Original source:Hash Hunter
Original source:

Original Author: Masterdai
Whoever controls the past controls the future; whoever controls the present controls the past. — "1984"
In 2007, Katsuyama, a trader at the Royal Bank of Canada, discovered something that puzzled him. When he pressed the buy button on the trading terminal, all the orders disappeared.
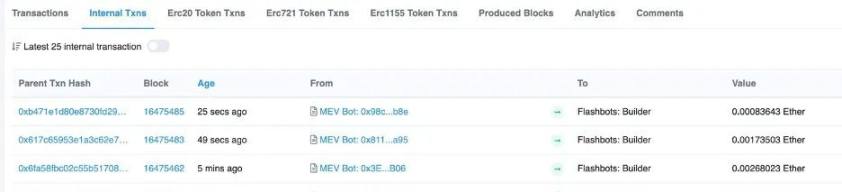
And a similar thing happened in the blockchain world. In June 2022, Scott Bigelow deployed an encrypted contract on the Ethereum mainnet and deposited 0.035 ETH in it. Only he knew the password to withdraw the deposit in the contract. And the moment he sent the password information to the contract, the ether currency in the contract disappeared.
There is no doubt that they all encountered early runners. The orders that Shengshan wants to place are distributed in different exchanges. Due to the geographical location, the time for each order to reach the exchange is slightly different. High-frequency traders know in advance through the faster optical fiber network A buy order, so as to buy out the order before Shengshan's order is placed on other exchanges.
Although Scott's password information is only known to him, before his transaction information is broadcast by each node, it is sniffed by the front-runner in the memory pool, and his password is copied to pre-empt with a higher Gas fee Steal the money from the contract. These pre-emptive bots are just the tip of the iceberg of what these "predators" are doing. Different from the high-frequency trading of traditional finance, in the dark forest of the blockchain, which has no access mechanism, more sophisticated and cruel strategies have emerged, and are widely used in various fields of DeFi and NFT.
This article will demonstrate the roles played by MEV robots and Flashbots from the perspective of the underlying principles of Ethereum; the impact of the PBS architecture on the subsequent encryption ecosystem and the evolution prediction of each role in the future. Divided into three chapters:
The first chapter is the interpretation of the principle.
The third section is the prediction and prospect of the future builder-proposer separation architecture.
first level title
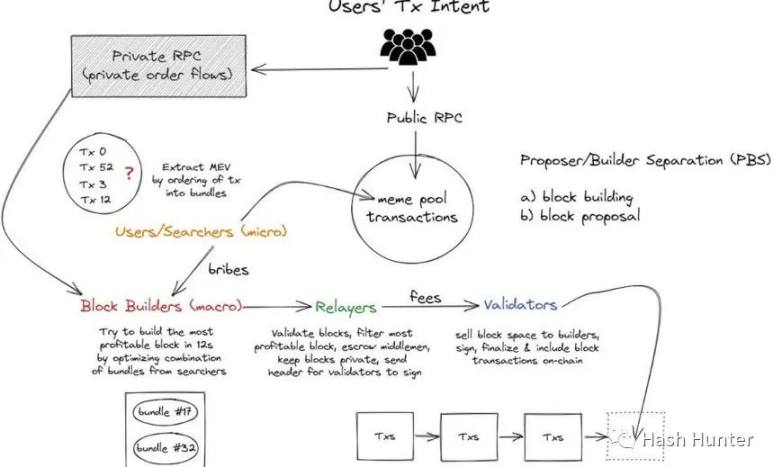
1. Industrial chain
To fully understand the current PBS ecosystem (proposer-builder separation), we can look at it from the perspective of sending a stroke from the user side: "When a user presses the button to interact with the decentralized application, then What exactly happened in this process until it was fully established on the consensus layer?”
In order to facilitate understanding, I split these links into several steps:
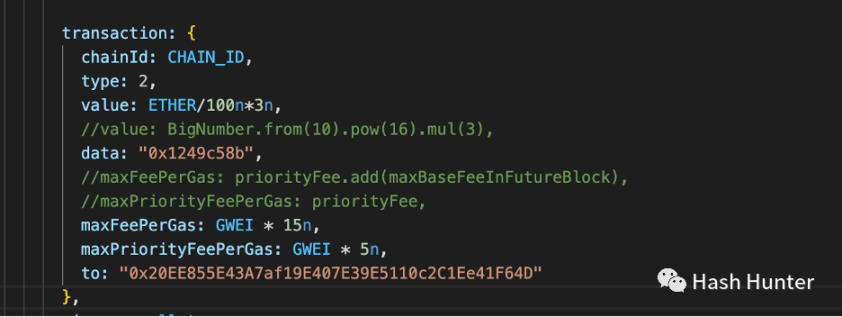
User transaction: When we transfer money in the wallet or exchange tokens in a decentralized exchange or a Mint NFT, the data structure on the chain is similar.
As shown in the figure above, it is the information needed to Mint an NFT contract, and the most important information is data. In the data in the figure above, 0x 1249 c 58 b is the call to the mint() function. And if we replace the data in data with 0x, then it represents an ordinary transfer. Through these data and value data, we can clearly judge the user's intention and function of this transaction.

Memory pool (mempool): When users use public nodes to remotely call services (for example, Metamask uses Infura's Ethereum node to call services by default), transactions will run into the memory pool. The memory pool is a buffer where the node receives the transaction and includes it into the block. Its function is to help the node check various transactions and judge the legitimacy and validity of the output and signature of the transaction.
The transactions in the memory pool are different for each node, but for the entire blockchain network, the data it contains is public. In other words, as long as someone can set up nodes on cloud servers around the world, he can obtain most of the mempool data. The abuse of memory pool data is extremely unfriendly to ordinary users. As in the case I described at the beginning, arbitrageurs can profit by knowing the user's trading intentions in advance. We call this profit-making process MEV (Maximum Extractable Value).
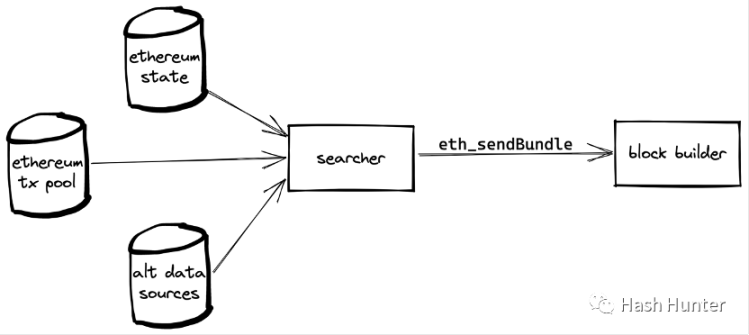
Seacher: Also known as an Ethereum robot operator, the arbitrageurs and nft-mint robots we know so far can all be classified into the category of searchers. Searchers are closely related to Flashbots. After Flashbots open-sourced their auction components, searchers can splice their own transactions or mempool transactions in sequence by sending bundles, and designate a certain block builder to let They include the transactions in this bundle in the block so that their transactions are not sniffed in the public mempool.
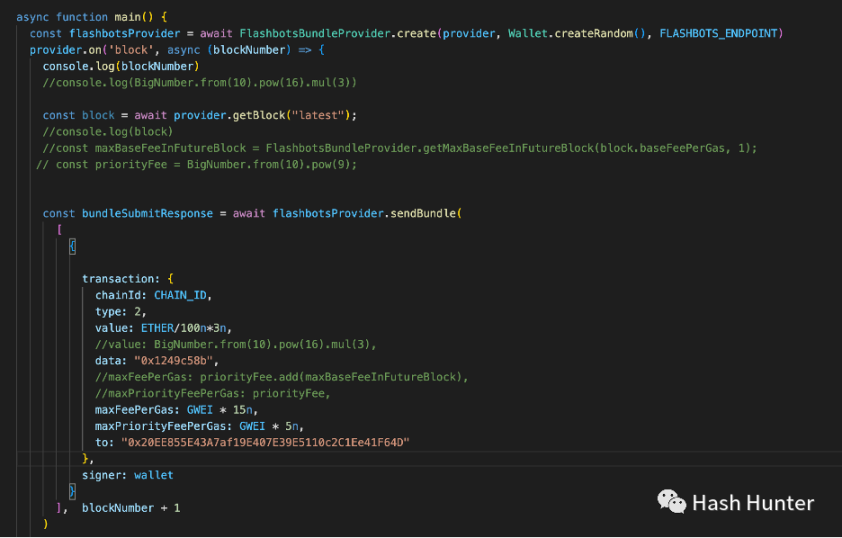
Flashbots actually created a new transaction information channel, which enabled some users to communicate directly with block builders. For example, in the example below, I use Flashbots to pass the mint transaction content in the above picture directly to the block builder, thus avoiding my mint information from being known in advance.
Searchers also need to pay a certain price to make their bundle more attractive. For example, by increasing the gas fee, or directly transferring the ether to the builder's Coinbase address.
Through the mechanism of bundles, searchers have the ability to change the order of transactions in a small range. And from the mechanism, it can ensure that the transactions in the order are not likely to be queued. By arranging and combining external transactions and self-generated contract call transactions, various attack strategies in the MEV field are formed. Examples include frontrunners, backrunners, sandwich attacks, JIT bots, time thieves and uncle block thieves to name a few.
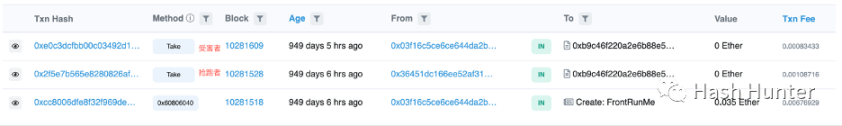
Frontrunning: Gain profits by getting ahead and copying your opponent's trading strategies. For example, preempting Mint to NFT with a higher Gas fee in front of ordinary users, seizing the Mint share of human users, and so on.
Backrunning: Gain profits by scrambling for the follow-up position of a certain transaction. After the robot creates new trading pairs on Uniswap by monitoring certain tokens, it creates a large number of buy transactions after it deploys the pool. The strategy is to be the first to buy tokens. In the same way, the robot can also become the first mint NFT person by monitoring the transaction in which the NFT project party activates the NFT contract mint(). Most of the existing NFT grab mint robots on the market follow this principle and architecture to design.
Sandwich attack: When a user wants to exchange token a in a decentralized exchange, the bot can create two transactions and use the bundle function to sandwich the victim's transaction between them. The robot's first transaction buys token a, the victim's transaction then pushes up the price of token a, and the third transaction sells the same amount of token a to make a profit. The profit depends on the slippage set by the victim exchange.
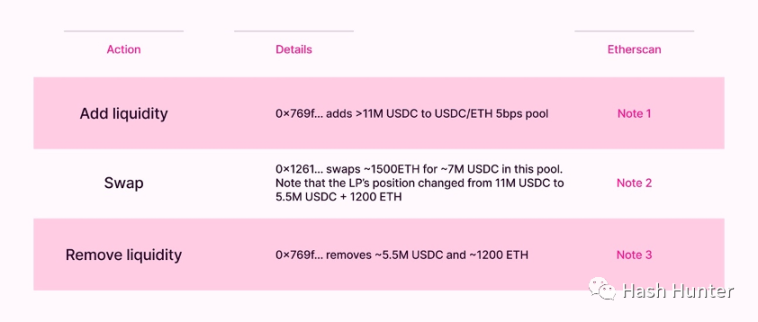
JIT robot (Just In Time): This mode appears in the token pool of Uniswap V3. Because of the centralized liquidity characteristics of V3 itself, users can set up an LP within a very small range. When a user wants to trade a large amount of tokens in V3, he immediately initiates a transaction to add liquidity and a transaction to destroy liquidity. The user's transaction is included in it, so as to obtain the liquidity income generated by this transaction. This mode requires the JIT robot to calculate the position changes before and after the transaction in advance, so that the user's transaction just falls within its designed liquidity range.
Due to the limited space, I will not introduce the detailed attack methods and steps in this article. Interested readers can visit here (https://www.mev.wiki/attack-examples). Not all searchers are arbitrageurs. We can also use these mechanisms to do good things.
Transfer service: Some hackers will use the NFT in the user's stolen wallet to carry out phishing. Usually, the ETH in this wallet is not enough to pay the gas fee for the transfer. When the victim wants to transfer into Gas for transfer, the hacker will use the script to transfer the Gas fee away. We can use Flashbots to get back the NFT in the wallet where the private key was stolen before the hacker takes away the Gas fee you transferred. Create a transaction into the hacked wallet, create a transaction out of the compromised wallet, put these two transactions in a bundle and send it to the block builder. Since these two transactions are consecutive on the block, the hacker has no way to prevent you from transferring the stolen NFT. When a searcher finishes building a bundle, he can send the bundle to his assigned block builder.

Block builder: Thanks to Flashbots open-sourcing the block building architecture in November 2022, we can know the internal architecture design of the block builder. A complete block building client consists of two different nodes, including a block building specification geth execution layer node program, and a modified prysm consensus layer node.

Block builders need to expose an RPC endpoint that enables searchers to send bundles to specified builders. The builder itself is divided into two modules: the miner (geth) and the construction (prysm). The miner module selects the bundle that meets its program requirements through an algorithm program and selects transactions from the memory pool and inserts them into the created blocks. middle. The builder module starts to generate block data while continuously communicating with the repeater and miner modules, including the hash value of the block, payment address and additional information (usually the builder will write his name inside) . And set up a transaction to send the proceeds of the entire block to the receiving address of the verification node in the form of transfer.
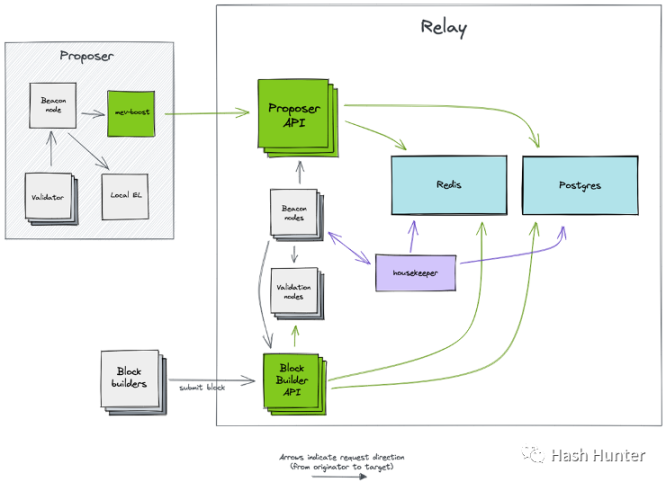
Relay: The block builder needs a trusted third party to send the block it sends to the verifier without being leaked. The same verifier also needs a trusted relay layer to help it Ensure the legitimacy of the block. Of course, different repeaters have different characteristics and characteristics. A validator uses MEV-Boost to access multiple repeaters to obtain the most block selection rights.
From the above architecture, we can find that repeaters also need to run consensus layer nodes and execution layer nodes to accept and send block information. There are two APIs on the outside of the repeater to connect to the block builder and MEV-Boost respectively. Such an architecture can minimize the cost of communication and trust between proposers and builders while ensuring that block information is not leaked.
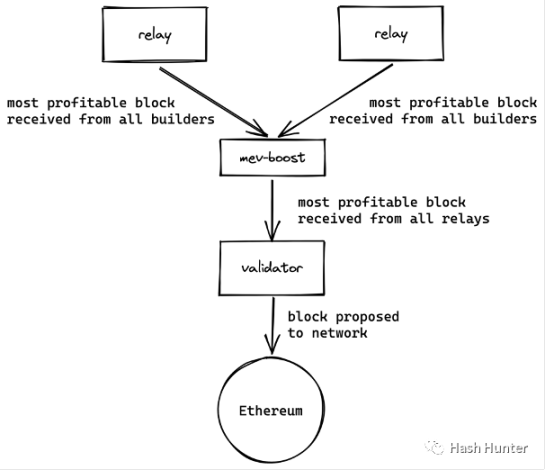
Proposer: After the Ethereum merge, new consensus layers were added to the network. The proposer's architecture consists of four clients: execution layer nodes, consensus layer nodes, validators (32 ETH), MEV-Boost. This is also the underlying architecture of most Ethereum node pledgers. The original node pledger is composed of the first three software, and MEV-Boost can be understood as a plug-in to coordinate the communication between two nodes and obtain additional block information from the relay layer.
Such an architecture actually strips the ability of the original proposer to build blocks, so that the proposer only needs to propose blocks from MEV-Boost and add them to the beacon chain. Likewise, MEV-Boost can connect multiple relay layers to maximize the benefit of the proposer. In the end, the income generated by the searcher and the block is paid to the proposer, that is, the Ethereum pledger, through this entire structure.
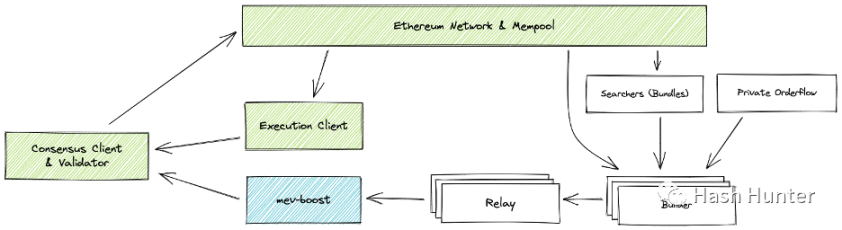
Transaction chain:
When a user initiates a transaction, it will first enter the public memory pool. If it is an ordinary transaction, it will be put into the block created by the block builder after waiting for a period of time. A transaction targeted by a searcher will enter the block in the form of a bundle. After passing through the relay layer, it is finally signed by the block proposer and broadcast to the network. Users can also use block builders' private nodes, thereby avoiding the public mempool.
Benefit chain: The searcher looks for a transaction that can capture benefits in the memory pool, salvages this transaction and combines it with the transaction created by itself and puts it into a bundle. The profit obtained by the searcher will go directly into its wallet, and in order for this transaction to be packaged into the block by the block builder, the searcher needs to pay a transaction fee to the block builder (via Gas or Coinbase Transfer) .
Block Builder's Profit = Transaction Fee (Gas) + Searcher Pays Fee - Burned Gas Fee
Block builder's profit = transaction fee (Gas) + searcher payment fee - gas fee for destruction - block builder's fee to validators (cost)
Mev-Boost reward = last transfer in block = fee (cost) from block builder to validator
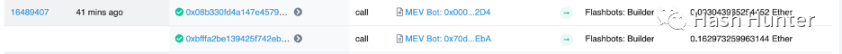
Let's take block 16489407 as an example. Etherscan shows that his overall block reward is 0.129830707718222266 Ether. This is not his actual block construction profit, but just the transaction fee - the gas fee for burning. The record of coinbase.transfer can be queried from the address of Flashbots, and it can be seen that the searcher has paid two transaction fees totaling 0.16601722521 Ether. Of course, there are actually 6 bundles in this block, but the remaining 4 bundles are paid in the form of Gas fees. The space is limited and the author will not go into details here. I will write an article in the future to introduce in detail how to calculate the MEV income of a block.
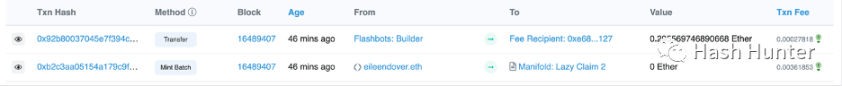
In the last transfer of this block, the builder gave the verifier a transfer of 0.295569746890668 Ether.
By calculation:
Block Builder Earnings = 0.129830707718222266 + 0.16601722521 = 0.29584793292 Ether
Block builder profit = 0.29584793292 - 0.295569746890668 = 0.00027818602 Ether
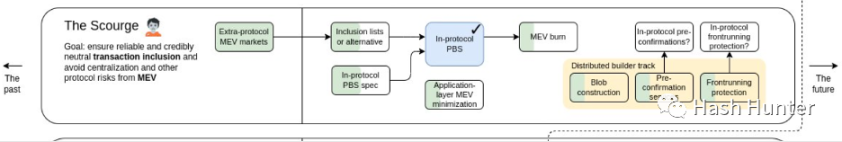
From the point of view of the overall technical architecture and links, the existing PBS architecture design is not simple. PBS itself is also Ethereum's transition before The Scourge phase. There is currently no complete solution to the collusion between the relay layer and the construction layer and the centralization of block builders. This is one of the main reasons why Flashbots later launched Suave.
first level title
2. Ecological pattern and investment opportunities
In the previous chapter, the MEV chains were classified and sorted through the implementation of the underlying architecture. Project parties in the ecology often occupy multiple fields and directions to achieve profitability and creation. Of course, this field is still in a very early stage, and there are currently no very clear business models and top players on the track. For judging these early projects, the author roughly divides several tracks (not involving node pledgers), and measures them from three aspects: whether they can make profits from them, whether they have the conditions for large-scale commercialization, and whether they are sustainable .
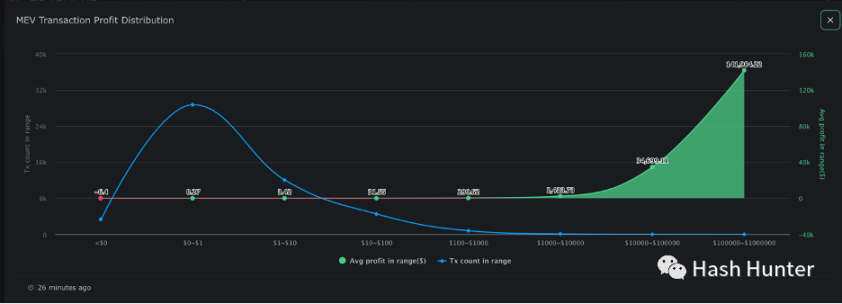
Searchers: According to their functions and sources of profit, they are also divided into arbitrageurs, sandwich attackers, and liquidators. Its profitable areas cover decentralized transactions, lending, NFT transactions, flash loans, and more. From the data provided by EigenPhi, we can see that the income distribution of searchers themselves is extremely unequal.
The vast majority of arbitrage profits are concentrated at the position of $0.27, and only a very small number of arbitrage profits can exceed $1,000. At the same time, searchers also face the risk of being trapped by peers and being reversed arbitrage (Salmonella tokens). Nathan Worsley said in his speech on MEV Day: “This field requires very top talents to cooperate with the team, 20 small teams occupy most of the market share, the strategy of arbitrage becomes more and more complex and the competition is very fierce. "
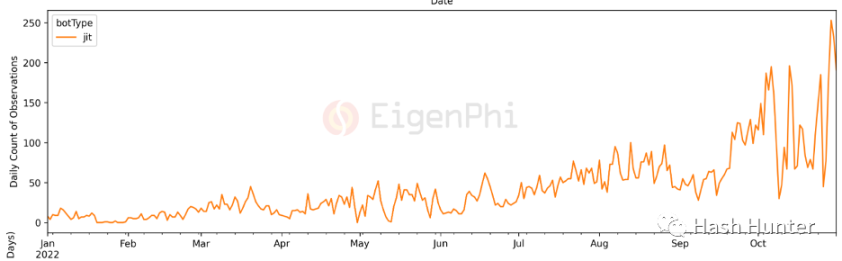
A large part of the reason for the fierce competition of searchers comes from the openness and non-accessibility of the blockchain network. On the one hand, they need better servers and faster information transmission channels to obtain the latest mempool data. It also requires ingenious algorithms and strategies to keep yourself from being captured by others while gaining benefits. There is no doubt that the searcher field is a profitable and sustainable track, but this field does not have the possibility of commercialization for the general public, it is more like a quantitative transaction in the encryption field. For large investment institutions, the rate of return for investing in an on-chain quantitative trading team may not be very high. But for small entrepreneurial teams and individuals who are familiar with quantitative trading and smart contract development, this may be a relatively good practice for entering the encryption field. For example, set up an encrypted quantitative fund and promise a return of xx%. Of course, this field is not static. It can always be seen from the data that the trading volume of JIT robots has surged in recent times.
With the increase of on-chain transaction users and the emergence of various new DeFi protocols, there will be a large number of new profit opportunities in the future. This is a test of the execution ability of the team itself and the ability to understand the protocol on the chain.
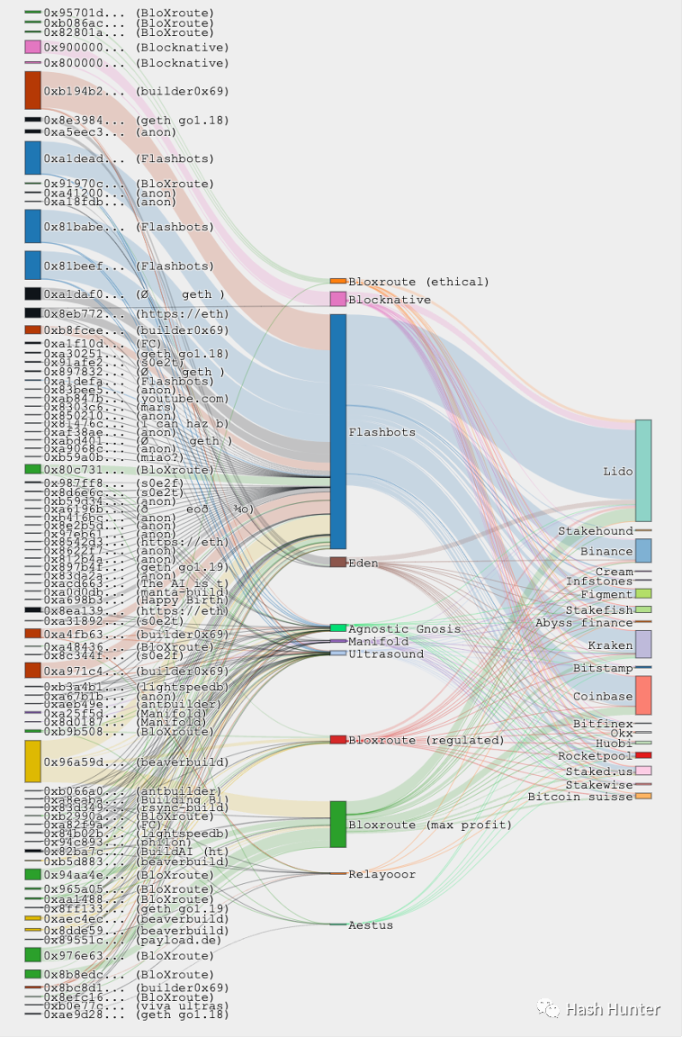
Builders: According to the current data on the chain, the market for builders is facing fierce competition. And more and more node service providers have entered this market.
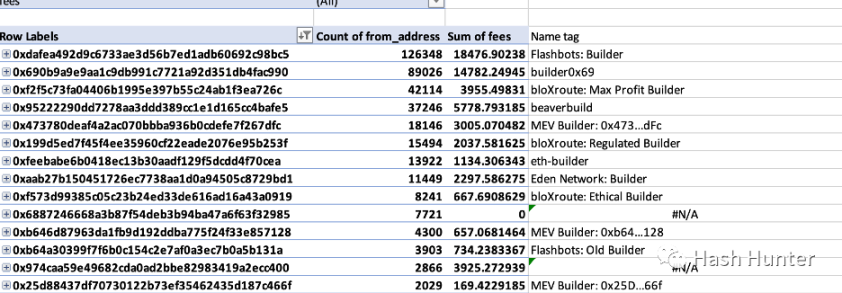
For example: BloXroute, Manifold, Blocknative, Beaverbuild, 0x69, Eden Network, Lightspeed, ETH-Builder, etc. The leftmost part of the figure above is the block occupancy of the builder, the middle is the occupancy of the relay layer, and the right is the occupancy of the verifier. Flashbots is not the largest block builder, but is indeed the largest relay service provider. In December 22, the author counted 600,000 block data since the merger.
In this field, BloXroute, Manifold, Blocknative, and Eiden Network are one of the few project parties that have raised funds in the open market. Among them, Eden Network and Manifold only provide block building and relay services, while Bloxroute and Blocknative provide other services as well as block building services. Bloxroute provides different relay interfaces according to the needs of validators, such as profit-maximizing relay and regular relay. From a functional point of view, Bloxroute is closer to validator users and project parties, such as providing node protection services and faster transaction initiation services. And Blocknative is more for searchers and some DeFi project parties, such as memory pools and transaction simulation services.
secondary title
market size
We can measure the market size through the production volume of future blocks. The profit of each block constructed by the existing block builders is about 0.0005 ETH. The average daily block output of Ethereum is about 7000 blocks. Then in the future, the overall block construction profit in Ethereum will be 1,200 ETH. This income is actually very low (the overall execution level income is about 250,000 ETH), which is why these project parties will have other businesses. as a reason for income. There are many factors that affect the profit of block construction, and the current data cannot represent the future. For example, block builders actively reduce profits in order to seize the market, or insufficient existing transaction volume affects the number of bundles, etc. From the perspective of the overall interest chain, the benefits of block builders are more controllable. Its technical architecture also has the possibility of large-scale deployment and operation. For the project side, more paid services can be added on the basis of building block services, making block building and relay services an option to attract developers and protocol layer diversions (similar to Web3 infrastructure providing nodes for free transfer).
SAAS service: There are also some business models in the market that provide services to searchers and researchers, such as Blocknative, which provides MEV data analysis EigenPhi and the memory pool data service mentioned above. The other is the faster private node call service and node hidden service, enabling searchers to quickly and covertly call and communicate with nodes.
Anti-MEV services: There are also some decentralized exchanges that are resistant to front-running and sandwich attacks, such as the private transaction services provided by 1inch and cowswap. Its principle is similar to the private RPC service, and the user's transaction is sent to the block builder separately, so that the transaction does not go through the memory pool.
Order feedback service: This model is more common in the traditional securities trading market. Robinhood uses this service to make money when retail investors place orders through its software. Robinhood will pass this order to the market maker, and the market maker will also pay Robinhood cash when trading in the market. On-chain transactions can also follow this principle, such as the rook protocol. Users can place orders on rook's exclusive decentralized exchange, but this transaction will not be executed directly on the chain, but is now internally auctioned to rook's custodian (keeper). Once the bid is successful, the custodian has the power to put the user's transaction into its bundle, thereby using the user's transaction to conduct MEV activities and obtain profits. After this transaction closes, the user gets a portion of the rook tokens from the auction and the custodian gets the MEV profit. In this link, the custodian actually acts as a searcher, but the source of its order is no longer the memory pool in the past but the private dark pool established by rook protocol itself. From the perspective of value distribution, users can obtain a part of the MEV revenue while completing the order.
Encrypted dark pool service: The author also conceived a business model. The new decentralized protocol can build a protocol-specific block construction layer and relay layer while establishing transaction services. All transactions generated by users using the protocol will enter this dark pool. Searchers need to pay a fee to get exclusive order flow for arbitrage. The protocol layer can return the fees paid by searchers to users, such as airdrops and gas-free services, so as to attract more users to enter dark pool transactions.
Example: The wallet provider can set up a dedicated dark pool node, so that all transfers and transactions using the wallet are performed through this dark pool: a user exchanges token a for token b on Sushiswap; user b exchanges token b on Uniswap The b token is exchanged for a token above. The moment when these two orders are combined will lead to an imbalance in the ab transaction exchange rates of the two exchanges Uni and Sushi. Arbitrageurs can auction off these two orders and bundle their own arbitrage strategies to achieve flash loan arbitrage and so on. Of course, these two transactions must reach a certain level before the exchange imbalance between different pools can be realized. It can only be realized when the transaction scale reaches a certain level, for example, a market maker auctions off 20 user orders to complete a huge arbitrage. Of course, this model also has a lot of risks, such as the user's own transaction loss and the excessive centralization of block builders.
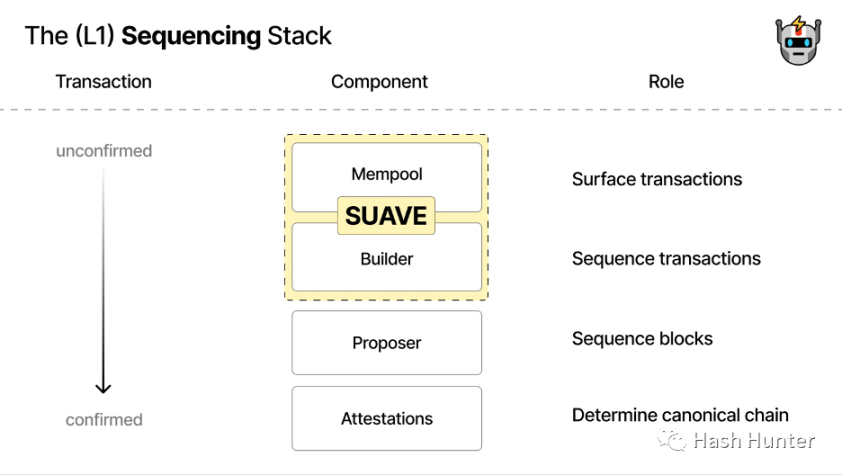
SUAVE: By establishing an independent memory pool and block construction network, all future order streams and blocks can be publicly bid and accessed by searchers and verifiers and span the multi-chain architecture.
At present, the architecture design of SUAVE is still in the discussion stage. I think SUAVE is very likely to launch its own dedicated node client. If the existing PBS design is used, in order to realize the communication with the L2 layer, it is necessary to increase the communication with the L2 node on the basis of the existing architecture. That is to say, by deploying multiple chain nodes to verify transaction messages, this design method is too bloated and complicated. It is better to re-develop a set of light node clients compatible with all EVM ecology to achieve what is described in its documentation. Modular functionality.
There is no doubt that Flashbots is the leading player in this field. Most of the current architecture design and code are open sourced by it, and it leads the direction of the entire industry. The author believes that the opportunity in this field does not lie in arbitrage and staking, but in who can have the ability to build blocks and distribute transactions. The value of this ability does not lie in the economic layer but in the power layer of the entire Ethereum ecosystem - whoever controls the ordering of transactions in the block controls the distribution of power, and whoever controls the distribution of power can reshape the overall network Benefit value distribution. Past circulation value of user tokens is distributed through smart contracts and transaction by transaction, while future value is distributed through block builders who combine these order streams. In other words, we will move from the era of competing for single transaction value to the era of competing for block space resources in the future.
first level title
3. Prospects and concerns for the future
The reason why many users have difficulty understanding MEV is that, from our human point of view, we believe that the order sent out can be executed simultaneously in chronological order and is continuous. From the perspective of the block network, the user's intentions and behaviors are arranged by an indivisible order, which is discontinuous. Seekers can capture a transaction after a user sends it and reorder it for benefit. On a macro level, we can approximate that searchers have achieved the ability to manipulate time in a small area through bundles. To give an inappropriate example, from the user's point of view, one's own transaction is attacked by a sandwich, which is similar to being snatched away by searchers from the future and the past at the same time. The cases described in this article all happened on the Ethereum chain, but one thing I can be sure of is that as long as the blocks contain non-continuous and indivisible order arrangements, MEV will definitely happen.
secondary title
centralization trend
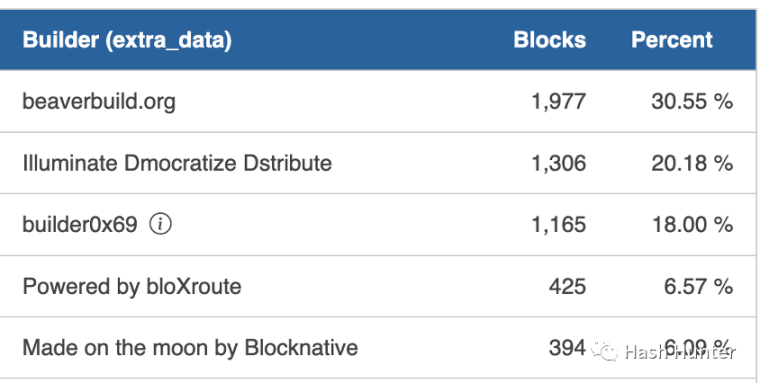
The impact of the power of block building on future protocol layers is profound. As "1984" said: "Whoever controls the past controls the future; whoever controls the present controls the past." From January 3rd to 27th, more than 80% of the blocks were only 5 blocks Created by block builders.
It is worth mentioning that there is a special function in the block building client, the builder can prevent certain addresses from being included in the block by setting up a blacklist. This also means that future builders have the ability to review transactions. When some users who do not meet their specifications initiate a transaction, his transaction will be in a pending state and never reach the real network. The Tornado-Cash incident is a node-level review launched by major node service providers, while the builder launched a mempool-level review. Of course, with the participation of more and more users and project parties, the increase in the decentralization of future block construction will dilute the impact of this kind of review. However, the potential harm brought about by the centralization of block construction is still not to be underestimated. The author conceived several possibilities for readers' reference.Law enforcement block:
Assuming that most of the builders and node service providers in the future are controlled by a single entity, then we will formally enter a blockchain network manipulated by the laws of entities. The deployment of all transactions (smart contracts, transfers, authorizations, interactions) here will be reviewed and approved multiple times. The node caller reviews the wallet address and IP of the transaction initiator, and confirms that it is correct. The initiated transaction will enter the monitored non-public memory pool, and the searcher will undertake the law enforcement function to judge the legitimacy of the transaction content. The content and information of the transaction is graded and tagged, and it is included in the bundle and sent to the different builders. Builders can put transactions of different levels into blocks with different priorities according to transaction types and functions, and then be reviewed by validators through broadcasting. Some transactions that do not meet the entity rules will be discarded in the memory pool, and no searchers and builders are allowed to salvage until the user cancels it himself. In this case, hacking and theft activities are minimized, but users lose maximum access to the blockchain network, stifling innovation and expression of information.Enterprise block:
Assuming that the future builders and node vendors are monopolized by a few commercial giants, we will enter the era of zero-sum game for block resources. Although users and developers have gained relative freedom, they are subject to the inability of multiple giant agreements to flexibly choose the object of transaction, and even the user's order flow is exploited and used by the auction at a clear price in the dark pool. We will face maximum malicious commercial competition, such as builders selling review rights and building rights for profit. Some protocols can delay and block the opponent's user transactions to a certain extent by buying out the competitor's order flow. For example, when a user buys and sells on an NFT exchange, when he takes an order, the transaction is placed at the end of the block by the counterparty, and the counterparty user can take the NFT first to make the original user’s transaction failed. The DEX protocol can also reach a deal with the builder to put all the transactions of the counterparty into a block, causing a short-term token pool imbalance, thereby invalidating the transactions of the counterparty user. In this case, business activities still exist, but users and developers have to choose sides according to the rules, thus curbing business innovation.Tampering with history:
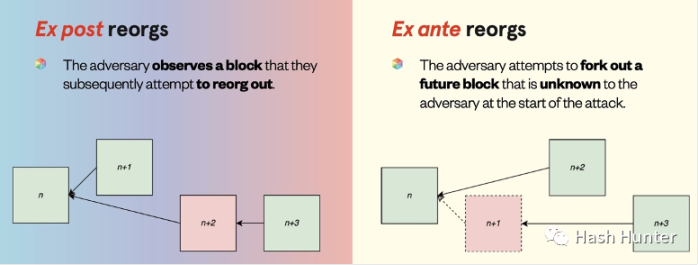
In the case of too much concentration of builders and nodes, the proof-of-stake chain can delete unwanted blocks in the past through reorganization attacks. And the proof-of-work chain can change the timeline by re-mining blocks from the past through a time thief attack.
In this case, the power machines have the ability to change the past, thereby erasing history that is not in their favor.secondary title
light up the dark forest
light up the dark forest
The above-mentioned case is an event trend that only occurs under very extreme circumstances. The subsequent launch of the SUAVE architecture and the influx of participants will alleviate the impact of abuse of private order flow and centralization of builders. The premise here is full free market competition and protection for pioneers and innovators. It is hard to imagine what a closed and dark environment we would have without the open source of code by participants in various fields and the openness of MEV data by researchers in various institutions. The continuous contributions of developers and researchers to code and data allow us to see a glimmer of light in this dark forest.
A truly open and fair MEV market: All searchers and builders are allowed to participate, and users are free to choose their transaction direction. Searchers and builders can fully compete and give back to users of the protocol layer to the greatest extent. The protocol can use the order flow to achieve efficiency and maximize the use of block resources.
A fair market-oriented competition environment is the soil that breeds innovation, and a more effective benefit distribution mechanism and a decentralized structure are the cornerstones for its realization. The technology of searchers and block building is neutral and its impact on the environment depends on how people use it. In other words, whoever controls the present controls both the future and the past. Reaching the conditions to illuminate the dark forest does not only depend on the capital; it does not depend only on the plan, and the right to decide is in the hands of everyone at the moment.
first level title
MEV-Boost Architecture Preview
The over-centralization problem caused by MEV
Coinabse announces adoption of MEV-Boost as its staking node component
Restoration Services Source Code
EigenPhi's report on MEV on Unisawp
Open source block builder architecture
Papers on Recombination Attacks
Reassembly attack detailed video