foreword
foreword
Know that Chuangyu Blockchain Security Lab tracked and analyzed this incident for the first time.
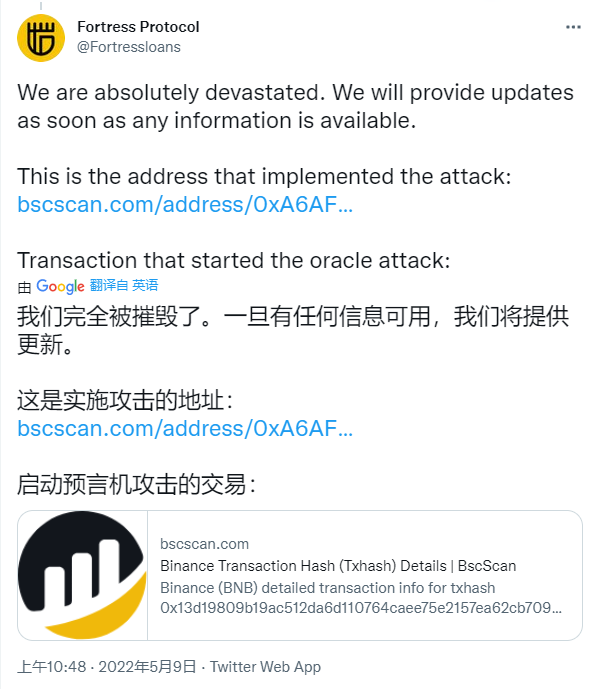
basic information
basic information
Attacked Comtroller: 0x01bfa5c99326464b8a1e1d411bb4783bb91ea629
Attacked oracle address: 0xc11b687cd6061a6516e23769e4657b6efa25d78e
Attack contract: 0xcD337b920678cF35143322Ab31ab8977C3463a45
tx:0x13d19809b19ac512da6d110764caee75e2157ea62cb70937c8d9471afcb061bf
Vulnerability analysis
Vulnerability analysis
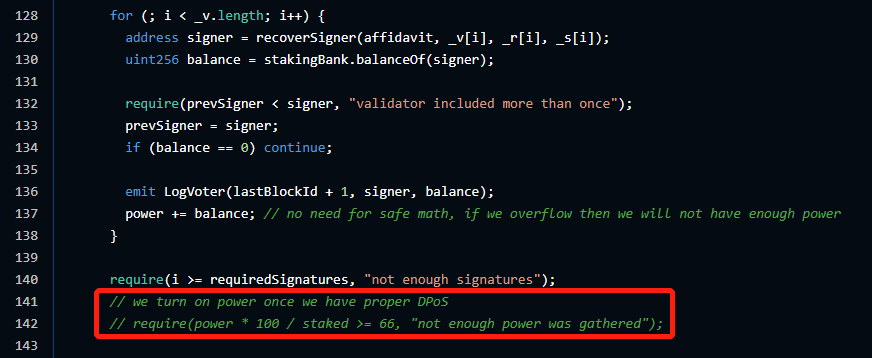
The attacker borrowed assets from other pools by changing the price of FTS in the agreement. The loan pools in the market are as follows:
attack process
attack process
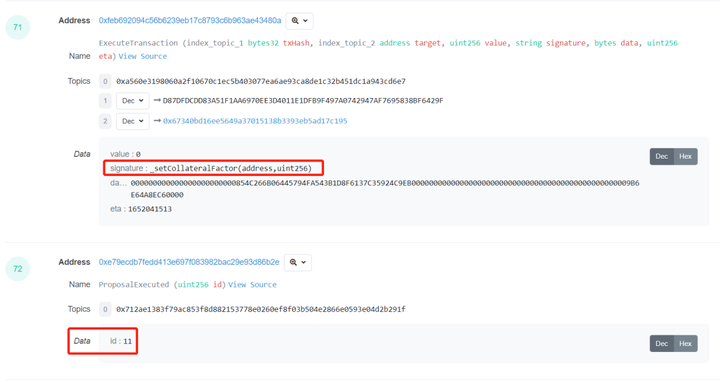
1. The attacker purchased FTS tokens and voted for adding FTS as collateral through a proposal, and the proposal ID is 11;
2. Change the price of FTS by calling the oracle submit function;
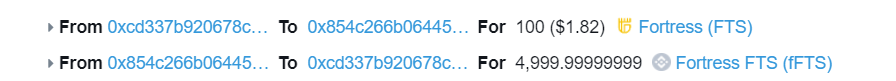
3. The attacker uses 100 FTS as collateral to call enterMarket to enter the market;
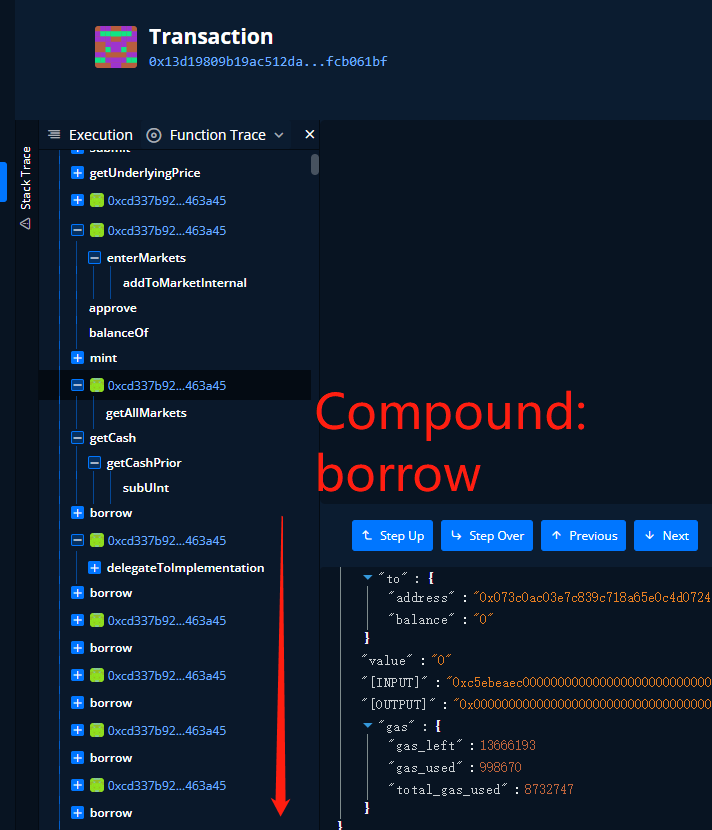
4. Due to problems in the calculation of the value of FTS by the market price, the attacker uses the collateral to directly call borrow to borrow;
5. Since the 100 FTS has no value and does not need to be retrieved, the attacker will still use the other FTS used in the first step to completely cash out in the Pancake exchange.
Summarize
Summarize
The reason for this attack is that there is a problem with the use of the Compound imitation disk in the oracle. Recently, a large number of Compound imitation disk projects have been attacked. We urge all project parties that forked Compound to take the initiative to conduct self-examination. The currently known attacks are mainly due to the following problems: