
more comprehensiveWeb3Cross-chain bridgeCross-chain bridgeUsed to transfer digital assets from one blockchain network to another in the form of wrapper tokens (one-to-one digital representations of tokens from another blockchain). They are needed because by default differentBlockchains are usually not interoperableimage description
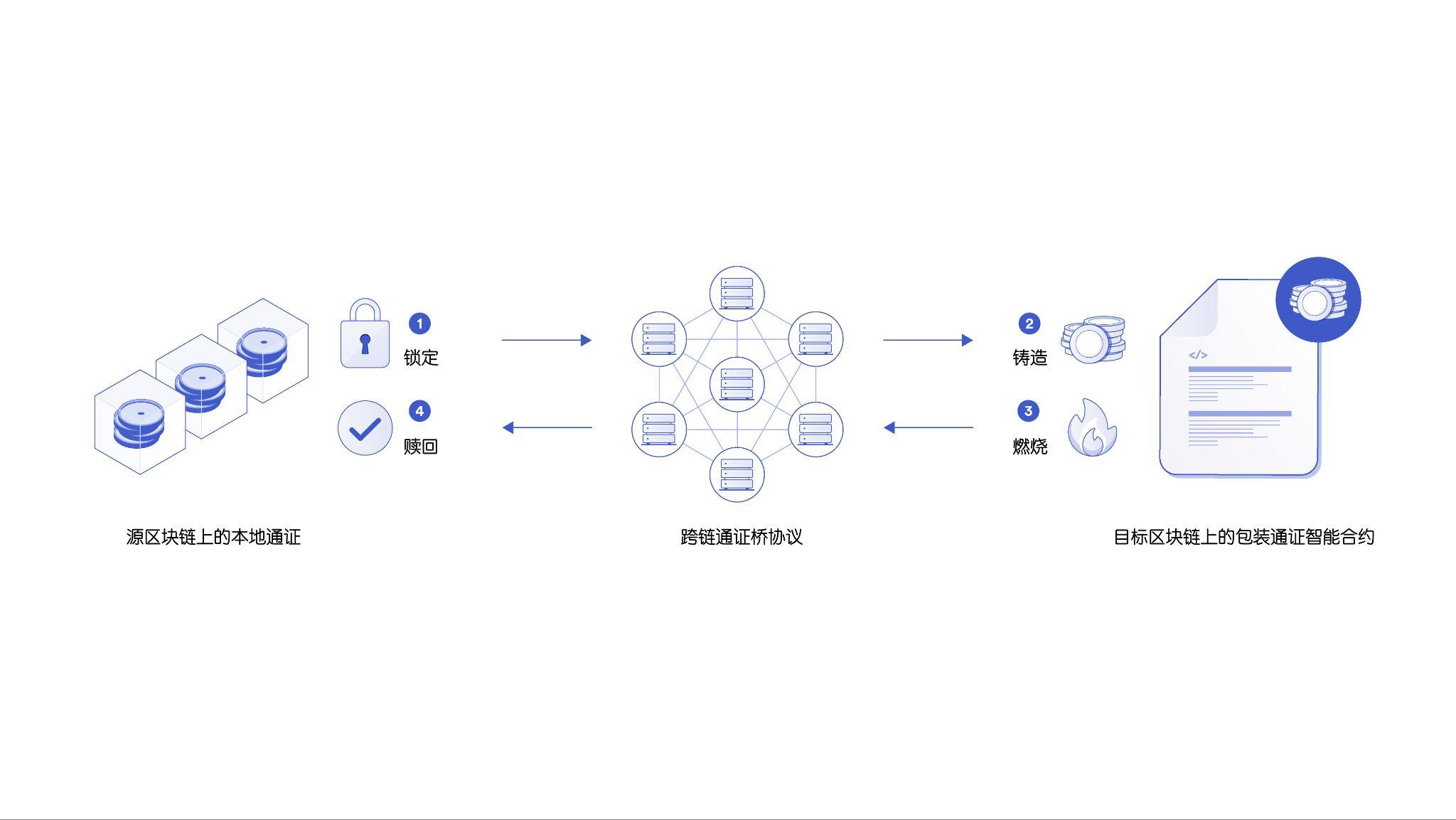
first level title
The complexity of cross-chain bridge security
image description

Although cross-chain bridges are an integral part of Web3, they have always been the target of bad actors
first level title
Vulnerability Exploitation and Attack Risk
secondary title
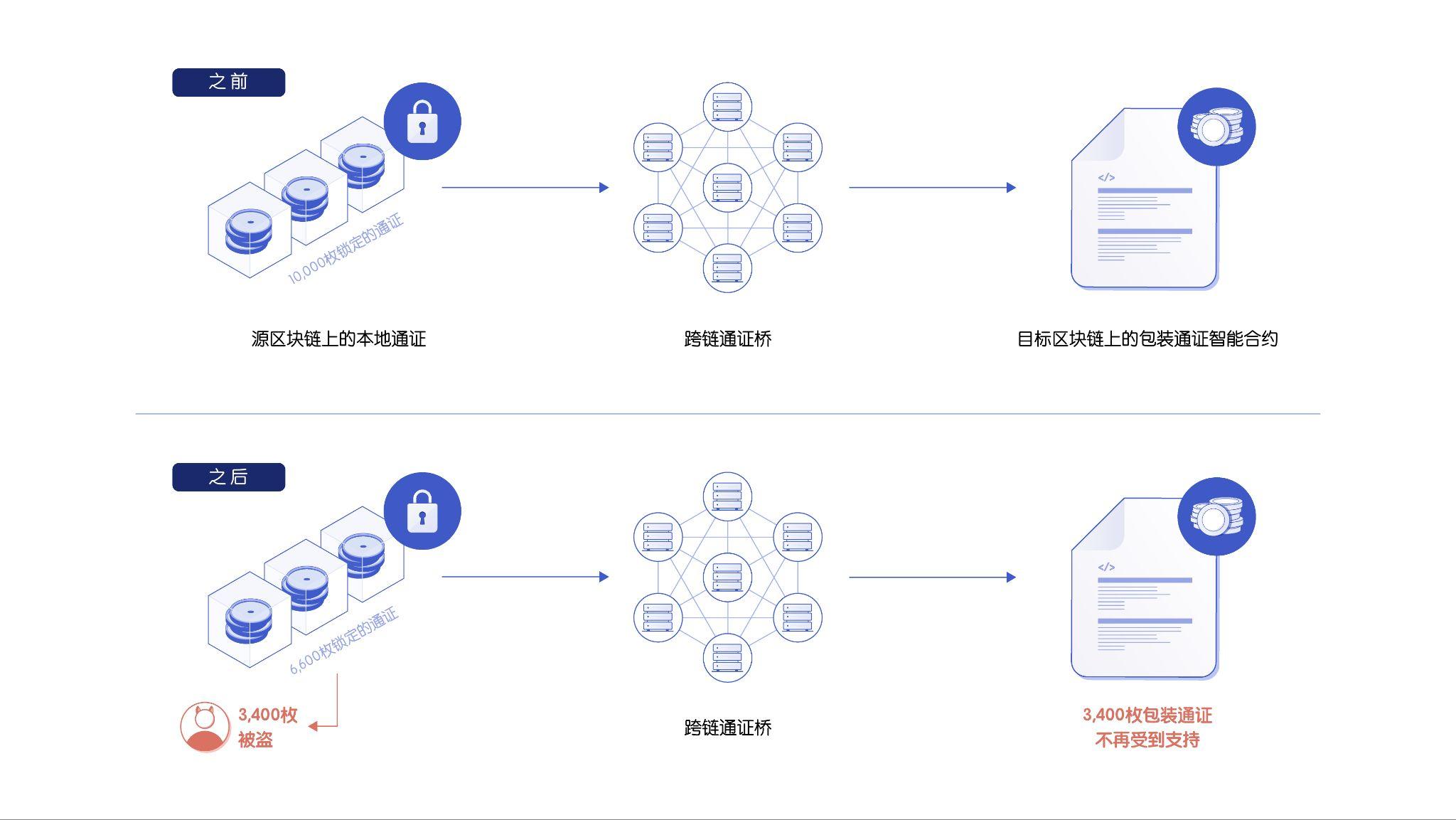
1. Collateral on the source chain is taken without proper ownership.
image description
secondary title
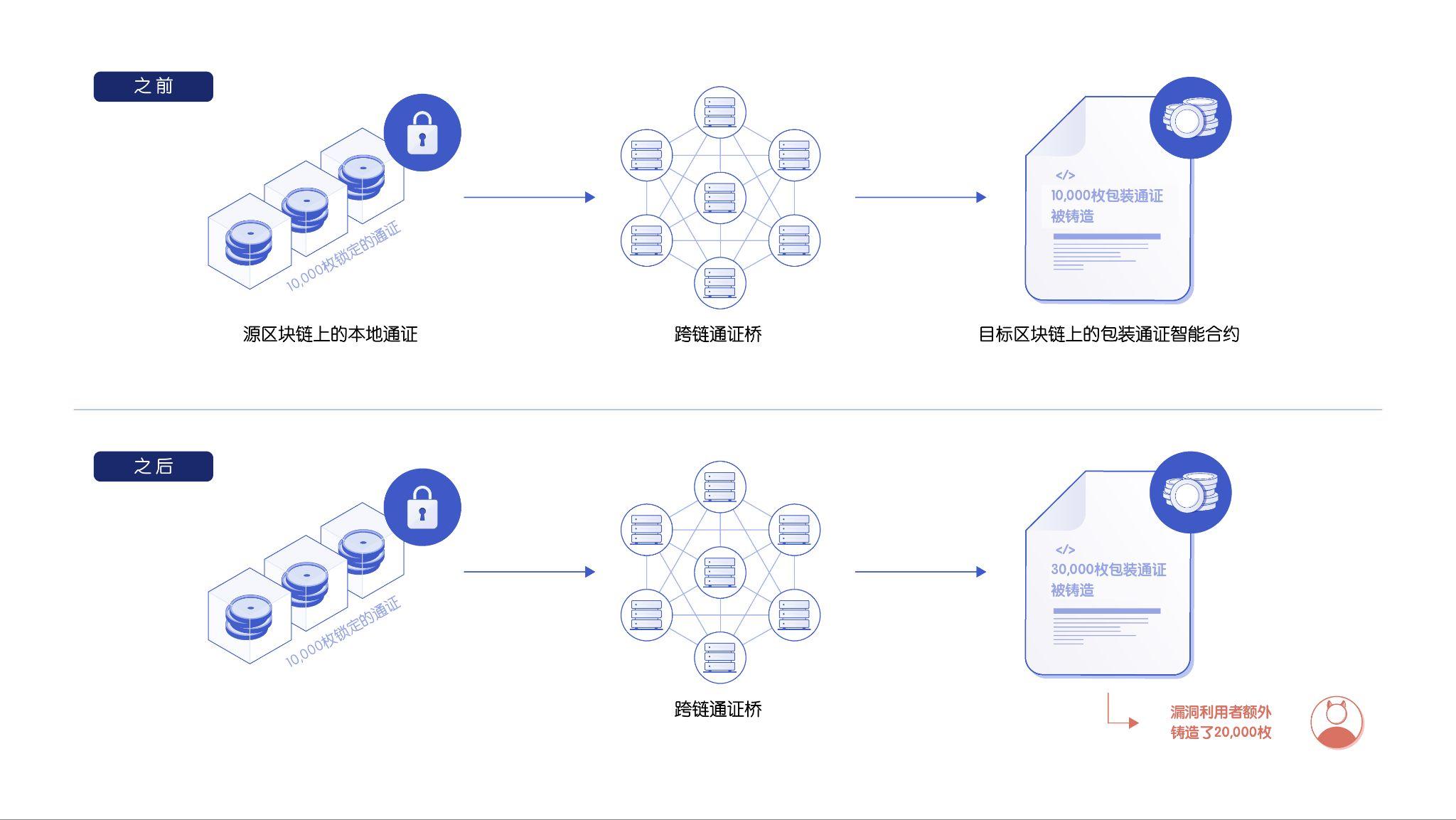
2. The cross-chain token on the target chain is minted without sufficient collateral.
image description
first level title
ecosystem risk
Once the cross-chain token bridge is compromised, it will not only bring direct risks to users who use the cross-chain bridge, but also bring risks to all projects that directly integrate and support packaging tokens. Wrapper tokens are usually inDeFiprotocol, a single exploit or hack can have a significant impact on operations, sometimes even causing the protocol to go bankrupt.
image description
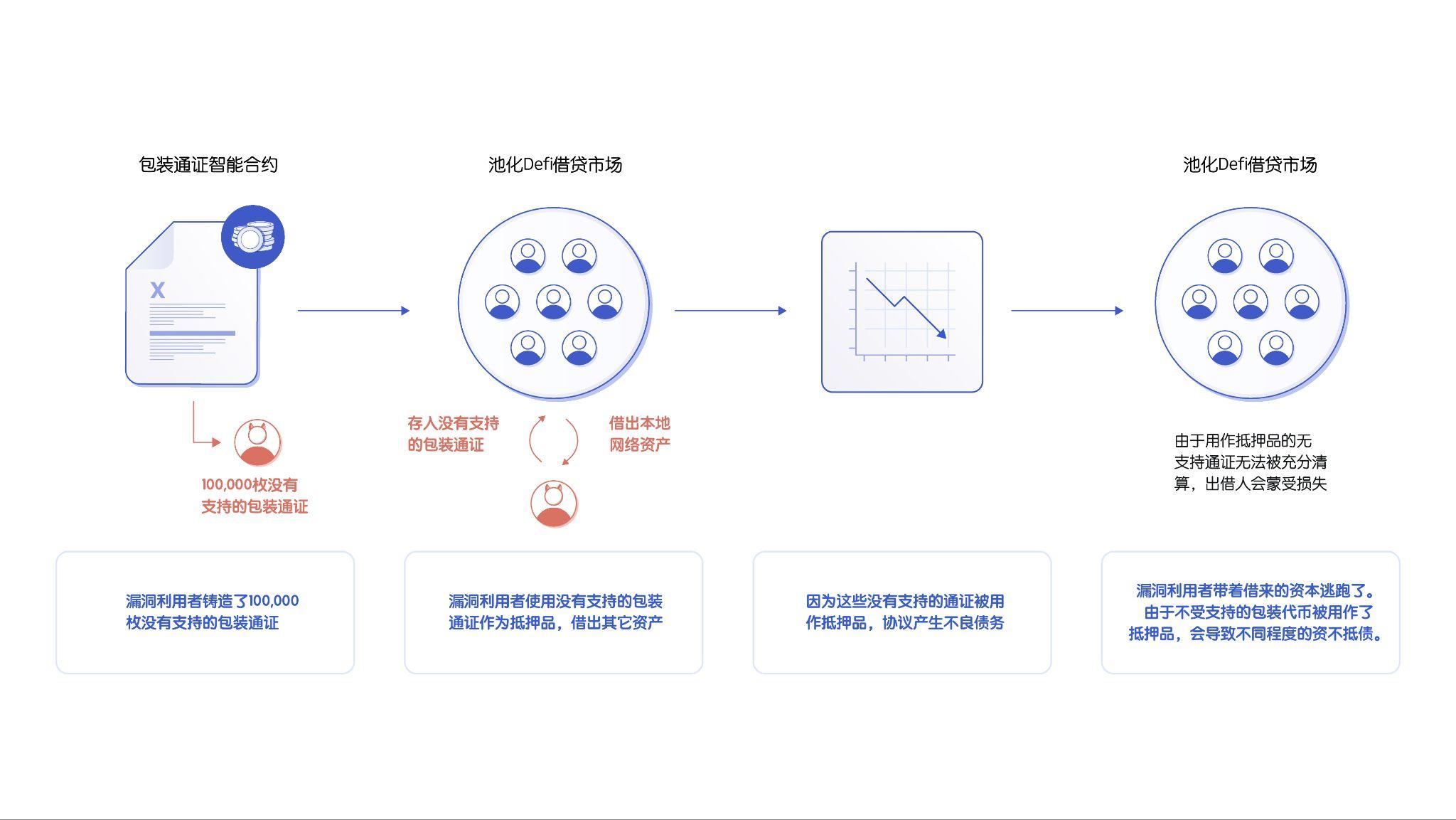
How Bad Guys Are Using 'Infinite Minting' to Attack the Pooled DeFi Lending Market
first level title
How to Improve the Transparency and Security of Wrapped Tokens Using Chainlink Proof-of-Reserve (PoR)
OracleOracleimage description
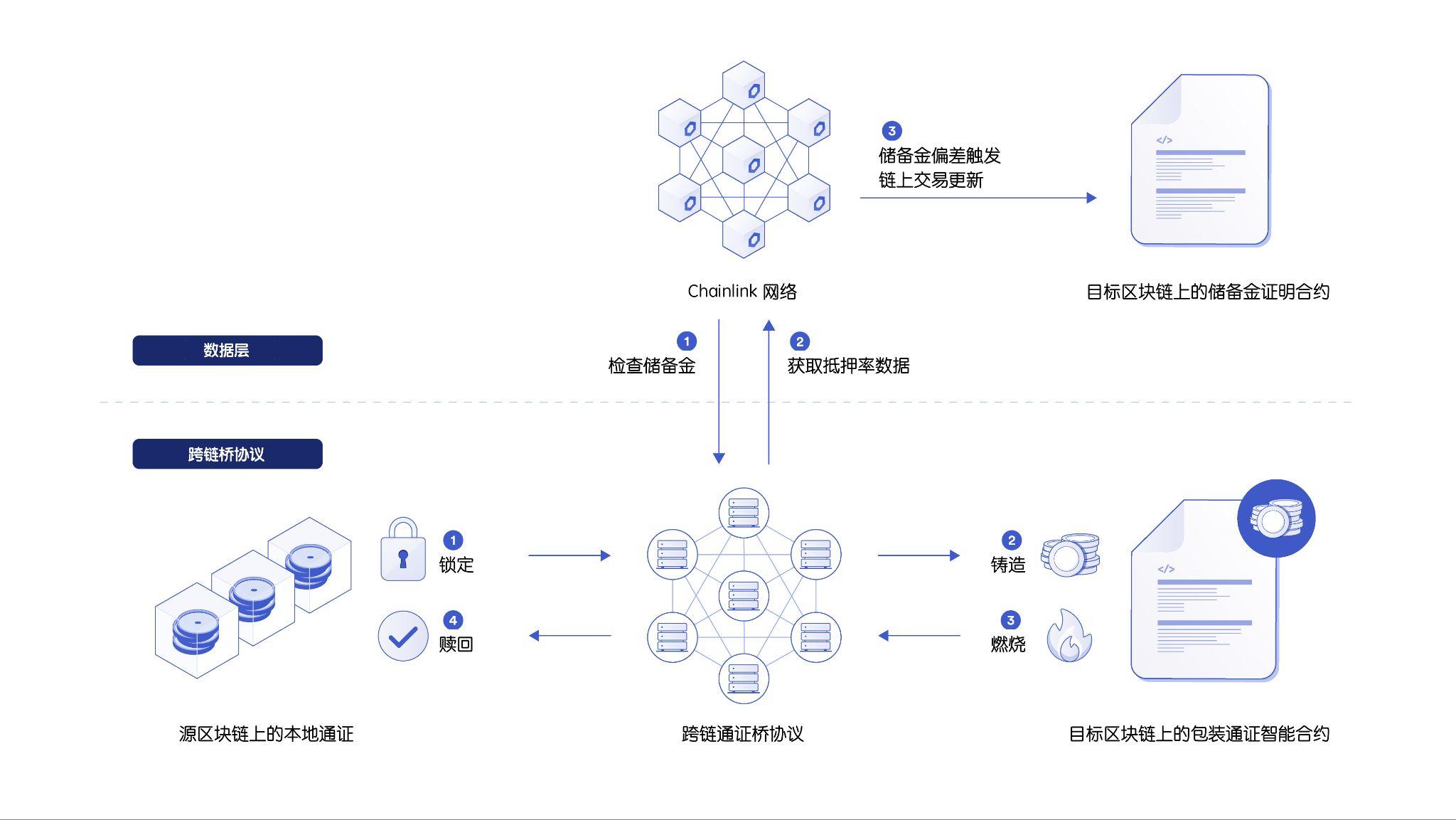
Chainlink Proof-of-Reserve (PoR) is the data layer for cross-chain bridges, enabling any user to independently verify the collateral balance on the target chain
Note: Chainlink PoR increases the transparency of the reserves backing wrapped tokens and can be used to provide additional safeguards, but does not prevent cross-chain bridges from being drained due to attacks. Precisely, cross-chain bridges and dApps can use PoR to help mitigate the impact of such events.
There are 3 main benefits of using Chainlink Proof of Reserve (PoR) to back wrapped tokens.
1. Guarantee smart contract functions
A robust and decentralized source of reserve data gives cross-chain bridge developers the tools to build automated failsafes that suspend the minting, redemption, and burning of wrapped tokens. For example, one way to prevent infinite minting attacks is to use the Chainlink Proof-of-Reserve (PoR) data source to check whether there is an equal or greater reserve backing the wrapped token. If not, the additionally minted wrapper tokens will be revoked.
Thanks to the Chainlink Proof of Reserve (PoR)On-chain reserve dataCan serve as a key security in case the cross-chain bridge is hacked or exploited, therefore, even in exceptional circumstances, the data source must be safe, reliable and accurate.
By utilizing the provennode operatorimage description
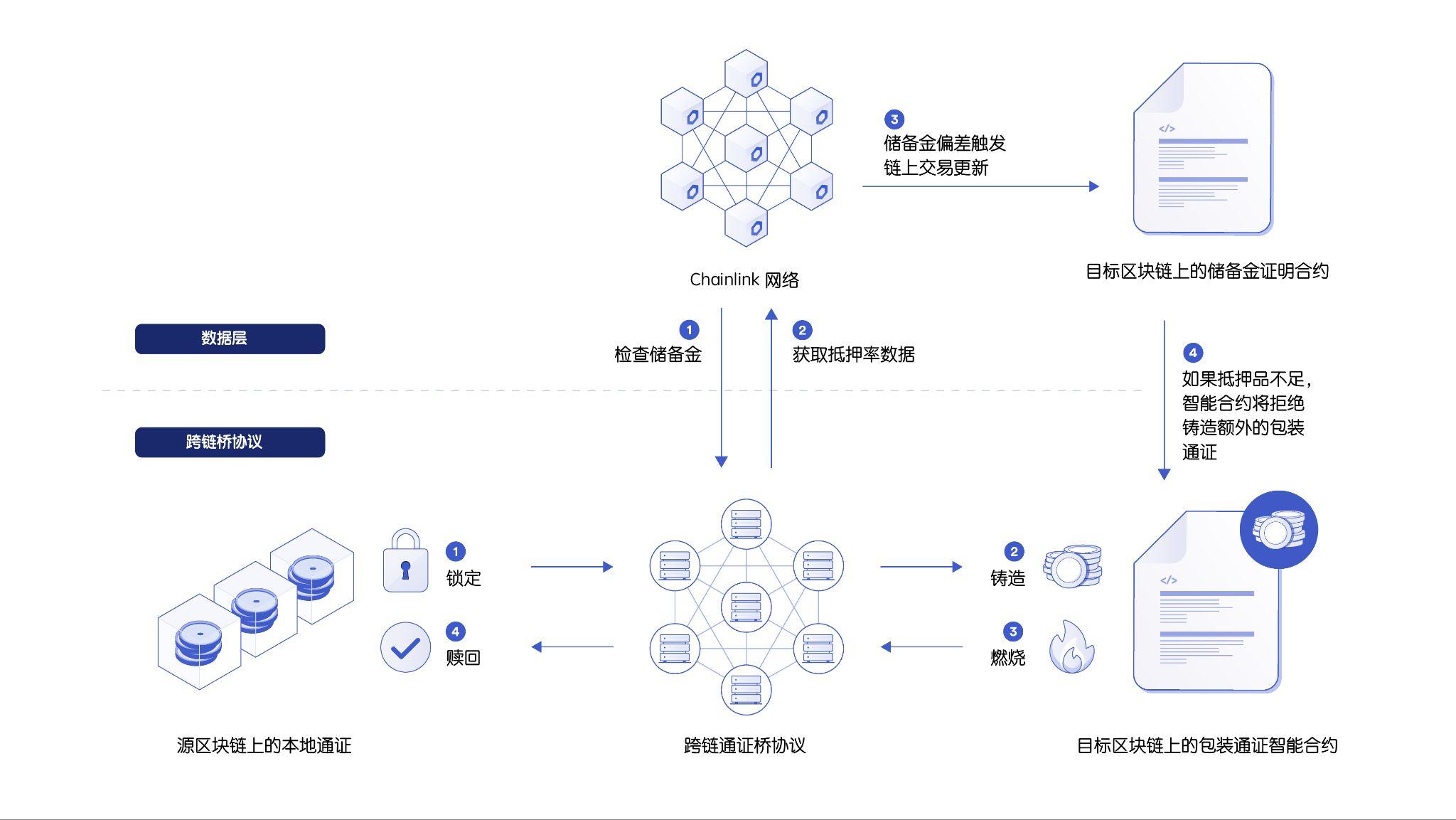
secondary title
2. Enable automatic DeFi responses
Strong on-chain Proof-of-Reserve for wrapped tokens via Chainlink PoR enables DeFi developers to build protections against potential cross-chain bridge attacks or exploits, which helps mitigate the risk of contagion in the event of a DeFi crisis. As more and more DeFi protocols implement these fail-safe measures, the resilience and anti-reflection of the ecosystem will increase.
For example, DeFi lending protocols can add a circuit breaker protection mechanism to automatically suspend lending pools using wrapped assets as collateral by reading data from Chainlink PoR data sources. If it is found that sufficient reserves are not locked up on the source blockchain, DeFi lending protocols can automatically cease operations to mitigate the severity of the incident.
A good proof-of-reserve solution for wrapping token assets can make it easier for DeFi developers to leverage data to deal with this situation. In order to lower the barriers to operation, the reserve data source should be easy to implement, use a standardized solution, and be published on the local chain.
As the industry-standard oracle solution for DeFi protocols, Chainlink Proof-of-Reserve (PoR) has delivered more than5 billion data points, making DeFi developersjust three stepsimage description
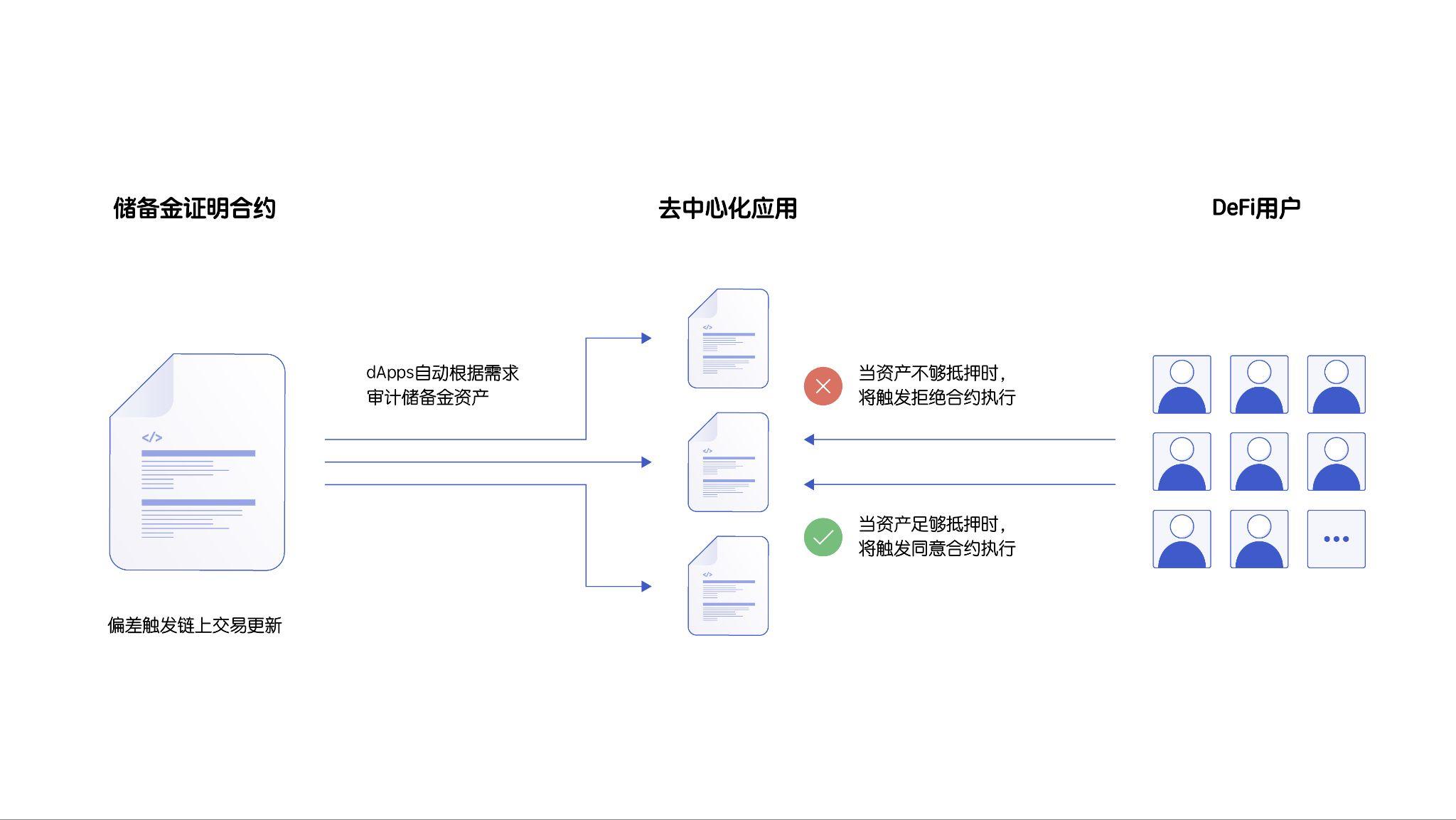
secondary title
3. Provide users with transparency of cross-chain collateral
Automated data delivery across chain reserves enables users to seamlessly verify collateral backing wrapped tokens and make informed decisions quickly during unusual events - a key competitive advantage for wrapped asset issuers, all of whom Hope more users use packaged assets. Without Proof-of-Reserve, it is difficult for users to verify on-chain that the wrapped asset corresponds one-to-one with the asset on the source blockchain.
A key consideration is that exploits or hacks can happen at any time. Reserve data feeds should be designed to be updated on-chain in near real-time to provide users with maximum transparency across chain bridges when most needed.
image description
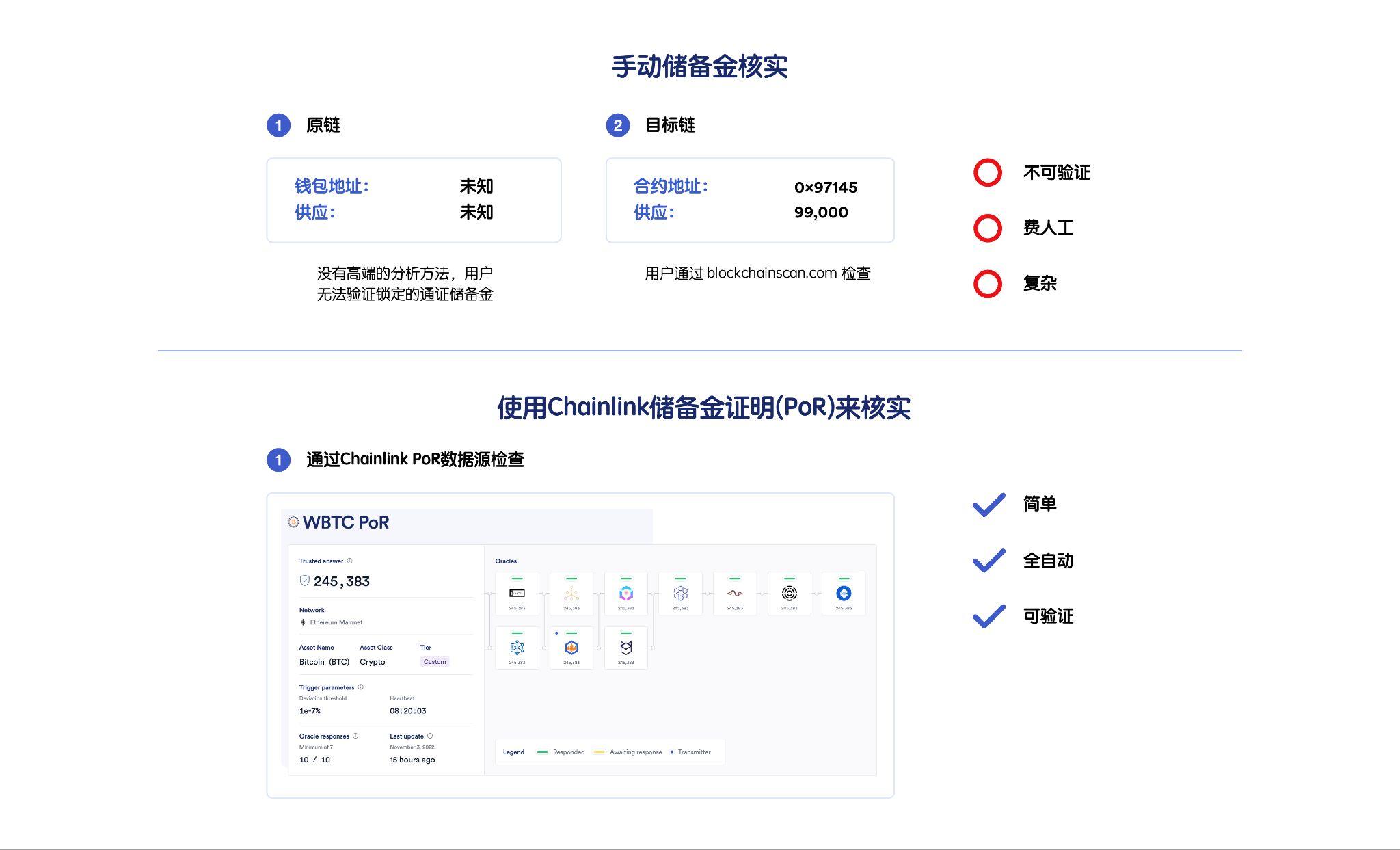
in conclusion
in conclusion
The introduction of reserve data into the blockchain provides vital protection for cross-chain token bridges. It could enable anyone to independently verify the collateral of wrapped tokens, enabling projects to integrate automatic defenses in the event of hacks or exploits.
To learn more about how Chainlink can be used to help secure wrapped token assets or DeFi protocols, please visitcontact our experts。