As the Bitcoin halving approaches, attention is increasing on how to improve the capital utilization of $BTC, and the development of Bitcoins second layer has become the focus. Against this background, Merlin Chain quickly emerged, with TVL exceeding US$3.5 billion within just one month of the start of the staking activity. This month, Merlin Chain launched M-Token. With the gradual release of liquidity, market popularity continues to rise, and its technical design has attracted much attention.
Based on ZK-Rollup, Merlin Chain introduces the decentralized Oracle network and uses Celestia as the DA layer. This technical architecture gives Merlin Chain powerful performance while providing enhanced support for the Bitcoin network.
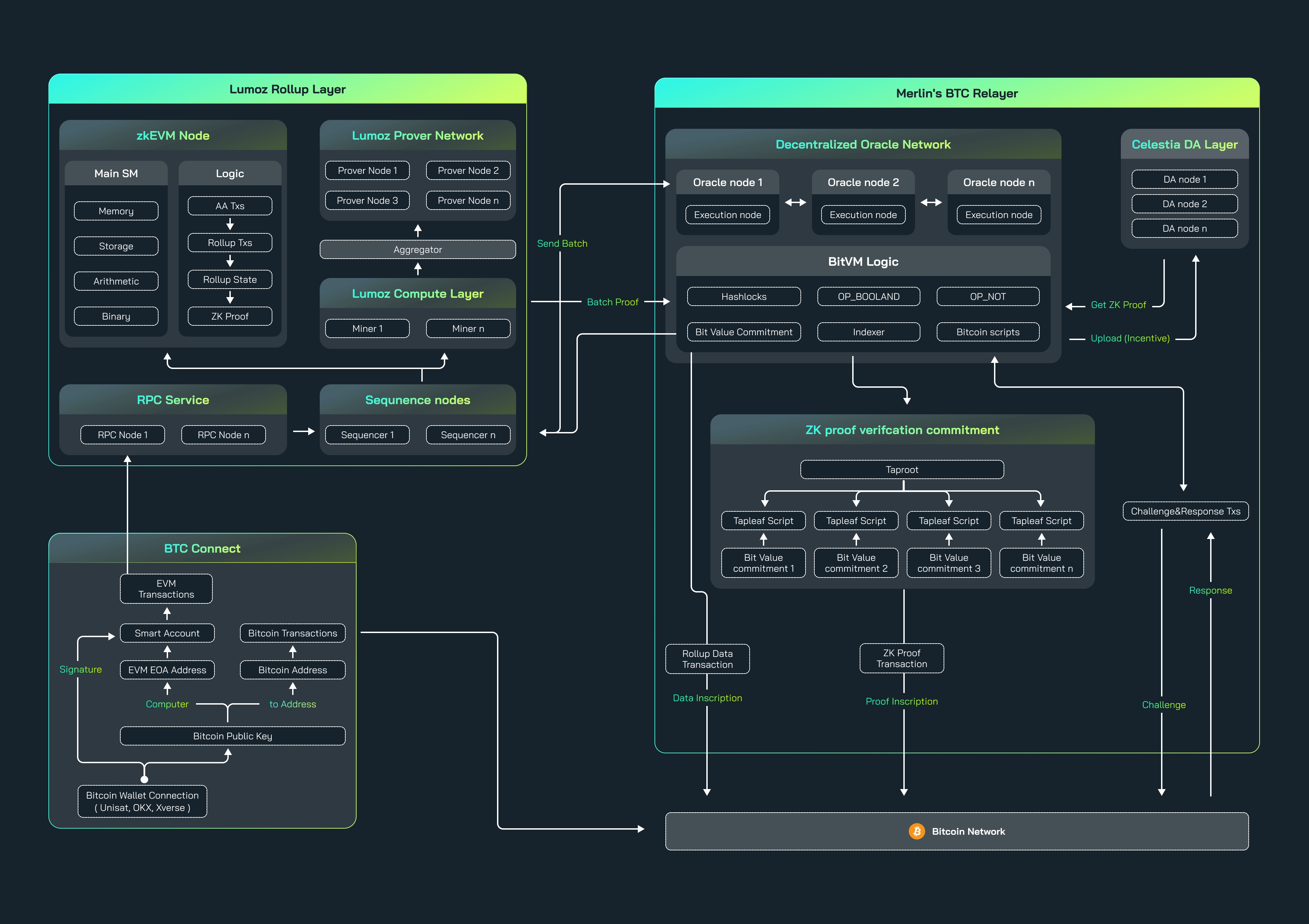
In this article, we will delve into the technical features and innovations of Merlin Chain.
Highly scalable ZK-Rollup
Merlin Chain proposed a solution based on Taproots aggregated zero-knowledge proof and Rollup data writing to the Bitcoin main network, realizing a highly scalable ZK-Rollup and solving the Turing incompleteness of the Bitcoin network.
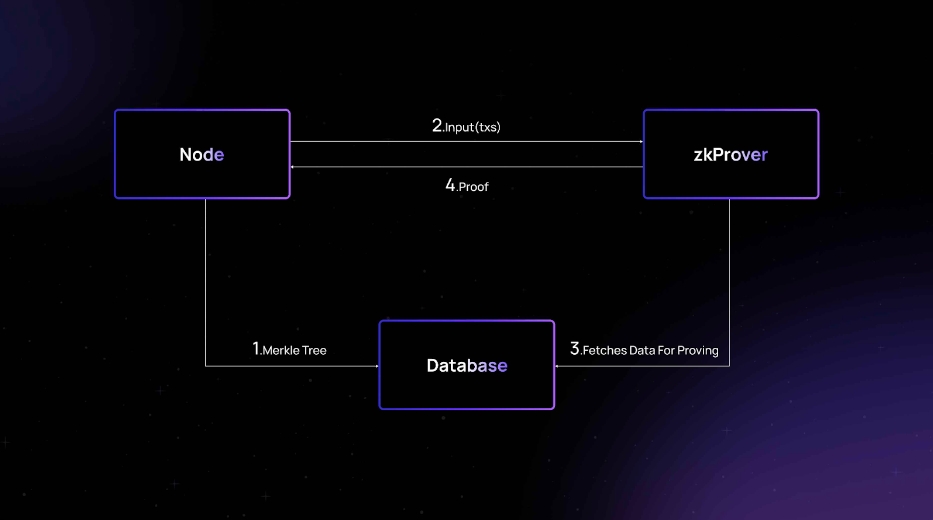
The network aggregates and compresses transaction data into batches, and then submits them to Taproot on the Bitcoin mainnet through zero-knowledge proofs. Important components include nodes, zkProver and database. The three work together to complete data exchange and storage to ensure the smooth progress of transaction processing and verification processes:
Node: responsible for processing and transmitting transaction data, as well as interacting with zkProver and the database
Send the contents of the Merkle Tree to the database and store it there
Send input transactions to zkProver for processing
Interact with zkProver to ensure the validity and correctness of transactions
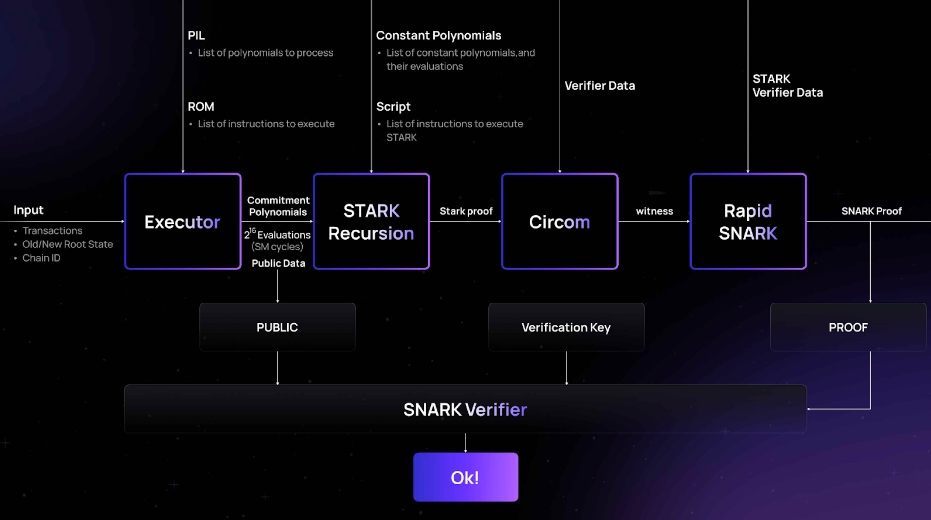
zkProver: Use SNARK technology to generate zero-knowledge proofs to prove the validity and correctness of transactions
Contains 13 types of state machines, divided into main state machines and sub-state machines (such as BinarySM, StorageSM, MemorySM, ArithmeticSM, etc.)
Perform complex mathematical calculations, use PIL (Polynomial Identity Language) to describe state transitions and constraints during transaction execution, convert them into polynomial constraints or polynomial identities, and verify them on the smart contract
Interact with nodes and databases to obtain information to generate verifiable proofs of transactions, including information such as the Merkle Root, associated sibling keys, and hashes
Send the generated transaction proof back to the node so that the node can further verify and record it to ensure the legality and security of the transaction.
Database: used to store important data, such as the contents of Merkle Tree and transaction information
Receive and store the contents of the Merkle Tree sent by the node
Provide zkProver with the information needed to generate transaction proofs
This model brings many benefits to Merlin:
Security: Inherits the security of Bitcoin, provides L2 batch processing scalability, and ensures that data is anchored in Bitcoin and cannot be tampered with.
EVM compatibility: Supports existing smart contracts and tools to ensure interoperability
Low cost: Use ZK proof and zkSNARK technology to reduce L1 space consumption and optimize transaction costs
High performance: ensure the fast finality of transactions through frequent validity proofs, and recursive STARK to achieve scalability to cope with high concurrency and large-scale user needs
Decentralized Oracle Network
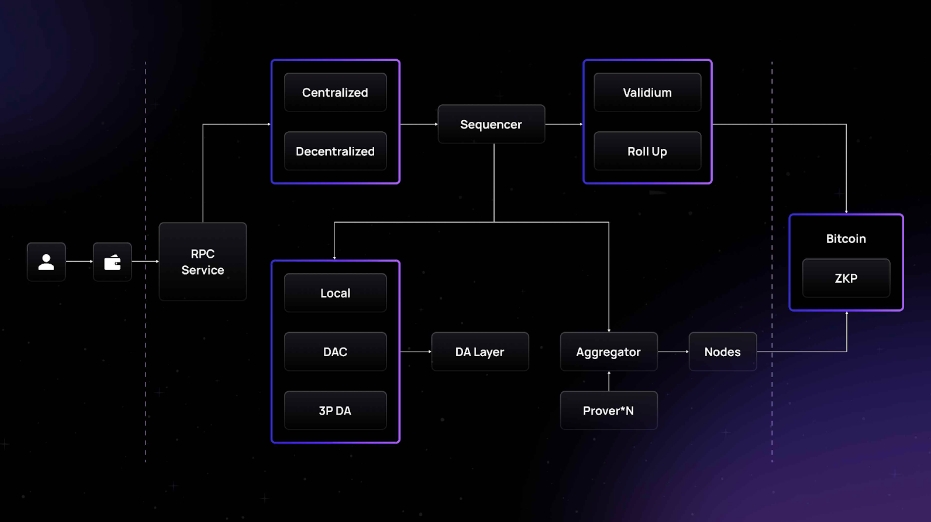
Merlin Chain uses a distributed Oracle network. Sequence nodes are responsible for collecting and batch processing transactions, generating compressed transaction data, ZK state roots and proofs. This data is compiled by the Oracle Network Execution Circuit and uploaded to Taproot on the Bitcoin mainnet, making it publicly accessible to the entire network. The specific mechanism is as follows:
Employs fraud prevention mechanisms specifically designed for ZK Proofs to provide final confirmations on Bitcoin
All original data is stored in the Oracle network, and the corresponding state root is stored in the Bitcoin network
Users can retrieve all aggregated transactions on Merlin Chain at any time
Users can use ZK to prove the correctness and validity of the data without exposing the specific data content.
By decentralizing power and data, Merlin Chain resists the risks of single points of failure and centralization. At the same time, the system uses multi-signature and cold storage technology to ensure the security of pledged assets. All staking and reward distribution processes are open and transparent, and users can check their staking status and expected returns at any time.
The design of node staking is as follows:
Diversified assets: Supports the pledge of $BTC, $MERL and other mainstream BRC 20 assets, improving flexibility and risk resistance.
Smart contract management: All agent staking and reward distribution will be automatically executed through smart contracts to ensure the non-tamperability and fairness of the process
Real-time monitoring: Users can view their agent pledge status and income in real time, as well as the performance records of agent nodes
Exit mechanism: The system provides a flexible exit mechanism. Users can withdraw their assets at any time to ensure the liquidity of funds.
Data availability
Merlin Chain uses Celestia as the data availability layer to ensure the verifiable release of block data and enhance the transparency and credibility of the network:
Celestia provides public data availability guarantees, allowing everyone to view and store the state of Merlin Chain
Rollups and applications are responsible for storing historical data once it is published on Celestia and confirmed to be available
When a node receives a new block, it will verify the availability of the data to ensure that the data in the network is complete and consistent.
Zero-knowledge proof two-step submission mechanism
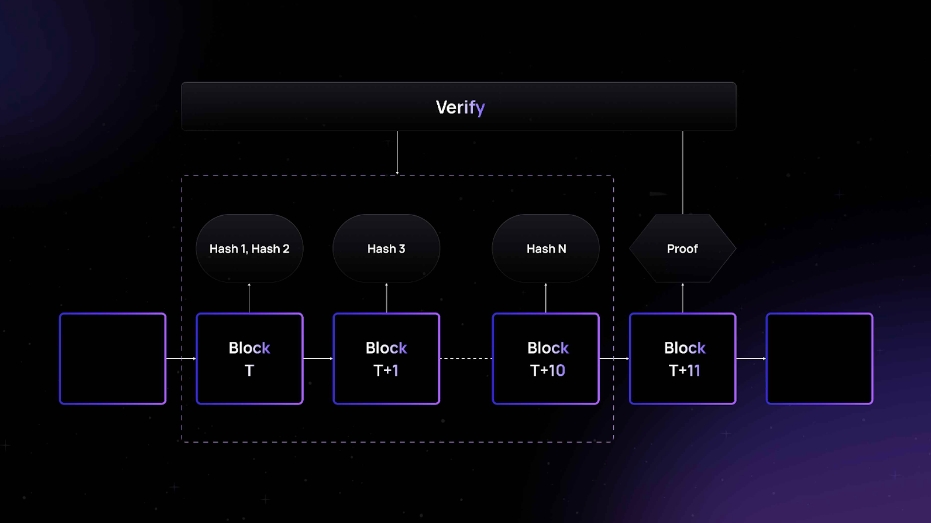
Merlin Chain will adopt the zero-knowledge proof (ZKP) two-step submission mechanism proposed by Lumoz in the future to achieve decentralized PoW:
Submit hash
Provers to generate ZKP for a specific sequence need to first calculate the hash of (proof/address) and submit that hash along with their address to the chain-level smart contract
proof represents the ZKP of the sequence, and address identifies the provers identity
The initial provers hash submission is unrestricted and will be processed and accepted within the next T+ 10 blocks; after the T+ 11th block, new provers will not be allowed to submit additional hash values.
Submit ZKP
After block T+11, any prover can submit a complete ZKP
A verified ZKP can be used to verify all previously submitted hashes
The prover will receive PoW rewards based on the proportion of the stake
This mechanism can effectively motivate miners to stay online, ensure a stable computing environment, and further enhance the security and reliability of the network:
Prevent racing attacks: Prevent malicious actors from trying to interfere with or disrupt the normal operation of the system by submitting large numbers of proofs quickly
Encourage stable participation: encourage miners to provide stable and continuous ZKP computing power through rewards, enhancing the security and reliability of the network
Ensure system efficiency: ensure efficiency and fairness, avoid resource waste and network congestion, while improving overall system performance and stability
Bitcoin-based fraud proof
Merlin Chain will introduce a fraud proof mechanism in the future to further ensure the integrity and security of data.
This mechanism involves two roles, Prover and Verifier. The specific implementation path is as follows:
Provers and verifiers pre-sign a series of transactions to ensure that a challenge-response mechanism can be enabled between them
The prover converts the program to be verified into a binary circuit containing many NAND logic gates to ensure the integrity and correctness of the data
Each logic gate has a leaf script that defines and describes the behavior and functionality of that logic gate
The prover puts the leaf script of each logic gate in this large binary circuit into a Merkle Tree and submits the Merkle Root to the Taproot address
The verifier extracts the Merkle Root from this Taproot address and verifies its validity
If the verifier suspects that there is a problem with the Merkle Root submitted by the prover, such as incorrect data or fraudulent behavior, the challenge-response mechanism can be enabled to challenge the prover and require them to provide the corresponding leaf script or other proof to prove the Merkle Root. correctness
The prover needs to provide corresponding evidence according to the challenge to prove that the Merkle Root they submitted is correct.
The verifier will verify these evidences to ensure the correctness of the proofs and the integrity of the data
With the Bitcoin halving approaching, the market is full of expectations for the continued development and innovation of Merlin Chain. As the leader of Bitcoins second-layer network, Merlin Chain is expected to continue to promote development and innovation, providing users and developers with more stable, secure, and rich blockchain services and application scenarios.