April 23, 2022Chengdu Lianan Chain Bing-Blockchain Security Situational Awareness Platformfirst level title
#1 Event Related Information
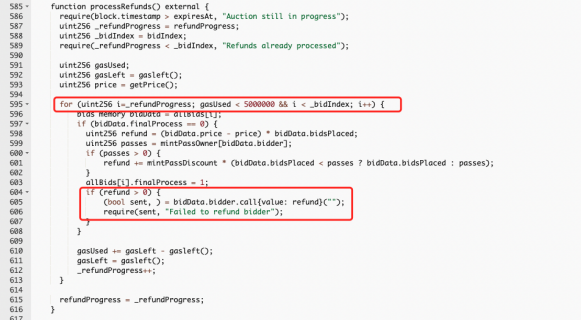
On April 23, Solidity developer foobar tweeted that 11,539 ETH (worth $34 million) was permanently locked in the AkuDreams contract, and neither individual users nor development teams could withdraw funds. Set each bid status to 1 after the refund has been processed. Therefore, the user cannot call emergencyWithdraw(). In addition, the team cannot receive funds, which is basically equivalent to destruction.
Vulnerable contract:
Vulnerable contract:
0xf42c318dbfbaab0eee040279c6a2588fa01a961d
#2 Vulnerability Analysis
Vulnerability one:
Vulnerability one:
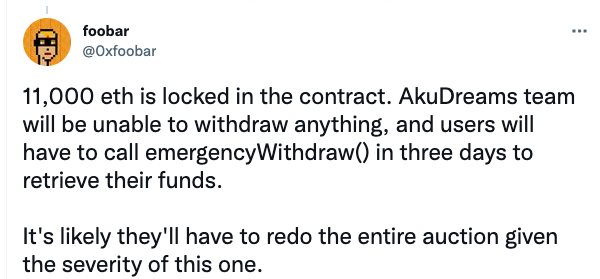
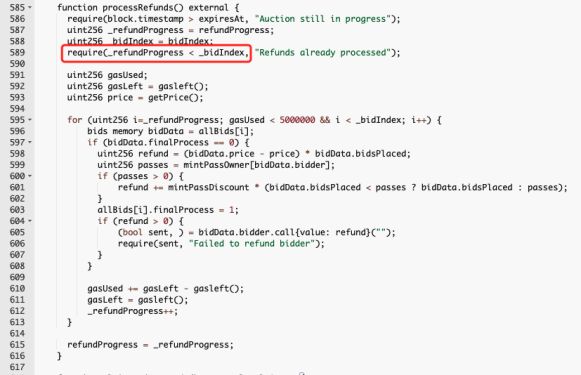
1. The first contract loophole is inprocessRefunds, the designer performs a circular refund according to the refundProgress counter.
2. Here, the call function is used for the refund operation, and the result of the refund is used as the judgment condition of require.
3. Therefore, if an attacker is performing a refund operation in the queue at this time, when the call refund is called to the attacker, the attacker performs a malicious revert in the fallback, which will cause the refund queue to be stuck at the attacker, resulting in Everyone behind the queue cannot be refunded.
Vulnerability two:
Vulnerability two:
The bug was also the culprit that caused about $34 million worth of ETH assets to be locked in the contract.
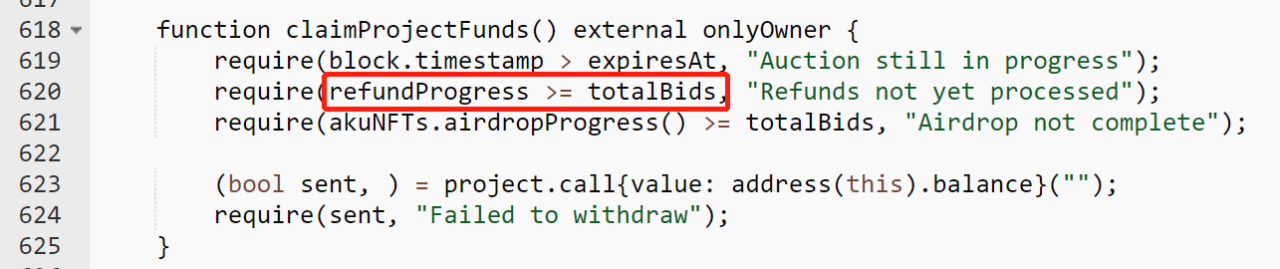
1. In the claimProjectFunds function, this function is mainly used for withdrawal by project parties. In order to prevent the project party from having too much authority and transferring all the assets in the contract before the user completes the withdrawal, the user cannot get a refund. All refund operations should be completed before the project can withdraw funds. In terms of business logic design, there is no problem. However, in the specific code implementation, the current code is vulnerable to Vulnerability 1, causing the project party to be unable to withdraw funds, but this is only a potential risk, and the culprit of the fund lockup this time is not the reason.
2. Pay attention to the 620th line of code in the function: require (refundProgress >= totalBids) where refundProgress indicates how many users' refunds have been processed, and totalBids indicates how many NFTs all users have bid for. Note that since a user can bid for multiple NFTs, refundProgress may be less than totalBids in numerical comparison.
Let's take a look at the refund function processRefunds: require(_refundProgress < _bidIndex); bidIndex means that all users participating in the bidding, refundProgress will never be higher than bidIndex.
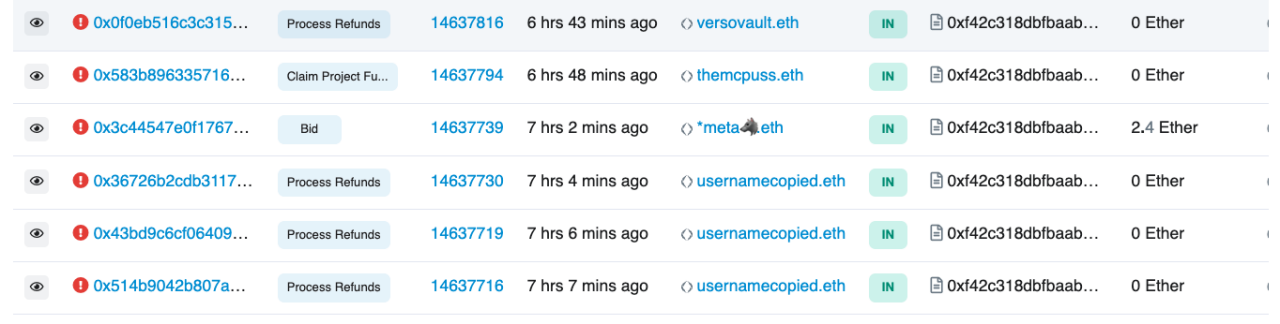
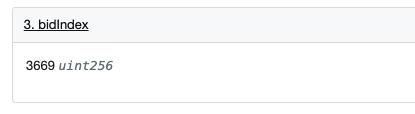
At this point, let's take a look at the value of bidIndex, which is 3669:
The value of totalBids is 5495:
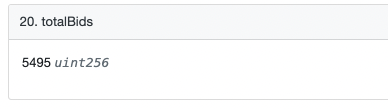
3. So refundProgress>=5495 and refundProgressfirst level title
#3 Summary
In response to this incident, the Chengdu LianAn technical team suggested:
1. Developers should have basic security development awareness and be familiar with security issues that should be paid attention to in smart contract development;
2. When designing and implementing the contract, pay attention to the correctness of the code implementation. Before the project goes online, you can choose a professional security audit company to conduct a comprehensive security audit to avoid security risks.