In 2021, Vitalik once said in an article:
Perhaps the most powerful cryptographic technology to come out of the last decade is general purpose succinct zero knowledge proofs,usually called zk-SNARKs. (Perhaps the most powerful cryptographic technique of the past decade is the general-purpose succinct zero-knowledge proof zk-SNARKs.)
It is true that zero-knowledge proofs have played a key breakthrough role in two very important directions in the Crypto field, one is Scalability and the other is Privacy.
Zero Knowledge Proof (Zero Knowledge Proof, ZKP) means that the prover can convince the verifier that an assertion is correct/true without providing the verifier with information beyond the validity of the statement itself. There are two most widely used technologies after the zero-knowledge proof mechanism is transformed into a computer programming language—zk-SNARK and zk-STARK.
zk-SNARK is a zero-knowledge concise non-interactive knowledge argument. The basic logic is as follows:
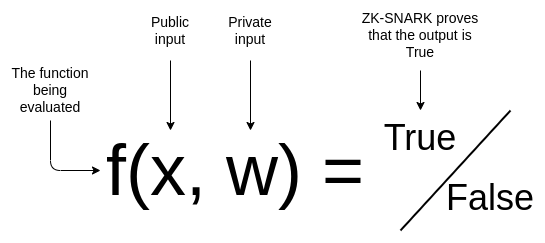
In the case of zk-SNARK implementation without revealing specific information, the simplest method to prove the correctness/authenticity of events is: based on credible initial settings, when each data is in the legal range, prove that "input" = "output" .
zk-STARK is a zero-knowledge scalable transparent knowledge argument, the basic logic is essentially the same as zk-SNARK:
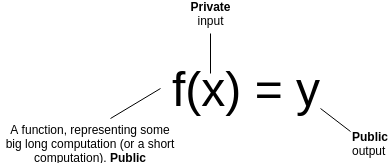
Compared with zk-SNARK, zk-STARK has its own advantages and disadvantages:
Initial trusted settings: required for zk-SNARKs, not required for zk-STARKs;
Proof data size: the proof size of zk-SNARK is about 288 bytes, and that of zk-STARK is a few hundred KB larger;
Cost: zk-STARK is lower than zk-SNARK;
Proof process speed: The proof process of zk-STARK is faster than zk-SNARK.
first level title
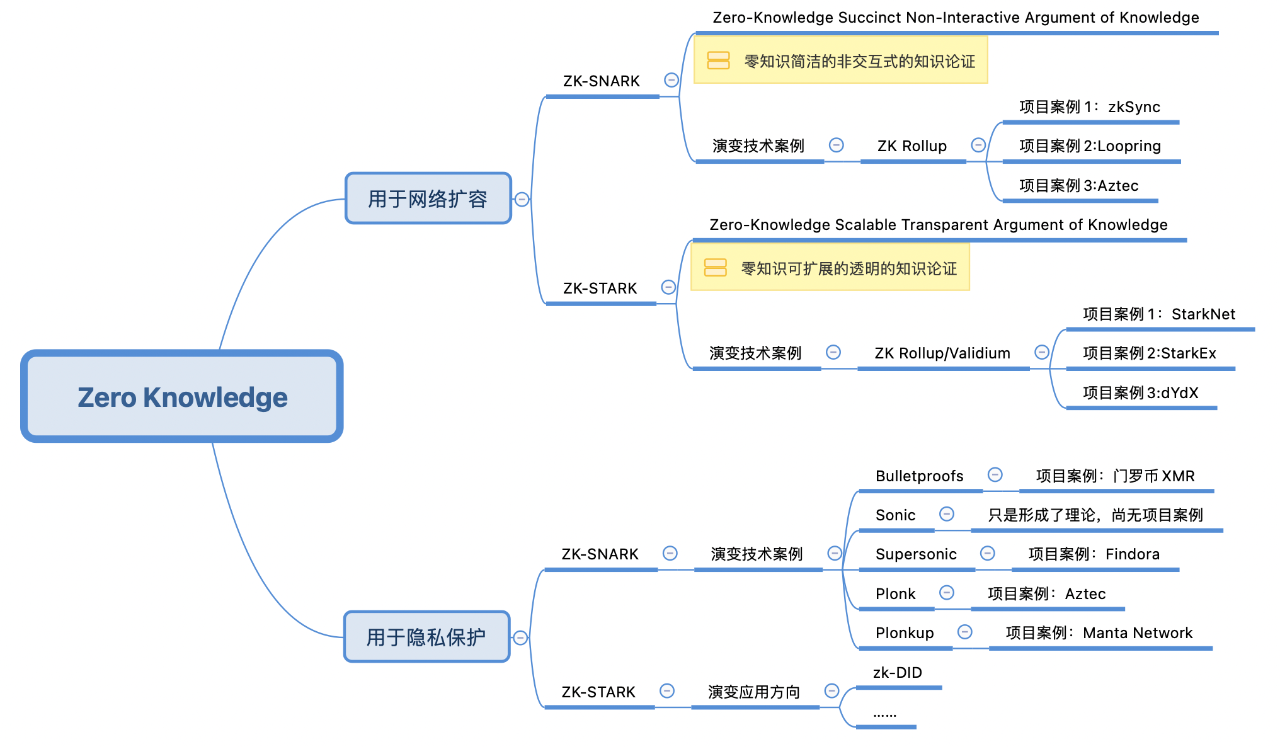
The application of zk in expansion
secondary title
StarkWare
StarkWare is a Validium-type Ethereum Layer 2 expansion solution based on zero-knowledge proof (zk-STARK), and launched StarkNet and StarkEx based on this solution. The mechanism of Validium is very similar to zk Rollup, the only difference is that the data availability in zk Rollup is on-chain, while Validium keeps it off-chain, which allows Validium to achieve higher throughput.
Since the data is processed off-chain, the process in the process of data on-chain must be very important. The zk-STARK data on-chain process is as follows:
1000 transactions are sent to zk-STARK;
As the prover, zk-STARK generates a proof (as shown in the figure below: generation stage);
The node acts as a verifier to read the proof and update the data on the chain.
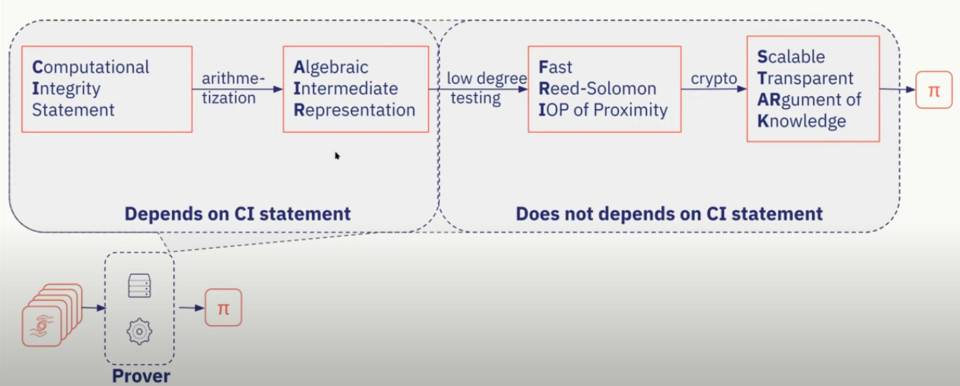
Proof Generation Phase
Therefore, the core logic of zk-STARK is to allow the blockchain to transfer calculations to a single off-chain STARK prover, and then use the on-chain STARK verifier to verify the integrity of these calculations.
secondary title
zkSync
The zkSync expansion solution launched by Matter Labs is a zk Rollup-like Ethereum Layer 2 expansion solution based on zero-knowledge proof (zk-SNARK).
zkSync improves scalability by introducing two roles: Validators and Guardians:
Validators are responsible for processing transactions and packaging blocks. Validators need to pledge tokens, and then need to provide a transaction zero-knowledge proof for the transaction, proving that the transaction process is correct and there is no fraud. If the Guardians find out that they have done evil, the pledged tokens of the Validators will be confiscated; if there is no evil, the Validators will be rewarded with tokens.
In this process, by using zero-knowledge proof, Guardians do not need to know the specific content of the transaction, but also know that the transaction process is correct/authentic. Based on this logic, many transaction processes can be processed on the Layer 2 chain, and the correct results can be fed back to the Layer 1 Ethereum chain, thereby improving the scalability of the Ethereum network.
Of course, now Matter Labs is promoting zkSync2.0, which has a great technical update. On the one hand, zkSync2.0 introduces zkEVM, which can deploy Ethereum smart contracts on zk Rollup. On the other hand, zkSync2.0 will adopt the technical solution of Volitions. Volitions is equivalent to including zk Rollup and Validium, and can support multiple data availability modes of ZK Rollup and Validium or other combined modes at the same time. The right to choose is returned to the user, and the user can choose which mode to trade in. In the ZK Rollup mode, all data is submitted on the chain, and the validity of the state update is guaranteed by zero-knowledge proof; in the Validium mode, the data is stored off the chain, and only the latest state and the validity of the state are proved on the chain submit.
first level title
Application of zk in privacy
Zero-knowledge proof is used for privacy, which is divided into transaction privacy and data privacy.
In terms of transaction privacy, zk-SNARK and derivative technologies based on zk-SNARK are basically used. Previously in "Talking about the evolution of technology in private transactions"The application of zk-SNARK technology and its derivative technology in transaction privacy was introduced in detail in the article, so I won't go into details in this part. The core workflow is:
Set up a trusted setup to ensure the initial security of the system;
Set up a range proof (Range Proof) to prevent surround attacks;
Check input note = output note to ensure the correctness of UTXO.
In addition to being used for transaction privacy protection, zero-knowledge proof can also be used for data privacy protection. For example, your age, through the zero-knowledge proof mechanism, you do not need to provide specific identity information, you only need to pass a simple zero-knowledge proof algorithm-for example, prove that your age is greater than or equal to 18 years old, you can prove that you are an adult and have The right to participate in an activity – this is both data privacy protection and proof that you qualify for something.
Zero-knowledge proofs may also have many application scenarios in future on-chain reputation proofs. For example, in the current on-chain credit problem, the core difficulty lies in the fact that a personal on-chain identity system has not yet been established. There are at least two reasons why the identity on the chain is not easy to establish:
First, real-world identity proof tools are not suitable as on-chain identity proofs. On-chain wallets do not have a one-to-one correspondence with real identities, and to a certain extent, real identity proof tools (such as ID cards) are not suitable as identity proofs in the Crypto field. On the one hand, many Crypto assets hold Some are unwilling to disclose personal identity information. On the other hand, even if the DeFi protocol has mastered the personal identity information of the defaulting user, the rights and interests of tokens such as USDT in many countries and regions are not protected by law. Responsibility is useless.
Second, users on the chain are unwilling to reveal too much privacy in terms of personal assets. In order to assign credit points to each user on the chain, it is necessary to know all aspects of the user's on-chain assets and on-chain behavior information. But many users are unwilling to let others know what addresses they have, what transactions they have made... and other information. However, in order to give users on the chain a reasonable credit score, it is necessary to have as much user information as possible. Therefore, in terms of on-chain reputation and on-chain credit, the empowerment of zero-knowledge proof may also be needed.
All in all, the application of zero-knowledge proof in terms of expansion and privacy is a clear trend in the current industry development.