Attacked contract
#1 Event Related Information
attack transaction
0xcd314668aaa9bbfebaf1a0bd2b6553d01dd58899c508d4729fa7311dc5d33ad7
attacker address
0x1c5dcdd006ea78a7e4783f9e6021c32935a10fb4
attack contract
0x79224bC0bf70EC34F0ef56ed8251619499a59dEf
Attacked contract
0xc1e088fc1323b20bcbee9bd1b9fc9546db5624c5
#2 Attack Process
1. The attacker initiated a proposal transaction from the day before the attack, and the funds in the Beanstalk: Beanstalk Protocol contract will be withdrawn if the proposal is approved.
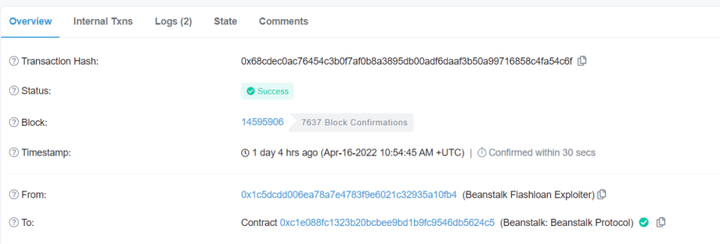
2. The hacker exchanged 350,000,000 DAI, 500,000,000 USDC, 150,000,000 USDT, 32,100,950 BEAN, and 11,643,065 LUSD as capital reserves through flash loans.
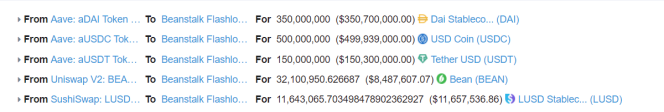
3. The hacker added the 2-step DAI, USDC, and USDT funds to the Curve.fi DAI/USDC/USDT trading pool as 979,691,328 3Crv liquidity tokens, and exchanged 15,000,000 3Crv for 15,251,318 LUSD.
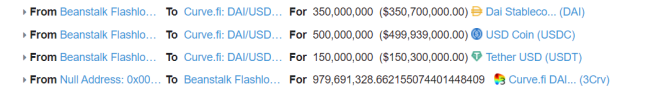
4. Exchange 964,691,328 3Crv tokens for 795,425,740 BEAN3CRV-f for voting, add 32,100,950 BEANs and 26,894,383 LUSD to get 58,924,887 BEANLUSD-f liquidity tokens.


5. Use BEAN3CRV-f and BEANLUSD-f in step 4 to vote on the proposal, resulting in the proposal being passed. Thus, the Beanstalk: Beanstalk Protocol contract transferred 36,084,584 BEANs, 0.54 UNI-V2, 874,663,982 BEAN3CRV-f and 60,562,844 BEANLUSD-f to the attack contract.
6. Finally, the attacker removed the liquidity and returned the flash loan, and converted the excess tokens into 24,830 ETH and transferred them to the attacker's account.
#3 Vulnerability Analysis
This attack mainly uses the number of votes in the voting contract to be obtained based on the amount of tokens held in the account.
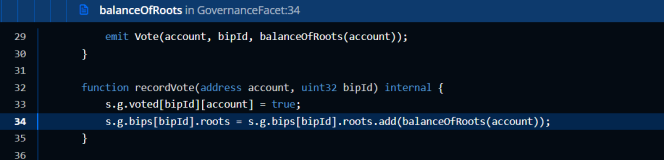
The attacker initiated a proposal to withdraw funds from Beanstalk: Beanstalk Protocol at least one day ago, and then called emergencyCommit to perform an emergency commit to execute the proposal. This is the reason why the attacker launched an attack preparation 1 day ago.
#4 Funds Tracking
In response to this incident, the Chengdu LianAn technical team suggested:
In response to this incident, the Chengdu LianAn technical team suggested:
1. The funds used for voting should be locked in the contract for a certain period of time, avoid using the current fund balance of the account to count the number of votes, so as to avoid possible repeated voting and use flash loans for voting;
2. The project party and the community should pay attention to all proposals. If the proposal is a malicious proposal, it is recommended to take timely measures during the proposal voting period, discard the proposal, and prohibit it from accepting votes and execution;
3. Consider prohibiting contract addresses from participating in voting; in addition, it is best to conduct a comprehensive security audit before the project goes online to avoid security risks.