Original title:Seedless Self-Custody: On MPC and Smart Contract Wallets
Original Author: Nichanan Kesonpat
Original compilation: ChinaDeFi
Original compilation: ChinaDeFi
Self-custody has long been hailed as a best practice for managing crypto assets. The FTX and Celsius debacles are the latest in a long string of events that have reminded the industry that "whatever is your key is not your coin" has sent people running towards non-custodial wallets. After the FTX incident was exposed, Safe received a net inflow of more than 800 million US dollars, Ledger experienced multiple record high sales in a short period of time, Trezor sales soared 300%, and ZenGo achieved triple digits overnight growth, deposits at an all-time high, all in the same week.
However, a large number of users are still willing to take hosting risks in exchange for lower costs and ease of use. We still have a long way to go before non-custodial wallet infrastructure becomes the path of least resistance for securing and managing assets.
Luckily, there is now a thriving ecosystem of wallets offering even more options for individuals, DAOs, and institutions. Encryption is no longer just about secure storage, it includes using assets in the new economy. However, the ever-increasing attack surface and vulnerabilities, coupled with increasingly rich features, require wallets that can resist attacks while supporting daily business and personal use.
As with all design decisions, this is an optimization question of multiple considerations for a given use case, and the capabilities of wallet solutions and key management practices that need to be pragmatically balanced against the collective needs of target users:
Individuals need a seamless user experience, low fees, and flexibility in interacting with dApps.
DAOs require transparent treasury management, ecosystem governance participation.
Institutions want to outsource responsibility through chain agnosticity, auditability, and institutional-grade security.
Significant progress has been made in two classes of alternative key management solutions: smart contract wallets (including multi-signature wallets) and multi-party computation (MPC) protocols.
This article covers:
properties to be considered in the wallet;
Overview of traditional, MPC and smart contract wallets;
Ongoing challenges for the wallet ecosystem;
A summary of the trade-offs of current wallet solutions, and an outlook for wallet infrastructure.
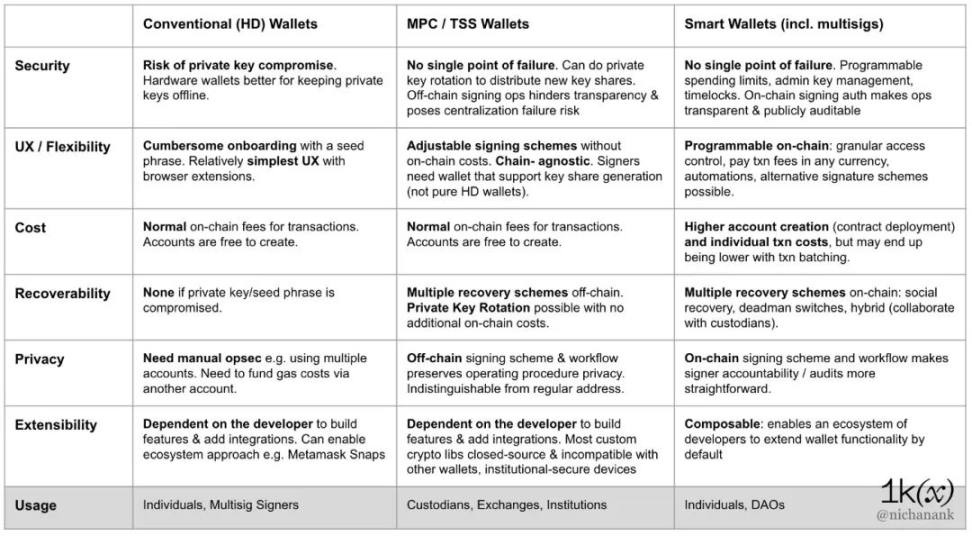
Properties to consider in wallets
Safety. Level of protection from simple to complex attacks. "Good key management" requires choosing a range of solutions whose onboarding and operating costs match the nature of on-chain activity and the amount of risk involved.
cost. How expensive it is to create accounts, manage access and execute transactions.
User experience and flexibility. Granularity of access control management, overhead policies, restrictions and permissions.
recoverability. Have the ability to restore assets and access in the event of a threat or loss.
scalability. Can bring new features to core products and build a comprehensive ecosystem of products and services.
privacy. Addresses can be easily linked to individuals.
Traditional (HD) wallet
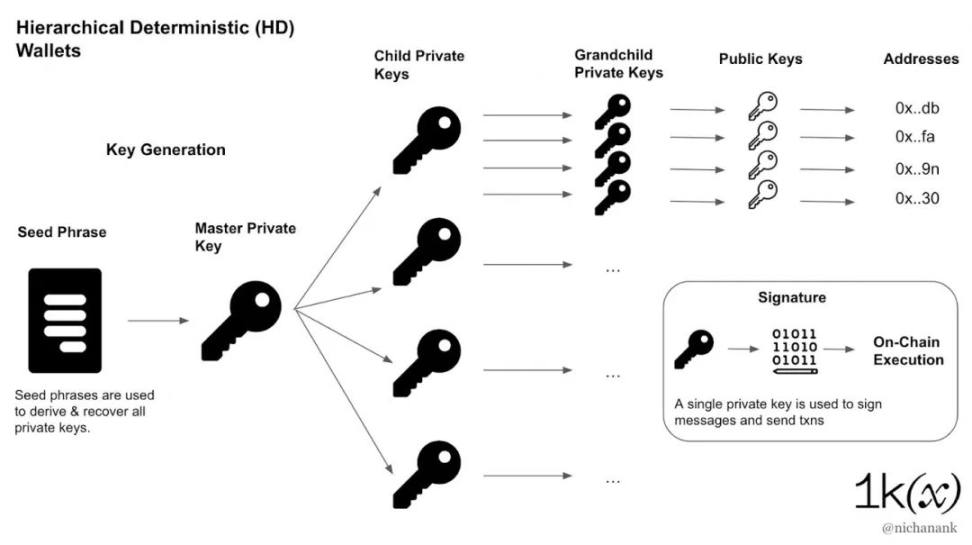
Traditional wallets use mnemonics and a Hierarchical Deterministic (HD) structure to derive private keys, corresponding public keys, and on-chain addresses. These wallets allow users to generate private keys used to sign transactions and recover all keys using a seed phrase.
Until now, traditional wallets have been the tool for users to keep their assets and their main entry point for interacting with blockchain applications. Browser extensions like MetaMask and mobile apps like Rainbow have attracted millions of users to this ecosystem. Users who want to reduce their risk can opt for hardware wallets such as Ledger and Trezor, which provide better security by protecting private keys offline.
While a huge collective effort has been made by the industry to inform users of the importance of keeping seed phrases and keys secure, this single point of failure remains a significant barrier to widespread adoption. If the private key is lost, in addition to losing all assets, users must manually track multiple addresses, token approvals, and compromise privacy by having to fund new addresses.
Today, irrevocable strings not only allow full “access” to a person’s life savings, but there is a growing trend to link the on-chain history of a user’s online identity. The incentive to gain access to private keys is so great that hackers, each devoting unlimited resources, carry out increasingly creative attacks. Now, it's no longer enough to rely solely on the user - we need to completely eliminate this single point of failure.
Multi-party computation (MPC) wallets and smart contract wallets help us achieve this, and there is already an ecosystem of products and services for both types of products and services adopted by institutions, individuals, and DAOs alike. While both types of wallets eliminate single points of failure, they have some fundamental technical differences that lead to different trade-offs.
MPC Wallet
Broadly speaking, multiparty computation (MPC) enables a group of mutually distrusting parties to jointly compute a function based on their inputs while keeping those inputs private. In cryptography, this is especially useful for holding private keys used to decrypt data or generate digital signatures.
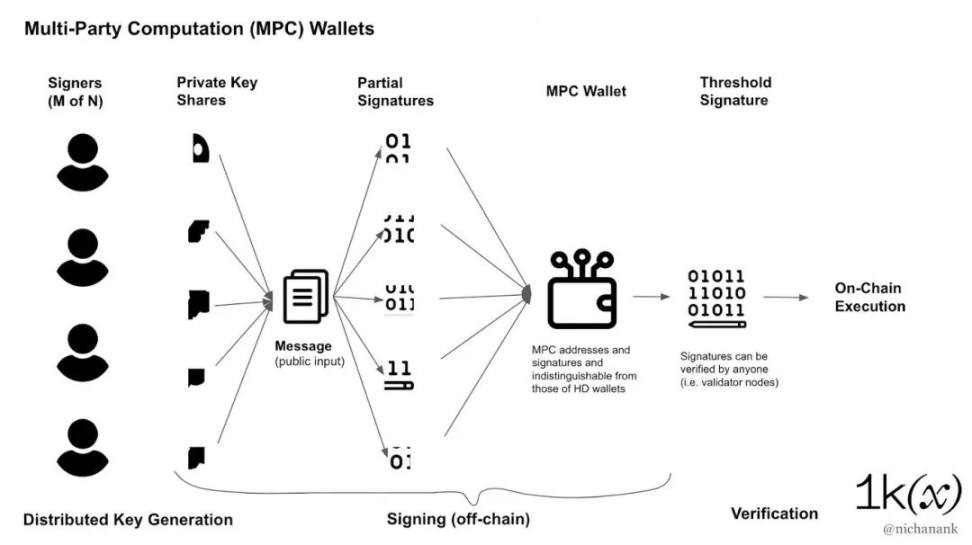
MPC wallets eliminate single points of failure by using a Threshold Signature Scheme (TSS). In this paradigm, we create and distribute parts of the private key so that no single person or machine has full control over the private key—a process known as distributed key generation (DKG). We can then combine the parts and co-generate the public key without exposing the parts between the parties.
To sign messages and transactions, each party enters the secret shared part with the public input (the message to be signed) to generate a digital signature. From there, anyone who knows the public key (i.e. a validator node) should be able to verify and verify the signature. Since key parts are combined and signatures are generated off-chain, transactions generated from MPC wallets are indistinguishable from those of traditional private key wallets.
This preserves a level of privacy for MPC wallet users. This feature is useful out of the box for organizations that wish to keep their signature schemes and signer activities out of the public eye, as these processes happen off-chain. This way, organizations can keep internal logs of participating signatures without making them public.
Private Key Rotation is another MPC protocol that takes as input a secret share and outputs a new set of secret shares. The old secret share can be removed and replaced with a new share, which can be used in the same way without changing the corresponding public key and address.
Advantages of MPC Wallet
There is no single point of failure. A complete private key is never centralized on one device at any time. There is no mnemonic either.
Adjustable signature scheme. Approved fixed headcounts can be modified as individual and organizational needs change while maintaining the same address. Organizations can dynamically adjust signature schemes without having to notify counterparties of a new address each time.
Granular access control. Organizational users can assign an unlimited number of transaction approvers to a policy, and assign permissions that accurately reflect organizational roles and security measures (time locks, MFA, fraud monitoring). Individuals can choose the semi-custodial route through MPC wallet-as-a-service, where a third party holds a key shared portion.
Lower transaction and recycling costs. MPC wallets are represented on the blockchain as a single address with the same gas costs as regular private key addresses. This is very important for users who make hundreds of transactions per day (such as in B2C use cases). Lost key shares can also be recycled off-chain.
Blockchain agnostic. Key generation and signing rely on pure cryptography off-chain. Extending compatibility to new blockchains is simple, as wallets only need to be able to generate signatures using an algorithm recognized by that chain.
Disadvantages of MPC wallets
Off-chain accountability. Signing authorization policies and approving fixed numbers are managed off-chain, so these custom rules are still prone to centralization issues. The key share is still a cryptographic secret and should be treated like the entire private key. Off-chain rules and signatures hinder transparency and require stricter operational audits.
Incompatible with most traditional wallets adopted by many users (no seed phrase, no full private key stored on a single device). The MPC algorithm is also not standardized, nor is it natively supported by agency-grade security devices such as the iPhone SEP and HSM.
Mostly isolated custom products. Many MPC libraries and solutions are not open source, so it is difficult for the ecosystem to independently audit and integrate them if something goes wrong.
MPC-based solutions are primarily aimed at institutional clients such as funds, exchanges and custodians. MPC technology providers like Fireblocks and Qredo allow their customers to define their own workflows for different types of transactions, allowing them to remain compliant and secure. However, the retail investor base still relies on independent research and private key wallets. Web3Auth recently released an MPC SDK that users can use their iCloud or email as a backup. Decentralized custody protocols like Entropy are building open source tools for consumers and DAOs so they can store assets online.
Notable Developments in MPC: Programmable Key Pairs
Lit is a decentralized protocol that stores key shares on Lit network nodes. A public/private key pair is represented by a PKP (Programmable Key Pair) NFT whose owner is the sole controller of the key pair. The PKP owner can then trigger network aggregated key sharing to decrypt files or sign on their behalf when arbitrary defined conditions are met.
This has great implications for decentralized access control, asset management, and automated on-chain interactions. By granting signing privileges to Lit Actions (immutable code deployed to IPFS), PKP can be used as an MPC or a decentralized cloud wallet, using any authentication method expressible in javascript.
Minting a PKP NFT is an MPC-based distributed key generation process that makes the NFT owner the root owner of the PKP. Therefore, transferring this NFT is equivalent to the transaction private key, which actually breaks the concept of "soul-bound" tokens (SBT), because SBT is bound to a specific owner, and now the wallet itself can be safely traded, so , "wallet-bound token" might be a more appropriate name.
Smart Contract Wallet
Ethereum currently has two account types:
Externally Owned Account (EOA) - controlled by a private key
Smart contract account - controlled by code
A smart contract wallet ("smart wallet") is a smart contract that behaves like a wallet, ie an interface that allows users to manage funds, do web3 logins, and interact with dApps. Unlike private key wallets, smart wallets require an initial cost to create because smart contracts need to be deployed on-chain.
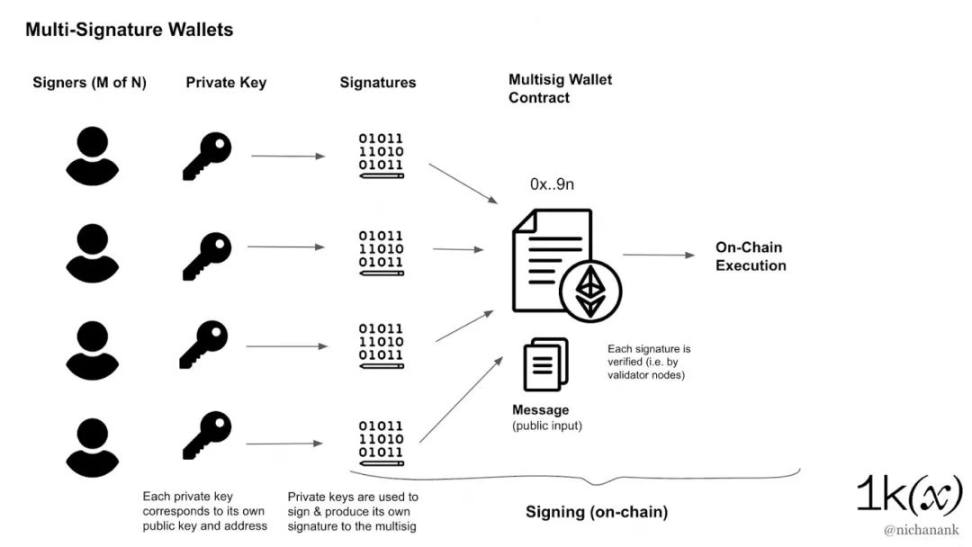
Multi-signature wallets are smart contract wallets that require signatures of M-of-N keys to execute transactions. MPC only creates a single signature regardless of the number of participating key shares, and multisig signs transactions using different signatures generated by different private keys. This makes it compatible with existing private key wallets and sits a layer above traditional wallet addresses like Ledger or MetaMask.
Smart contract account standards like Safe provide a foundational layer for an ecosystem of asset management products and services. Functionality is added through modules, which allow users to define management key logic, spending limits, recurring transactions, account automation, tiered access, and more. Currently the most prolific set of Safe modules is built by the Zodiac team.
Advantages of smart contract wallets
There is no single point of failure. Multiple signatures are required to execute a transaction.
Programmable access control. Users can define different policies, set time locks, spending limits, automation.
Transaction batching can be implemented to save costs.
Scalable. Thanks to the composability of smart contracts, wallet developers can create an ecosystem of modules that users can choose to add to their wallets, creating an ecosystem for new features like NFT lending frameworks, DAO voting modules, and non-custodial asset management services. app store.
Programmable recovery. Wallets can offer several options for recycling funds to the smart contract itself.
On-chain accountability. On-chain signature authorization policies and aggregations make it clear which keys are used to sign transactions, making operations more transparent and straightforward, allowing auditing of who participated in transactions in case of errors.
Migration to other signature schemes is supported. Smart contract wallets can change their signature schemes to something simpler, less gas-efficient, or quantum-resistant. They can also be used on iOS and Android devices (turning the phone into a hardware wallet), or enable Ed25519, which allows the use of iOS biometrics and web authentication.
open source. Anyone can audit the implementation and function expansion of the smart wallet, thereby addressing bugs and adding new functions through the ecosystem.
Disadvantages of smart contract wallets
higher fees. Smart wallets have higher fees than normal single-address transactions because of the need to verify multiple signatures. Operations such as adding/removing owners and changing thresholds also require on-chain transactions.
Not universally supported. While smart wallets can be deployed on any EVM chain of the same address, they require custom implementations on non-EVM chains.
Recovery costs are higher. While the recovery logic is programmable, on-chain fees need to be paid to execute it.
Incompatible with non-upgradeable contracts. Although EIP-1271 allows applications to sign on behalf of contract wallets, it is still not universally supported and cannot be added to non-upgradeable contracts.
Notable Developments in Smart Contract Wallets: Account Abstraction
Smart wallets play a vital role in the ecosystem-wide effort to completely move away from EOA and private keys (also known as account abstraction). In this paradigm, all accounts are smart contracts with their own logic to dictate what constitutes a valid transaction, allowing users to tailor accounts to their specific needs.
Account abstraction has been discussed since 2016, but the ecosystem has been slow to coordinate on a solution. L2 has greatly accelerated its awareness and adoption, for example StarkWare has localized all Starknet accounts into smart wallets, and zkSync 2.0 will also be launched with AA.
On Ethereum, multiple EIPs exist to complete milestones on the roadmap, making account abstraction a reality.
EIP-4337: Move signature verification, gas payment, and replay protection from the core protocol into the EVM, allowing users to use smart wallets with arbitrary verification logic instead of using EOA as their main account, and without any consensus layer Change. This EIP introduces a UserOperations memory pool that exists in parallel to the existing memory pool. Bundlers (validators, MEV searchers, or the application itself) fetch transactions from the UserOperations pool, forward them to the blockchain and pay fees. Here, the startup wallet itself does not pay the gas fee, but the application can aggregate it for the user through a fee-based subscription model.
EIP-3074: Allow EOAs to delegate control to contracts, allowing existing EOAs to send operations paid for by third parties.
EIP-5003: Upgrade existing EOAs to contracts and allow them to migrate from ECDSA to more efficient or quantum-resistant signature schemes.
Challenges Facing the Wallet Development Ecosystem
technical loopholes
The Parity Multisig hack and the recent Rabby Swap attack showed that even the best conceptual way of storing funds means little if the implementation is flawed. We can foresee that standards for smart contract accounts will emerge.
level of social aggression
The merits of any technological solution still cannot eliminate the risks at the societal level. The $600 million Ronin Bridge breach was not due to any technical flaw, but a social engineering attack on a Sky Mavis employee that gave attackers access to validator keys. In addition to deciding which wallet to use to manage assets, organizations also need to ensure that each "component" of this critical system is truly independent at the social and technical layers.
Security and Migration Costs
Migrating from one account to another is neither fun nor cheap. While there are currently strong wallet alternatives on the market, there are real costs for users to migrate their existing EOA: transaction fees, closing/opening DeFi positions, revenue impact, user error, time and effort.
Self-custody is a scary prospect for most users today, and since improvement requires conscious effort, it can be a daunting task. Most transaction data is unreadable (although this is changing), and errors are irreversible. Like crypto education, this problem cannot be solved by a team alone, it requires tools and user experience patterns.
in conclusion
in conclusion
Although MPC and smart wallets share a common "this vs that" framework, in the long run they are not competing but complementary. MPC provides shared security at the key generation and management level, while smart contracts bring scalability and an ecosystem approach to function and application development. For example:
MPC can enhance existing multi-signature schemes by splitting one or more private keys into multiple parts. If three people are used to secure a 2/3 multisig, each of the three users can subdivide their individual private keys using MPC and store their MPC key parts on separate machines.
A community or DAO can be a multi-signature signer with a PKP NFT that manages a decentralized cloud wallet that can be used for automated investing or DEX interactions.