background
background
The world of blockchain follows the law of the dark forest. In this world, we may suffer from unknown external attacks at any time. As ordinary users, we do not do evil, but it is very necessary to understand the way hackers do evil.
The SlowMist security team previously releasedBlockchain Dark Forest Self-Help Manual, which mentioned a lot of methods of attacking the Discord of the NFT project party. In order to help readers have a clearer understanding of the relevant phishing methods, this article will expose one of the phishing methods, which is to steal projects through malicious bookmarks. The Token of the party's Discord account is used to publish false information to induce users to visit phishing websites, thereby stealing users' digital assets.
fishing incident
image description
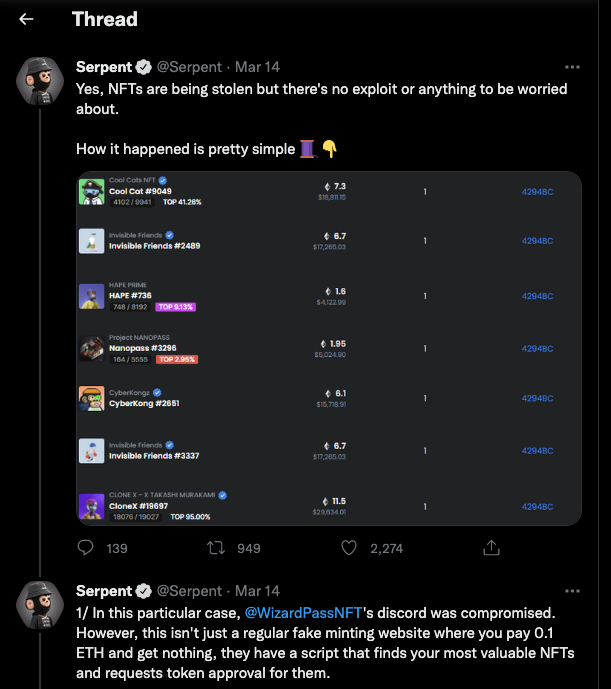
Source: https://twitter.com/SerpentAU/status/1503232270219431941
image description
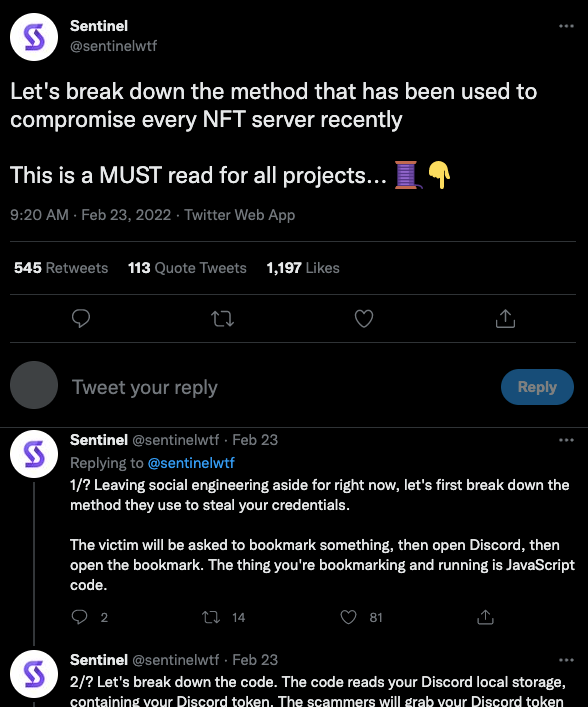
Source: https://twitter.com/sentinelwtf/status/1496293768542429187
The bookmark mentioned in this interpretation is a browser bookmark. The content of this bookmark can be a piece of JavaScript malicious code. When a Discord user clicks, the malicious JavaScript code will be executed in the Discord domain where the user is located, and the Discord Token will be stolen. The attacker will get After the Discord Token of the project party can directly and automatically take over the relevant permissions of the Discord account of the project party.
background knowledge
To understand this incident, readers need to have certain background knowledge. Today's browsers have their own bookmark managers, which provide convenience but are also easy to be exploited by attackers. By carefully constructing a malicious phishing page, you can insert a piece of JavaScript code into your favorite bookmark. When the victim clicks on the bookmark, it will be executed in the domain of the current browser tab.
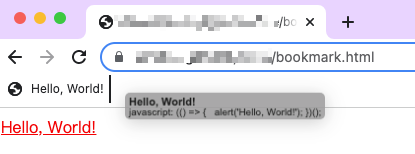
Take the above picture as an example. The victim opened the official website of discord.com, and clicked the malicious bookmark “Hello, World!” on this page to execute a pop-up statement. It can be found that the source of execution shows discord. com.
There is a domain concept here. Browsers have protection policies such as the same-origin policy. Logically, operations that do not belong to discord.com should not respond to pages in the discord.com domain, but bookmarks bypass this restriction.
It is foreseeable that such a small function of bookmarks implies security issues. The normal way of adding bookmarks will clearly see the bookmark URL:
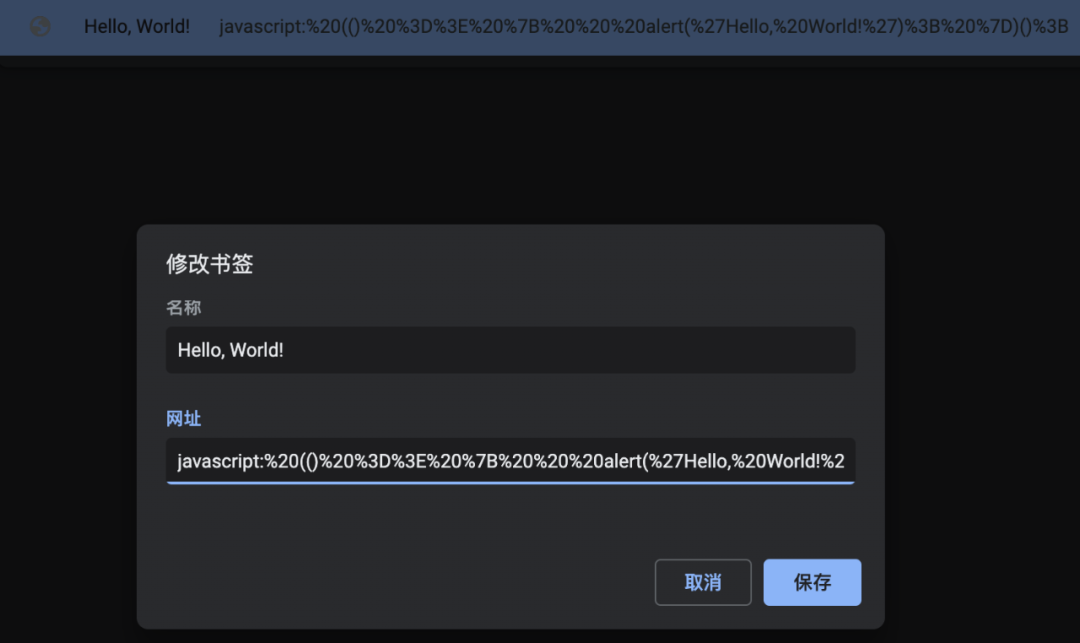
Readers with a little security awareness should directly see that there is an obvious problem with the URL information.
Of course, what if it is a well-structured structure that induces you to drag and drop the collection to the bookmark bar to the page? You can see that the demonstration video in the Twitter link has constructed such an inductive page: "Drag this to your bookmarked".
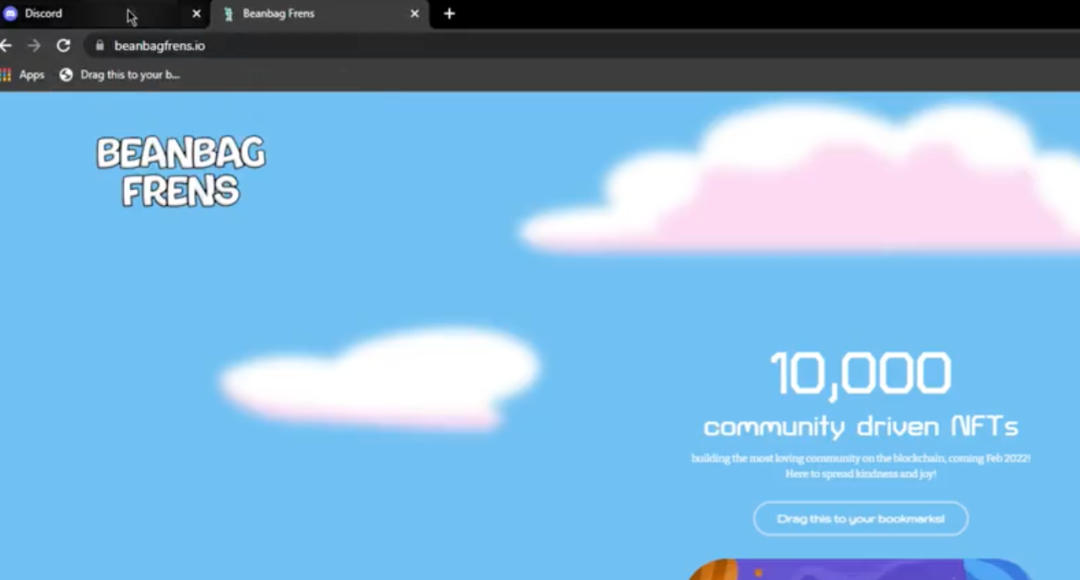
That is to say, you can add a link to the bookmark bar by dragging a link. As long as the phishing script is realistic enough, it is easy for users with insufficient security awareness to be recruited.
To add to the bookmark bar by dragging and dropping, you only need to construct an a tag. The following is the sample code:
Bookmarklets can execute like code in the developer tools console when clicked, and will bypass CSP (Content Security Policy) policies.
Readers may have doubts. When a link like "javascript:()" is added to the browser bookmark bar, the browser will not give any reminder?
The author compares Google and Firefox browsers here.
Using Google Chrome, drag and drop to add a normal URL link without any editing reminder.
Using Google Chrome, drag and drop to add malicious links will also not have any editing reminders.
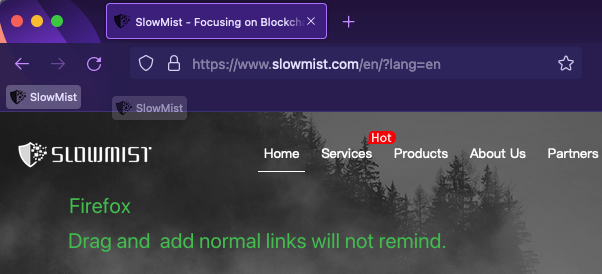
If you use Firefox browser, if you add a normal link, there will be no reminder.
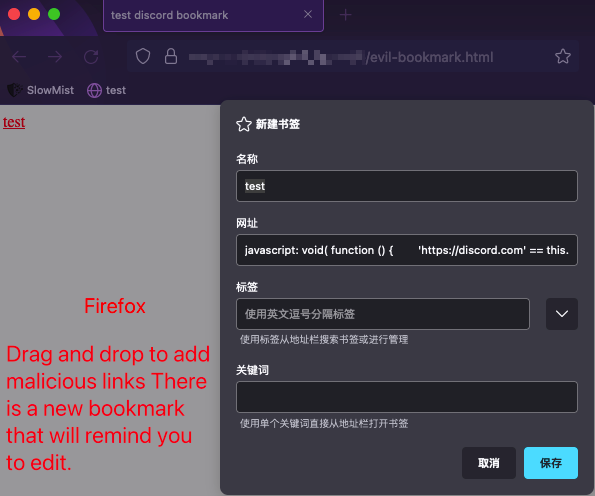
Using the Firefox browser, if you add a malicious link, a window will appear reminding the editor to confirm the save.
It can be seen that the processing security of the Firefox browser is higher in the aspect of adding bookmarks.
Scenario demo
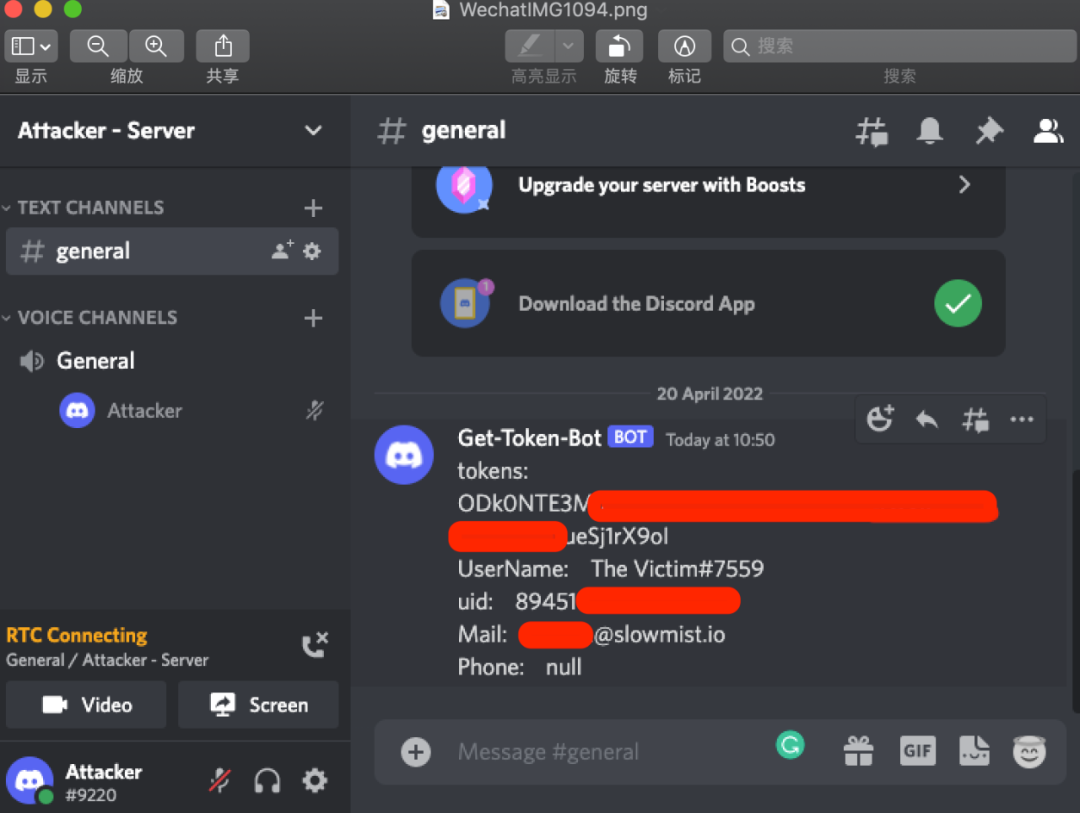
The demo uses Google Chrome. On the premise that the user logs in to Discord on the web, it is assumed that the victim has added a malicious bookmark under the guidance of the phishing page. Personal information such as Token will be sent to the attacker's channel through the Discord webhook set by the attacker.
The following is a demonstration of the JavaScript code written by the attacker to obtain Token and other personal information, and receive it through the webhook of the Discord Server.
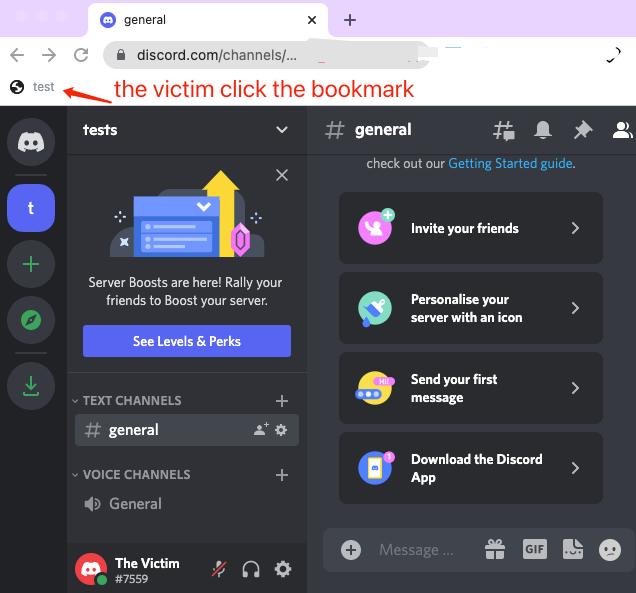
The following is a demonstration of the JavaScript code written by the attacker to obtain Token and other personal information, and receive it through the webhook of the Discord Server.
The author adds a few attack details that may cause doubts:
1. Why did the victim get it after one click?
We know from the background knowledge that a bookmark can be inserted into a JavaScript script. With this, you can do almost anything, including obtaining information through the webpackChunkdiscord_app front-end package packaged by Discord. However, in order to prevent evil from happening, the author will not give you the detailed attack code. out.
2. Why would the attacker choose Discord webhook to receive?
Because the format of the Discord webhook is
"https://discord.com/api/webhooks/xxxxxx" is directly the main domain name of Discord, bypassing issues such as the same-origin policy. Readers can create a new Discord webhook for testing.
3. What can I do if I get the Token?
Summarize
Summarize
Attacks are happening all the time. For users who have suffered malicious attacks, it is recommended to take the following actions immediately to remedy:
Reset your Discord account password immediately.
After resetting the password, log in to the Discord account again to refresh the Token, so as to invalidate the Token obtained by the attacker.
Delete and replace the original webhook link, because the original webhook has been compromised.
Improve security awareness, check and delete malicious bookmarks that have been added.
As a user, it's important to be aware that any additions and code can be malicious, and there are plenty of extensions on the web that look very friendly and flexible. Bookmarks cannot prevent network requests. At the moment when the user manually triggers the execution, it is still necessary to maintain a suspicious heart.