foreword
Knowing that Chuangyu Blockchain Security Lab tracked and analyzed this incident for the first time.
Knowing that Chuangyu Blockchain Security Lab tracked and analyzed this incident for the first time.
basic information
basic information
Attacker address: 0x9dadbd8c507c6acbf1c555ff270d8d6ea855178e
tx:0x9b16b1b3bf587db1257c06bebd810b4ae364aab42510d0d2eb560c2565bbe7b4
CommunityFund contract: 0xEca7fC4c554086198dEEbCaff6C90D368dC327e0
Vulnerability analysis
Vulnerability analysis
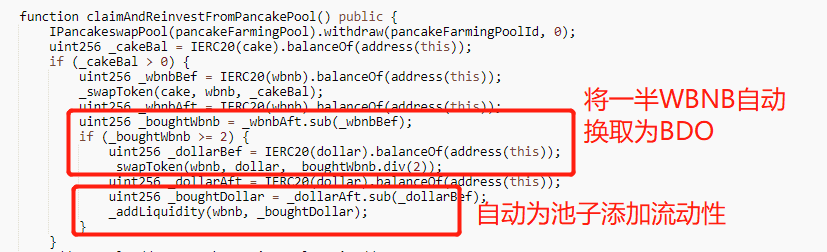
The key to the vulnerability is that the claimAndReinvestFromPancakePool method in the CommunityFund contract will judge the amount of WBNB exchanged when using Cake tokens for token conversion, and will automatically exchange half of the exchanged WBNB for BDO tokens; and then the contract will automatically use the contract The WBNB in the pool adds liquidity to the pool. If the value of the BDO token is maliciously raised at this time, this will cause the project side to use more WBNB to add liquidity to the pool.
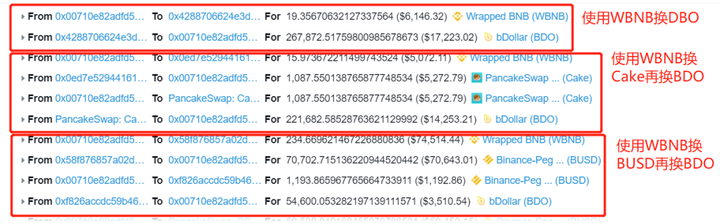
The most critical thing is that before the attack, the attacker exchanged a large number of BDO tokens in the WBNB/BDO, Cake/BDO, and BUSD/BDO pools, which caused the price of BDO to be raised.
After we analyzed the attack transaction many times, we found that the matter was not that simple. The attack was most likely to be preempted by the preemptive robot. The basis is as follows:
1. The gas fee for this attack transaction is much higher than that of ordinary transactions on the BSC chain. The default gas fee for ordinary transactions on the BSC chain is 5Gwei, but this transaction is as high as 2000Gwei.
3. We found the address and transaction of the real attacker in the same block, and the transaction was rolled back.
attack process
attack process
1. The attacker used flash loan to loan 670 WBNB;
2. Afterwards, the attacker exchanged WBNB for a large number of BDO tokens in various pools;
3. Then the attacker used flash loan again to loan 30516 Cake tokens;
4. Swap the loaned Cake tokens to exchange for 400WBNB, 200 of which will be automatically exchanged for BDO tokens by the agreement;
6. Finally, the attacker exchanged the appreciated 3,228,234 BDO tokens for 3,020 WBNB, repaid 671 flash loans, and successfully arbitraged 2,381 WBNB worth about $730,000.

Summarize
Summarize
The core of this attack is that the contract will automatically replenish liquidity for the liquidity pool without considering whether the price of the token is out of balance, which may lead to the project party supplementing liquidity at a high price and taking orders at a high price.
It is recommended that the project party pay more attention to the logic implementation of the function when writing the project, and consider the various attack situations that may be encountered.