This morning, the suspected bug in OpenSea has aroused a lot of attention and heated discussions.
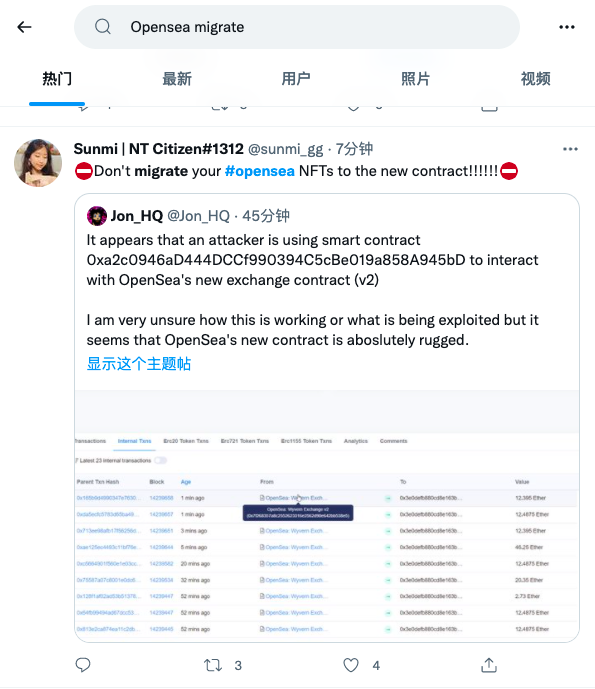
The cause of the incident was that a number of users tweeted this morning to warn that the new migration contract (address: 0xa2c0946aD444DCCf990394C5cBe019a858A945bD) launched by OpenSea yesterday was suspected to have a bug, and the attacker (address: 0x3e0defb880cd8e163bad68abe66437f99a7a8a74) was Use this bug to steal a large number of NFTs and sell them for arbitrage .
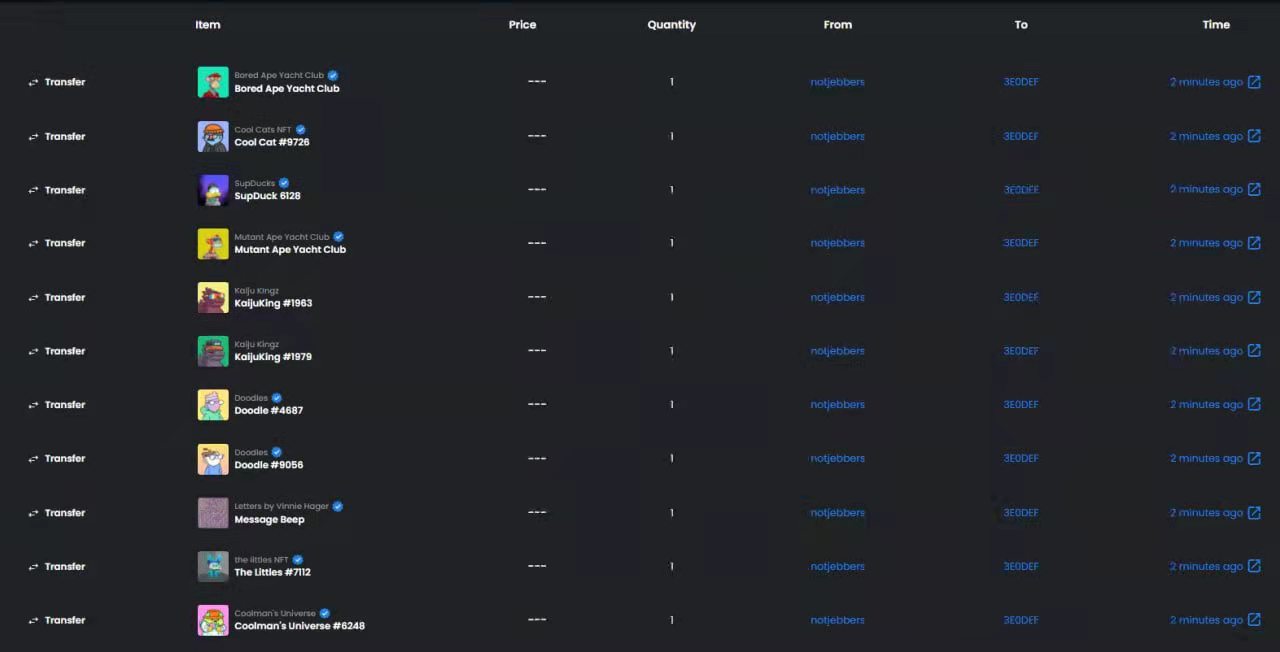
Judging from the screenshots of the attacker’s wallet, the currently stolen NFT covers a variety of high-value series such as BAYC, BAKC, MAYC, Azuki, Cool Cats, Doodles, Mfers, etc. Some of them have been sold at the floor price, but some have been reversed. Return the stolen address (the hacker also sent some ETH to some of the stolen users).
The so-called migration contract comes from a new upgrade released by OpenSea yesterday. Yesterday, OpenSea announced that its smart contract upgrade has been completed, and the new smart contract has been launched. Users need to sign a pending order migration request to migrate the smart contract. Signing this request does not require Gas fees, and there is no need to re-approve NFT or initialize the wallet. During the migration, quotes on the old smart contract will be invalidated. The English auction will be temporarily disabled for a few hours after the contract upgrade is completed. After the new contract takes effect, you can create a new timed auction again. The Dutch auction for existing smart contracts will expire at the end of the migration period at 3:00 on February 26, Beijing time.
After the incident, OpenSea responded on its official Twitter: "We are actively investigating rumors related to OpenSea smart contracts. This looks like a phishing attack from outside the OpenSea website. Do not clickhttp://opensea.ioAny link other than . "
Alchemix, Sushiswap contributor, Twitter user @0xfoobar also posted a personal investigation on the matter on Twitter after the incident. @0xfoobar said that the hacker used the auxiliary program contract deployed 30 days ago to call the OpenSea contract deployed 4 years ago. The auxiliary contract also has valid atomicmatch() data, which may have started a few weeks ago. Attack, hackers are rushing to attack before all pending orders expire.
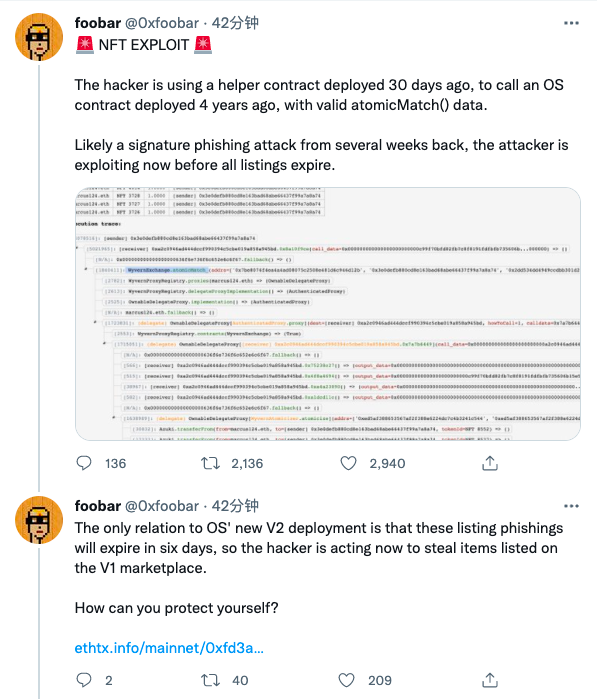
@0xfoobar further analyzed that the only relationship between this matter and OpenSea's new migration contract is that all historical pending orders will expire within 6 days after the OpenSea smart contract is upgraded, which also includes all orders from addresses that have been breached by phishing Pending orders, so the hacker had to act immediately. In other words, this is a phishing attack, not a general smart contract vulnerability, and there is nothing wrong with OpenSea's contract.
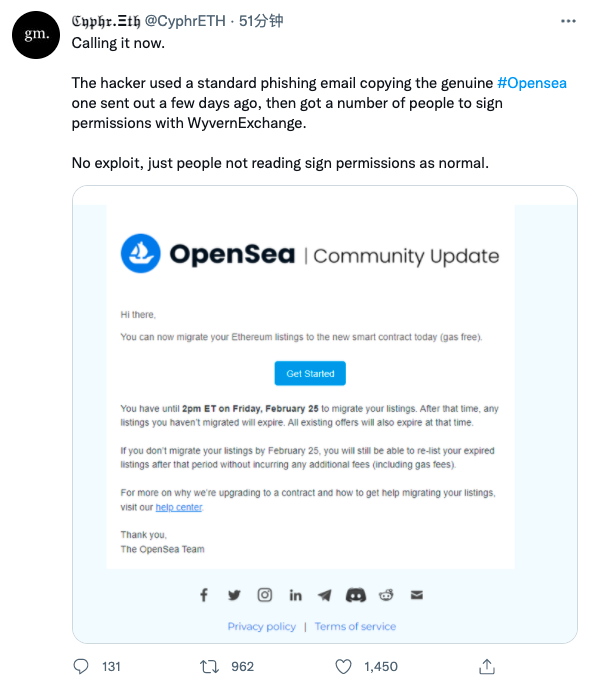
@0xfoobar's analysis coincides with some other big V's. Cyphr.ETH, the founder of gmDAO, tweeted that hackers used standard phishing emails to copy genuine OpenSea emails sent a few days ago, and then let some users use WyvernExchange Sign permissions. OpenSea isn't vulnerable, it's just that people don't have permission to read signatures like they usually do.
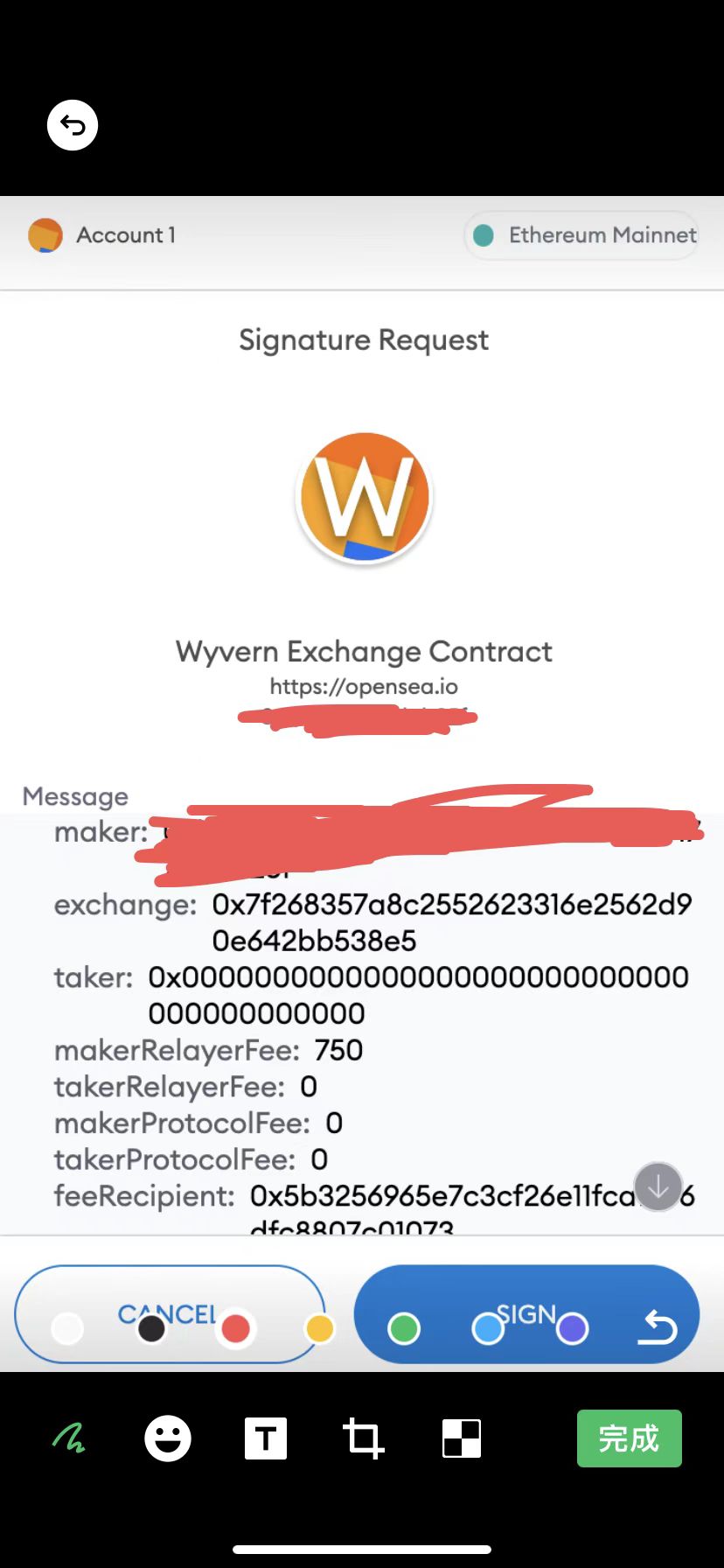
So far, the cause of this security incident has been basically clear. The affected groups are users who have clicked on the above email and signed the permission. For safety reasons, it is recommended that these users temporarily revoke all authorizations of OpenSea. Available contract authorization signing tools includehttps://revoke.cash/orhttps://zapper.fi/revokeorhttps://etherscan.io/tokenapprovalcheckerorhttps://approved.zone/orhttps://tac.dappstar.io/#/, some websites may not be able to open due to the current heavy traffic, you can try more.