
Chengdu Lianan newly launched the "Security Research Quarterly" column, which will take stock of the global blockchain security situation every quarter.
first level title
1. Overview of blockchain security ecology in Q1 2022
Losses from security incidents amounted to approximately $1.2 billion
In the first quarter of 2022, according to the statistics monitored by Chengdu Lianan [Chain Bing-Blockchain Security Situational Awareness Platform],The loss caused by attack security incidents is as high as about US$1.2 billion, which is about 9 times higher than the US$130 million in the same period last year (Q1 2021).It's also a higher amount than lost in any quarter in 2021.
secondary title

From the point of view of the chain platform
secondary title
From the perspective of capital flow
secondary title
From the point of view of attack method
secondary title
From the point of view of audit
secondary title
From the project type
first level title

2. More than 30 typical attack incidents occurred in Q1
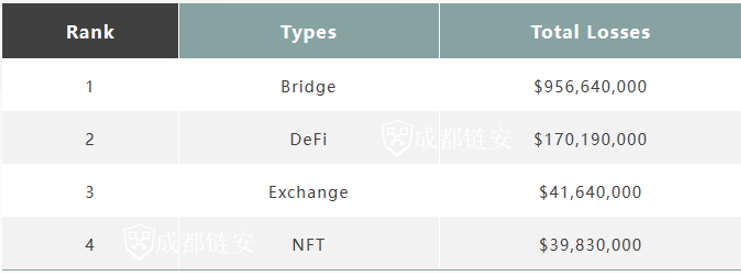
Cross-chain bridge projects suffer heavy losses
In the first quarter of 2022, there will be about 30 typical security incidents in the blockchain field. The total loss amount is approximately$1.2 billion, compared to the same period last yearincreased by 823%。
Among the top 20 rankings, Ronin with the highest loss amount is625 million, which is about the lowest amount of Build Finance ($1.12 million)558 times。
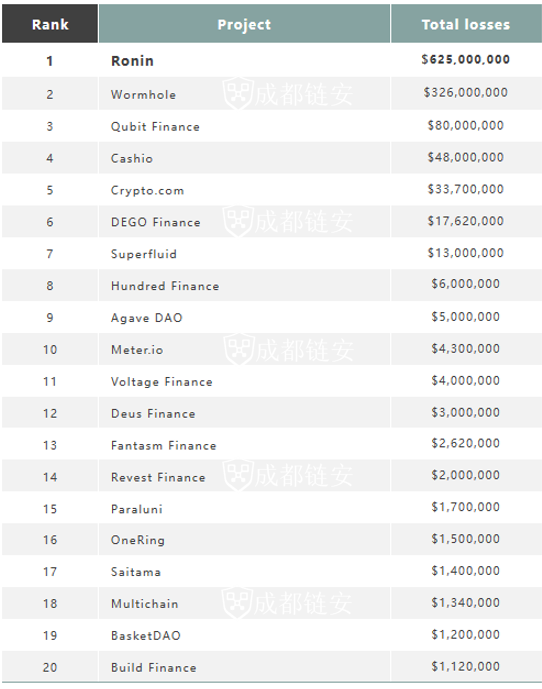
As can be seen from the statistical chart, the loss amount of the two projects Ronin and Wormhole has reached$950 million, accounting for 80% of the total loss in Q1 in 2022.first level title
3. Types of attacked projects
DeFi remains an area of focus for hackers
In the first quarter of 2022, in the blockchain field, DeFi projects are still the key areas of hacker attacks. A total of 19 security incidents occurred, and about 60% of the attacks occurred in the DeFi field.
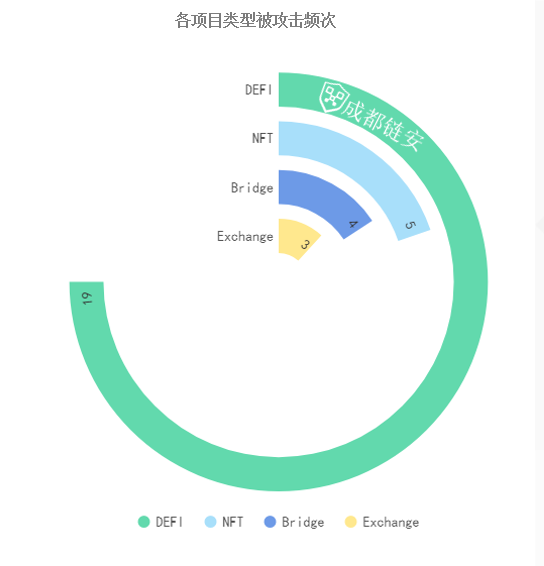
In addition, attacks against NFTs increased in the first quarter of 2022, and the cross-chain bridge project was attacked 4 times, causing lossesUp to $950 millionfirst level title
4. The loss amount of the chain platform
Ethereum has the highest proportion of losses
Q1 2022,The attack losses on the Ethereum and Solana chains ranked the top 2, with USD 654.48 million and USD 374 million respectively.
Ethereum is also the most frequently attacked, accounting for 45% of the total frequency; the second is BNB Chain, accounting for 19%.
Both attacks on the Solana chain resulted in huge losses: $326 million for Wormhole and $48 million for Cashio. The attack methods of both are the sameimage description。
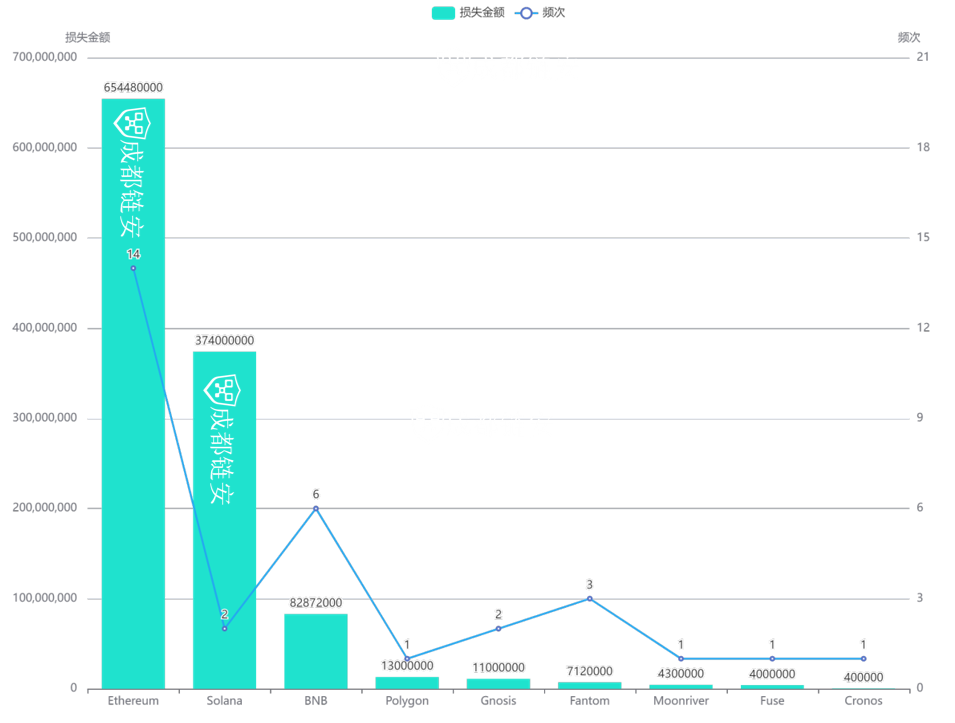
Chain platform loss ratio
first level title
5. Analysis of attack methods
Contract exploits and flash loans are the most common
In the first quarter of 2022, in the field of blockchain security ecology, about 50% of the attack methods are contract vulnerability exploits, and 24% of the attack methods are flash loans.
12% of the attacks were private key leaks, phishing attacks and social engineering attacks. This type of attack stems from the failure of the project party to keep the private key or lack of vigilance.
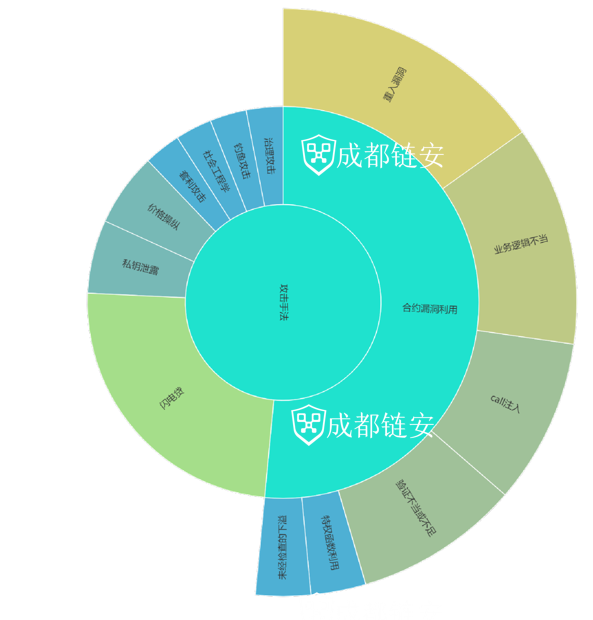
Among the contract loopholes exploited by hackers, the most common loopholes areReentrancy Vulnerabilities (30%), followed byImproper business logic (24%), call injection attacks (18%), and poor or insufficient validation (18%)first level title
secondary title
background:
background:
Details:
Details:
image description
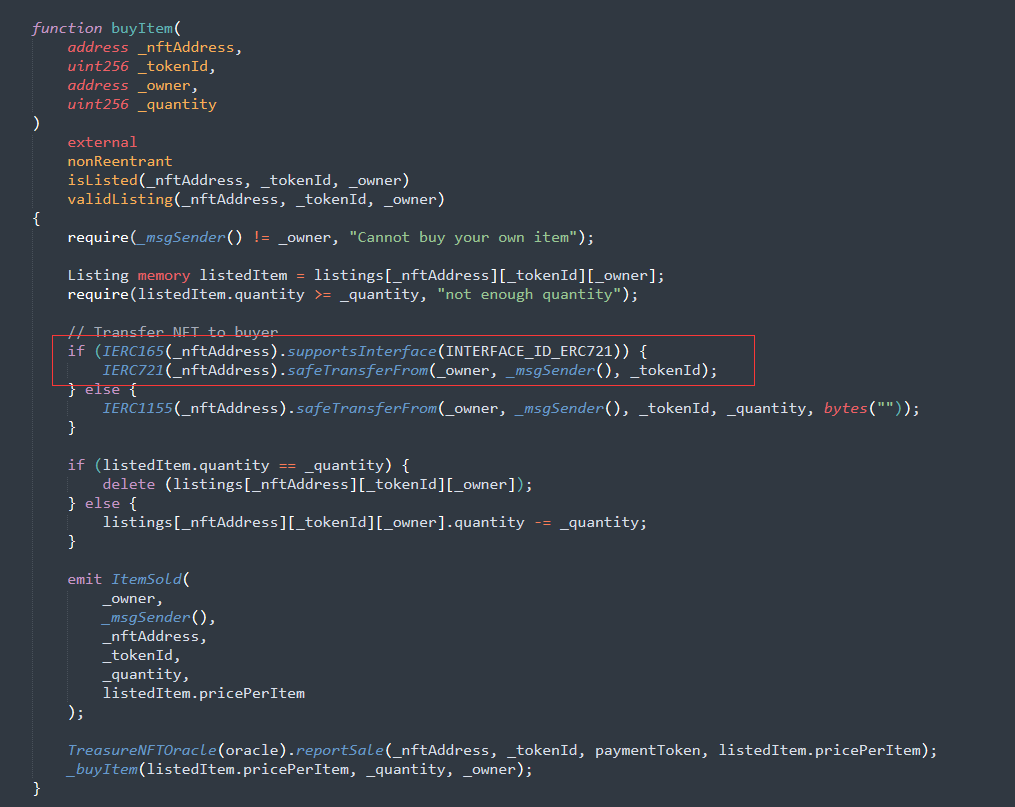
The buyItem function code of the item contract
From the code point of view, the buyItem function of the contract does not judge the token type after passing in the _quantity parameter, and directly multiplies _quantity and _pricePerItem to calculate the totalPrice, so the safeTransferFrom function can be paid in ERC-20 tokens When the amount is only 0, call the contract's buyItem function to purchase tokens.
suggestion:
suggestion:
The main reason for this security incident is the logical confusion caused by the mixed use of ERC-1155 tokens and ERC-721 tokens. ERC-721 tokens do not have the concept of quantity, but the contract uses quantity to calculate the purchase price of tokens. Finally, in There is also no taxonomy discussion when tokens are transferred.
secondary title
background:
background:
Details:
Details:
image description
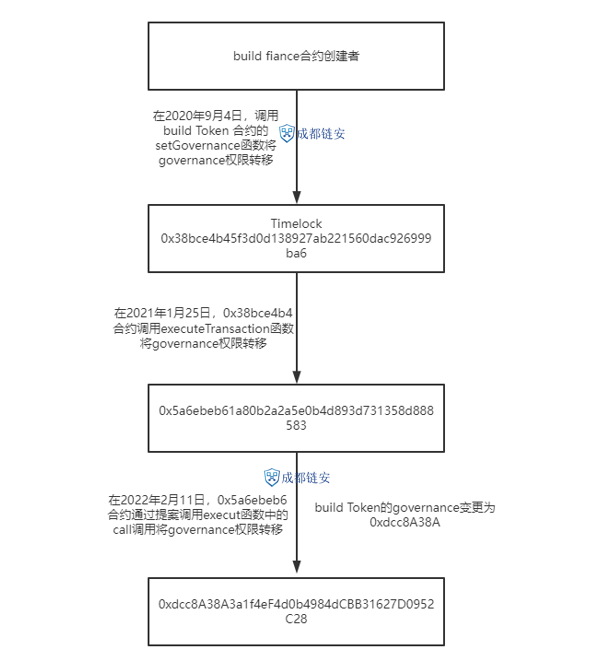
Process of Build Finance being attacked
suggestion:
suggestion:
secondary title
background:
background:
Details:
Details:
image description
suggestion:
suggestion:
1. Pay attention to the security of the signature server;
2. When the signature service goes offline, the policy should be updated in time, the corresponding service module should be closed, and the corresponding signature account address can be considered discarded;
3. During multi-signature verification, the multi-signature services should be logically isolated, and the signature content should be verified independently. It cannot happen that some verifiers can directly request other verifiers to sign without being verified;
first level title
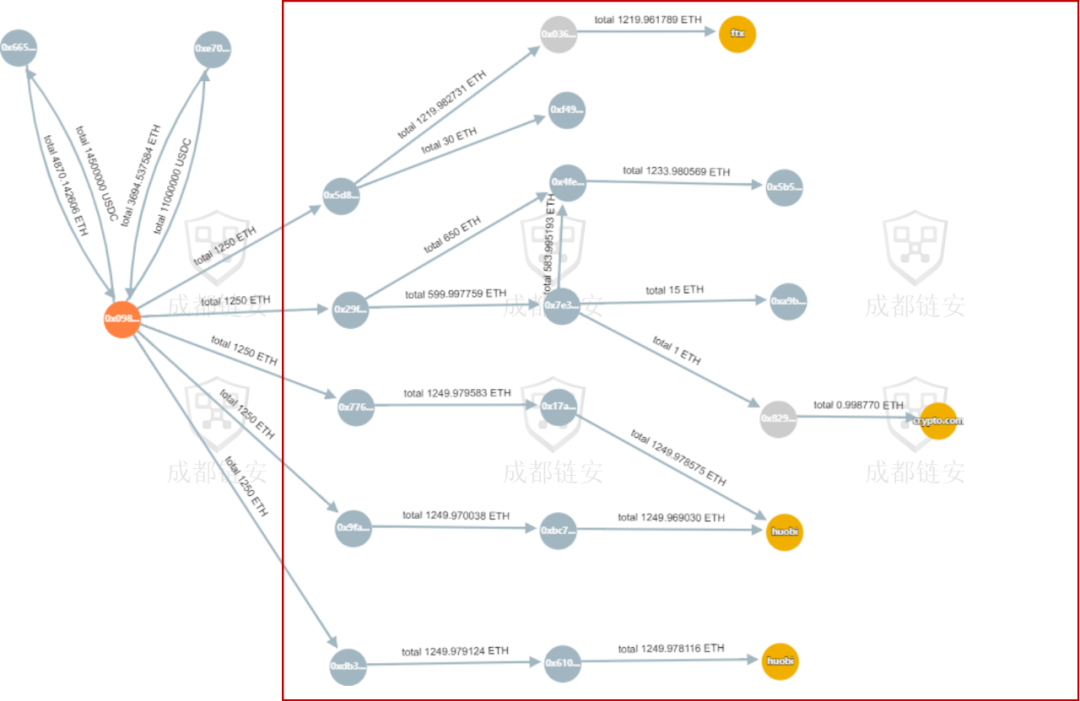
7. Analysis of the flow of stolen funds
Tornado.Cash may be the usual way for hackers to launder money
In 80% of cases, hackers will transfer the stolen funds to Tornado.Cash for currency mixing immediately or within a few days after they succeed.
In 10% of cases, hackers will temporarily leave the stolen funds in their own addresses and wait for months to years before transferring the funds. For example, the AscendEX exchange that was stolen in December last year, hackers waited until February and March this year to start laundering money in batches. This year, Ronin attackers are still carrying out frequent money laundering operations.
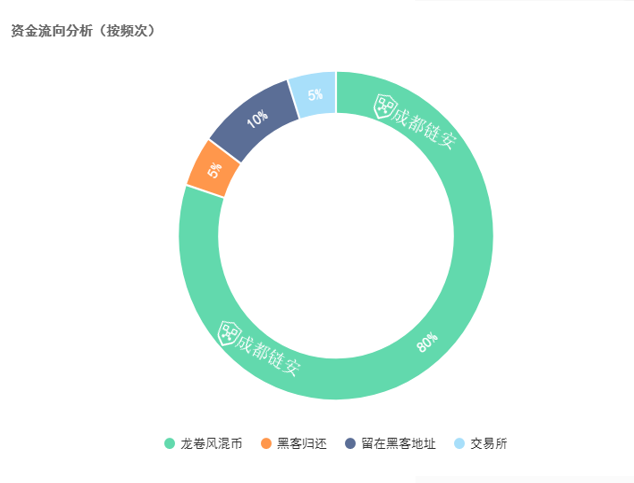
A small number of hackers will return stolen funds. After stealing $48 million in funds, Cashio's attacker publicly stated that he would refund to accounts worth less than $100,000, and claimed that "my purpose is to take money from people who don't need it, not from people who need it." where people take money."
first level title
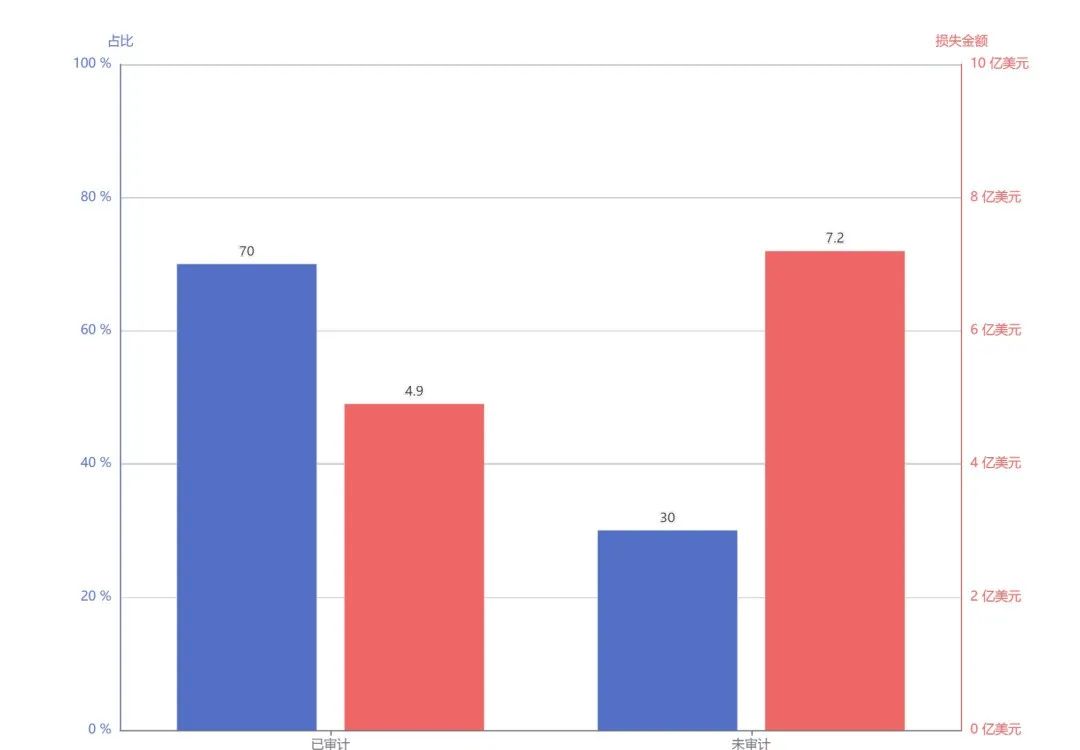
Eight, project audit situation analysis
30% of the unaudited project loss accounted for 60% of the total
Project Audit Status:
70% of the attacked projects have been audited by third-party security companies;
30% of unaudited projects, the loss amounted to 720 million US dollars, accounting for 60% of the total loss amount in the first quarter;
image description
first level title
9. Conclusion of Q1 in 2022
Security incidents occur frequently, and the amount involved has increased significantly
In the first quarter of 2022, the losses caused by attacks on security incidents in the blockchain field are as high as about 1.2 billion US dollars, which is higher than the amount lost in any quarter in 2021. Cross-chain bridge projects have been stolen with a huge amount, and DeFi projects have been attacked most frequently. These two areas may also be the focus of hackers in the future.
The project party should pay attention to the abnormal situation of funds in a timely manner. Chengdu Lianan [Chain Bing-Blockchain Security Situation Awareness Platform] can allow the project party and users to discover risky transactions in a timely manner, so as to quickly take measures. For example, immediately suspend related services, or inform users to cancel authorization, etc., to avoid subsequent greater losses.
Project security audits are still important. About 50% of the attack methods are contract exploits, and most of these vulnerabilities can be discovered and repaired early through security audits.