Solana is going through a massive security incident.

The early warning was sounded by the NFT market Magic Eden. This morning, Magic Eden issued a warning saying that there seems to be a widespread SOL vulnerability that can drain the wallet assets of the entire ecosystem. Magic Eden reminds users to perform the following settings to protect personal assets: enter the Phantom wallet settings page; click the trusted Apps (Trusted Apps); revoke permission for any suspicious links.
However, just when everyone thought that this was just a relatively common misauthorization incident, many security researchers voiced that the problem did not seem to be that simple.
Decaf developer @JuanRdBO tweeted and pointed the finger at Phantom, the largest wallet in the Solana ecosystem, saying that this is not a problem about "trusted applications". If the user ever interacted with DeJBGdMFa1uynnnKiwrVioatTuHmNLpyFKnmB5kaFdzQ (which Phantom interacted with when creating the wallet), the wallet was compromised.
Subsequently, the Phantom official announcement stated: "We are working closely with other teams to clarify the Solana vulnerability issue. At present, the team does not believe that this is a Phantom-specific issue. Once we collect more information, we will release an update. .”
According to the current situation, Phantom should indeed not be the only wallet affected by this incident. The well-known developer @0xfoobar tweeted that in addition to Phantom, Slope wallet users have also reported theft; Cinneamhain Ventures partner Adam Cochran also said that a Slope user told him that the incident even affected his Ethereum address ( Use TrustWallet wallet).
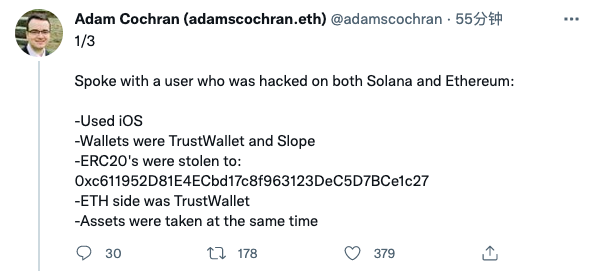
In this regard, Slope Wallet responded: "We are actively working to resolve this issue as soon as possible and do our best to rectify it. We are currently working with Solana Labs and other Solana-based protocols and teams to identify the issue and correct it. We will Update progress again in 30 minutes.
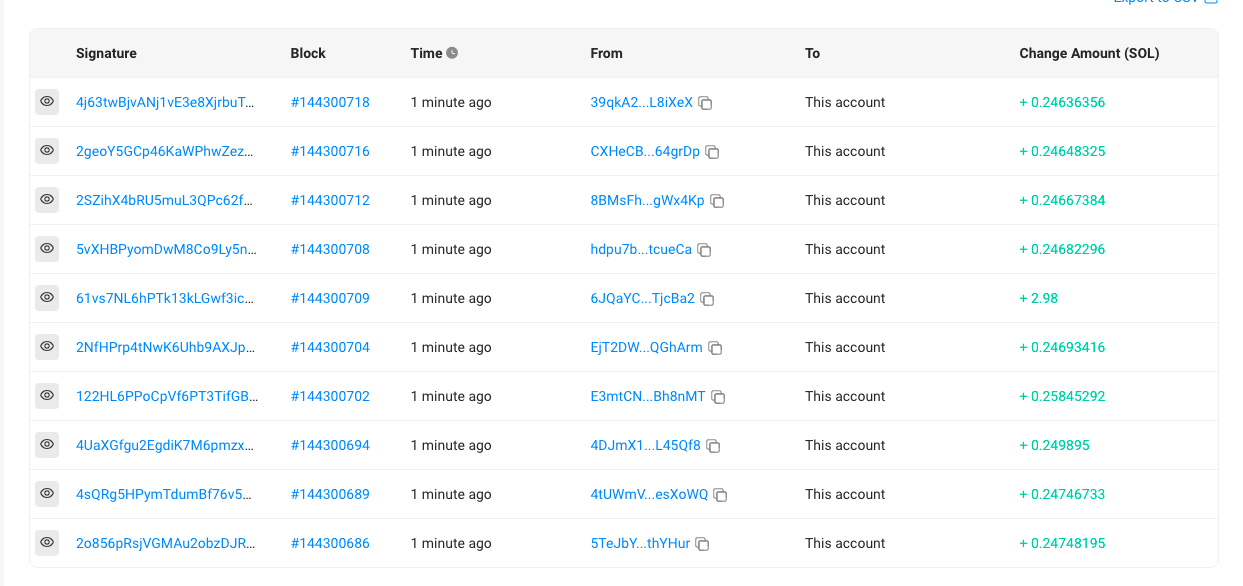
@0xfoobar also added on the incident that hackers are currently stealing a large amount of SOL and other SPL standard tokens (such as USDC) in the affected wallets, even wallets that have not been active for 6 months are not immune.
According to Watcher.Guru, more than 8,000 addresses have been affected so far. Currently confirmed hacker addresses include: Htp9MGP8Tig923ZFY7Qf2zzbMUmYneFRAhSp7vSg4wxV; CEzN7mqP9xoxn2HdyW6fjEJ73t7qaX9Rp2zyS6hb3iEu; 5WwBYgQG6BdErM2nNNyUmQXfcUnB68b6ke sxBywh1J3n; GeEccGJ9BEzVbVor1njkBCCiqXJbXVeDHaXDCrBDbmuy.
As for the cause of the attack, all parties have temporarily stated that they have not yet been ascertained, but @0xfoobar reminds all Solana ecological users,If you have the conditions, you can transfer the assets to the hardware wallet as soon as possible. If there is no condition, you can transfer the assets to the centralized exchange with good reputation.
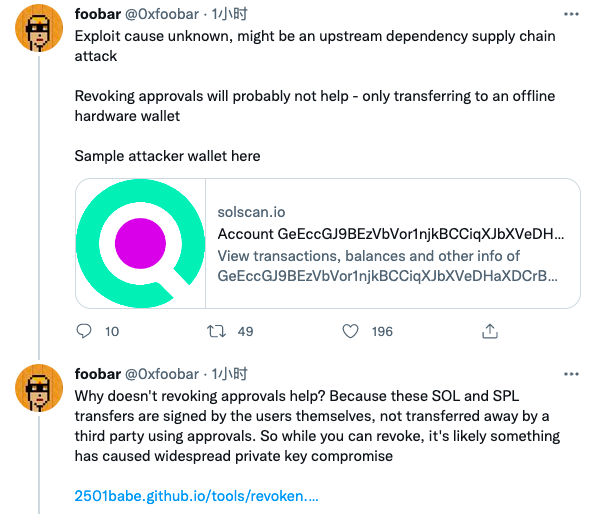
The reason why you need to do this,Regarding the whole incident, Solana’s current official response is: “Engineers from multiple ecosystems are investigating this large-scale wallet theft with the help of several security companies. There is currently no evidence that hardware wallets will be affected. Follow-up information will be announced as soon as the investigation progresses.”
Regarding the whole incident, Solana’s current official response is: “Engineers from multiple ecosystems are investigating this large-scale wallet theft with the help of several security companies. There is currently no evidence that hardware wallets will be affected. Follow-up information will be announced as soon as the investigation progresses.”
Since the cause of the incident has not yet been identified, Odaily will pay close attention to the development of the situation, and will update it below this article if there are important trends.
————
10:55 update:
The SlowMist security team conducted a follow-up analysis of this incident and said that from the perspective of transaction characteristics, the attacker signed and transferred the account without using the attack contract, and the preliminary judgment was that the private key was leaked. Many victims reported that they have used a variety of different wallets, mainly mobile wallets. We speculate that the problem may be in the software supply chain. Before new evidence is discovered, we recommend that users transfer the hot wallet tokens to a relatively safe location such as a hardware wallet or a well-known exchange, and wait for the event analysis results.
11:30 update:
Ava Labs founder Emin Gün Sirer tweeted that because the attack is still in progress, there is a lot of misinformation and speculation. Since the transaction is signed correctly, the attacker has likely gained access to the private key. One possible avenue is a supply chain attack, where the JS library is hacked and leaks (steals) the user's private key. The affected wallets appear to have been created within the past 9 months, but there have been reports of newly created wallets being affected as well. Downtime is currently useless, and the attack will resume when the chain is restored.
11:35 UPDATE:
Magic Eden stated that after further investigation, the team recommends that users also do the following to protect their personal assets:
1. Create a new wallet with a new mnemonic;
2. Transfer all NFTs and liquid cryptocurrencies to a new wallet, or more safely put all assets into a cold wallet.
11:44 UPDATE:
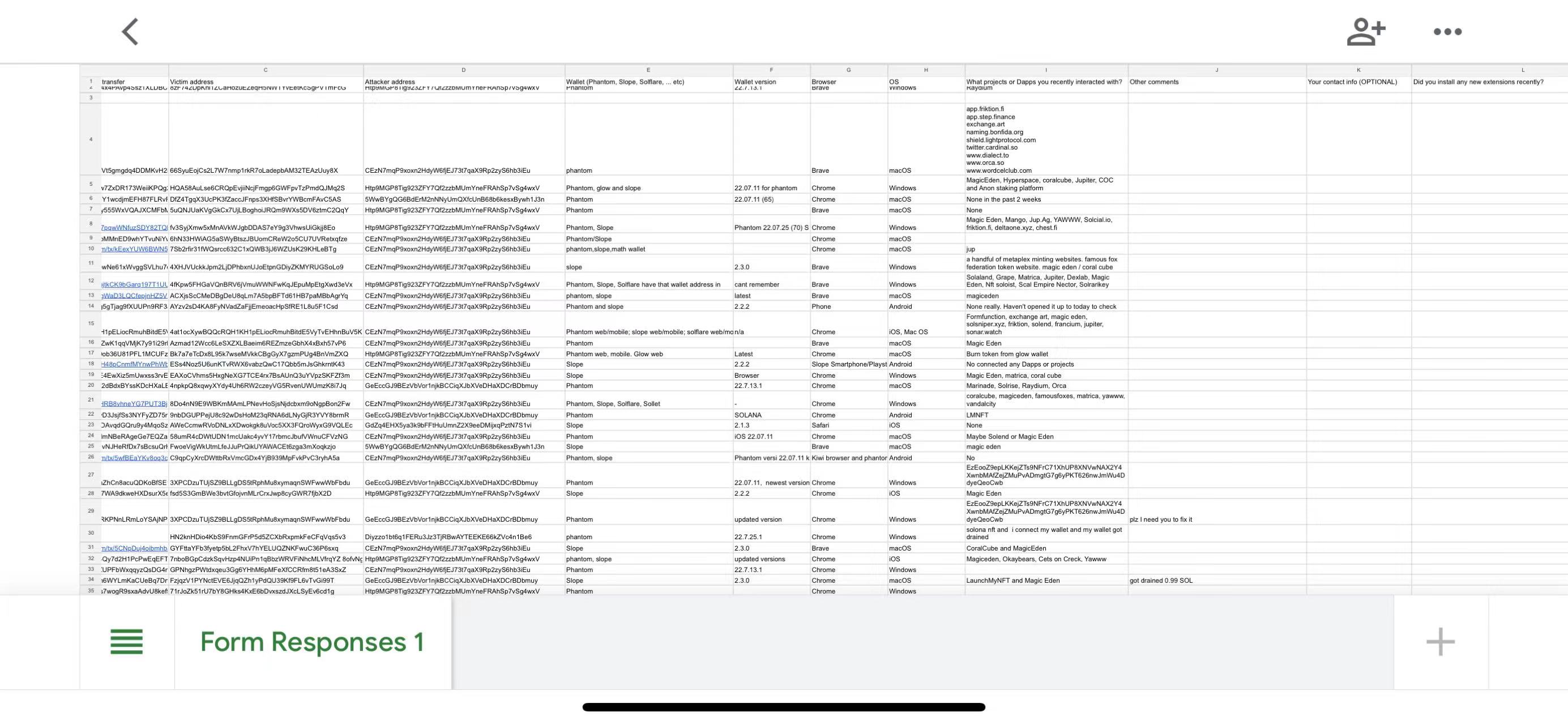
Solana ecological developers revealed to Odaily that Solana is currently convening Phantom, Slope and other ecological core teams, and is comparing and checking victim addresses and interactive application records one by one. It is still impossible to determine the specific cause of the vulnerability.
Update at 13:35:
Solana Status tweeted again that engineers are currently working with multiple security researchers and ecosystem teams to determine the root cause of the exploit, which is still unclear. There is no evidence that hardware wallets are affected, users are strongly advised to use hardware wallets, and do not reuse the mnemonic phrase on the hardware wallet, create a new mnemonic phrase. Stolen wallets should be considered damaged and discarded.
Update at 17:07:
Solana Labs co-founder @aeyakovenko tweeted that according to the analysis of the attack, it seems that the iOS supply chain has been attacked, and multiple trusted wallets that only received SOL and had no other interaction were affected. import the private key to iOS.
At the same time, he said that it's just that all the confirmed information shows that it is an iOS device, but it may also be because of its popularity.
Update at 8:30 on August 4th:
1. Solana Status tweeted that after investigation by developers, ecological teams, and security auditors, the affected addresses seem to have been created in the Slope wallet application, imported wallet addresses, or used the application. The exact details are still under investigation, and it may be that private key information was inadvertently transferred to the application monitoring program.
2. Phantom also tweeted, "There is reason to believe that the reported vulnerability is due to the complexity associated with importing and exporting accounts between Slope, and is still actively working to determine if there are other vulnerabilities that lead to this incident. If there are Phantom users Other wallets are also installed, we recommend you try transferring your assets to a new non-Slope wallet with a new seed phrase."
3. In response to this matter, Slope issued an announcement in response, saying that according to the current situation, many Slope wallets have been compromised, and the wallets of many Slope employees and founders have also been stolen. Slope has a few hypotheses about the cause of the attack, but has not yet confirmed it. Slope is actively conducting internal investigations and audits; working with top-tier external security and audit teams; and working with developers, security experts, and protocols across the ecosystem in an effort to identify and correct these issues.
Slope recommends that all users take the following action: Create a new, separate seed phrase wallet and transfer all assets to the new wallet. Also, it is not recommended to use the same seed phrase on a new wallet as on Slope. Hardware wallets are still safe.