Compilation of the original text: The Way of DeFi0xfoobar
Compilation of the original text: The Way of DeFi
"Suddenly my wallet got an airdrop of an unknown NFT collectible, and then someone made an offer for 1 WETH. What's going on? Is it safe to accept it?"
Long story short, these are scams and you cannot profit from the interaction. Now, let's understand how these scams work!
The way OpenSea works is to transfer your NFT or WETH through "authorizations", which are special smart contract functions that you call directly on the token contract. it says:
"Token contract, please allow my funds or JPG to be used by this market contract."
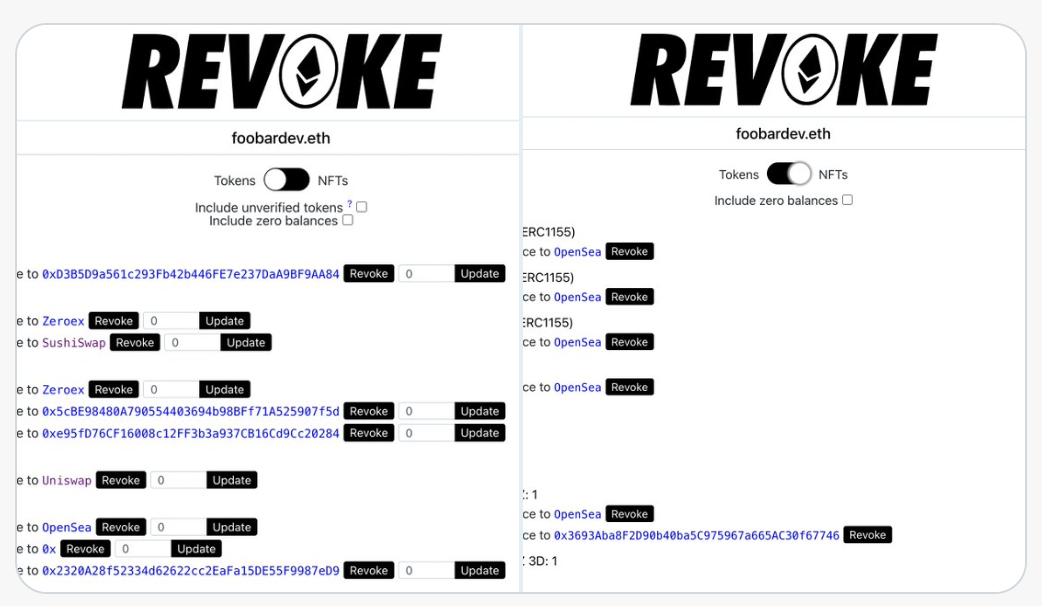
This is dangerous! But only in one direction. If the marketplace is malicious, it can steal your funds and JPGs. However, if the funds/JPGs are malicious, they "can't" steal your market.
A poorly designed marketplace may have a loophole that allows one authorized set to steal another authorized set. That's why we only use robust, well-tested sites.
Here is an example of an attack using the old Wyvern contract used by opensea:
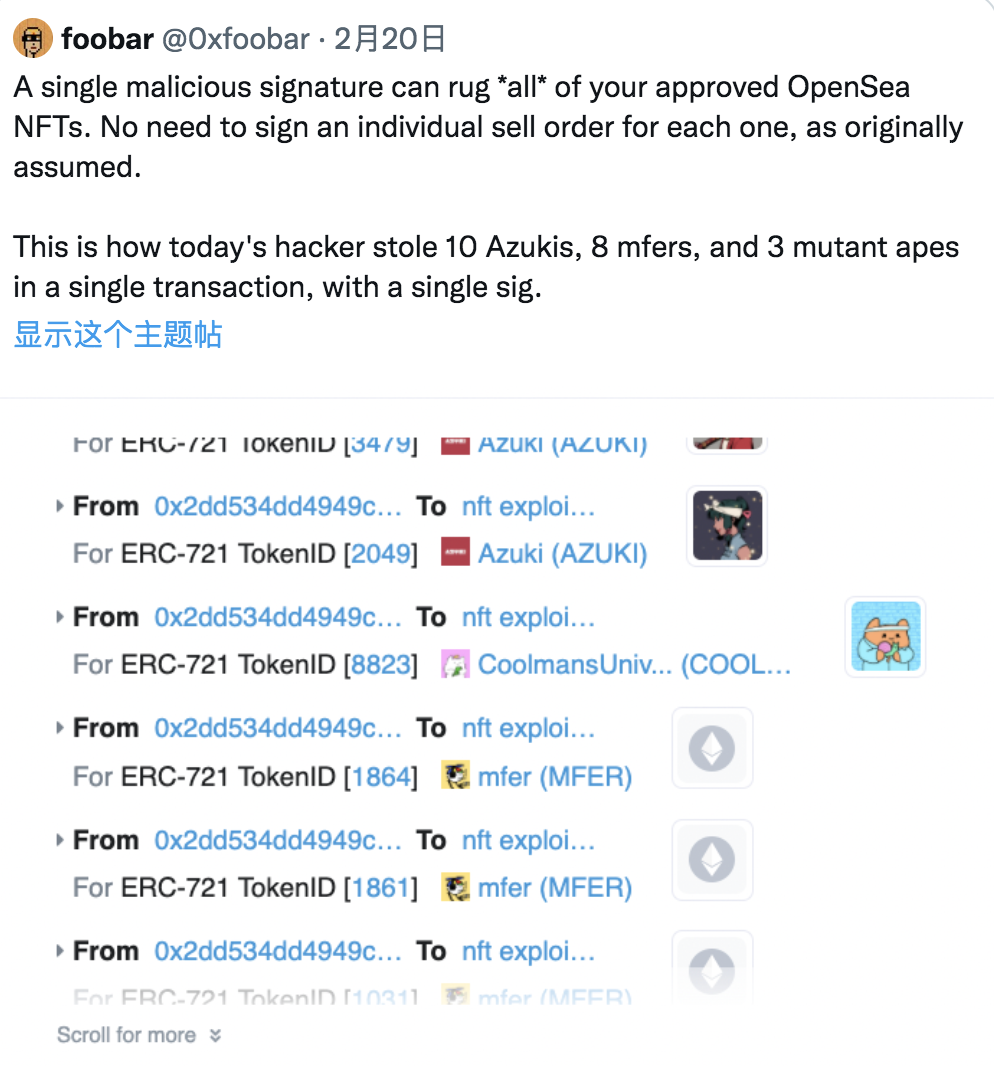
Therefore, you can only approve external contracts that use funds/JPG by calling the funds/JPG contract.
rather than by calling an external contract.
This is why in theory it is "safe" to interact with the malicious contract, provided your transaction goes directly to the malicious contract and you don't send any raw ETH to the payable function.
But be careful not to try this dangerous operation yourself.
Of course, danger occurs when people think they are interacting with an external contract, but are actually interacting with their money/JPG contract.
A website will pop up and say, "Click here to activate your ape", but the wallet transaction actually says "SET APPROVAL FOR ALL".
Under the influence of the drunk/high/drowsy/fomo combination, people sign up to give their life savings to others.
So what's the plan for these fake NFT offer games if hackers can't get control of your wallet or assets?
The malicious actors used several attack schemes:
Offer acceptance will resume when you approve the opensea market contract to use your NFT, then attempt to accept that offer. The error message will contain a URL that, if you visit the website, will try to get you to sign a malicious transaction.
NFT is a kind of proxy contract, which can be replaced with different implementation logic later.
Below is an address that receives dust transactions from 260 different addresses, each of which created a proxy contract to masquerade as a unique collection.
here
hereThere's more on the Proxy pattern.
Some believe that recent NFT proxy deployers have developed secret functionality that allows them to steal all your NFTs if you call approve on the proxy.
For the reasons mentioned above, this seems to be completely wrong.
Gas optimization is the most likely proxy usage assumption.
in conclusion:
in conclusion:
A fake WETH offer will allow you to approve the sale of that NFT, but when you try to accept the offer, the transaction will resume. This will cause you to waste gas fees, and at the same time revert messages on Etherscan to lure you to phishing websites.
Original link