Original title: "33 Privacy Public Chains: The Evolution of the Privacy Track"
Original author: Beep News
TL;DR
The privacy public chain provides solutions to the privacy problems existing in the public chain, and has three main features: programmability, interoperability, and ecological scalability;
Zero-knowledge proof technology, secure multi-party computing technology, etc. provide technical support for the privacy public chain;
The privacy public chain can hide sensitive information during user transactions, maximizing the protection of user privacy on the chain;
The overall privacy public chain ecology is in the early stage of development, and the valuation is relatively high.
Messari pointed out in a research report on Oasis Network that most Layer1 public chains currently have a lack of privacy.
The research paper writes: Layer 1 does not currently support privacy on its public network, as all records are recorded on the blockchain, and anyone can read its content. This raises privacy concerns due to the possibility of linking distributed ledger addresses to real identities.
The open and transparent nature of the blockchain allows anyone to view the user's transaction transfer records and on-chain activity records. Sensitive information of users may be easily obtained, and users face the dilemma of "streaking" in the Web3 world.
The privacy public chain provides users with privacy protection solutions. Through technologies such as zero-knowledge proof and secure multi-party computing, users can selectively hide sensitive information. Privacy public chains such as Oasis Network, Secret Network, and Aleo are constantly expanding their application scenarios, allowing privacy protection to cover more users.
The privacy public chain has three characteristics: programmability, interoperability, and ecological scalability. Based on the three characteristics, this article will introduce four development trends of the privacy public chain: the gradual enhancement of programmable features, cross-chain interoperability, expansion of application scenarios, and the continuous emergence of high-quality new public chains.
In order to gain a deeper understanding of the characteristics and development trends of privacy public chains, Beep News has sorted out 33 privacy public chains. These privacy public chains focus on two aspects: private computing networks and private transaction networks.
Representative projects of private computing networks include Oasis Network and PlatON, and representative projects of private transaction networks include Aleo, Aztec, Secret Network, and Nym.
Among these two categories, the number of privacy public chains is relatively large, but most public chain ecology is relatively poor, and the valuation of public chains is also problematic. In the long run, users' rigid demand for privacy protection may bring a large number of users and developers into the leading privacy public chain, enriching the public chain ecology, and users may consider early deployment of the privacy public chain ecology.
The value and technical core of the privacy public chain
(1) The privacy public chain meets the privacy protection needs of Web3 users
Blockchain technology improves the authenticity and transparency of data, but the transparency of user data is difficult to meet the data privacy requirements of Web3 users in some scenarios.
For example, the user's transaction records can be queried through the blockchain browser, and the data includes the sent data object, time, quantity, etc. Anyone can search for linked transactions and account balances based on wallet addresses.
The privacy public chain provides a solution for protecting user activity data on the chain. For example, Anoma allows users to freely choose any of their own assets for private transactions, and Iron Fish uses zero-knowledge proof technology to protect users' transaction information, mining information, and wallet information.
(2) Features of the privacy public chain
The privacy public chain has three characteristics: programmability, interoperability, and ecological scalability.
Programmability refers to the fact that private public chains can enable any developer or organization to build and extend truly private applications.
Taking Secret Network as an example, Secret Network's smart contracts (such as "Secret contracts") are private by default. Inputs, outputs, and state are encrypted and cannot be viewed by others unless they are granted access.
Interoperability means that the privacy public chain can enable two-way interaction between various blockchains, providing users with an extremely fast cross-chain experience with the L1 chain. Users can use the original cross-chain bridge of the privacy public chain to realize the cross-chain transfer of assets and protect their privacy during the transfer process.
Taking Secret Network as an example again, users can transfer assets through Secret Network’s native cross-chain bridge, and create a private version (Secret Token, such as sETH) based on their assets. Secret Token can be programmed like ERC-20 tokens, and in the application used in . At present, the cross-chain bridge of Secret Network has supported the asset transfer of Ethereum and Binance Chain.
Ecological scalability means that the ecology of the privacy public chain includes various DeFi, NFT, and chain game applications. Developers can build various Dapps based on the privacy public chain.
(3) Technical support of privacy public chain: zero-knowledge proof technology, secure multi-party computing, TEE
It is better to understand that the privacy public chain is split into "privacy + public chain". In order to make the public chain have privacy attributes, technologies such as zero-knowledge proof and secure multi-party computing are essential. This article will introduce three technologies that are widely used in mainstream privacy public chains: zero-knowledge proof technology, secure multi-party computing, and TEE (Trusted Execution Environment).
1. Zero-knowledge proof technology
The definition of zero-knowledge proof technology is: the prover (prover) can convince the verifier (verifier) that a certain assertion is correct without providing any useful information to the verifier (verifier).
Taking the transaction scenario as an example, the useful information of the transaction includes the parties involved in the transaction, the time of the transaction, the amount of assets transferred, etc. Zero-knowledge proof technology can ensure the privacy of this information and verify the validity of asset transfers on the chain without revealing transaction details.
There are three main types of zero-knowledge proof protocols, zkSNARK (simple non-interactive zero-knowledge proof), zkSTARK (simple zero-knowledge proof) and Bulletproof.
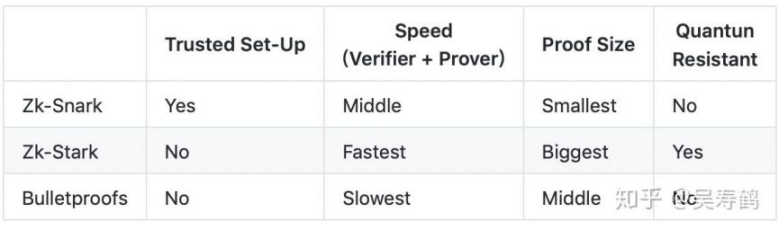
Wu Shouhe's "Introduction to Zero-Knowledge Proof" article introduces the differences between the three zero-knowledge proof protocols in trusted settings, verification time, size of generated zero-knowledge proof and resistance to quantum attacks. Taking zkSNARK, which is the most widely used in the privacy public chain, as an example, zkSNARK is the only one among the three protocols that requires trusted settings. The time required for verification is medium, and the generation of zero-knowledge proof is the smallest. It is most suitable for private public chains with expansion needs.
2. Secure Multi-Party Computation
HashKey is defined as follows when introducing secure multi-party computing: secure multi-party computing is in a distributed network and there is no trusted third party, multiple participating entities each hold a secret input, and hope to jointly complete the calculation of a function and To obtain the result, the premise is that each participating entity cannot know any input information of other participating entities except itself.
From this definition, three characteristics of secure multi-party computing can be derived: privacy, correctness, and decentralization.
Privacy: Each participating entity cannot know any input information of other participating entities except itself, ensuring the privacy of the input information of each participating entity.
Correctness: All parties involved in multi-party computing initiate computing tasks and perform collaborative computing by agreeing on a secure multi-party computing protocol, and the calculation data results are correct.
Decentralization: All participants have equal status, and there are no privileged participants or third parties, providing a decentralized computing model.
3. TEE (Trusted Execution Environment)
TEE is a separate "area" at the chip level. This area is responsible for providing a more secure place for code execution and data storage to ensure its confidentiality and tamper-proof.
The article "Analysis of TEE Technical Practice in Privacy Computing" pointed out that the most common specific application scenarios of TEE include: authentication and comparison of private identity information, cross-institutional joint modeling analysis of large-scale data, data asset ownership protection, and on-chain data confidentiality Computing, privacy protection of smart contracts, etc.
From the scenario of TEE technology, it can be seen that authentication and comparison of private identity information, confidential calculation of data on the chain, and privacy protection of smart contracts are highly compatible with the privacy public chain.
Privacy public chain ecology
The panorama of the Web3 privacy track ecology produced by Chain Catcher shows that the privacy track ecology is divided into four categories: privacy coins, privacy computing networks, privacy transaction networks, and privacy applications. The 33 privacy public chains counted by Beep News this time come from these four categories.
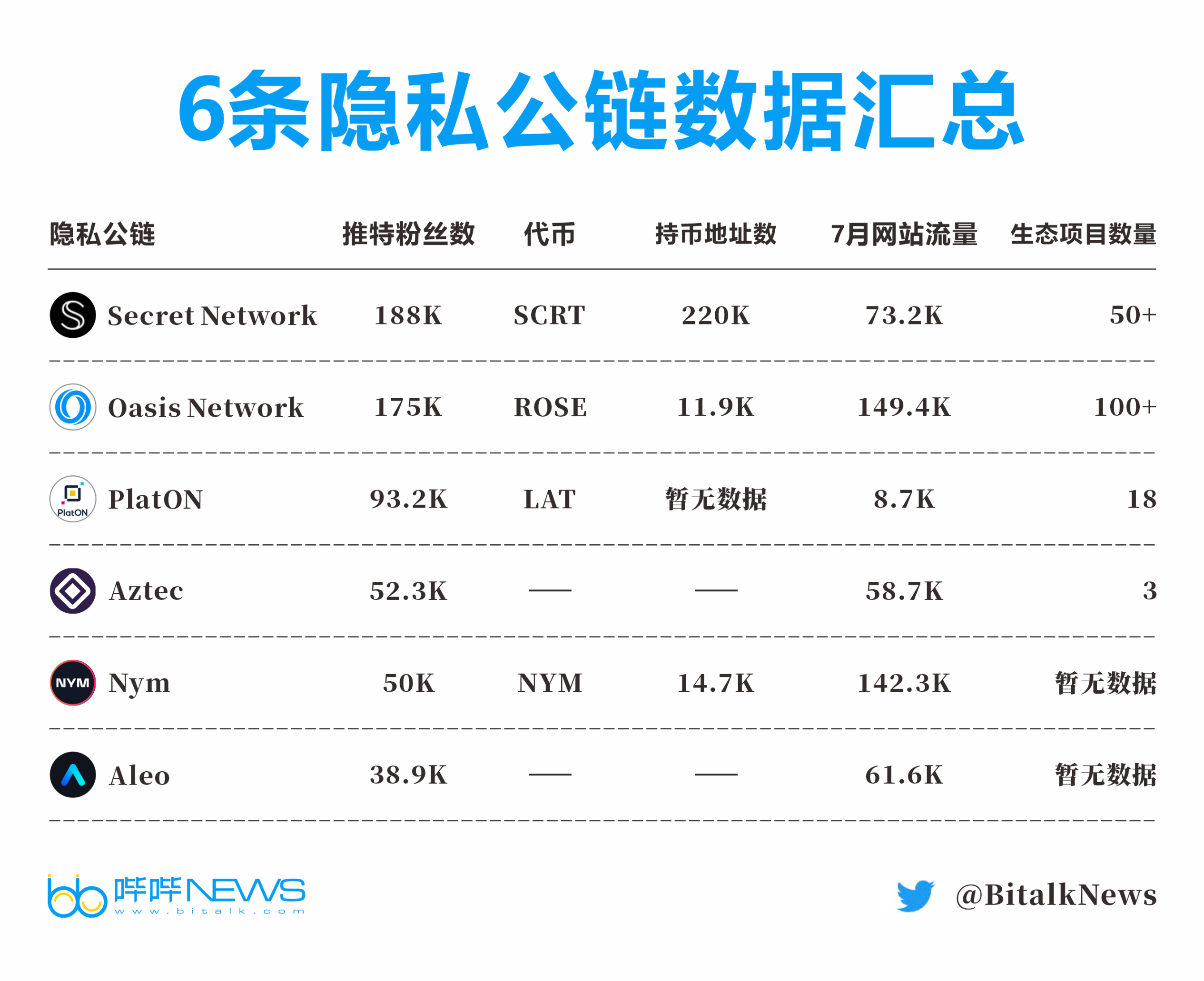
Among the privacy public chains, privacy coins appeared the earliest, and private computing networks and private transaction networks accounted for a large proportion. There are more Oasis and Findora ecological projects in the private computing network, and there are more Secret Network ecological projects in the private transaction network.

Among privacy coins, Monero (Monero) and Zcash rank the top two in terms of market capitalization, at $2.76 billion and $1.04 billion, respectively. Privacy coins were an early attempt to add privacy attributes to cryptocurrencies, with Monero officially launched in April 2014 and Zcash in 2016. The two can hide the transaction address and transaction amount during the transaction to ensure the privacy of the transaction process.
In the private public chain, the private computing network and the private transaction network account for a large proportion. This article will focus on the introduction of these two parts of the private public chain.
(1) Privacy Computing Network
In essence, privacy computing is to solve data service problems such as data circulation and data application under the premise of protecting data privacy. It is an effective way to solve data islands.
The most typical technology used in privacy computing public chains is Secure Multi-Party Computation (SMPC). The three characteristics of secure multi-party computing technology mentioned above: privacy, correctness, and decentralization. Under the premise of protecting privacy, multiple parties ensure the correctness of calculation data results through collaborative computing.
Typical projects in the privacy computing public chain include PlatON and Phala Network.
PlatON is a private AI computing network, which realizes private computing by superimposing homomorphic encryption (HE) and secure multi-party computing (MPC), ensuring the privacy of input data and computing logic itself.
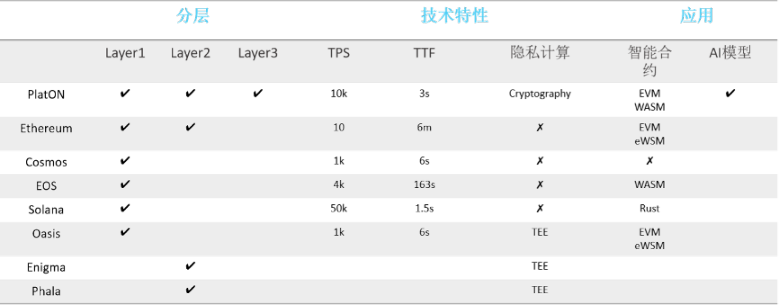
In the PlatON 2.0 white paper, PlatON uses a comparison chart to illustrate its positioning and competitive advantages, which highlights its privacy computing and AI model. PlatON focuses on building privacy-preserving computing networks and artificial intelligence (AI) collaboration networks.
Phala Network is a Polkadot ecological privacy computing parallel chain, which aims to build a distributed privacy computing cloud network composed of hundreds of thousands of miners around the world, and realize the privacy and trustlessness of cloud computing.
Phala Network uses the TEE-blockchain fusion architecture to implement private smart contracts. TEE technology allows users to become miners only with an Intel CPU.
There are a large number of Oasis and Findora ecological projects in the privacy computing network.
Currently, there are more than 40 DeFi applications deployed in the Oasis ecosystem, and the types of projects include DEX, lending, cross-chain bridges, and revenue agreements. In addition to DeFi, Oasis' NFT sector is also expanding rapidly.
Findora’s official website shows that its ecological project categories include cross-chain bridges, DAO, wallets, DEX, CEX, lending, NFT, etc. The project categories are relatively rich, and the number of ecological projects is close to 20.
(2) Privacy transaction network
The privacy transaction network, as the name implies, is to protect the transaction privacy of the user during the transaction process and hide the user transaction data (transaction object, time, amount of asset transfer, etc.).
Taking Aztec and Iron Fish as examples, Aztec is a Layer 2 scalable and programmable privacy protocol based on zkRollup, based on the underlying PLONK proof system, to realize anonymous transactions between accounts, and to achieve private interaction with DeFi projects through the grafting of gateway contracts . Iron Fish uses the PoW consensus mechanism and zero-knowledge proof technology to protect transaction information, mining information, and wallet information.
There are many new public chains in the private transaction network, including Aleo, Anoma, Aztec, Espresso Systems, etc. The ecology of the four public chains mentioned above is still in the early stage of development, and Aleo, Anoma, and Espresso Systems are in the testnet stage, but the four public chains have recently All have relatively large development progress.
Well-known investment banks are actively deploying privacy trading networks. Taking a16z and Sequoia Capital as examples, a16z participated in Aleo, Iron Fish, and Nym, and Sequoia Capital participated in Iron Fish and Espresso Systems.
6 privacy public chains
This chapter will introduce 6 public chains from the privacy computing network and privacy transaction network. Oasis Network and PlatON are introduced in the privacy computing network, and Aleo, Aztec, Secret Network and Nym are introduced in the privacy transaction network.
1 Introduction
1 Introduction
Oasis Network is a privacy-enabled, scalable Layer1 blockchain designed to power private, scalable DeFi.
Oasis Network has a design for Tokenized Data whereby users can earn rewards by staking their data in applications supported by Oasis Network.
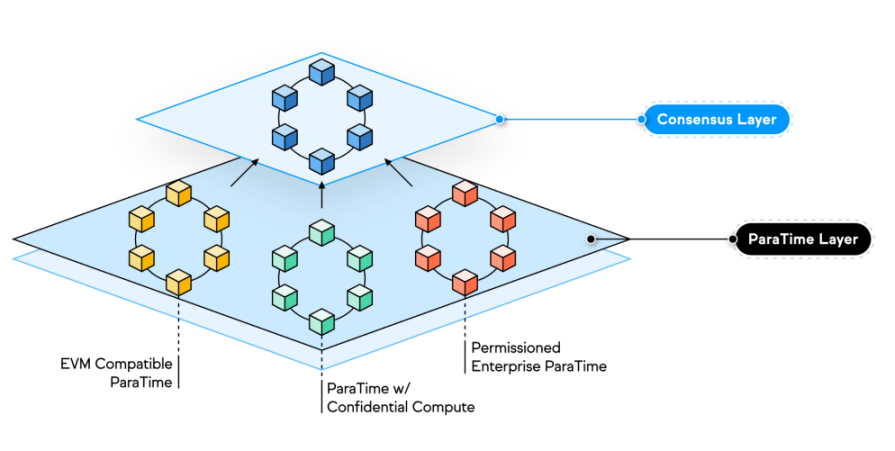
The scalability of Oasis Network is reflected in its layered architecture design, which is divided into consensus layer Consensus Layer and application layer (or computing layer) ParaTime Layer. The ParaTime Layer is the key to the operation of the Oasis Network, allowing multiple ParaTimes with different functions to work at the same time, improving its capacity for expansion.
2. Ecological application
2. Ecological application
The chart produced by HC Capital shows that the Oasis ecosystem is very large, including node operators, developer tools, wallets, DeFi applications, etc., and NFT is its emerging sector. is increasing rapidly.

ValleySwap, YuzuSwap, and Fountain Protocol are the top three applications in Oasis' ecological lock-up volume. ValleySwap and YuzuSwap are DEXs, and Fountain Protocol is a lending protocol. All three are native applications of the Oasis ecosystem.
As of June this year, the Oasis Ecosystem Development Fund has reached US$235 million. Oasis uses the Ecosystem Fund to attract developers to deploy applications in its ecosystem.
3. Latest progress
Recently, Oasis announced its development roadmap for the third and fourth quarters of this year. The roadmap shows that Oasis will promote the launch of the first EVM-compatible privacy ParaTime Sapphire mainnet, upgrade the mainnet to strengthen the existing privacy ParaTime Cipher, and realize WebAssembly (WASM)-based privacy smart contract functions.
4. Investment institutions: a16z, Polychain Capital, Binance Labs, etc.
1 Introduction
1 Introduction
PlatON is a private AI computing network. By superimposing homomorphic encryption and secure multi-party computing, it realizes private computing and ensures the privacy of input data and computing logic itself.
PlatON mentioned in its 2.0 white paper that PlatON plans to launch an infrastructure platform that can connect autonomous AI agents. The goal is to create a decentralized, secure and open source platform for ordinary users and provide AI solutions on this platform.
PlatON divides its development plan into three phases.
In the first stage, PlatON is positioned as a reliable data sharing privacy network connecting users and developers.
In the second phase, PlatON will establish a decentralized artificial intelligence (AI) marketplace, enabling asset sharing. At this stage, PlatON will apply artificial intelligence in all aspects.
2. Ecological application
2. Ecological application
There are a total of 18 ecological projects displayed on the PlatON official website, covering cross-chain bridges, oracles, developer tools, NFT, block browsers, etc.
3. Investment institutions:Hashkey Capital, Liang Xinjun, former CEO of Fosun Group, Hash Global Capital, etc.
1 Introduction
1 Introduction
Aleo is a programmable privacy public chain that uses zero-knowledge proof to solve privacy problems, and uses zero-knowledge proof technology to hide interaction details such as participants, smart contracts, and amounts.
Aleo's technical core lies in three aspects: Zexe architecture, Leo programming language and zkCloud.
The Zexe architecture is its solution for zero-knowledge proofs. By computing offline first, and then generating online transactions that can prove that the calculations are correct without disclosing the details of the calculations, the transactions can be verified by anyone in a very short time.
Leo is a Rust-inspired, statically typed programming language purpose-built for writing private applications, designed to remove as much cryptography knowledge as possible.
zkCloud adopts a peer-to-peer, decentralized privacy computing model, in which shielded identities can interact directly (such as asset transfers) or programmatically (via smart contracts). Moreover, zkCloud performs privacy calculations off-chain, and only needs to submit a shielded transaction at the end of the calculation, which improves the scalability of the network.
2. Latest progress
Aleo runs Testnet 3 between August-October. The first phase (August) is for developers, who can start writing, deploying, and executing programs. The second phase (September) is for provers who solve Coinbase puzzles (PoSW) to earn credits. The third phase (October) is for validators, and validators get rewards for producing blocks.
Aleo will distribute 25 million Aleo Points (ALEO) to the developer, prover, and validator communities in 3 phases of Testnet 3.
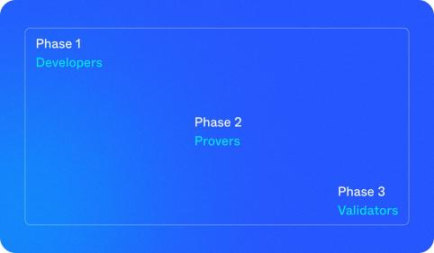
The Aleo team plans to launch the mainnet in the fourth quarter of this year.
3. Investment institutions:a16z, Softbank, Tiger Global, etc.
1 Introduction
1 Introduction
Aztec is a Layer2 scalable and programmable privacy protocol based on zkRollup, which focuses on protecting user privacy during user transactions.
Aztec Network has two main functions.
Guarantee privacy during user interaction;
Users can provide programmable privacy contracts through Aztec to build completely private applications.
The implementation method of ensuring the privacy of interactions: Aztec Network has developed the application zk.money, which Ethereum users can use to send and receive tokens anonymously to protect their own transaction data.
Programmable privacy contracts: The Aztec team invented Plonk, a general-purpose ZK-SNARK technology, to provide zero-knowledge proof technical support for privacy contracts. Users can implement programmable privacy protection contracts in Plonk Rollup through its programming language Noir, and develop applications according to different privacy requirements and application scenarios.
2. Application
Aztec develops two applications in-house: zk.money and Aztec Connect.
zk.money: A Layer 2 private payment program that Ethereum users can use to send and receive tokens anonymously.
Aztec Connect: A private cross-chain bridge that allows users to interact with DeFi applications on the Ethereum chain in a private and low-Gas manner.
3. Integrated application
According to Aztec's official website, there are currently three integrated applications: the lending application Aave, the Staking protocol Lido, and the fixed-rate lending protocol Element Finance.
Applications that are planned to be integrated in the future include the lending protocol Compound, the lending protocol Liquidity, the stablecoin protocol mStable, etc.
4. Investment institutions: Paradigm, IOSG Ventures, Variant Fund, Nascent, Vitalik Buterin, etc.
1 Introduction
1 Introduction
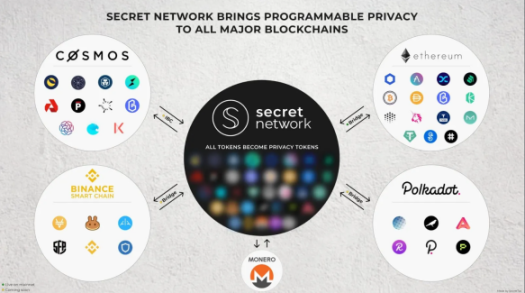
Secret Network is a Layer1 blockchain built using Cosmos SDK and Tendermint BFT. It is a privacy-centric smart contract platform.
Secret Network aims to bring privacy to every blockchain application, including DeFi, gaming, DAO, healthcare, insurance, commerce, payment systems, and more.
2. Ecological application
2. Ecological application
According to the Secret Network ecological map released in April this year, the categories of Secret Network ecological projects cover cross-chain bridges, asset management, DEX, wallets, NFT, developer tools, etc., and the number exceeds 50.
According to DeFillama data, the top two locked positions on the Secret Network chain are the cross-chain DeFi protocol Sienna Network and the decentralized trading platform SecretSwap.
As of August 26, the locked positions of the two were 7.73 million US dollars and 3.7 million US dollars respectively.

3. Investment institutions:Fenbushi Capital, Dragonfly, Hashed, etc.
1 Introduction
1 Introduction
Nym is a "full-stack" privacy system. Developers can bind applications to the Nym system through the Nym hybrid network, and protect users through Nym private credentials at the application layer.
Nym creates private Web3 application development programs for users by enabling privacy blockchains and based on the Mixnet privacy protocol.
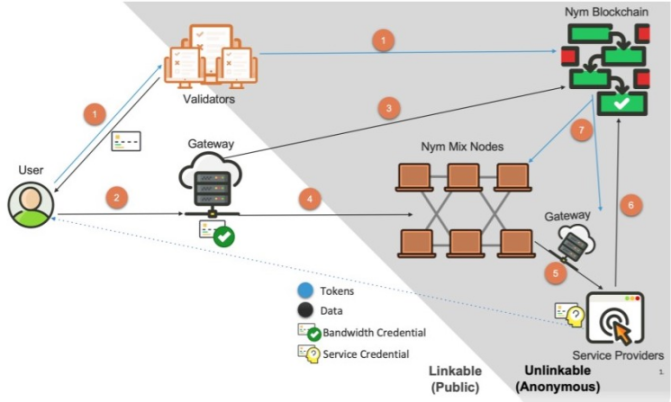
Nym has 5 types of network participants: end users, mixing nodes, gateways, validators, service providers.
End users: all available service users who choose to communicate privately;
Hybrid nodes: Hybrid nodes provide community privacy to end users through anonymous data packaging;
Gateway: The gateway keeps Nym Mixnet in a non-free state. Participants may choose to use the same gateway to run data, disperse into various gateways to run, or choose different gateways every day;
Verifier: maintain the Nym cross-chain network, distribute and notify all information within the network;
Service Providers: Send and receive information through private communication between Nym Network and users.
2. Roadmap
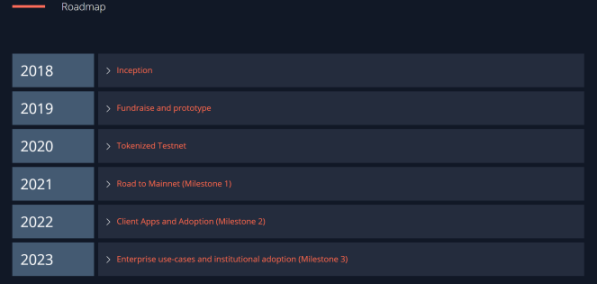
The Nym roadmap shows that it will usher in two milestones in 2022 and 2023. The client app will be launched in 2022 to achieve large-scale adoption. Enterprise users will appear in 2023 and institutional-level adoption will be achieved.
The latest developments in the network: Nym released two updated versions, v1.0.0 and v1.0.1, in May this year.
3. Investment institutions:a16z, Polychain, NGC Ventures, HashKey Capital, Distributed Capital, etc.
The development trend of privacy public chain
Combined with the privacy public chain mentioned above, this article will discuss four development trends of the privacy public chain:
The programmable features of the privacy public chain are gradually strengthened;
Cross-chain interoperability;
Application scenario expansion;
High-quality new public chains continue to emerge.
(1) The programmable features of the privacy public chain are gradually strengthened
As mentioned above, programmability refers to the privacy public chain can enable any developer or organization to build and expand truly private applications. Aleo, Aztec, Secret Network, Oasis, etc. introduced above are all programmable. Zero-knowledge proof technology and specially developed programming languages help developers build privacy-friendly applications based on these platforms.
Programmable privacy public chain is the general trend of the development of privacy public chain, which is caused by the needs of privacy public chain, users and developers.
The development of a new privacy public chain requires ecological applications and new users, which requires a large number of developers and users. The programmable privacy public chain just meets the privacy requirements of users and developers.
Users need to hide metadata (transaction object, time, transfer amount, etc.) during transactions, and developers need to design applications according to the needs of users. The programmable privacy public chain provides a development platform for them. Developers use privacy The programming language provided by the public chain can be used to develop applications.
(2) Cross-chain interoperability
Cross-chain interoperability is a way to break data islands. The private public chain is connected to other public chains through the native cross-chain bridge application, and users can also get a private experience when passing through the cross-chain bridge.
As mentioned above, Aztec and Secret Network use privacy cross-chain bridges Aztec Connect and sToken respectively to allow users to obtain privacy experience in cross-chain transactions.
The cross-chain interoperability trend of the privacy public chain should be cross-chain + privacy. Cross-chain means that users can transfer assets between chains through the cross-chain bridge, introducing new assets to the privacy public chain.
Privacy is to provide users with a privacy experience during cross-chain transfers, such as hiding the user's cross-chain specific information during cross-chain transfers, and users hiding their specific information when interacting with other non-private public chains.
(3) Expansion of application scenarios
The application scenario expansion of the privacy public chain is reflected in two aspects: the fields involved, and the types of assets traded by users.
Privacy public chains focus on serving all scenarios in the encryption field. For example, Secret Network aims to bring privacy to every blockchain application, including DeFi, games, DAO, medical care, insurance, commerce, payment systems, etc.
As regulatory agencies gradually strengthen their scrutiny of the encryption field, privacy public chains must protect user privacy under the premise of compliance, which means that the intersection between privacy public chains and traditional finance is gradually deepening.
The range of asset types that users trade on the privacy public chain will be extended to all types of encrypted assets, not limited to assets on a certain chain or certain supported chains.
Taking Anoma as an example, Anoma has created a payment system that allows any digital asset to be directly used as a means of payment, enabling everyone to freely choose the digital asset or asset combination used in payment transactions. These digital assets include assets created on Anoma, other on-chain assets and stablecoins transferred to Anoma through cross-chain bridges.
(4) High-quality new public chains continue to emerge
High-quality new public chain projects on the privacy track continue to emerge. Oasis, PlatON, and Findora will gradually enter the public eye in 2020. In 2022, Aleo, Anoma, and Espresso Systems, the three projects that are on the testnet The heat is soaring, and Aztec has been attracting attention for filling the gap in Layer 2 privacy.
The status of the privacy public chain in the Web3 era is self-evident. Users' demand for hiding sensitive information makes the privacy public chain and privacy applications a rigid need for Web3. The programming language and relatively complete development tools provided by the privacy public chain attract developers. Participate in building.
The demand for privacy projects in the encryption industry will give birth to more new high-quality privacy public chains, and these new privacy public chains may appear in every round of new public chain narratives thereafter.
Privacy public chain network value and investment prospects
To judge the value of the network, the indicator used in this article is market value/TVL (Mcap/TVL). This basic ratio represents the valuation method of the network relative to the locked value. A large value indicates a high valuation. It is mentioned above that Oasis and Secret Network have good ecological development. This article will take Oasis and Secret Network as examples.
As of August 26, the market cap of Oasis tokens was $342 million, and the TVL was $31.62 million, with a market cap/TVL ratio of about 11.
Secret Network tokens have a market cap of $226 million and a TVL of $11.36 million, giving a market cap/TVL ratio of about 20.
Judging from the TVL data of the two, the lock-up volume of DeFi applications in the Oasis and Secret Network ecosystems is not high, and the market value/TVL exceeds 10, indicating that the valuation is relatively high.
From August 1st to August 26th, the market value of Oasis tokens decreased by 20.9%, and the TVL on the Oasis chain decreased by 5.5%.
The market value of Secret Network tokens increased by 14.6%, and the TVL on the Secret Network chain increased by 3.1%.
It can be seen that from August 1 to August 26, Oasis' Mcap/TVL ratio decreased, while Secret Network's Mcap/TVL ratio increased. And the change range of TVL of the two is smaller than the change range of market value, which has something to do with the lack of DeFi applications in the ecosystem.
To reduce their Mcap/TVL indicators, the two need to continue to enrich the applications within the ecology and improve the TVL of the ecology applications.
Referring to Solana and Avalanche, the ratio of this indicator is 8 for Solana and 3.1 for Avalanche.
Projects that have not issued coins in the privacy public chain also have relatively high valuations. After completing the B round of financing, Aleo’s valuation is 1.45 billion US dollars. Compared with the two analyzed in this article, Aleo’s valuation has increased after it launched the main network Space is in doubt.
Although the valuation is relatively high, the overall privacy public chain is worth investing in. The reason is based on needs and ecology.
From the perspective of demand, users' demand for privacy protection will inevitably attract a large number of users and developers, and the entire track is very active.
Reference article:
Reference article:
1. "Panoramic interpretation of the status quo, evolution logic and typical players of the Web3 privacy track" by Chain Catcher
2. "Messari Research Report: Panoramic Interpretation of the Oasis Network, Building a Responsible Data Economy" by Oasis Chinese Channel
3. "Comprehensive Interpretation of Aztec: How to Bring Privacy DeFi into L2?" 》by Chain Tea House
4. "Privacy Public Chain Ecological Inventory: It is generally in the early pioneering state, and the ecological development is slow" by PANews
5. "Secret Network: What is a Programmable Privacy Public Chain" by Rhythm BlockBeats
Original link