Original Author: Glaze, Fundamental Labs
Original compilation: Aididiao
The Ethereum merger is underway, but the launch of the proof-of-stake (PoS) mechanism has been delayed time and time again.
The merger of Ethereum refers to the conversion of the existing proof-of-work (PoW) consensus mechanism into a proof-of-stake (PoS) consensus mechanism. The rewards for mining will be determined by the number of participants' pledges and digital assets, rather than electricity and resources. Intensive computing power decision. In order to ensure the smooth merger of Ethereum, miners turned to proof of equity, and Ethereum decided to increase the bomb difficulty mechanism to ensure a smoother merger of Ethereum.
After the difficulty bomb mechanism is set, the mining difficulty of the PoW network will increase exponentially over time, thereby reducing the miners' ETH rewards. Finally, the PoW network stops producing blocks, and all miners can only switch to the PoS network.
source:
source:Etherscan
For a long time, Ethereum's high Gas fees and slow network transaction speed have been criticized by users, and the PoW consensus mechanism can help Ethereum solve these problems.
This article will explain the history of the PoS consensus mechanism and the difficulties encountered in the merger of Ethereum.
Quickly understand the new consensus mechanism
There are many nodes on each blockchain network, and the consensus mechanism coordinates these nodes so that different nodes can reach a consensus on the new blocks generated. The consensus mechanism is the key to the smooth and self-operation of the distributed network.
Consensus mechanisms are often complex, and to quickly understand a new consensus mechanism, you only need to answer:
Who proposes new blocks?
If there is a fork in the blockchain, what are the factors that determine who is the main chain?
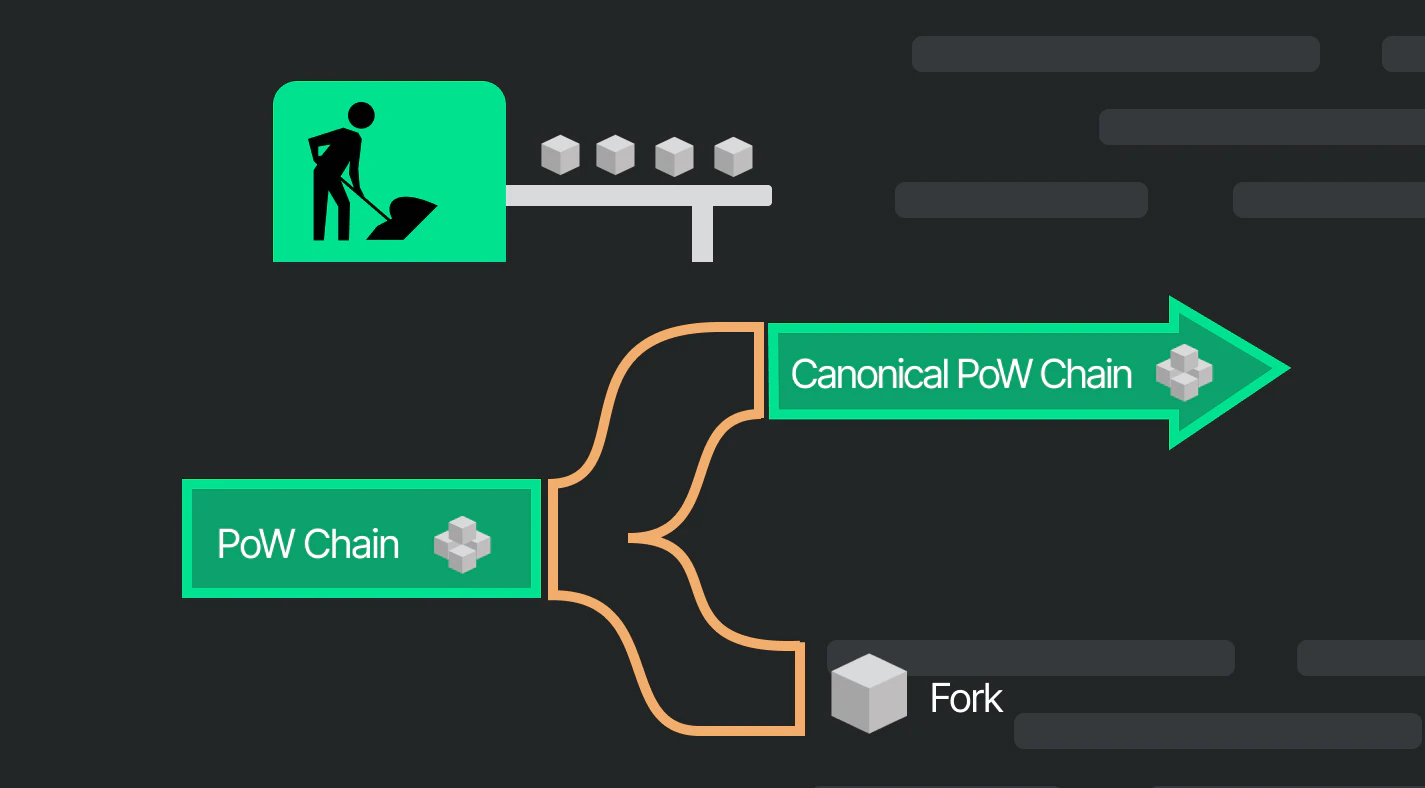
Overview of PoW consensus mechanism
In the PoW consensus mechanism, miners repeatedly try to solve a mathematical problem based on a hashing algorithm. The miner who solves it first will get the right to bookkeeping and propose a new block. If the blockchain forks, the longest forked chain will become the main chain. If someone wants to manipulate the blockchain, the attacker needs to reach at least 51% of the computing power. PoW network mining requires power resources, and at the same time has high requirements for hardware, and there is a certain cost threshold. The rewards obtained by mining are proportional to their computing power.
Compared to PoS, PoW is relatively simple. Because PoW does not need to involve issues such as random numbers, and PoS needs to use random numbers to randomly select block proposers.
Detailed explanation of PoS consensus mechanism
During the merger process of Ethereum, more nodes are encouraged to join the network in a decentralized manner, so more complex protocols are needed to support peer-to-peer communication of thousands of nodes and ensure the normal operation of the network.
The PoS consensus mechanism is the proof-of-stake mechanism, and nodes need to pledge native tokens on the network. The more tokens staked, the more likely a node is to produce a block. The PoS consensus mechanism does not require high hardware requirements, but requires funds to complete the pledge. If a node cheats, the network will immediately cut the tokens pledged by the node. Since nodes do not need to spend power resources and use high-end hardware equipment, PoS network has sustainability, more efficient response mechanism, higher TPS and security, so most networks will adopt PoS consensus mechanism.
Two Phases of PoS
PoS has gone through two stages of development, PoS 1.0 is a consensus mechanism based on blockchain, and PoS 2.0 is a consensus mechanism based on BFT (Byzantine Fault Tolerance).
PoS 1.0 consensus mechanisms: PeerCoin, NextCoin, BlackCoin and Ethereum Serenity.
PoS 2.0 consensus mechanism: Projects such as Ethereum 2.0, Tendermint, and Cosmos.
PoS 1.0
In the PoS 1.0 phase, most PoS mechanisms:
Node Pledge Tokens
Randomly select a node to generate a new block, and the probability of a node generating a new block is proportional to the number of pledged tokens
The most important thing in this process is the production of random numbers. If the generation of random numbers is based on timestamp and hash algorithm, then the node may increase the probability of being re-elected as the block proposer by affecting the random number production. probability, resulting in a new block.
attack vector
Attack vectors allow hackers to gain access to computers or web servers to deliver payloads or malicious results. Attack vectors enable hackers to exploit system vulnerabilities, potentially resulting in theft of assets. Common attack vectors are:
Staking grinding: Block proposers perform some computation or take other steps in an attempt to bias the randomness in their favor in order to gain more chances to generate blocks.
Nothing at stake: In a PoS network, nodes do not need additional opportunity costs for mining, so they will mine on each competing branch to maximize their rewards. But this is detrimental to the stability of the network.
Long-range attack: Early miners may trace back to the early version of the blockchain, which is easy to cause forks.
PoS 2.0
PoS 2.0 uses BFT, and its goal is to reach consensus among different nodes.
Among all nodes, the master node is selected by a random algorithm, and proposals and communications can be made. There are malicious nodes among other nodes, that is, Byzantine nodes. In order to prevent the transmission of real information and the achievement of consensus, Byzantine nodes will send inconsistent information to each node, usually cheating in this way:
no results returned
respond with wrong result
responding with intentionally misleading results
respond with inconsistent information
Except for Byzantine nodes, all other nodes are honest nodes, and the most difficult scenario master node is a Byzantine node.
BFT has other limitations:
Nodes can only communicate peer to peer
Nodes keep a log of sent messages
Point-to-point communication causes different nodes to have different views, and the nodes are not in the global synchronization state. For example, when node A finds 3 new blocks, node B can only see 1 new block.
The main purpose of BFT is that after the main node proposes, every node except the Byzantine node can reach an agreement, and the secondary goal is to discover the Byzantine node.
Introduction to BFT algorithm
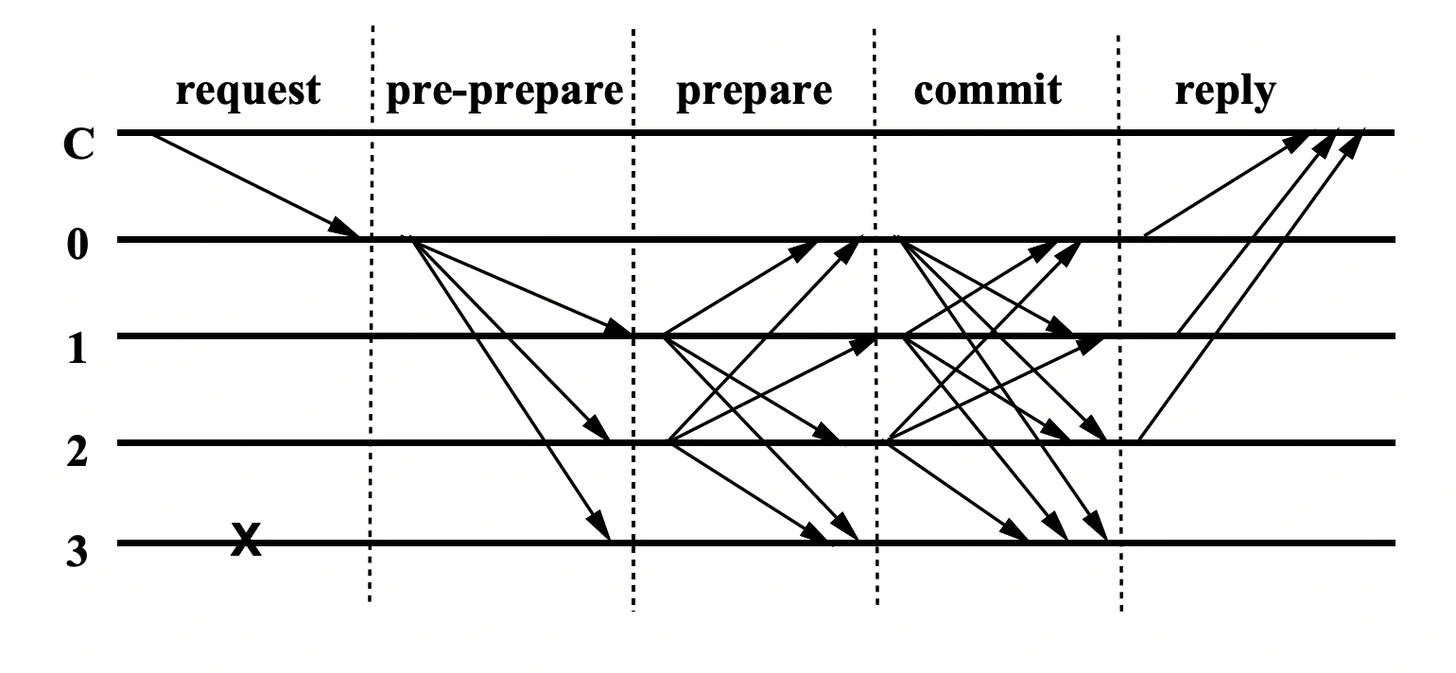
Now the BFT algorithm usually adopts multiple rounds of voting to ensure that each node knows whether the proposal is approved by more than two-thirds of the nodes.
Each round of voting has four steps:
The client sends a request to the master node
The master node forwards requests to all nodes
The node returns the execution result to the master node
After getting more than two-thirds of the nodes with the same results, the master node will feed back the results to the client
The figure below shows the 5 nodes of the execution process. Where C is the client, 0 is the master node, and 3 is the Byzantine node.
During the prepare and commit phases, it is necessary to ensure synchronization between different nodes.
Tendermint has the following limitations:
In point-to-point communication, the number of network nodes cannot exceed 100
Point-to-point communication requires complex design
Execution delay. The node first decides on the new block, and then executes all the information of the new block. While individual transaction executions work fine, executing all transactions at once can lead to double spending issues.
Editor's note: Tendermint is software for securely and consistently replicating applications across multiple nodes. Tendermint works even if up to a third of the nodes fail in any way. Tendermint is designed to be easy to use, easy to understand, performant and suitable for a variety of distributed applications.
The current BFT algorithm can reach consensus in the following conditions:
At most 1 of 4 nodes is a Byzantine node
At most 8 out of 25 nodes are Byzantine nodes
Up to 33 Byzantine nodes out of 100 nodes
The network operation status can be divided into the following centralized situations. Assuming that f is the number of Byzantine nodes, the network has a total of 3k+1 nodes, and k is a random integer.
f ≤ k, the network is stable
k < f < 2k+1, some nodes may not be able to reach a consensus. blockchain pause
f ≥ 2k+1, there are potential safety hazards
Ouroboros Algorithm Mechanism
Compared with the BFT algorithm, Ouroboros can support more nodes and support nodes to enter and exit at any time. Ouroboros is more decentralized and flexible than BFT, but has a longer reaction time. Cardano and Mina use the Ouroboros algorithm mechanism.
The Ouroboros algorithm mechanism divides time into different periods, uses VRF (Verifiable Random Function) to generate random numbers in each time slot, and uses the generated random numbers to determine new block proposers. Nodes with more stakes are more likely to become block proposers.
looking to the future
looking to the future
The blockchain network balances decentralization and performance. Switching from PoW to PoS shows that the blockchain has a higher pursuit of TPS, decentralization, token economics and transaction speed. Around these four characteristics, more innovations will emerge in the future.
Token economics innovations in GameFi and DeFi applications can be applied in consensus mechanisms. The current staking mechanism is simple and outdated. For example, many DeFi projects generally use Ve tokens to increase the staking ratio and reduce circulation. Users need to pledge the project tokens for a certain period of time to obtain VE tokens. The longer the pledge time, the more Ve tokens will be obtained. In this way, the pledge rate can be increased. The dual-token model is also a good direction for innovation. Reward tokens and governance tokens can be separated to obtain more value. Many successful projects reduce market selling pressure through the dual-token model.
Original link
references
https://www.geeksforgeeks.org/practical-byzantine-fault-tolerancepbft/
http://muratbuffalo.blogspot.com/2020/01/practical-byzantine-fault-tolerance.html
https://minaprotocol.com/blog/how-ouroboros-samasika-upholds-minas-goals-of-decentralization
https://arxiv.org/pdf/1807.04938.pdfhttp://www.cs.cmu.edu/~dga/15-712/F13/papers//castro99.pdf
http://muratbuffalo.blogspot.com/2020/01/practical-byzantine-fault-tolerance.html