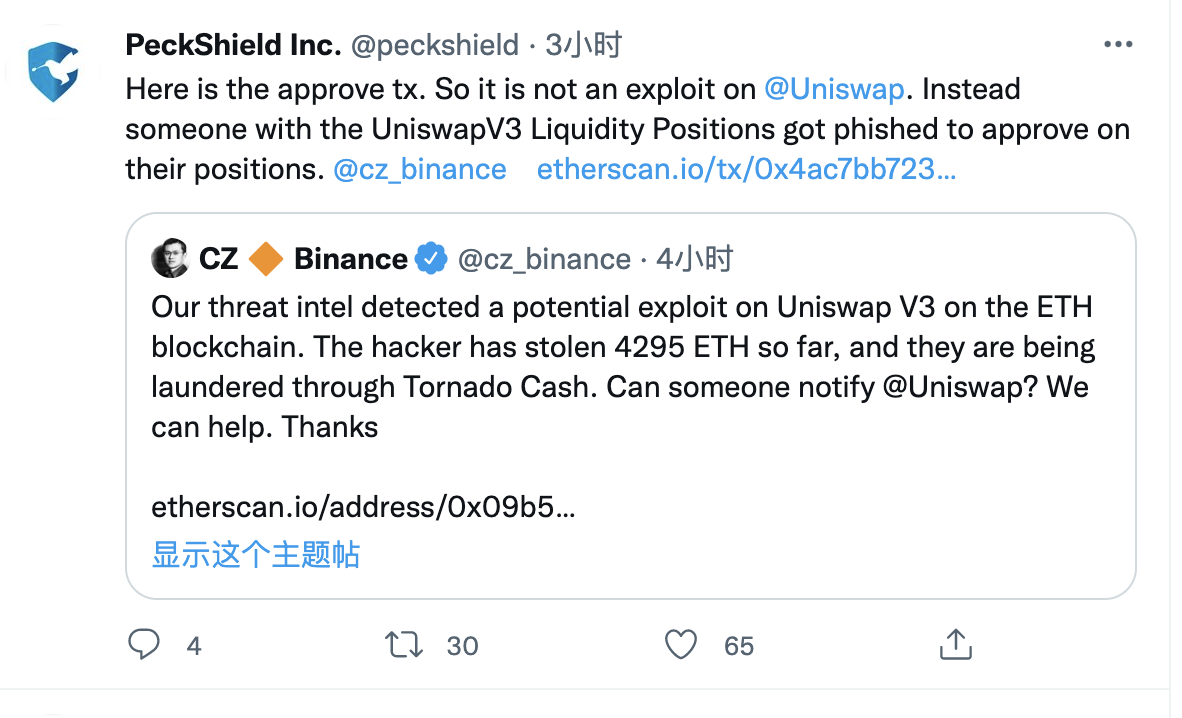
This morning, CZ tweeted to remind: Our team discovered a potential vulnerability on Uniswap V3 on ETH; so far, hackers have stolen 4295 ETH, and they are laundering money through Tornado Cash. connect.
After querying the smart contract address in the CZ prompt, it was found that a large amount of ETH was indeed transferred out of Uniswap V3, but it seemed to be no different from ordinary LP withdrawal transactions.
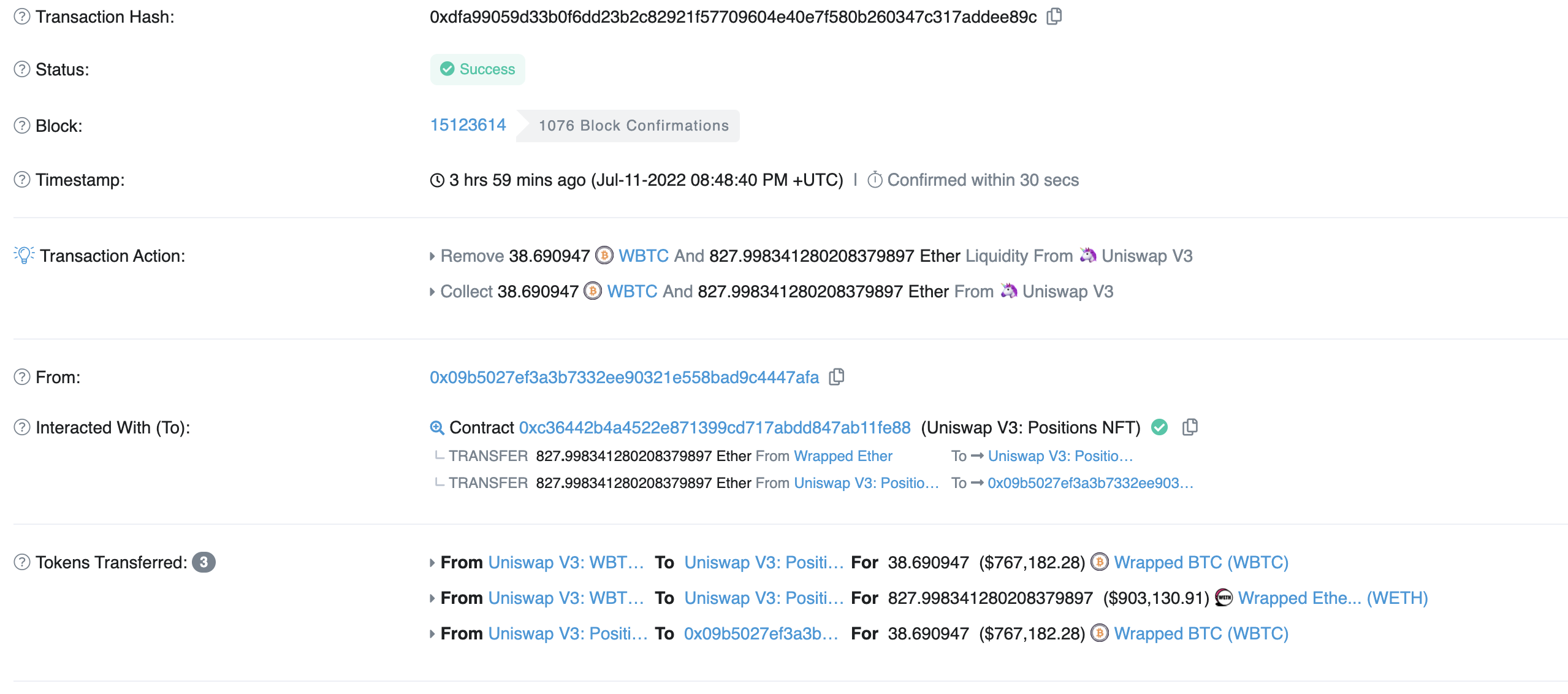 Not long after CZ tweeted, a Twitter user @samczsun said that this was not a Uniswap V3 exploit, but a successful phishing campaign.
Not long after CZ tweeted, a Twitter user @samczsun said that this was not a Uniswap V3 exploit, but a successful phishing campaign.
When everyone was discussing this matter enthusiastically, CZ tweeted again, posting a screenshot of the conversation with the founder of Uniswap V3, saying that this was indeed a phishing attack, which resulted in some LP NFTs of users who approved malicious transactions being illegally Get, but this has nothing to do with the Uniswap V3 protocol, which is secure. Finally, CZ expressed his apologies for the warning, and hoped that everyone would protect themselves from phishing and not click on malicious links.
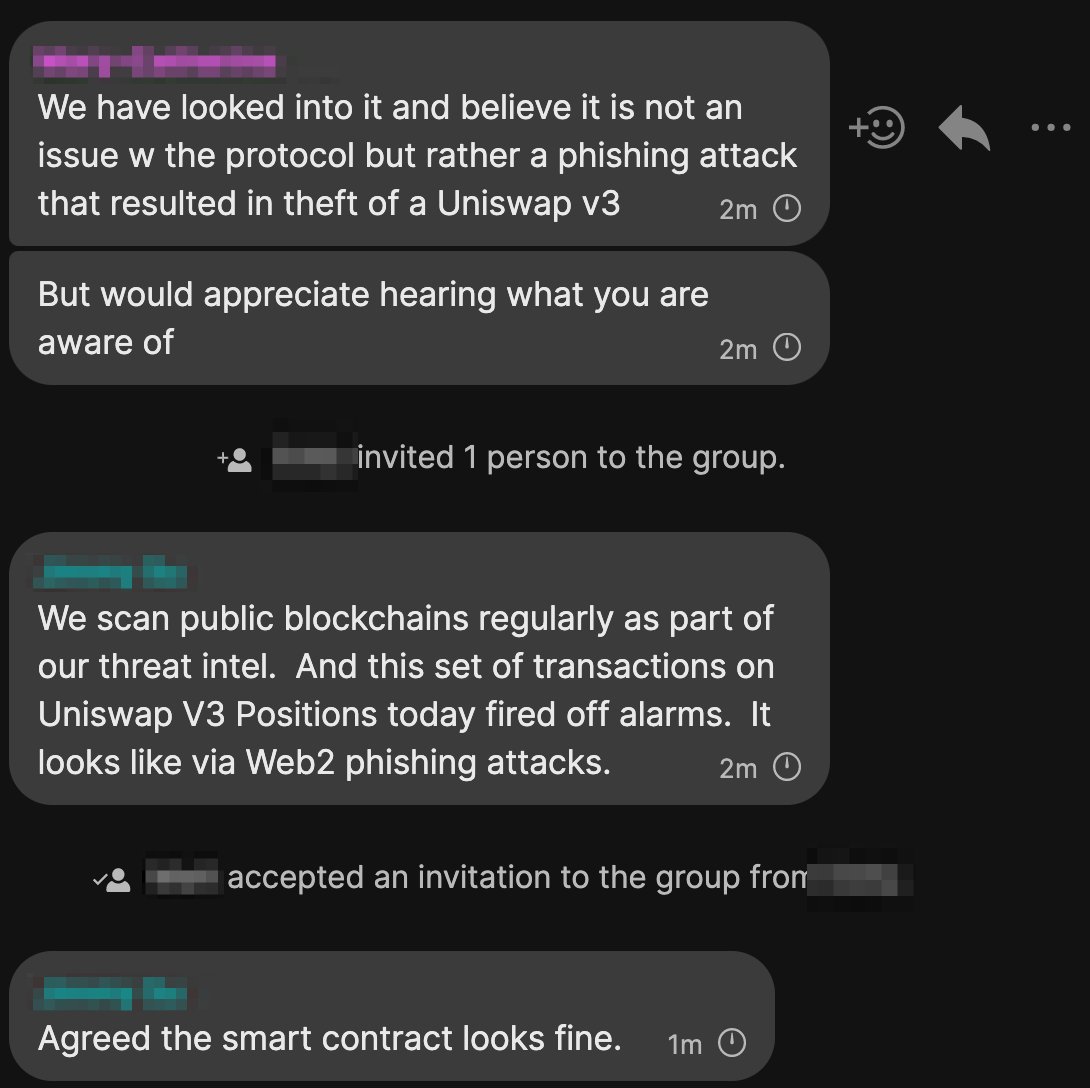
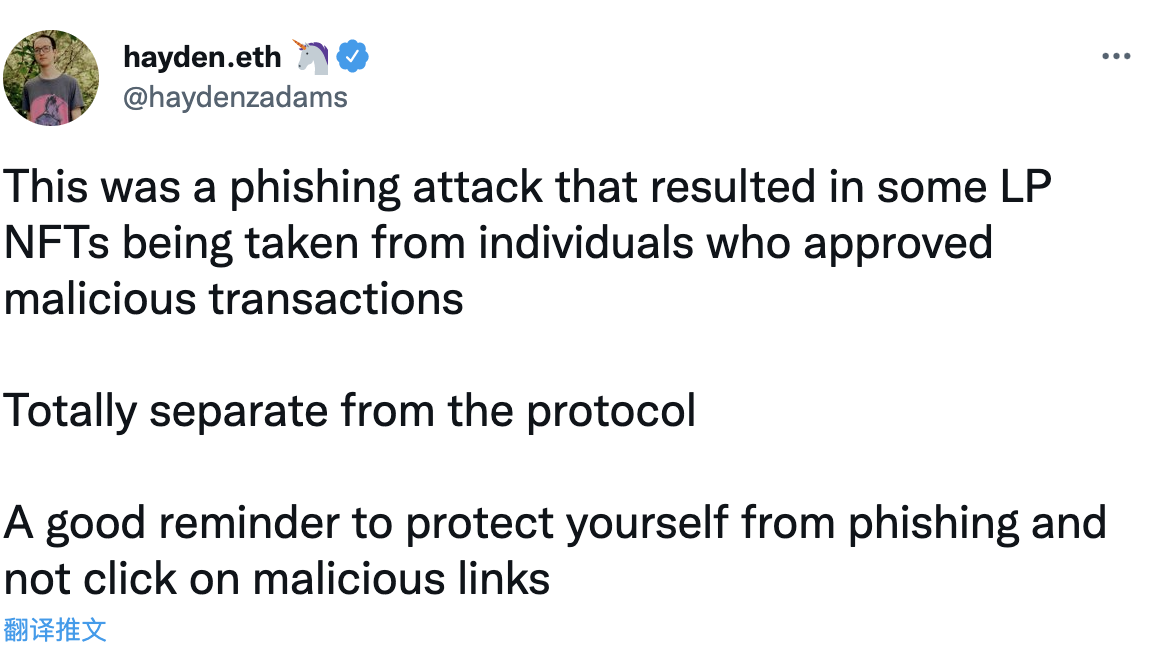
Subsequently, the founder of Uniswap also tweeted to confirm that the incident was a phishing attack, and thanked CZ for his timely reminder.
In fact, as early as 6 hours ago, some netizens discovered the phishing attack. The first is that the malicious contract pollutes the event data, so the block explorer will index "From" as the legitimate "Uniswap V3: Positions NFT" contract.
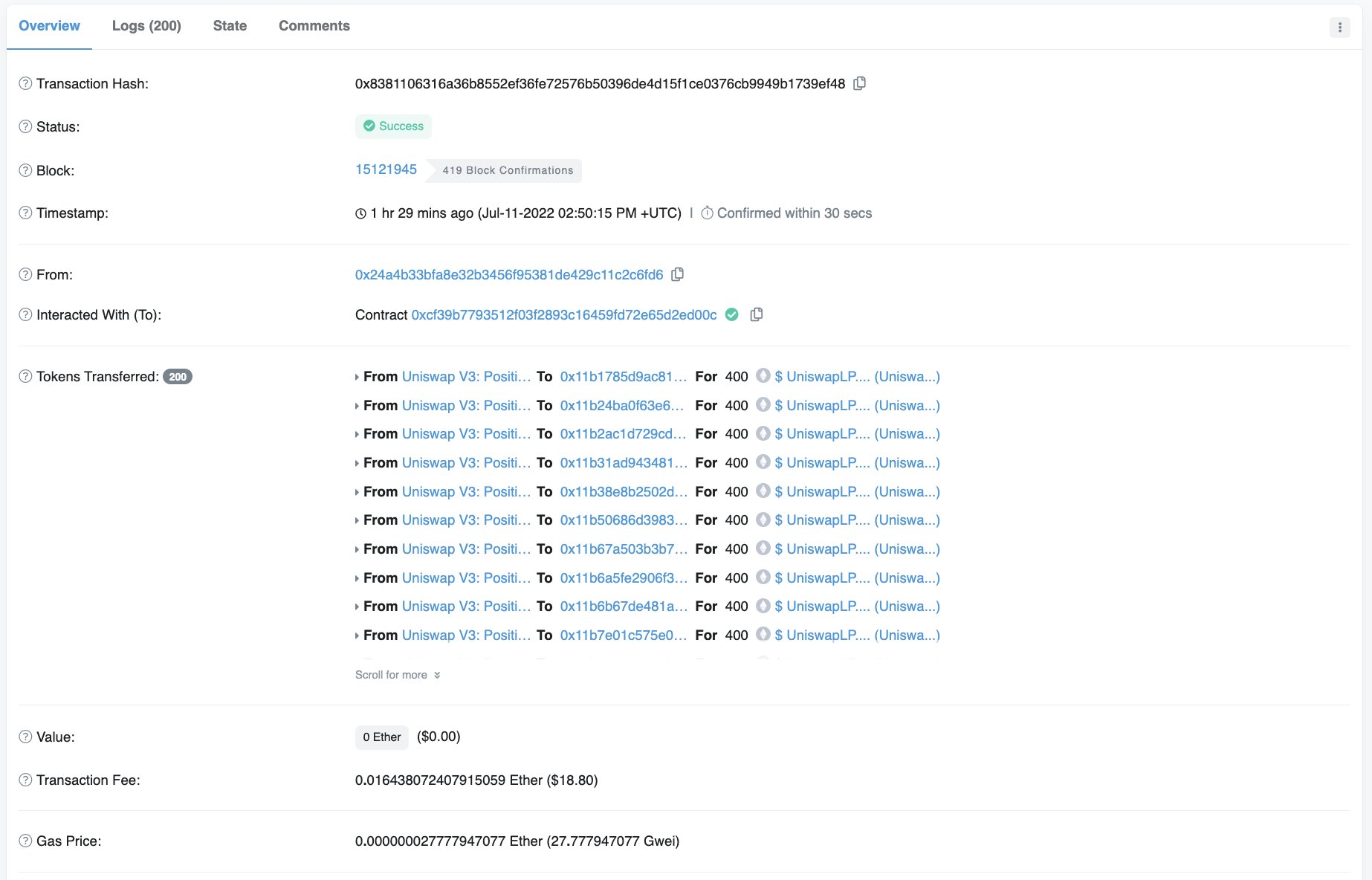
Therefore, users will see that "Uniswap V3: Positions NFT" sent them a token. They’ll get curious and click, which will direct them to an address with the domain name “/Uniswplp.com,” which mimics a real Uniswap address.
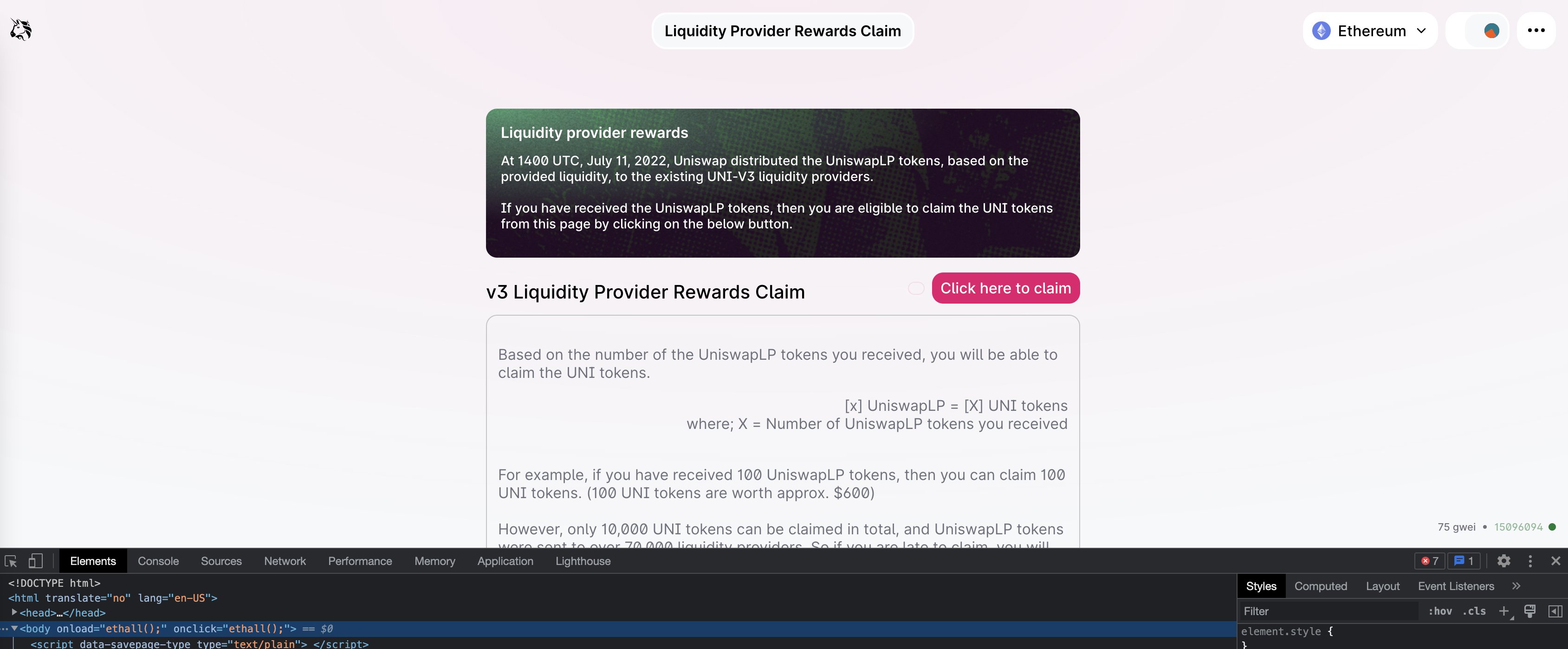
The website hosted by the thief then called ethall() when the document was clicked. The content of this function has been tampered with, but we can understand that it does two things:
a) Send your address and browser client information to /66312712367123.com, which can be used by thieves for illegal activities.
b) Attempt to steal your assets.
PeckShield also conducted a retrospective investigation on this incident: It confirmed the above inference, and believed that people with UniswapV3 liquidity positions mistakenly clicked on the phishing website, resulting in the theft of LP NFT.
Although it is only a common phishing attack, this wave of operations has caused panic in the market. The performance of UNI in the secondary market has fluctuated greatly, with the lowest point falling to $5.23, and the tentative report is $5.62 as of the publication date.
As the leader of DEX, Uniswap V3 has a large amount of liquidity, and the amount of locked positions is at the forefront, showing a growing trend. In the current industry tightening and leading competition, CZ's "little oolong" is easy to be "over-interpreted" on social media.
Some netizens also said that there is nothing wrong with CZ's approach. If it weren't for heavyweight industry leaders to publicly warn of this incident, the Uniswap V3 team might not have paid attention to it and took quick action. CZ responded quickly.
Odaily also reminds everyone that phishing attacks by hackers have occurred frequently recently, and a large number of different phishing websites can be copied in batches with a single phishing template, and the cost of doing evil is extremely low. It is hoped that ordinary users will be more vigilant, strengthen their security awareness, remain suspicious at all times, and avoid becoming the next victim.