Original - Odaily
Author - Nan Zhi

introduction
On October 20, Bitcoin Core core developer /dev/fd0 announced on the X platform,Will cease involvement in the development of the Lightning Network and its implementation, including coordinating the handling of protocol-level security issues。
/dev/fd0 means that each Bitcoin node has its own memory pool. Transactions are forwarded by peer nodes. If a Lightning Network node is used to open a channel and accept HTLC forwarding, it is vulnerable toReplacement cycle attack(Replacement Cycling Attacks)。
What is the replacement loop attack that the developer refers to and how it is implemented, Odaily will reveal in this article.
Lightning Network
The TPS of the Bitcoin network is only about 7, and the handling fees are high. To solve the needs of small payments, the Lightning Network came into being.
Lightning Network is a second-layer scaling solution for Bitcoin and other cryptocurrencies designed to solve the scalability and transaction speed issues of cryptocurrency networks.
Its implementation principle can be simplified as:
Transaction parties A and B established a transaction channel (actually a multi-signature wallet)
A and B recharge money A1 and B1 respectively (this step is on the chain)
Any transaction between A and B occurs off-chain, and A’s net transfer amount is
Update the transactions of A1-X and B1+X on the chain
Through the above process, no matter how many transactions A and B conduct off-chain, they only need to pay two on-chain fees, saving a lot of time.
Hash Time Lock Contract (HTLC)
The form introduced above is limited to direct transaction channels between A and B, and relay nodes appear for cross-channel payments.The relay node relays the transactions between the two to facilitate cross-channel payments., and the relay node can charge tips.
But this faces a problem:It is necessary to ensure that every participant in each channel is honest and trustworthy, is secure over multi-channel links.
Therefore, HTLC (Hash Time-Lock Contract, Hash Time Lock Contract) appeared. A payment transaction with HTLC can be simplified to:
A prepares a secret code R and calculates its hash value H
A sets a time limit T
A sends a payment transaction with HTLC to B. The transaction will be finally established only when the following two conditions are met.
B answers the secret code R (verified by H)
B’s answer time is within T (for example, the answer is given within 10 blocks)
If B does not know the password, or the answer times out, the funds will be returned to A
normal transaction process
Through the above HTLC, a payment process involving relay nodes is as follows:
The final recipient C provides the secret code to the sender A
A initiates an HTLC payment with hash value H (please note thatAt this time, the funds have not reached B’s hands)
B receives the payment information and initiates HTLC payment to C using the hash value H
In order to receive funds, C answers the code and receives the funds. B also knew the password at this time
B uses the secret code to obtain the payment initiated by A, receives the funds, and the transaction is completed.
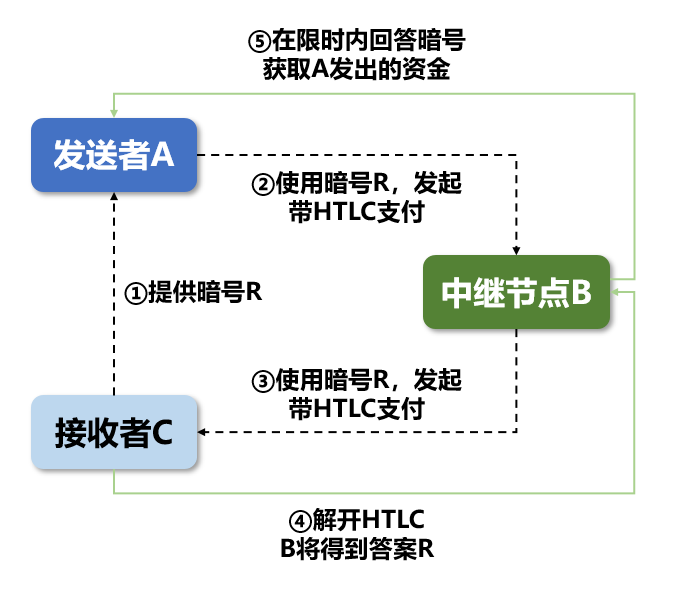
The process involving the three is as above. Several more relay nodes can also be added in the middle, while the payment mode remains unchanged. The payment is sent to the final recipient through the chain, and then the secret code is propagated back to the initial relay node. Finally, Seal the deal.
If the relay node does not receive the secret signal R for a long time,(I will not give the answer, the time limit is determined by the relay node itself), then the relay node can choose to close the channel,If successfully uploaded,Then the payment initiated by B will be invalid and there will be no loss of funds.
cycle substitution attack
Back to the basic principles of HTLC, in addition to answering the secret code, the relay node also needs to meet another condition the time for the relay node to answer is within T, and malicious attackers are targeting this point to attack:
A and C collude maliciously, and the victim is relay node B (B requires the next node to answer within 3 blocks)
A initiates payment to B (assuming the block height is 1000 at this time) and requires a response before block 1020
B initiates payment to C (block height 1005)
When the block height is 1008, B sees that C has not answered yet and decides to close the channel, which will take effect in block 1009.
C initiates a high-gas transaction ① (block 1008), preventing the transaction initiated by B from entering the memory pool.
C initiates a high-gas transaction ② (block 1009), but B still cannot enter the memory pool.
C operates in an infinite loop until block 1020, gives the password R, and withdraws funds.
Although B obtained the password, he no longer had time to respond to the payment initiated by A. The funds were returned to A, and the payment to C was established. Finally, the cyclic substitution attack was realized.. In addition, A and C can also achieve double spending by colluding and cyclically attacking Bs closed transaction.
Conclusion
Although the above attack paths exist, it does not mean that attackers can do whatever they want and steal funds in the Lightning Network. The author also proposed five solutions in the original article, such as local memory pool and transaction relay traffic monitoring, miner memory Pool monitoring etc.
The future is bright, but the road is tortuous. This year, a series of new things such as Ordinals, BRC-20, and Taproot Asset have been born on the Bitcoin network. Although problems exist, continued development will eventually solve them.
References
https://lists.linuxfoundation.org/pipermail/bitcoin-dev/2023-October/022032.html
https://github.com/ariard/mempool-research/blob/2023-10-replacement-paper/replacement-cycling.pdf