Original Author: Yao & Lisa
According to the intelligence of Slow Mist District, the NFT project verb phishing website is found as follows:
Phishing website 1: https://mint-here.xyz/verblabs.html
Phishing website 2: https://verb-mint.netlify.app
Let's first analyze the phishing website 1:
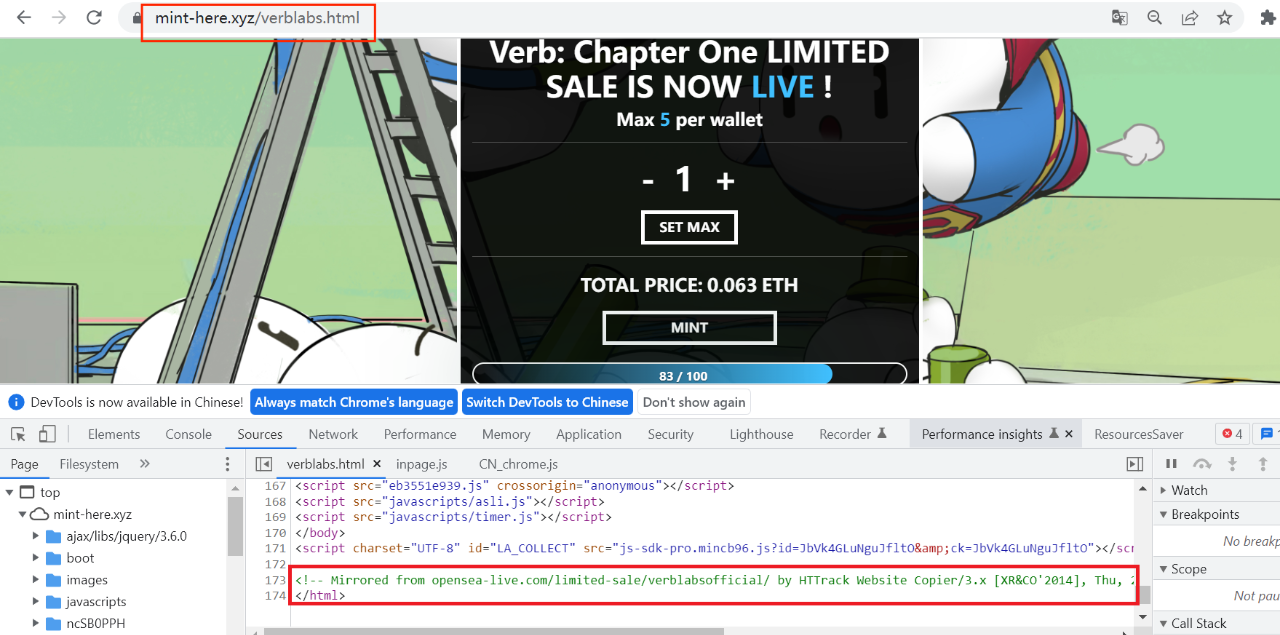
View the source code and find that this phishing website is directly cloned using the HTTrack tool
http://opensea-live.com/limited-sale/verblabsofficial/ site (phishing site 3).
This cloned site is very suspicious and appears to be a phishing site as well.
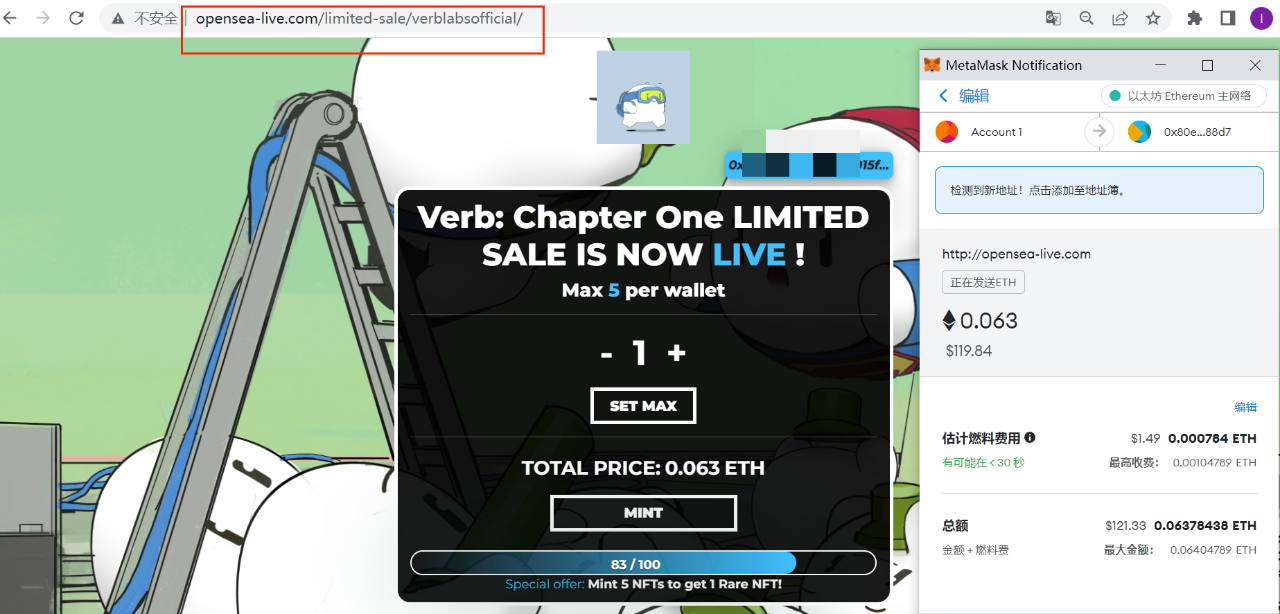
Let’s take a look at the phishing website 2:
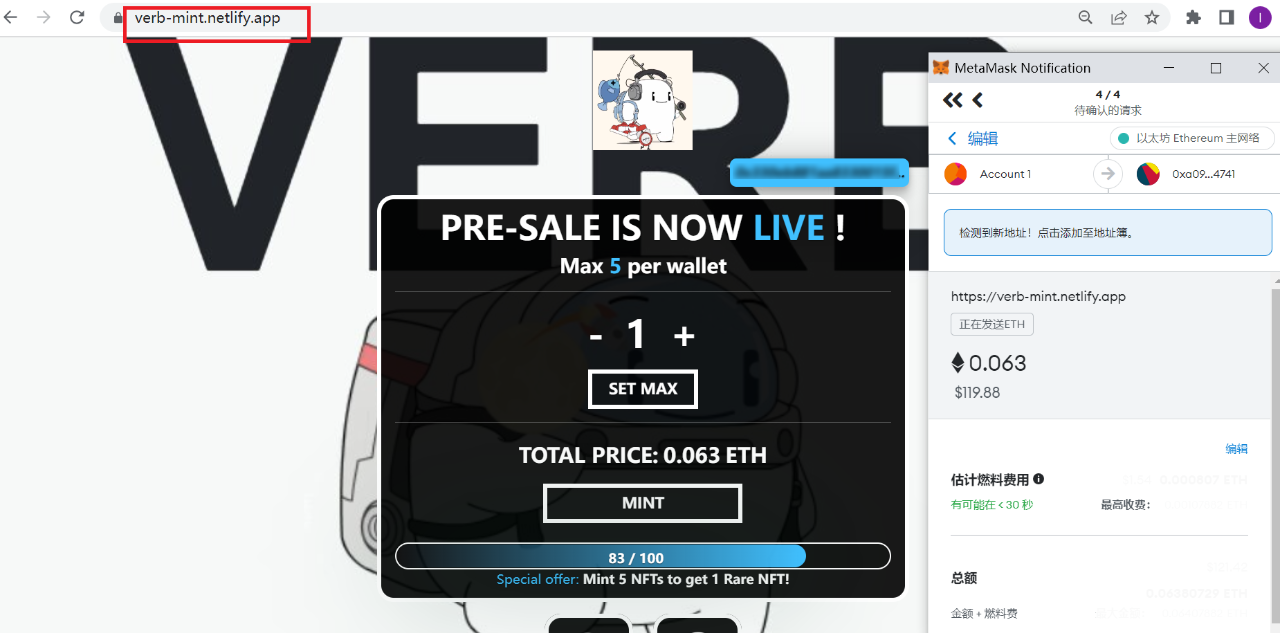
These three sites seem to be generated from a template.
Compare the three phishing websites to find out the phishing addresses:
Phishing address 1: 0xe7b2AAa70D6133c78006A078b95dF8Be3613385E
Phishing address 2: 0xa096356DeB502d1F5670A2E26a645eA4dbAA4741
Phishing address 3: 0x80eE5caDf0f04058b9dF853017542Ab3dF9D88d7
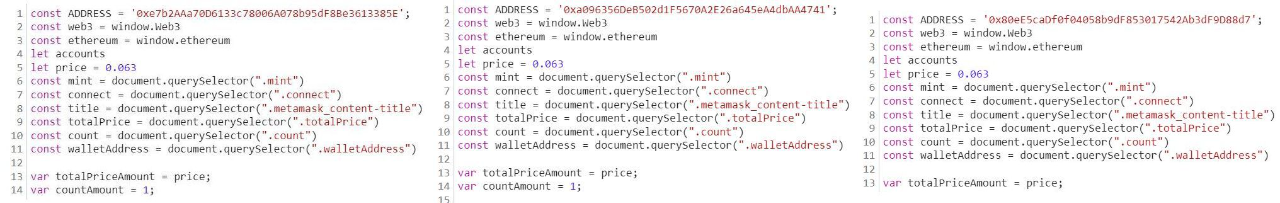
First analyze the phishing address 1 (0xe7b...85E):
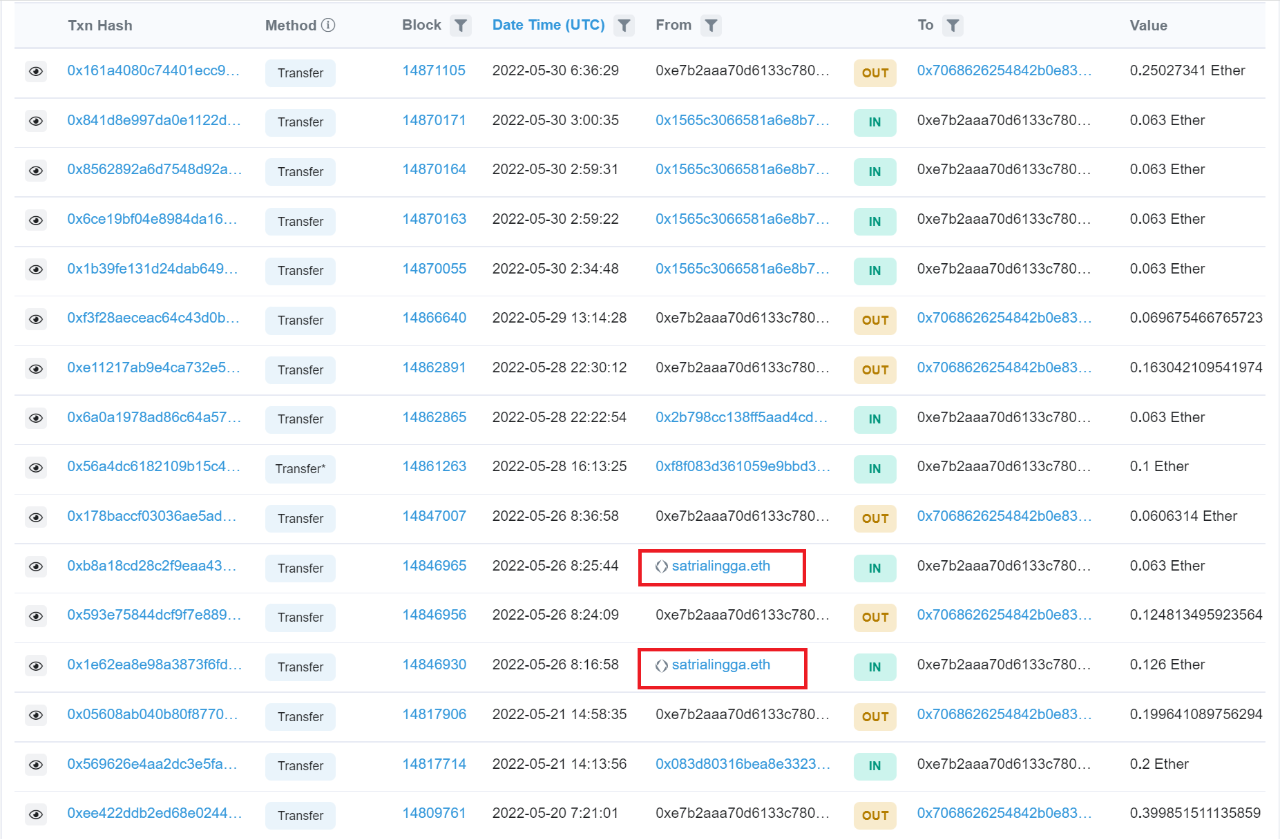
It was found that the address satrialingga.eth had transferred two transactions of ETH, 0.063 and 0.126 respectively.
image description
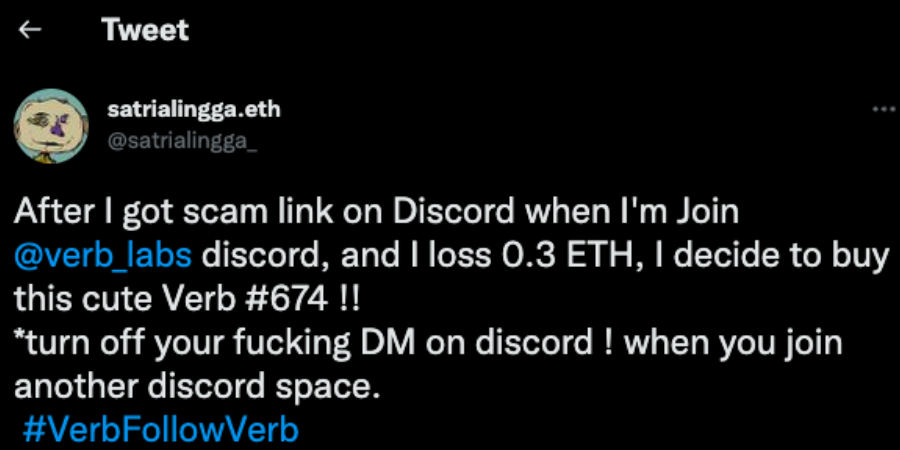
(https://twitter.com/satrialingga_/status/1529776369533480961)
According to the information of user @satrialingga_, we joined the Discord of @verb_labs. As soon as we joined, 2 robots sent private messages to conduct phishing scams.
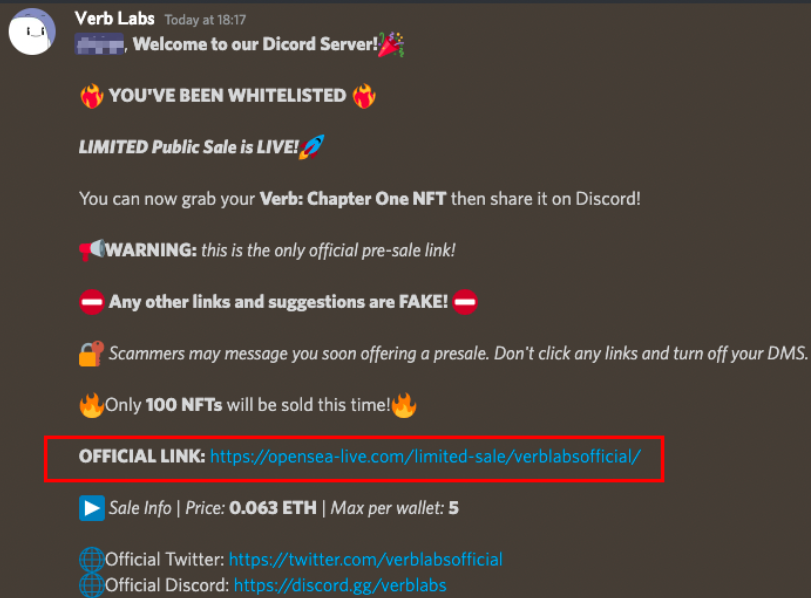
The scammer directly left an NFT picture of a phishing image, for fear that others would not recognize that this is a phishing website?
Next, we use MistTrack to analyze the phishing address 1:
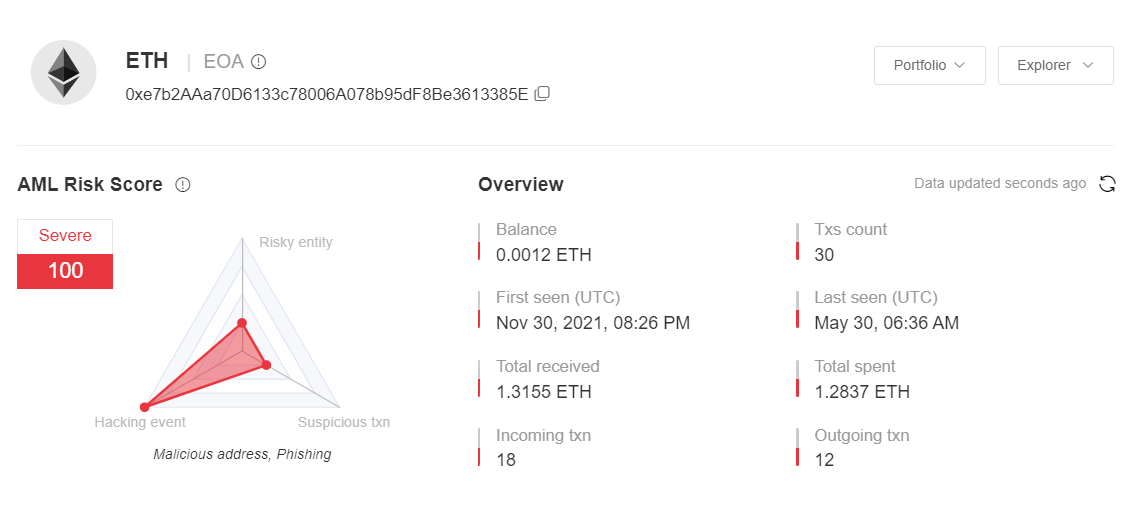
It was found that the stolen money was basically transferred away immediately.
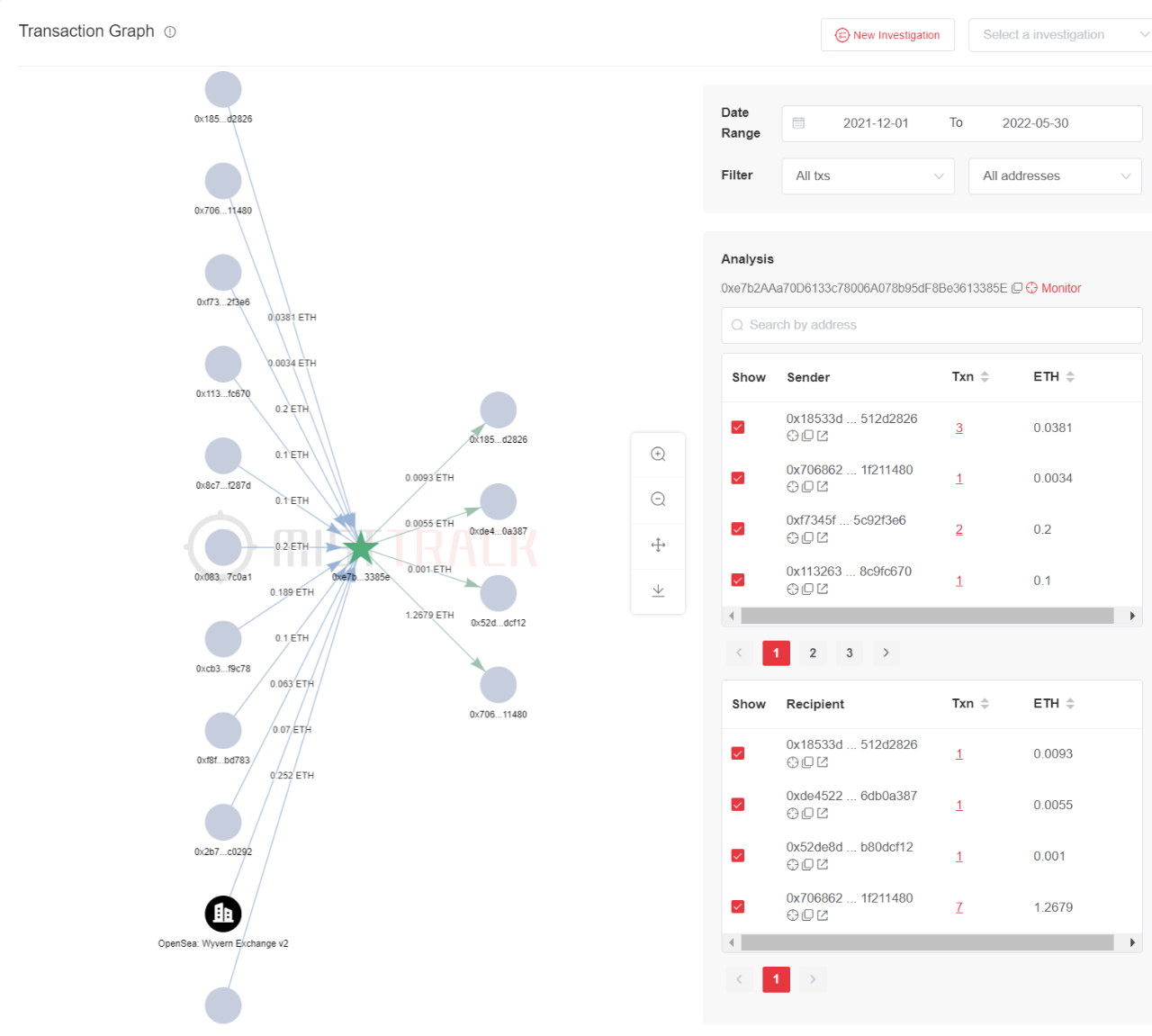
Look at this address with a large number of transactions:
0x7068626254842b0e836a257e034659fd1f211480:
The initial funds of this address came from two transfers of 1 ETH from TornadoCash, received a total of about 37 ETH, and laundered coins through 189 transfers, and had transaction records of withdrawal and deposit from Binance.
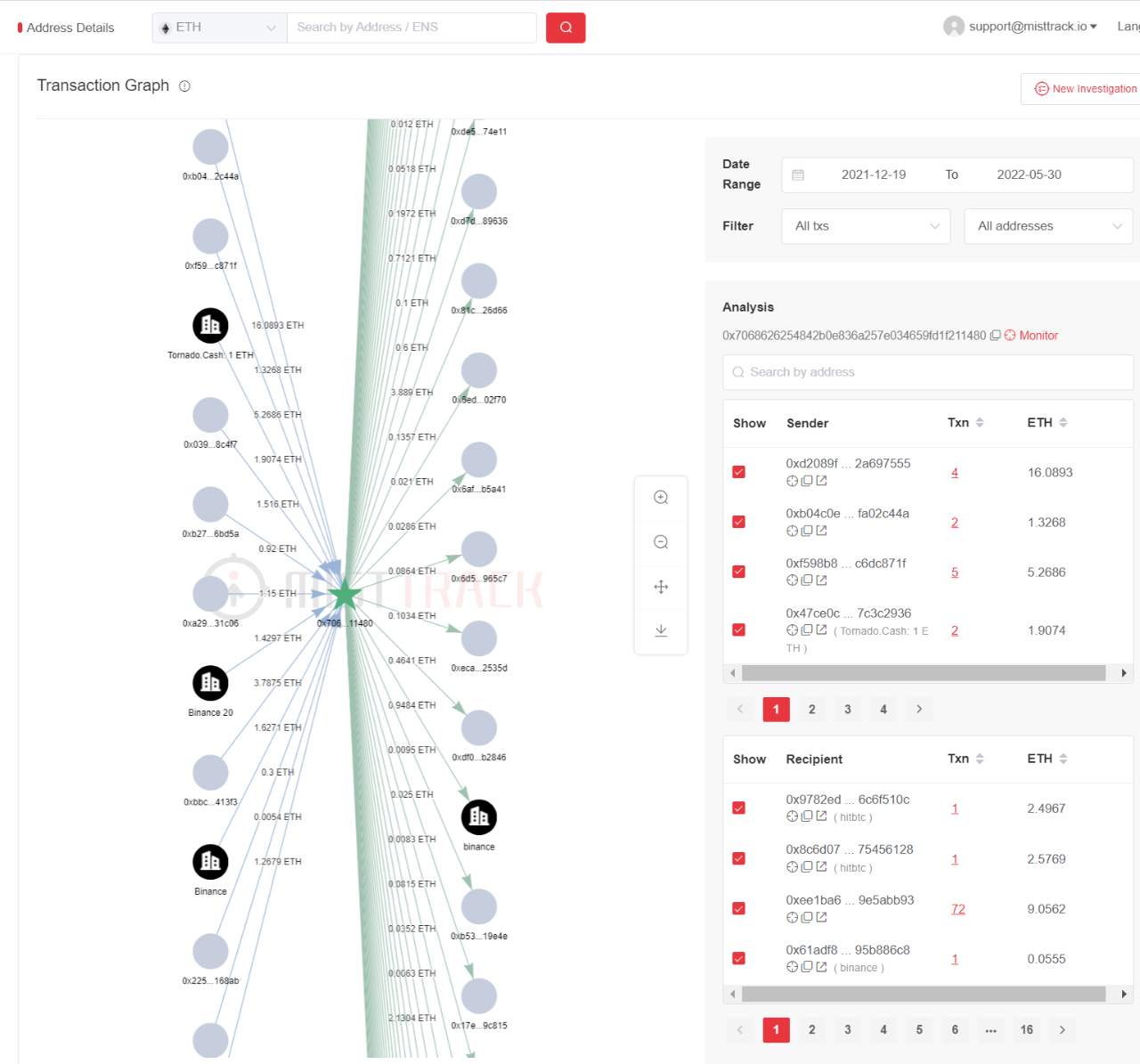
Next, let's analyze the phishing website 2.
It was found that address 2 (0xa09...741) exchanged most of the stolen ETH into USDT, and transferred it to address 0xf44c65d285d6282c36b85e6265f68a2876bf0d39, which has not been transferred yet.
Let's take a look at the last phishing site 3:
According to MistTrack analysis, address 3 (0x80e...8d7) received a total of about 5.5 ETH, and there were 53 deposit transactions. It seems that many people have been cheated.
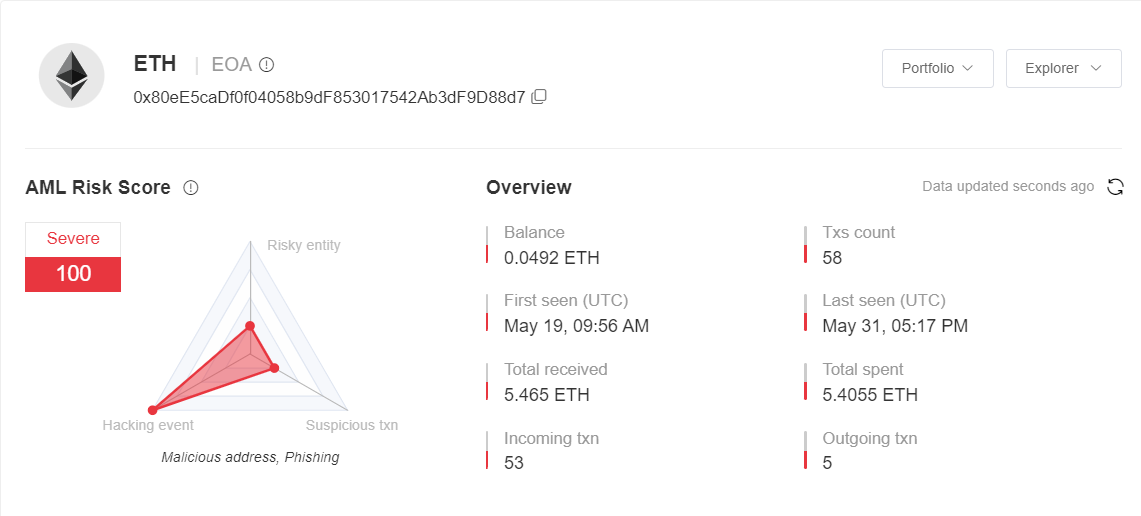
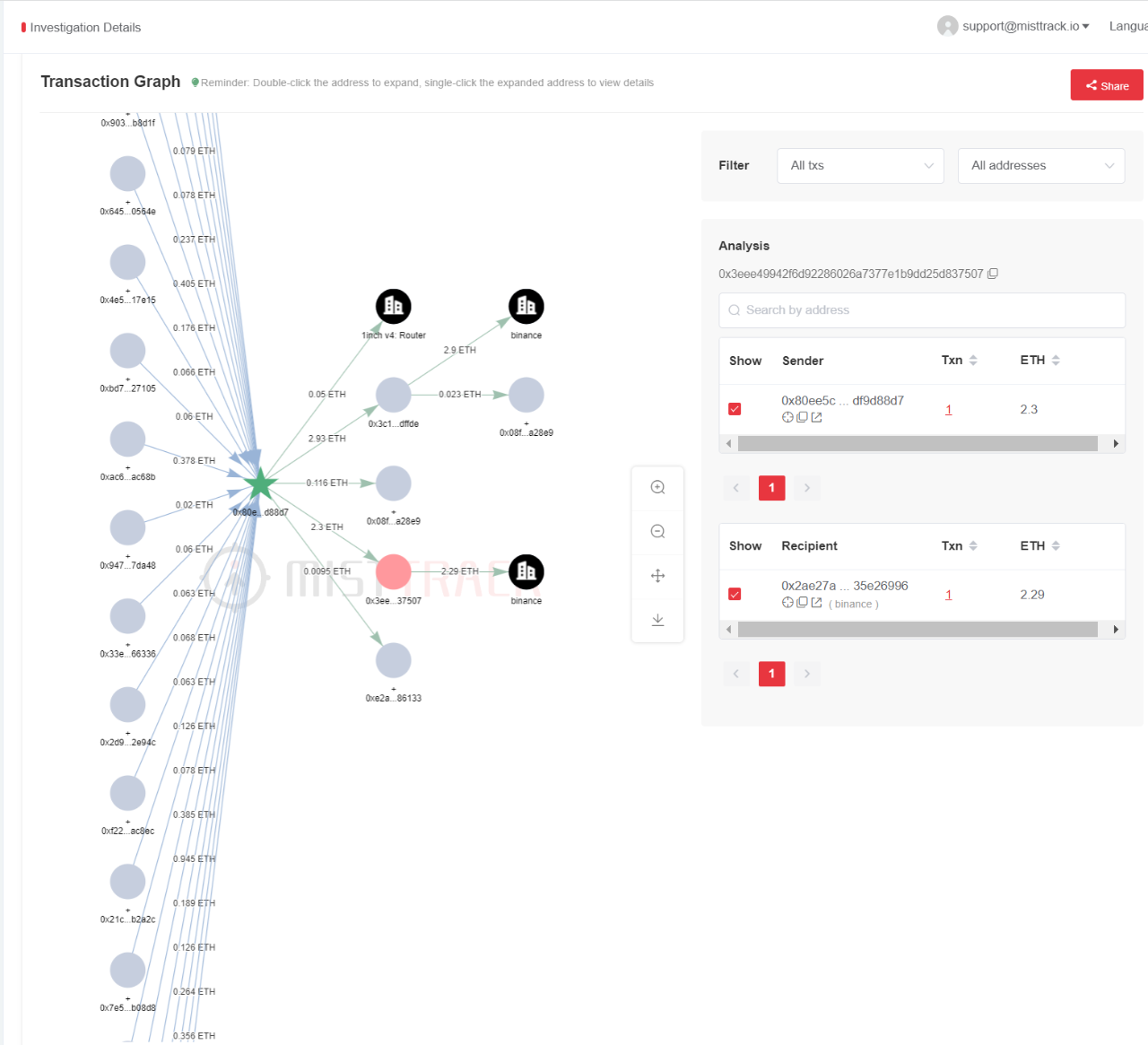
Continue to track and find that most of the ETH is transferred to the Binance address
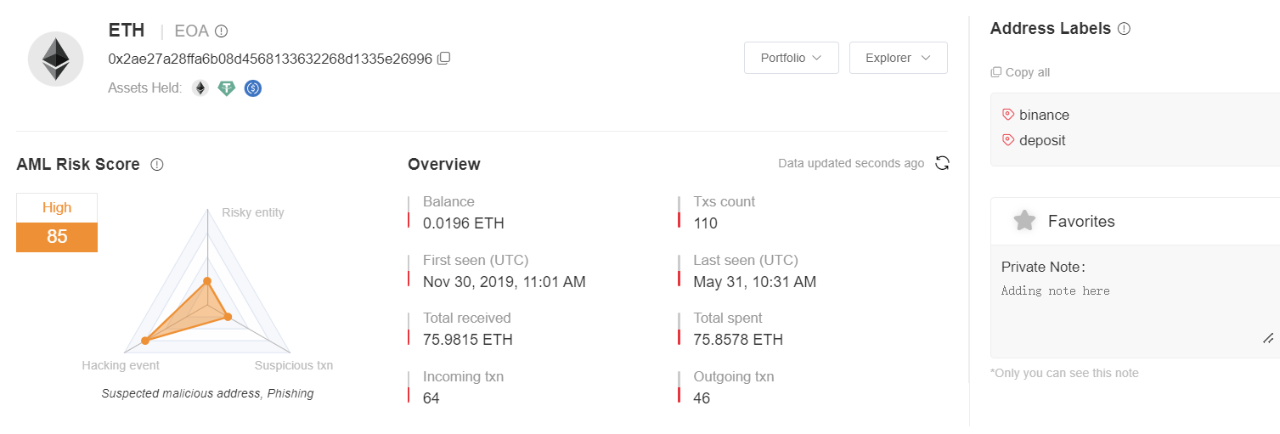
0x2ae27a28ffa6b08d4568133632268d1335e26996:
This address has a high risk rating on MistTrack and received about 76 ETH in total.
Summarize
Summarize
This article mainly explains the event that a large phishing website was analyzed from two small phishing websites. NFT phishing websites emerge in endlessly, with very low production costs, and have formed a professional industrial chain. These scammers usually directly use some tools to copy well-known NFT project websites, tricking users into entering private key mnemonics or inducing users to authorize .We recommend that you always verify the URL of the NFT site you are using before attempting to log in or make a purchase. At the same time, don't click on unknown links, and try to join Discord through official webpages or official media platforms, which can also avoid some phishing.