first level title
Cross-chain bridges have become the main target of hacker onslaught
According to Elliptic statistics, in 2022, hackers will steal more than US$1 billion on cross-chain bridges. On February 3 this year, Wormhole, a cross-chain project connected to Solana, was hacked, with an estimated loss of $325 million. On March 23,
The total value of more than $600 million in Ethereum and USDC was stolen in the Ronin Bridge case. On June 23, hackers also attacked the Horizon Bridge, which leads to Harmony’s layer 1 blockchain. On August 2, the cross-chain bridge Nomad was stolen and lost $190 million. Wormhole, Sky Mavis, and Harmony have all suffered more than $100 million in losses this year from blockchain vulnerabilities.
In view of the recent frequent security incidents, MixMarvel DAO Venture specially conducted interviews with relevant technical leaders regarding some technical security issues. The person in charge of technology believes that bridge security will be a key issue for the entire blockchain industry. According to the interview results, we combined MixMarvel DAO Venture's own cognition and thinking on the underlying technology to form this discussion.
To sum up, most of these attacked cross-chain projects use multi-signature technology. Regarding the security issues of multi-signature, we will make a specific analysis later. Before that, we must first clarify what the role of cross-chain is, and why it has become the main target of hackers.
Why Hacking Attacks Mostly Happen on Cross-chain Bridges
secondary title
What is the function of cross-chain bridge
MixMarvel DAO Venture believes that there are at least two aspects worthy of attention.
first,first,The cross-chain bridge can break the state of "blockchain island" formed by transaction difficulties between different public chains
, and greatly improve the utilization of assets. We have entered the multi-chain era represented by new public chains such as BSC, Solana, Polygon, and Heco. After several rounds of iterations, the diversity of cross-chain bridges is becoming increasingly evident. Anyswap (now renamed Multichain), as one of the widely used cross-chain bridge representatives, has completed three key version updates and upgrades. The latest V3 version uses multi-chain routing to realize Native Assets cross-chain, but also retains The V2 version of the asset cross-chain destruction scheme is introduced to reserve more diverse choices for users. The cross-chain bridge allows users to transfer assets, data and information between chains, which greatly promotes the communication and compatibility between multi-chain ecosystems. real needs.
Second, the cross-chain bridge strengthens the cooperation between the underlying infrastructure. After the data island state is broken, the competition and cooperation between chains gradually intensifies. In order to win more resources, each blockchain underlying infrastructure project will cooperate with each other through cross-chain bridges to expand their respective ecology.We believe that the low difficulty of attacking cross-chains and high returns are the fundamental reasons for the frequent theft of cross-chain assets.
Attacking cross-chains is more profitable and less difficult than public chains
text
1. In terms of income: it is more profitable to attack cross-chain bridges
According to the data of DeFi Llama, as of July 2022, the cryptocurrencies locked in cross-chain bridges are as high as $10.88B, of which WBTC accounts for the largest market share, with a TVL of $5.2B, and Multichain ranks second, with a TVL of $1.88B.
This means that the amount of assets on the cross-chain bridge is quite attractive to hackers. According to the CertiK report, when a "bridge" has hundreds of millions of dollars in custody assets and operates on two or more blockchains, the likelihood of them being hacked increases significantly.
2. Difficulty: 51% attack
In terms of difficulty, hackers are more likely to focus on cross-chains that are less difficult to steal. In blockchain, there is a concept of 51% attack. Regardless of PoW (Proof of Work) or PoS (Proof of Stake), when it comes to consensus mechanisms, 51% attacks are theoretically possible.
In the PoW algorithm, if a hacker has more than 51% of the computing power, he will have an absolute advantage in obtaining the right to bookkeeping. In other words, he has the right to tamper with blockchain data.
However, if a 51% computing power attack is to be carried out, hackers need to spend a lot of money to purchase mining equipment and electricity to obtain stronger computing power than other ordinary miners. Therefore, if a hacker attacks the public chain, he needs to perform a 51% computing power attack. The cost is too high, and the profit is too low, which makes it more likely that the gain outweighs the gain.
Attacking the public chain of the PoS algorithm is more difficult than attacking the public chain of the PoW algorithm. Attacking the public chain of the PoS algorithm requires the attacker to obtain at least 51% of the tokens used for pledge in the entire network, and the pledged tokens are mainly obtained through purchase. Therefore, in reality, obtaining 51% of the tokens used for stake in the entire network is often more than
It is much harder to rent 51% of the computing power (to attack the public chain of the PoW algorithm). As Ethereum founder Vitalik believes, no one will conduct a 51% attack on Ethereum just to steal 100 Solana-WETHx. According to statistics in 2019, hackers need $31,367,656,630 for a 51% attack on the public chain of the PoS algorithm, and $255,629 for a 1-hour 51% attack on the public chain of the PoW algorithm.
In fact, attacking large public chains takes at least several hours to complete. The cross-chain is different. If a hacker wants to attack the cross-chain, he only needs to find the loopholes in the target cross-chain bridge and break through it to achieve his goal without spending a lot of time and money.
first level title
Hash-locking, Notary Schemes, and Relays are currently the most common blockchain cross-chain technical solutions.
secondary title
hash lock
Satoshi believes that Hash Time Locked Contracts (Hash Time Locked Contracts) are composed of Hashlocks and Timelocks. Hashlocks are similar to two-factor authentication. Timelocks requires the intended recipient of funds to provide the correct secret phrase within the time limit and then receive the payment . Otherwise, the transaction returns funds to the sender.
Hash time-locked contracts, which can be viewed as time-limited, conditional payment agreements, do not require a trusted third party. These programmable escrow protocols enable conditional P2P value transfers and reduce the risk of transactions. In addition, hash locking technology mainly helps realize atomic swaps in cross-chains (Atomic Swaps, peer-to-peer transactions in cross-chains) and Bitcoin Lightning Network (Lighting Network).
However, hash locking has certain limitations. First of all, the connecting party needs to bear certain transaction risks. When trading, the two coins limit the delivery time, if the time limit of one transaction party is greater than that of the other transaction party. This may cause one party to obtain the agreed asset, while the other party cannot obtain the corresponding currency value.
Therefore, hash locking can only be exchanged but not the transfer of assets or information, and its usage scenarios are very limited. At least at this stage, it has not been widely used. In the following analysis of cross-chain insecurity, we will skip hash lock directly.
secondary title
relay
The disadvantage of relay technology is that when the network load is heavy, the storage space of the relay buffer may be insufficient, resulting in overflow phenomenon and signal frame loss. If the repeater fails, it will affect the work of two adjacent subnets.
secondary title
Witness Mechanism
Witness mechanisms are mainly divided into three categories: single-signature witnesses, multi-signature witnesses, and distributed signature witnesses.
Single-signature witnesses are also called centralized witness mechanisms. Witnesses act as transaction confirmers and conflict arbitrators during the transaction process. The technical architecture of this model has a low threshold, which makes transaction processing efficient, but it is actually controlled by a centralized organization, and its limitation lies in the security of centralized nodes.
The multi-signature (Multi-Signature) witness mechanism is currently the most widely used technology. The multi-signature witness mechanism uses multi-signature technology, that is, a transaction requires two or more signatures to take effect. Different cross-chains will set multi-signature rules according to their own needs. For example, 3/6 multi-signature means that 3 validators with private keys among 6 people need to sign the transaction application to successfully complete a transaction. If the verifier's private key is leaked, such as the hard drive storing the private key is stolen or misplaced, it is likely to cause immeasurable losses to cross-chain assets.
The difference between the witness mode and the relay mode lies in how the target chain processes the received messages. The witness mode is unconditionally trusted and executed, and its security depends on the witness itself; the relay mode needs to be verified by itself before execution. The security depends on the data synchronizer (MerkleTree transmitter) of the light wallet on the target chain.
Unsafe factors of cross-chain technology
text
1. The security risk of multi-signature verification is the main reason for the theft of cross-chain assets
There are security risks in multi-signature verification, which leads to frequent hacker attacks, usually manifested in the following three points:
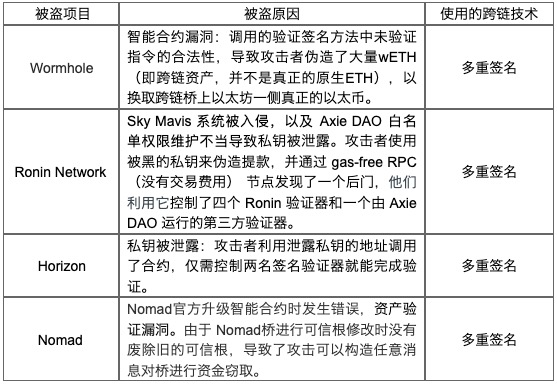
a) The leak of the private key causes the validator to be hijacked. For example, in the Ronin Network and Horizon attacks, hackers used leaked private keys to hijack signature verifiers and complete transactions. In order to identify deposit instructions or withdrawal instructions, the Ronin Network is protected by nine signature verifiers, of which only five signatures are required for verification and transactions. Hackers used hacked private keys to fake withdrawals while discovering a backdoor via gas-free RPC (no transaction fees) nodes, then exploited it to take control of four Ronin validators and a third-party validator run by Axie DAO device.
b) The number of validator nodes required for verification is small, which gives hackers an opportunity to exploit. For example, the Horizon bridge has only four multi-signature verifications and does not secure two of the four multi-signatures. Hackers only need to control Horizon's fewer signature verifiers to complete asset theft. Therefore, a small number (usually less than 50%) of signature verifiers required to verify may make it difficult to ensure the robustness of the cross-chain process.
c) The vulnerability of the signature verification method is also one of the smart contract vulnerabilities. The development models on each blockchain are different (for example, different communication protocols, different consensus mechanisms, and different governance models), which will increase the possibility of smart contract vulnerabilities when establishing cross-chain interfaces. For example, Wormhole attackers signed their own cross-chain requests using signature methods that were deprecated due to updates. Because this method does not strictly check the incoming instructions, the attacker forged a large amount of wETH (that is, cross-chain assets, not the original real ETH) and uploaded a fake smart contract address, successfully avoiding the verification signature. And withdrew a lot of money. At the beginning of the theft of the Nomad cross-chain bridge, its contract address still had about $100 million in assets. At this time, Nomad did not take any measures, neither repaired the smart contract vulnerability, nor changed the signature verification method. Competent hackers continued to steal assets on the Nomad bridge, and then others joined in, and multisig did not stop these transactions, and $100 million was quickly emptied.
2. Relay technology is not absolutely safe
The risk with repeaters is also that when the network is heavily loaded, the repeater buffers may run out of storage, causing overflow and dropped frames. Also, if a repeater fails, it may affect neighboring subnets as well.
Multi-party secure computing is one of the safest cross-chain technologies
secondary title
Multi-party secure computing is more secure than multi-signature-based methods
Multi-party secure computing is more secure than the multi-signature mechanism because its verification method relies on machines rather than individual verifiers.Multi-party Secure Computing (MPC)
, which means that in the case of no trusted third party, multi-party collaborative computing can be performed. In MPC, mutually distrusting organizations attempt to jointly compute a function while keeping those inputs private. The two main properties of MPC are correctness and privacy. Correctness means that the output produced by the algorithm is correct. Privacy means that the secret input data held by one party will not be revealed to the other party.
first level title
Summarize
Summarize
Some people think that cross-chain smart contracts may upend the development model of dApps, but it will not change the fact that most blockchain networks are still isolated in nature. To solve the problem of blockchain islands, the bridge is a prerequisite, and the security of the bridge is the core.
first level title
About MixMarvel DAO Venture
About MixMarvel DAO Venture