This article is from the WeChat public account Old Yuppie.
This article is from the WeChat public account Old Yuppie.
In this article, we'll dive into:
A detailed description of Ethereum's PoS consensus model
How Ethereum PoS Recovers From Malicious Attacks
Refuting Common Anti-PoS Arguments
image description
first level title
Consensus mechanism: PoS, PoW, PoA
The consensus mechanism defines how a distributed network of nodes determines the current state of the network, which blocks are on-chain, and in what order. Block production is a general term that describes who scans the mempool to pick up pending transactions, orders them into blocks, and appends the new blocks to the existing blockchain. Three common classes of consensus mechanisms are Proof of Stake, Proof of Work, and Proof of Authority.
PoW (Bitcoin) gives block production rights to whoever uses the most computing power. The protocol defines a one-way computationally intensive hash function such as SHA-256, and then miners compete to find an input that is hashed into an output with many leading zeros.
PoA (Binance Smart Chain) is a whitelist mechanism that hands over block production rights to several whitelisted nodes. This is your typical permissioned blockchain, nothing more.
PoS (Ethereum,first level title

Ethereum implementation
Ethereum’s PoS implementation has been ridiculed by the masses for the better part of a year, but with the beacon chain running for 18 months and successfully performing a live merge on the testnet, the implementation looks set to take shape. I will focus on the specifics of how a PoS chain operates in its stable state rather than getting lost in the implementation details of the merge.
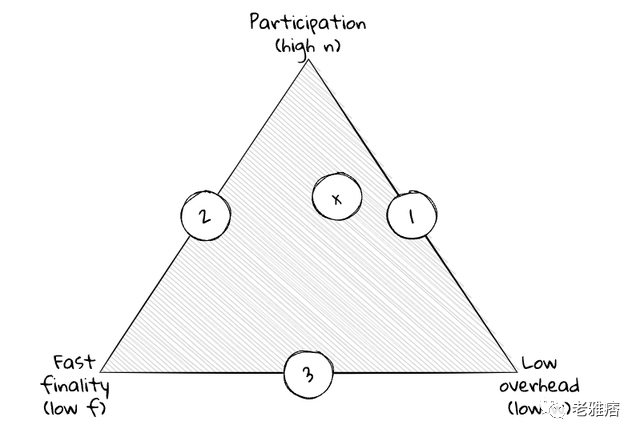
Another famous trade-off triangle. Pick two, or find yourself somewhere in the middle.
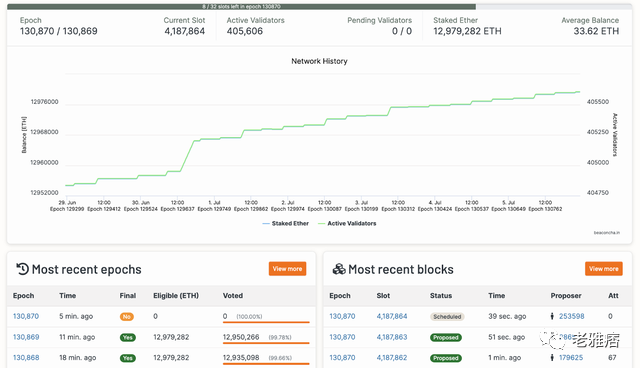
There are around 400,000 validators on the Beacon Chain, where you can track real-time stats and blocks. A validator refers to a specific deposit of 32 tokens in the main network's beacon chain deposit contract; a user can run multiple validators. Thawed withdrawals are not enabled today and will not be enabled at the time of the merge, but will be enabled in a later Shanghai hard fork update. A period occurs every 12 seconds, and a validator is randomly selected to submit a block during that period. An epoch consists of 32 epochs (or 6.4 minutes). If a validator is offline and does not propose a block within its slot, the slot is left blank. Therefore, the block time of Ethereum will change from the Poisson distribution with an average block time of 13 seconds (Poisson distribution, which is a discrete probability distribution commonly seen in statistics and probability, developed by French mathematician Simone Denis Poisson Siméon-Denis Poisson published in 1838), transitioning to the occasional empty slot of exactly 12 seconds. The first block within each epoch is considered a checkpoint block.
image description
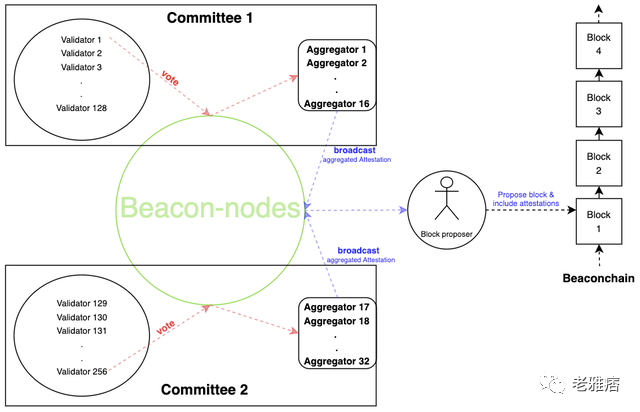
A technical overview of how validator proofs are aggregated and eventually included in blocks.
Epochs are groups of 32 slots that go through three stages: Proposal, Demonstration, and Finalization. Once a supermajority, or two-thirds of the current validators, have attested for an epoch, it can move forward. Proofs are associated with pairs of checkpoint blocks, one from previous epochs and one from the current epoch. We denote it by a pair of source and target blocks. A block is proposed by a validator, and it is considered valid when a supermajority of proofs marks it as the head. A supermajority of validators marks a reasonable epoch as previous epoch, it is considered finalized. Therefore, an epoch is usually finalized after one epoch (or 6 minutes).
A transaction is finalized when it cannot be re-aggregated without consuming a large amount of ETH. Since two-thirds of the validators have attested to the final block, in order to create a different final epochs at the same height, two-thirds of the validators also need to attest to a separate block of the same height. Therefore, at least one-third of the validators will prove to be ambiguous. The penalty for equivalent exchange is to cut off the validator's entire stake, so the attacker must commit to destroying at least one-third of all staked ETH. Even at today's depressed prices, the cost of reorganizing a final block is in the billions.
first level title
Staking requires active effort
Many people have a distorted image of staking because the term is widely used in DeFi and NFT. In many of these protocols, "staking" means depositing tokens into an escrow contract, reducing liquidity for sellers while tokens sit passively there. No downside risk, no active participation, just bribery of people with low time preference.
To be absolutely clear, these games are not what we're talking about. True protocol-level staking means entering into a rising and falling commitment that requires ongoing active participation in proposing new blocks and attesting to blocks created by others. This means you can be rewarded for honestly participating in high uptime, or you can lose money for going offline or supporting malicious forks. These rules are not arbitrarily applied by a centralized party; they are clearly defined in advance and deeply built into the decentralized protocol itself.
There are two key equivalence exchange rules that validators must follow, taken from Gasper's paper:
Double voting: no validator makes two different attestations for the same target block.
image description

Slashing conditions taken directly from the Gasper paper
Honest consensus layer clients are programmed to explicitly never do this, so a normal honest user should not have to worry about these mechanisms kicking in. However, they provide important protection against malicious validators and elegantly solve the risk-free problem.
first level title
Ethereum is self-healing against destructive minorities
The combination of equivalence deletions, inactivity leaks, and user-activated soft forks packs a powerful punch. Equivalent deletes handle security errors, inactivity leaks handle validity errors, and UASFs allow even the honest few to recover from the malicious supermajority.
Equal division means that the validator verifies two different blocks at the same height, which may lead to parallel forks and final re-splitting. This is a key element of the "nothing at stake" problem, i.e. building on all possible forks, because it does them no good. By collecting signed proofs, network overseers can prove this happened and slash the equivalent swapper's stake.
A leak of inactivity is when a validator fails to provide a proof. This cannot be proven malicious, since validators could accidentally go offline, but it is detrimental to the network.
A user-activated soft fork is when a subset of validators believe that the mainline ignores them and their transactions, so they band together to form their own block producing fork.
first level title

Lazy Censorship for the Few
first level title
Active censorship by the minority
first level title
Lazy Censorship for the Few
first level title
Minority Active Censorship
A group of whales with a total stake of 40% wants to censor transactions and refuse to prove honest blocks. Blocks stop being finalized because there is no longer an honest supermajority. The chain will fork into two child chains, as if there was a clean network partition. Honest validators will see both forks, but will build on the honest fork since it has greater weight in the LMD-GHOST fork selection rule. Review validators will also see both forks, but manually override the LMD-GHOST fork selection rules and choose to continue on the review chain, pretending they don't know the honest chain.
On the Honest Chain, the inactivity leak kicks in as soon as blocks stop being finalized. This means that all censoring validators will appear offline because they refuse to attest to honest blocks. The stake of review validators is slowly burned until their effective balance drops low enough that they are removed from the validator set. At this point, honest validators now have a supermajority, and blocks start finalizing again.
first level title
User-Activated Soft Forks From Malicious Supermajority
We have seen that even if honest validators do not have a supermajority, by proposing honest blocks, and censoring validators reject attestations, censoring validators will be forced out of the validator set. What happens if honest validators have a sub-majority and censoring validators have a super-majority?
Interestingly, the mechanism is almost the same. One key difference is that honest validators must explicitly join together to acknowledge each other's proofs and override the fork choice rule, but otherwise they can form their own child chains , the malicious supermajority will slowly drain from the validator set until the honest submajority regains the supermajority.
first level title
Possible Improvements to Ethereum
Of course, there are several aspects of Ethereum PoS that need further improvement. For example:
Single-slot finality refers to reducing the time for determinism from 2 epochs (64 blocks) to 1 block
Reducing the minimum amount required to stake will make home staking more viable for users without 32 eth
When the addresses of block proposers are known in advance, a single secret leader election will minimize potential DoS attacks against block proposers
first level title
secondary title
PoS = on-chain governance
Ethereum does not have on-chain governance (even though a subset of PoS protocols do). Just like Bitcoin full nodes allow miners to honestly produce valid blocks that meet the state transition function, Ethereum full nodes allow verifiers to honestly produce valid blocks that meet the state transition function. Even a supermajority of malicious validators cannot fool an honest full node.
secondary title
PoS = central bank
secondary title
PoS = scaling with cheap gas
secondary title
PoS = rich get richer, PoW = egalitarian
There is an egalitarian elegance to the idea of CPUs, GPUs, and ASICs churning in a math race to find the hash premap fastest. A sovereign individual, i.e. an individual running a home gaming computer, can compete with the nation-state for the right to 6.25 newly minted BTC.
Unfortunately, the ASIC supply chain is easily controlled by import and export regulations, not to mention the dangerous dependence on Taiwan. The need for cheap, abundant energy is another weakness that prohibits individuals from running discreet mining setups. And since we're not in a post-scarcity utopia yet, you need to pay up front to buy a mining machine. To make matters worse, technological advancements mean miners need to constantly upgrade their equipment to remain competitive, meaning reliance on supply chains is a constant point of weakness should things go bad.
secondary title
PoS = nothing
secondary title
PoS = no compulsive sellers
secondary title
PoS = central bank will buy all tokens
secondary title
PoS = trust centralized server for Canonical chain
secondary title
PoS = no real resource consumption
secondary title
PoS = bad complexity
first level title
secondary title
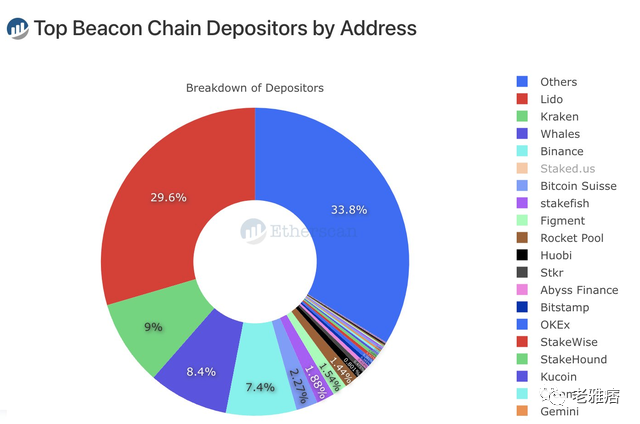
Liquidity (and Illiquidity) Collateral Custodians Cartels
image description
secondary title
Tokenization of real-world assets makes forking difficult
secondary title
Proof of any resource is centralized
secondary title
What does this mean to you?
image description
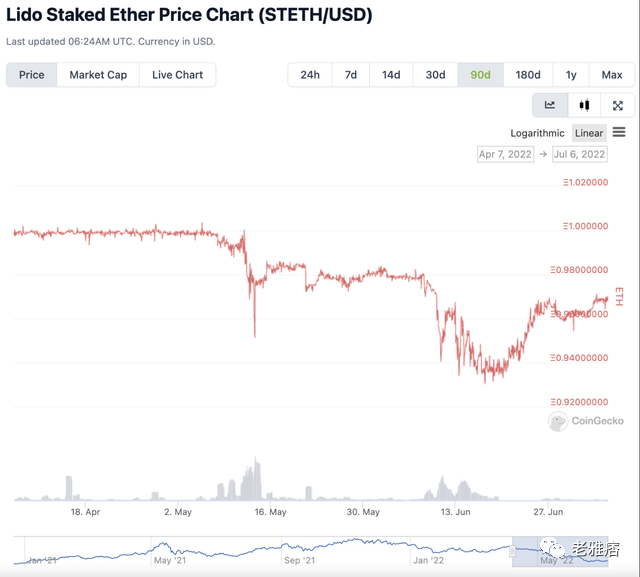
StETH/ETH price fluctuations over the past three months
This is odd advice, as the entire article has been hammering away at the ability to avoid malicious collusion, and now we describe how funds can be channeled into managed derivatives. But it would be remiss to let people enter the lockup at a 1:1 ratio without knowing that they can get paid for taking the risk of term+governance+smart contracts and mining cheap tokens from overleveraged funds up.
Summarize
Summarize
Original link