believed that only some invisible transactions needed private transactions. The awareness of transaction, transfer/payment and other behaviors and amounts is still relatively weak. With the outbreak of on-chain transactions such as DeFi, people's awareness of privacy protection for on-chain transactions is awakening; third, the early privacy protocols did not provide users with real For the currencies that you want to use, such as ETH, USDC, DAI mainstream chain assets, etc., the probability of ordinary users deliberately choosing to use privacy coins in order to maintain privacy is not high.
The deployment of privacy functions in mainstream blockchains may be the ultimate trend in the development of the privacy field
As an independent existence, privacy coins may no longer be sought after and welcomed, especially after being chased and intercepted by various countries in the past few years. For example, affected by FATF rules, Coinbase UK delisted Zcash in 2019, while OKEx South Korea delisted six cryptocurrencies including Monero, Dash, Zcash, ZCache, Horizon and SuperBitcoin.
But the demand for private transactions is real, and there will always be this demand, and if there is demand, there will be a market. According to the types of privacy projects that have received the most attention in the industry recently, the way of incorporating privacy protection functions into mainstream blockchains represented by Bitcoin, Ethereum, Polkadot, etc. may become a trend.
Coinjion technology is used in bitcoin transactions, which is currently a widely used mixer (Mixers) service for hiding transaction information. Mixers uses a third party to connect the bitcoin sender address and the receiver address A service that hides transaction information by scrambling.
The most concerned privacy solutions on Ethereum are the zero-knowledge proof series (zk-SNARK, zk-STARK, etc.). Vitalik once said that "Zero-knowledge proof is the most powerful privacy solution. Although the technology is the most difficult to implement, it has the best effect on protecting the privacy and security of the Ethereum network." And zero-knowledge proof privacy solutions Among the solutions, Aztec's PLONK technology is more respected.
In the Polkadot ecosystem, there is also a private transaction project that has attracted more attention-Manta Network. It is a zk-SNARK type (Plonk with Lookup) privacy protocol built by P0xeiden Labs. Manta Network is deployed on Polkadot, and its test network Calamari is deployed on Kusama. The chain deploys the corresponding privacy protocol. Manta Network plans to launch MantaPay, a multi-asset decentralized anonymous payment protocol, and MantaSwap, a decentralized transaction protocol with AMM mechanism supported by zk-SNARK.
References:
References:
1、https://vitalik.ca/general/2022/06/15/using_snarks.html
2、https://developers.aztec.network/
3、https://emphasized-seed-161.notion.site/PVM-P0xeidon-VM-primer-5bf16a3ef16e4a8696e99ede6d71ea95