According to data released by Chainalysis, the loss caused by cross-chain bridge looting incidents in 2022 alone will reach as much as US$2 billion. Cross-chain bridge security issues emerge in endlessly, and every attack incident has aroused the attention of the industry. Regarding product security issues, XChang, the security director of the cross-chain bridge project Multichain, recently disclosed in detail the product security mechanism of the project, hoping to take this opportunity to share the experience of Multichain with friends in the industry and observers who are concerned about the ecology of cross-chain bridges .
According to XChang, Multichain's security strategy is divided into three stages based on the time point of the attack event, namely: before the occurrence, when the occurrence occurs, and after the occurrence. Each stage has corresponding coping steps and strategies.
1. Before it happens:
The project eliminates any security risks through internal and external audits. At the same time, experts in the industry are also mobilized through bug bounties to help find loopholes and avoid losses. In addition, Multichain also hopes to make another preventive check on product security through the upcoming MultiDAO. In addition, Multichain also uses the keyword public opinion monitoring of major media platforms to observe the dynamics related to cross-chain bridge security issues in the industry, conduct introspection from it, and monitor whether the impact of other events affects Multichain's assets. For large-amount transactions, Multichain has also implemented cross-chain amount limits and chain capital flow and total limits to avoid repeating the same mistakes as Horizon.

2. When it occurs:
When an attack occurs, the key is to sound the alarm bell in time so that the platform can act quickly. Multichain is set up to detect Watchdogs, which can respond to abnormal phenomena in a timely manner. At the same time, the project also mobilizes the power of DAO to issue rewards to members who discover loopholes and report abnormal phenomena to the platform in a timely manner.
3. After the occurrence:
Mutichain will suspend the use of the product to deal with the hacking incident by stopping the loss first and then repairing it. At the same time, the project also conducts exercises and sets a pause function on the smart contract. In addition, Multichain also appropriated part of the project profits as a security fund to compensate users for losses in similar incidents.
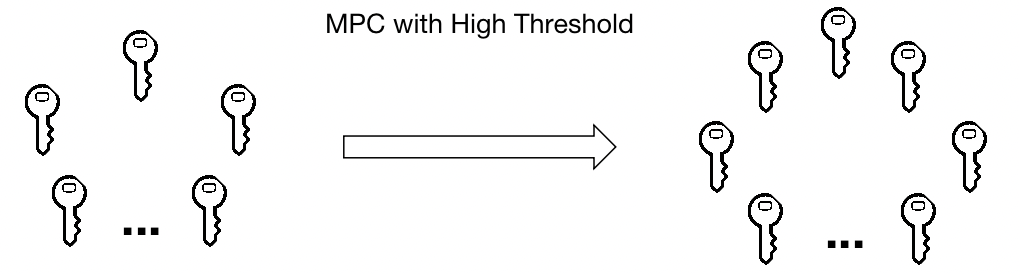
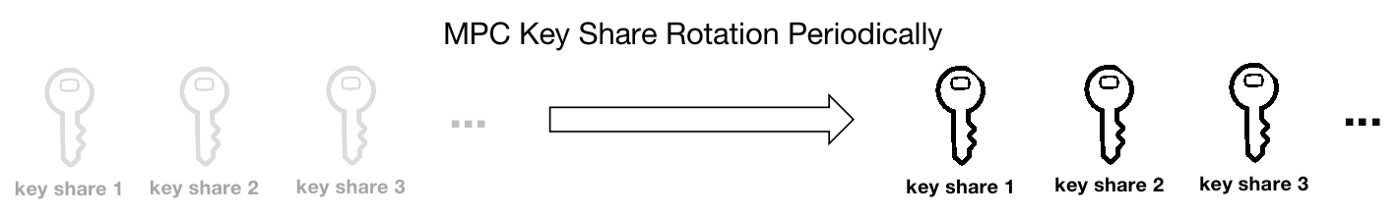
ChangX also clarified that the characteristics of multi-party secure computing (MPC) can ensure stronger decentralization and cost control, and MPC private key fragments will be regularly updated and invalidated to further prevent hacking. At the same time, Multichain is also cooperating with network infrastructure providers to create a more secure product environment. As for Multichain's upcoming MPC+HSM solution, it can ensure that hackers are still prevented from obtaining private key shards even if the server is attacked.
This article is reproduced from
https://medium.com/multichainorg/multichain-security-policy-detailed-disclosure-3c38360bfd0b