Article author: Crux. , Twitter:@ElaineZhoux, PKUBA researcher
Summary
question
1. As a long-term narrative that spans Web2 and Web3 and will continue to be mentioned in the foreseeable future, Anti Sybil (Anti Sybil), although its concept is straightforward and simple, involves complex tracks and application scenarios. How should it be integrated and coherent? How to view and understand the anti-witch actions in different historical stages and textual contexts?
2. Is the anti-witch campaign just an “anti-user” demand driven by the value of decentralized philosophy? What is the core underpinning logic behind the opposition to woolists/scientists?
3. At present, what is the development stage and solution maturity of anti-witch technology in different application scenarios? Which new narratives are actually continuations of anti-witches?
4. What is the likely outcome of the game between “anti-witches” and “wool”?
5. What potential project investment opportunities are there?
core points
Each user has a strong incentive to become a witch and achieve multi-identity arbitrage. Therefore, at the current stage, anti-witches are not the direct needs of users, but more the needs of application scenario projects. However, the anti-witch measures of the project side are closely related to the revenue ceiling that ordinary users can obtain in various economic incentive application scenarios. As a user, taking stock of the various layers of anti-witch narratives in advance may help you quickly determine which projects are worth gaining new recruits and which project incentives are actually unprofitable, so you can manage your expectations well.
Even if it may face community resistance in some cases, we have every reason to believe that anti-witches extend more solid ecological value in the broader scene narrative, and is a positive-sum game of continuous gain rather than a zero-sum game as commonly thought . In fact, the scenarios and solutions to witch attacks existed long before airdrops and wool parties became popular. Some new narratives and discussions that emerged later are actually a continuation of anti-witch attacks, such as mining, voting, donations, UBI, and credit scores. and social graph.
If the project side cannot provide credible commitments and technical proof to community members in combating Sybil attacks, long-term Sybil attacks will damage the security and credibility of the project. Old users and potential new users may reduce their participation or completely avoid investing in the project, which may lead to a series of chain problems at the application layer such as the loss of miners, a decrease in the pledge rate, an overestimation of the number of real users, insufficient donation incentives, and excessive issuance of universal basic income. .
The narrative related to anti-witches is mainly divided into three layers: application scenarios, protocol consensus and verification detection. The application scenario layer determines the value target of Anti-Sybil, the protocol consensus layer determines the institutional rules of Anti-Sybil, and the verification and detection layer determines the technical efficiency of Anti-Sych. The infrastructure work of catching witches and marking witch addresses is the narrative foundation of the future DeFi credit scoring layer, SocialFi and GameFi social graph layer.
The development of anti-Sybil protocol consensus and verification detection technology is maturing. With the expansion of application scenarios, many leading projects will announce their anti-witch measures before the plan is implemented, and have already gone through several rounds of iterations of technical solutions. Currently, interception detection using a combination of identity credentials and graph mining and other AI-ML algorithms is the most efficient.
Due to the native economic incentive characteristics of Web3, the witch problem is more likely to spread than in the Web2 network environment, and it is difficult to be completely solved by technical means. In the future, every real user may be a mild witch: only one main address can remember and identify one As an identity that can sustainably accumulate reputation (partially overlapping with the semantics of DID), users can only receive incentive benefits provided by project parties such as airdrops through the main address. However, TA can associate local addresses in multiple subdivision scenarios for interaction with application projects to prevent systemic risks arising from the loss or theft of the main address.
The overall logic of primary investment: application value prospects > verification and detection technology > protocol consensus innovation.
1. When we talk about witch attacks, what exactly do we mean?
1. Review of classic concepts
Anti-Sybil, also known as witch hunting and anti-witch attack. Sybil attacks generally refer to irregularities in which a real person controls multiple false identities in order to repeatedly receive incentive benefits provided by ecological builders. It is an extension and expansion of the concepts of anti-cheating and anti-fraud in Web2 in Web3. To put it simply, one person pretends to be several users and hides it from the project team many times. A related phenomenon that is easier for us to detect is the endless emergence of “hair-stroking studios”.
According to rumors, the reason why witch attacks are called witch attacks is because there is a movie called The Witch in which the heroine has more than a dozen personalities. I think it is very vivid to refer to one person controlling multiple false identities.
Witch attacks in the Web2 era: Didi was once defrauded of subsidies by drivers who ran empty orders. The video platform that lets you earn commissions by watching ads is actually spending the brands advertising budget to create false user click data. Celebrity fans are controlling it for crisis public relations. Commenting on the trolls, these are witch attacks in the Web2 era.
2. User needs or anti-user needs?
• From the perspective of users or community ecology participants, the first premise to consider is: Is the community ecology’s appeal against witches really strong enough? It needs to be admitted that at the current stage, anti-witches are not the direct needs of users, but more the needs of application scenario projects. It can even be said that the Woolies may have contributed a large amount of TVL in the early days. Taking the airdrop scenario as an example, users actually have a strong motivation to become witches, but they just weigh the pros and cons in the process of fighting against the reward and punishment rules set by the project team. Most users with potential risks of witches eventually take a step back and become airdroppers. hunter.
• For the project side, failure to issue tokens to real users has two easily imagined consequences: doubling of marketing costs huge selling pressure.
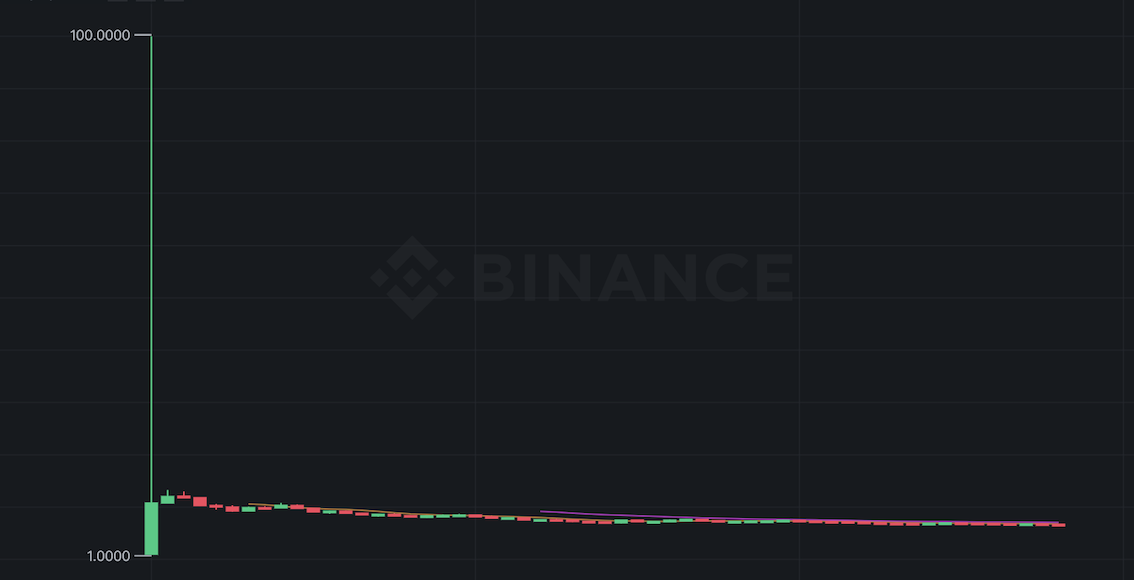
○ For example: Aptos has not formulated anti-witch measures. As soon as the airdrop news came out, there were hundreds of accounts on Twitter and in the community posting screenshots of applying for the test network. So on average, how much did the project actually spend? Ten times the unit cost to acquire a real new user. Second, judging from the trading trend of Binance, the Aptos community failed to withstand the huge selling pressure. After going online, a pin instantly reached $100, then returned directly to around $10, and then fell all the way to $6. Around USD. Research has found that about 40% of tokens flowing into exchanges come from Witch addresses. Therefore, it is also helpful to know the proportion of witch addresses in advance to predict the price fluctuation of project tokens.
○ We can do a simple game analysis to understand the possible collateral impact of the projects anti-witch measures on real users: Suppose Alice is a real user with only one wallet address for interaction; Bob is a witch who controls N A false account, the unit cost of additional investment is F. Before the airdrop, users need to complete tasks, earn points, pay gas fees and other time, energy and money investment. Set it as N*(aZ-bX-cY-dF). Generally speaking, project parties will choose to increase X, Y, or decrease Z to reduce the ROI of Sybil attacks. However, when the project teams anti-witch measures against Bob are not precise enough or too strict, the airdrop income (aZ-bX-cY) of the real user Alice may also drop significantly or even become negative. This can also explain why some airdrops receive a lot of praise from the community, while others cause a lot of dissatisfaction.
○ At present, there are usually two equilibrium states in the game between anti-witch and wool harvesting, and there is a chance to achieve a positive-sum game rather than the commonly thought of zero-sum game:
▪ (1) Default to mild grooming behavior. That is, airdrop hunters who only use 1-3 boutique wallets to obtain airdrops by default. But there will be a crackdown on witch behavior, that is, users who have hundreds of wallets, mostly use scripts or fingerprint browsers, and occasionally operate manually.
▪ (2) Work together to create “false” prosperity. On the one hand, from the perspective of the project side, grooming behavior is an important part of the active data on the project chain, and it can identify various project bugs in the early stages and promote the optimization of product experience, which is equivalent to helping Stress testing has been carried out, and most project parties also need data contributed by wool parties to increase valuations or list CEX. From the perspective of the Wool Party, they can also receive token airdrops in the future, so it is a win-win situation.
2. We are close to a mature anti-witch solution. Where is the progress bar?
To fully understand this issue, we must first realize that Anti-Witch actually has a three-layered narrative structure. Then we will find that the scenarios and solutions to witch attacks existed long before airdrops and wool parties became popular, and some of the new narratives and discussions that emerged later are actually a continuation of anti-witches.
1. The three-layer narrative structure of Anti-Witch: application scenario layer, protocol consensus layer and verification detection layer
The track related to anti-witches is mainly divided into three layers: application scenarios, protocol consensus and identification detection. The application scenario layer determines the value target of Anti-Sybil, the protocol consensus layer determines the institutional rules of Anti-Sybil, and the verification and detection layer determines the technical efficiency of Anti-Sych.
1.1 Application scene layer: Where do witches appear?
Mining
“Mining” here is taken in the narrow sense under the PoW consensus mechanism.
• Value goal: Maintain proportional verification computing power supply and main chain control. Under the Proof of Work (PoW) consensus mechanism, attackers who have mastered the majority of computing power can conduct fraudulent operations in the blockchain network. The goal of Witch may be to launch a 51% attack to create a new main chain, and then achieve double-spending (double spending) arbitrage on the new main chain by revoking, reversing, or not confirming the transaction records of the old main chain.
• Related solutions: Natural defense is usually achieved by increasing the scale of the blockchain network. Witch attacks generally occur in small chains. The computing power and hardware resources required by large chains are too high, and the input-output benefits of Witch attacks ( ROI) is very low and unprofitable will naturally reduce the frequency of Sybil attacks and security threats. In this sense, the leading public chain (such as BTC) naturally has the basic advantage of low-cost defense against Sybil attacks than other small chains based on PoW; other related concepts: decentralized distributed computing power.
vote
• Value goal: Maintain a proportional pledge rate and voting rights. Under the Proof of Stake (PoS) consensus mechanism, witches manifest themselves by intervening in voting by purchasing governance tokens. Voting power or decision-making power is usually related to the number of tokens a user holds, so an attacker who obtains a large number of tokens through a Sybil attack may disproportionately vote for an unreasonable proposal and subsequently manipulate the voting results. This can result in the bribery efficiency of a particular proposal being artificially increased or decreased, with resource allocation within the project tilted toward the interests of a particular group. Simply put, by purchasing a large amount of governance tokens and depositing them in multiple seemingly unrelated wallets, whales have the opportunity to obtain more than 51% of the voting rights and dominate the voting results.
• Related solutions: First, similar to the PoW consensus mechanism, a Sybil attacker cannot launch an attack just by registering a new wallet address, but needs to invest in purchasing a large number of governance tokens. Therefore, large chains are more likely to resist low-cost attacks than small chains. Witch attack. Second, the Proof of Personality (PoP) consensus mechanism can solve this problem. The core idea is to ensure that each participant has only one identity or voting right in the network. Unlike traditional blockchain consensus mechanisms such as Proof of Stake or Proof of Work, PoP focuses on the uniqueness of an individuals identity rather than weight based on economic resources such as currency age, token holdings, or computing power.
airdrop
• Value goal: Issue tokens to real early contributing users to maintain proportional new users and marketing costs. Airdrops are a commonly used user growth tool for project parties to attract new users, and are currently the main front for the anti-witch campaign. As mentioned above, failure to issue tokens to real users will have two easily imaginable consequences for the project: doubling the cost of marketing and attracting new users and creating huge selling pressure.
• There are two main types of airdrops: (1) Push airdrop: generally refers to tokens or NFT appearing in user wallets through full distribution; (2) Pull airdrop: users actively receive rewards, including Uniswap, ENS, 1INCH and Cow Swap, etc. wait. Push airdrops can easily be used as a means of fraud, so most project teams adopt the Pull mode for their airdrops.
• Related solutions: reputation score or identity proof (Gitcoin Passport, DegenScore, Otterspace, Trusta Labs); biometric information verification (Humanode, Worldcoin); KYC, SBT, Poap, Proof of human and other DIDs solutions.
Donate
• Value Goal: Maintain proportional public goods scores and donation amounts. For example, Quadratic Funding for public goods is a matching donation mechanism that balances the contradiction between donation incentives and decentralization. Although Quadratic Funding reduces the impact of a single large donation on the matching pool. The impact of public goods scoring has initially provided an algorithm design that balances the contradiction between donation incentives and decentralization, but it is very vulnerable to witch attacks. The reason is that compared to one account, registering multiple accounts can affect the allocation of allocations with a total investment of less funds. Moreover, even if project review, donor certification and data backtracking will reduce the success rate of witch attacks, there is still the possibility of witch poisoning:
○ Witch poisoning: The attacker uses a witch account to make small donations to competitors or projects at the top of the rankings, so that the project will be judged as a witch by the data analysis team, thereby preventing the project from receiving matching donations. On the one hand, this hits competitors, and on the other hand, the canceled matching donations will return to the matching pool, allowing the attackers own project to receive more matching donations. Once such an attack method is established, the blackmail behavior of the Witch account against the project will also occur.
• Related solutions: Reputation scoring or identity proofing solutions such as GitCoin Passport.
Universal Basic Income (UBI)
• Value Objective: Distribute UBI funds to real members of the organization to maintain a proportional share of organization member benefit receipts and fund expenditures. Universal Basic Income is also called Unconditional Basic Income. UBI is not a native Web3 proposal. In high-welfare European and American countries such as Norway, the United States, and Germany, it has appeared many times in proposals related to national governance and national welfare. Usually it means that there are no conditions, no qualification restrictions, no qualification examination, no need to have a job, and every citizen or community member can receive a certain amount of currency on a regular basis. Simply put, UBI is an undifferentiated subsistence allowance issued to members of an organization.
• Solution: Proof of Person (PoP) mainly based on biometric identification technology. For example, Worldcoin requires an Orb iris test at an offline site to receive the Worldcoin Grant. This is also to prevent a real person from controlling multiple accounts to avoid repeated grant placement. Worldcoin claims to only store the irreversible hash value of the iris information rather than the iris photo itself to identify the uniqueness of the users identity (World ID), thus overcoming the privacy and security issues of traditional KYC.
• Related Solutions: Iris Verification by Worldcoin
summary
• Although the specific manifestations in different application scenarios are different, it is not difficult to see that the value goal of Anti-Witch can be attributed to a network security mechanism in which the maintenance cost of the project partys value goal is proportional to the personal benefits of the organization members , which at the presentation layer is mainly related to preventing users from applying for fake accounts in large numbers.
• If the project side cannot provide credible commitments and technical proof to community members in combating Sybil attacks, long-term Sybil attacks will damage the security and credibility of the project. Old users and potential new users may reduce their participation or completely avoid investing in the project, which may lead to a series of chain problems at the application layer such as the loss of miners, a decrease in the pledge rate, an overestimation of the number of real users, insufficient donation incentives, and excessive issuance of universal basic income. .
1.2 Protocol Consensus Layer: Why do some anti-witches receive a lot of praise from the community, while others cause a lot of dissatisfaction?
Although there is no cost to create a new wallet address and it seems that a Sybil attack is easy to occur, certain features that resist low-cost Sybil attacks already exist at the protocol consensus level. For example, the PoW mechanism requires each node to contribute computing power to the network to participate in consensus; the PoS mechanism allocates voting rights based on the number of tokens invested by the validator. Therefore, there is no way for users to increase their influence simply by creating new addresses. However, the basic consensus mechanism only increases the cost of Sybil attacks. When the benefits of Sybil attacks are much higher than the costs, malicious actors will still choose to launch attacks. Therefore, there are many innovations at the consensus mechanism level, such as Proof of Personality (PoP), Delegated Proof of Stake (DPoS), Proof of Authority (PoA), etc. Distributed protocols with inherent protection against Sybil attacks have also been developed, such as algorithms such as SumUp and DSybil, which will not be discussed in detail here.
In addition, the project side may also change the effectiveness of anti-Sybils through rules and measures that affect the ROI of Sybil attacks. Generally speaking, regardless of the application scenario, the community’s evaluation of anti-witch initiatives is usually related to the project’s fund pool size, token distribution formula and qualification conditions.
1.2.1 Capital pool size
Fund pool size, that is, the amount of funds a project can use for rewards and incentives. Because the size of the capital pool directly affects the possible returns for each participant. When the pool is larger, community members may be generally more optimistic, but at the same time the potential risk of a Sybil attack is greater.
For example, the OP’s second airdrop fund pool only accounts for 0.27% of the total token supply, which is a drop in the bucket compared to the 5% of the first airdrop. Because the fund pool is small, it has caused widespread controversy in the community.
1.2.2 Token distribution formula
The token distribution formula determines how participants are rewarded with tokens. This includes how each participant’s contribution is calculated, and the rules for allocating tokens based on these contributions. Transparent and fair distribution formulas are generally well received by the community because they ensure that everyone is fairly rewarded for their efforts. However, if the allocation formula is complex, opaque, or biased, it may lead to dissatisfaction and disputes among community members.
For example, the OP’s second airdrop allocation focuses on governance while taking into account active users who do not participate in governance. The method of returning GasFee makes airdrop farmers who do not participate in Optimism governance unprofitable in this airdrop. Most users did not gain very good profits in this round of airdrops, which is also the main reason why this round of airdrops did not produce a wealth effect. Most addresses only received airdrop incentives of less than 50 $OP, and only a small number of addresses received airdrop incentives of hundreds of $OP.
1.2.3 Qualification conditions
Eligibility criteria are the criteria that determine who is eligible to participate. These conditions may include completion of specific tasks, multiple interactions with the project, or even identity verification processes such as KYC. If qualifications are too strict or onerous, it may prevent some community members from participating, leading to dissatisfaction. On the other hand, if conditions are too lenient, they may not be effective in preventing abuse, thereby weakening the effectiveness of anti-witch measures.
For example, in order to obtain SEI air investment qualifications, users not only need to interact multiple times and complete five major tasks, but also need to fill out forms multiple times, and KYC is required to receive them. The complex process and the risk of exposing private information have caused community dissatisfaction.
1.3 Verification and detection layer: similarities, differences and comparison of the technical paths and advantages and disadvantages of the solutions
It is certainly a good idea to reduce the input-output ratio of Sybil attacks through the protocol consensus layer, but the anti-witch effect does not guarantee eradicating the roots, and it is difficult for the project side to conduct accurate judgment and verification at this layer. . Therefore, we also need some incentive mechanisms or technical solutions to verify and detect witch accounts, such as community detectives, identity credentials proof of personality (PoP), and on-chain behavioral activity analysis. It is worth noting that each identified historical witch address list will also be inherited by the new project party.
1.3.1 Community Detective
• Safe, HOP, CONNEXT, Optimism encourages community detectives to make witch reports, shifting the responsibility for anti-witch reporting to the entire community. Although the original intention is good, Report to earn is also a very novel way to motivate users, but this approach has caused controversy in the community. For example, CONNEXTs reported witch account even threatened to poison other wallets, which could put the communitys anti-witch efforts into flames.
• Advantages: Generally speaking, community detective intelligence is timely and private experts show their talents.
• Disadvantages: Poor accuracy, low reporting success rate, easy to miss witch accounts, or trigger revenge poisoning by witches.
1.3.2 Identity certificate proof of personality (Proof of Personhood)
There are many solutions in the direction of identity credentials personality proof, which usually involve several concepts of decentralized identities (DIDs), such as soul-bound tokens (SBT), verifiable certificates (VC) and POAP (Proof of Attendance Protocol), etc. .
Soulbound Tokens (SBT):
• SBT is a special type of non-fungible token (NFT) that represents a personal identity, attribute or achievement. Unlike ordinary NFTs, SBTs cannot be traded or transferred because they are tied to the soul (i.e., personal identity) of the holder. They are used in the digital world to express non-transferable attributes such as educational qualifications, employment history or reputation in the community.
• advantage:
○ Personalization and non-transferability: SBT is closely tied to an individual’s identity and cannot be transferred or traded, which increases its accuracy in representing an individual’s identity and qualifications.
○ Flexibility and scalability: Various types of SBT can be created as needed for different verification purposes.
• shortcoming:
○Privacy issues: SBT that is closely related to individuals may expose too much personal information.
○ Difficulties with revocation and changes: Once issued, SBTs may be difficult to revoke or amend, which may be a problem when the information needs to be updated.
2. Verifiable Credentials (VC)
• VCs are digital certificates that certify certain attributes or qualifications of the holder. These certificates can be issued by various institutions or individuals and can be used to verify identity, qualifications, membership, or any other verifiable information. The key feature of VCs is that they can be used in a decentralized environment without being dependent on a single issuing institution.
• advantage:
○ Better privacy control: VC allows holders to choose the information they want to share, enhancing privacy protection.
○ Wide applicability: VC can be used in a variety of scenarios, from identity verification to qualification certification.
○Easy to manage and update: Compared with SBT, VC is easier to update or revoke.
• shortcoming:
○ Centralization: The trustworthiness of VC is highly dependent on the reputation and reliability of the issuer.
3. POAP(Proof of Attendance Protocol)
• POAP is a digital collection system used to authenticate records of an individual’s participation or attendance at a specific event or activity. This concept is becoming increasingly popular in the cryptocurrency and blockchain communities, especially as a validation of participation in various virtual and real-world activities.
• advantage:
○ Uniqueness and non-tamperability: POAP, as a blockchain-based NFT, is unique and non-tamperable. This helps ensure that each POAP represents an authentic engagement event, reducing the possibility of forged or duplicate identities.
○ Verify participation: POAP can be used as a credential to verify a users participation in an activity. This approach is particularly useful in voting or other scenarios where real participants need to be verified.
○ Increased cost of attack: To successfully perform a Sybil attack, an attacker would need to obtain a large number of POAPs, which may involve actually participating in multiple events or finding other ways to obtain these POAPs. This increases the cost and complexity of executing an attack.
○ Transparency and Traceability: Because POAPs are recorded on the blockchain, their issuance and transfer are transparent and traceable, which helps identify and prevent malicious behavior.
• shortcoming:
○ High costs: On some blockchains, such as ETH, creating and transferring NFTs can require expensive transaction fees.
Other identity credential solutions: KYC, biometric identification, OP’s on-chain certification AttestationStation, etc.
1.3.3 Analysis of behavioral activities on the chain
AI-ML algorithms can resist sybil attacks by monitoring behavioral activity patterns on the chain. However, the difficulty of sybil detection with this type of technology stems from the lack of labels for real witch accounts, making it impossible to construct a suitable training set for supervised learning and Extrapolate to the test set to check the accuracy of the algorithms decisions. For example, the algorithm may not only miss some witch accounts, but may also misidentify a real person account as a witch account, causing the airdrop list to be biased and causing dissatisfaction among community members. Therefore, the current anti-witch AI-ML algorithm is mainly based on time series analysis and graph mining of on-chain data, such as analyzing batch transfers and interactions, behavioral sequence pattern mining, and asset transfer graphs, and then gradually accumulating them through manual verification. Real witch tags.
•Batch transfers and interactions:Detect witch accounts by analyzing transaction behavior between different addresses. This includes identifying batch transfers and interaction patterns that may indicate witch behavior.
• Behavior sequence pattern mining:Mining the data to find consistent patterns of behavior that may indicate a Sybil attack.
• Asset Transfer Graph (ATG):Use asset transfer graph mining to analyze asset flows between entities to help identify potential Sybil attacks.
For example, the Celestia airdrop adopted Trusta Labs’ anti-witch program, which locked witch accounts through two-stage on-chain behavioral analysis.
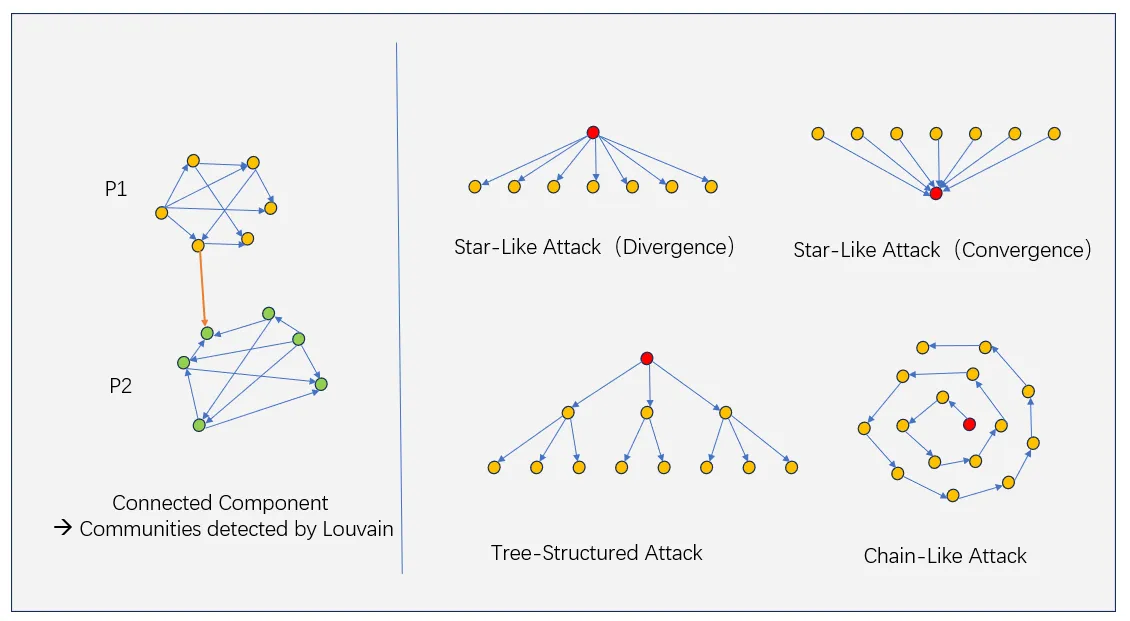
•Phase 1: Community detection on ATG.Analyze Asset Transfer Graphs (ATG) using community detection algorithms such as Louvain and K-Core to detect densely connected and suspicious sybil groups.
○ Star-shaped divergent attack:Addresses in the group receive transfers from the same source address;
○Star convergence attack:The address in the group sends funds to the same target address;
○ Tree attack:The fund transfer relationship within the group forms a tree topology;
○ Chain attack:Serialized transfers between addresses form a chain structure;
• Stage 2: K-Means optimization based on behavioral similarity.Calculate user profile and activity for each address. K-means optimizes clustering by filtering different addresses to reduce false positives in stage 1.
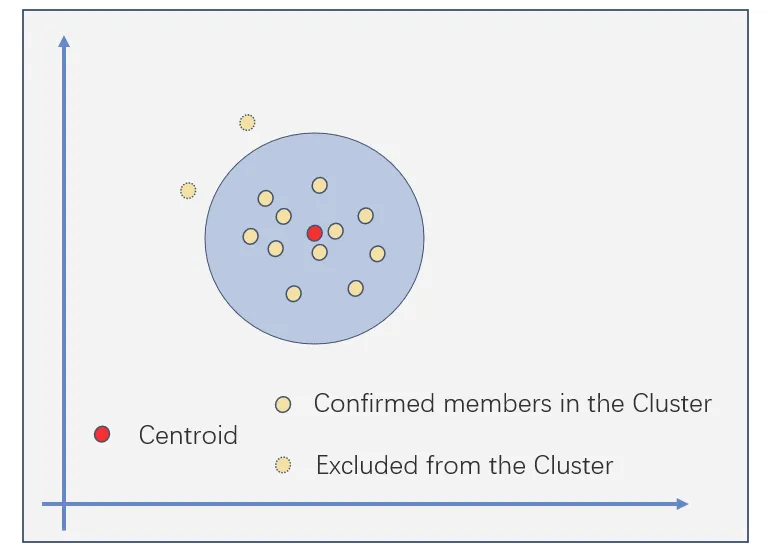
Image source:Introduction to the Trusta airdrop anti-witch framework: a reliability solution based on AI and machine learning
• advantage:
1 . AI-ML protects user privacy.The user does not need to provide personal biometric information and a series of identity authentication in Web2. Personality proof requires identity confirmation, sacrificing user anonymity.
2. AI-MLComprehensive analysis of large amounts of on-chain data to reduce vulnerabilities and make solutions morereliable. Identity verification can be exploited and forged, which makes personality proof schemes vulnerable to attacks.
3. AI-ML solutions essentiallyNo need for anyones permission, anyone can analyze the same publicly available data.
4. Due to the transparency of AI-ML analysis, witch detection can be publicly obtainedMulti-party verification。
• shortcoming:
1. The lack of real witch labels limits the complexity, accuracy and recall of the AI-ML algorithms that can be adopted.In 2022, there are no benchmark datasets that have been labeled as witches that can be used to train supervised models. When trained on static witch/non-witch data, the precision and recall of the model may be fragile. Since a single data set cannot cover all witch patterns, the recall rate is capped. Furthermore, misclassified users are unable to provide feedback, which hinders further improvements in accuracy.
2. The behavior of most witches is not significantly different from that of ordinary users, making it difficult to identify, currently the most appropriate detection method is the clustering algorithm. With the accumulation and confirmation of real witch labels, a more mature deep learning algorithm framework can be adopted in the future to optimize detection methods.
2. What new narratives extend from Anti-Witches?
Although the current anti-witch narrative sounds more like it is driven by the needs of the project side,"anti-user"Its characteristics make its rationality in terms of philosophical value questionable. But we have every reason to believe that it will expand on more solid ecological values in future narratives.
2.1 DeFi: Credit Score Credit Rating
One of the extended narrative directions is DeFi and credit lending. Previously, blockchain credit lending was almost blank. Due to the lack of an on-chain credit evaluation system, most loans now can only use the over-collateralization mechanism, which dissuades a large amount of liquidity that is unwilling to over-borrow. There is still a lot of room for new pledge rates, and the construction of the credit evaluation system needs to be based on the elimination of a large number of false accounts.
• Related projects:Gitcoin Passport、TrustaGo’s MEDIA Scorewait
2.2 SocialFi: social graph
Another growing narrative direction is SocialFi and social graphs. In content creation ecosystems based on social graphs and on-chain reputation (such as SocialFi and GameFi). Once social influence can be reasonably priced, Witches may make money by creating large numbers of fake accounts to manipulate reputation scores, comments, or social influence, much like trolls and bots on Web2 social media.
• Related projects: Social graph based on smart contractsLens ProtocolandCyberConnect, network-based social graphFarcasterandDeso, social trading protocolFriend.techEconomically related to content creatorsBodhi。
3. Outlook: What is the likely outcome of the game between “anti-witches” and “wool harvesting”?
• Expansion of application scenarios: on-chain credit social graph
The transition from “anti-user” project party needs to direct user needs.Although the current anti-witch narrative sounds more like it is driven by the needs of the project side,"anti-user"Its characteristics make its rationality at the level of philosophical value questionable, but we have every reason to believe that it is likely to expand to a more solid ecological value in future narratives.One of the extended narrative directions is DeFi and credit lending.Previously, blockchain credit lending was almost blank because we lacked an on-chain credit evaluation system. As a result, most loans now can only use the over-collateralization mechanism, and the construction of the credit evaluation system needs to be based on the elimination of false accounts. above.Another growing narrative direction is SocialFi and social graphs.In the content creation ecosystem based on social graph and on-chain reputation(e.g. SocialFi and GameFi). Once social influence can be reasonably priced, Sybil attacks may be able to achieve substantial profits by creating large numbers of fake accounts to manipulate reputation scores, comments, or social influence, much like trolls and bots that spam reviews on Web2 social media.Therefore, in DeFi, SocialFi and GameFi scenarios, we are likely to see application scenarios driven by user needs that extend from Anti-Witch.
• Diversification of address credit scoring system: integrated multiple detection solutions
Integrating multiple detection schemes to trade off privacy and accuracy.Binding identity credentials or providing biometric information can certainly more effectively distinguish between real people and fake accounts, and many more mature Web2 solutions can be used, but it is also accompanied by higher user information collection requirements. On the contrary, solutions based on AI-ML algorithms have the advantages of large-scale detection, multi-party verification, and privacy protection, but they also face the problem of being unable to intercept in advance or in real time. Therefore, integrating multiple detection solutions is a better solution.
•Users have a primary address and multiple secondary addresses, managed through the wallet
There is a trade-off between reputation binding and identity loss.In the future, perhaps every real user will have only one main address that can remember and identify an identity that can sustainably accumulate reputation (partially overlapping with the semantics of DIDs), and users can only receive incentive benefits provided by projects such as airdrops through the main address. However, TA can associate local addresses in multiple subdivision scenarios for interaction with application projects to prevent systemic risks arising from the loss or theft of the main address.
Conclusion
Through the above review, we can basically answer some of the questions raised in this article. First of all, Web3s anti-witch is an extension of Web2s anti-fraud and anti-cheating concepts, but it also has some native characteristics of Web3. For example, after the large-scale promotion of airdrop narratives, the revenue incentives for witch attacks have been significantly improved. Because of the distinct characteristics of the game between the project party and the wool party, the verification and detection measures of the witch hunt have also quickly changed from mild to severe and complex, and the technical methods are still being continuously upgraded. Secondly, although the current anti-witch narrative sounds more like it is driven by the needs of the project side,"anti-user"Its characteristics make its rationality at the level of philosophical value questionable, but we have every reason to believe that it is likely to expand more solid ecological value in the future narrative of Web3, and then complete user demand-driven value proof, such as DeFi credit lending. , SocialFi and GameFi’s social graph, and more. At present, the anti-witch technical solution is transitioning from the embryonic stage to the mature stage. The final form may be that users have one main address and multiple secondary addresses, managed through wallets; the main address is linked to a credit scoring system that integrates multiple detection solutions, and multiple This secondary address is used for interaction in vertical application scenarios and account retrieval verification.
Finally, I hope that when readers see a project’s narrative related to anti-witches and on-chain reputation in the future, they will be able to clearly understand which value scenario the “witches” they call are trying to use false identities to attack;Is the project team proposing a new protocol consensus to reduce the ROI of Sybil attacks from the source, or are they talking about access credentials or identities before the attack occurs, or are they talking about detection tools and methods after the attack occurs?Of course, related projects are likely to do more than one level.The game between anti-witches and wool-gathering will continue, but it is likely to be a positive-sum game rather than the commonly thought of zero-sum game.Specifically, the primary investment logic is roughly application value prospects > verification and detection technology > protocol consensus innovation.
References
[ 1 ] https://medium.com/@trustalabs.ai/trustas-ai-and-machine-learning-framework-for-robust-sybil-resistance-in-airdrops-ba17059ec5b7
[2] https://passport.gitcoin.co/
[3] https://docs.lens.xyz/docs
[4] https://cyberconnect.me/