Original compilation: 0x711, BlockBeats
Original compilation: 0x711, BlockBeats
According to The Block, in March this year, the Axie Infinity sidechain Ronin cross-chain bridge was attacked and $540 million in assets was stolen because Axie Infinity employees received and downloaded a recruitment offer in the form of a PDF document. A virus is attached to the document, resulting in information leakage.
As the amount of money in the encrypted world increases, phishing attacks are becoming more and more common. In October last year, AnubisDAO also had a suspected mailbox receiving a SAFT agreement in PDF format, resulting in the theft of 60 million US dollars. So how to detect and prevent PDF document phishing attacks?
first level title
Fake File Extension Scam Warning
Hackers are modifying file extensions to disguise malicious files as PDFs and targeting artists, influencers and projects. The principle is as follows:
Case: Crypto ArtistTARSIUSReceived a commission message and received a zip file purportedly containing "customer requirements, samples, sketches, etc." When the artist opened the compressed package, the original ordinary commission changed.
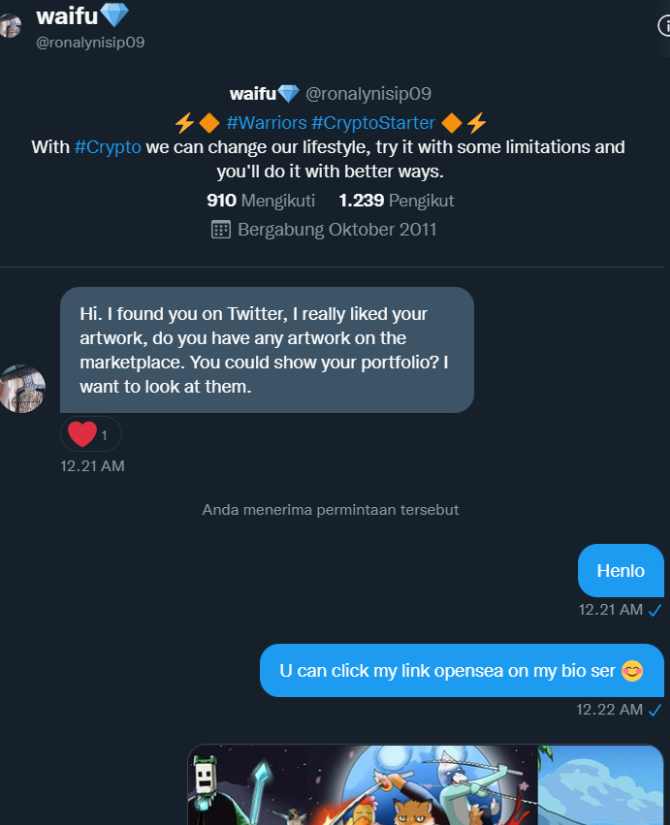
After opening the zip file, we can see the provided example, as well as a PDF file containing the "client" sketch, but this is no ordinary PDF file. It's actually a screensaver (.scr) file, which is an executable script disguised as a PDF file.
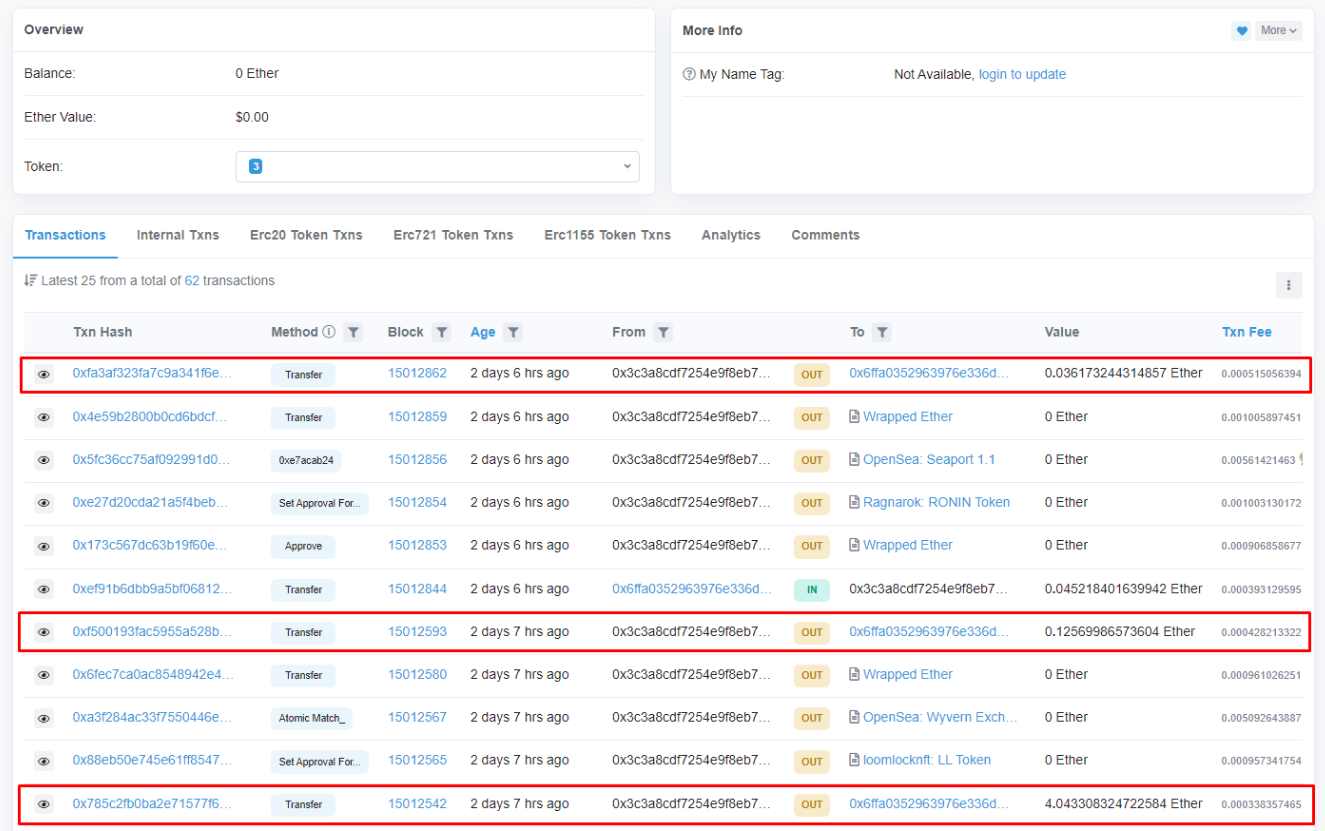
After the artist opened the PDF file to view the sketch, all his NFTs were listed and sold, and all his ETH was transferred to the scammer's wallet. Due to space limitations, this article only lists some of the transactions of the victims.
So how did hackers succeed? He changed the file extension and added .pdf to the end, and changed the file's icon to a PDF icon. He also filled the file with junk code, exceeding the file size of the virus file itself, to enhance the deception.
Artists aren't the only targets of this scam. Recently, KOLs, promoters, and project parties have all been targeted, many have lost control of their wallets and accounts, and everything has been completely wiped.
This is an old Web2 scam tactic that works with any and all file types.
How can this situation be avoided?
1. Do not download or open random files at will;
2. Always check the file type;
3. Research and learn basic Web2 security knowledge.
If you need to open any files, put them on Google Drive and view them there, or use a virtual machine. I personally use both.
You can enable file type extensions by clicking View at the top of File Explorer, then enabling File Extensions. This will display the file extensions of all files. (This feature is turned off by default.)
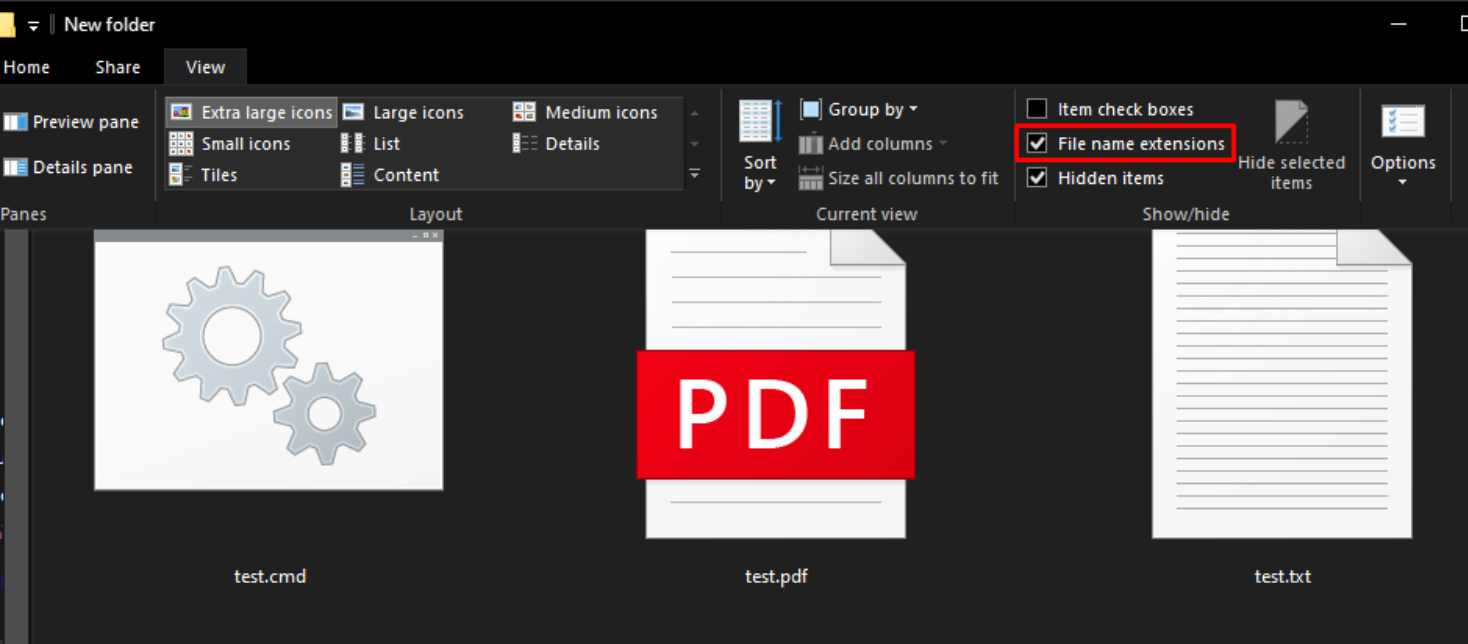
A .scr file is an executable file that can run any code, it's basically an .exe file. How are they going to compromise your wallet this way? Well, from this point on, we can assume your entire PC has been compromised.
All your cookies, passwords, extension data, everything, has been stolen. For example, they could change your MetaMask plugins to a modified, malicious version, or more simply, they could wait for you to log in and access your MetaMask, and they would have everything.
Original link