Table of contents:
Table of contents:
1. Is Ethereum really completely decentralized?
2. Pocket Network--Web 3's answer to Amazon Web Services(AWS)
3. Why Pocket Network?
4. Pocket's basic operating mode & how does Pocket ensure security?
5. POKT Token Economic Model
6. Pocket Team Introduction & Community Overview
7. Pocket ecology and partners & top of Web3Index
8. References
While most technologies tend to automate pointless work by workers around them, blockchain automation is decentralized, and instead of putting taxi drivers out of work, blockchain enables them to work directly with customers -- -- Vitalik Buterin
secondary title
1. Is Ethereum really completely decentralized?
According to Chainstack data (2019), the top ten cloud hosting providers run about 57% of Ethereum nodes, of which 24.6% are running on AWS (Amazon Web Services). From the perspective of country distribution, the United States and The data centers in Germany run 37.05% and 16.66% of the Ethereum nodes respectively. It is said that the globalized Ethereum is "half of the country" by the two countries. This means a major single point of failure, especially when a cloud platform monopoly shuts down due to interruptions or errors, the entire Ethereum will be greatly affected, but Node Provider, the infrastructure behind a technology platform that focuses on the concept of decentralization, is like this Centralization is embarrassing.
secondary title
2. Pocket Network--Web 3's answer to AWS
Pocket Network is a decentralized API infrastructure built for Web3 applications, providing a trustless API layer for easy access to any blockchain.

The service layer of Pocket Network consists of two main actors: applications and validators. An application submits a relay request, or an API request is routed to any relay chain. Validators "serve" applications by routing relay requests to the relay chain and forwarding responses to the application. This interaction between applications and validators is a fundamental function of Pocket Network.
secondary title

3. Why Pocket Network?
Reliability: Pocket Network supports developers to maintain confidence in the operation of their own DApps and no longer depends on a single service network provider. This is achieved by creating different deployment artifacts (such as Docker, Kubernetes, Docker compose, etc.), node operators are able to install the Pocket Core software on any server or computer. At the same time, Pocket Network coordinates requests through a decentralized relay network composed of different full-node operators, which can ensure that users' applications are truly anti-censorship, elastic, and multi-point backup.
Low Network Costs: By leveraging a cryptoeconomic model that balances inflation and usage, Pocket Network is not only more affordable for developers, but also provides a sustainable growth model for full node operators of any size. Developers can access the network by staking at least 1 POKT, and pay tokens for the relay throughput allocated by the application; nodes verify each API request to obtain POKT block rewards.
secondary title
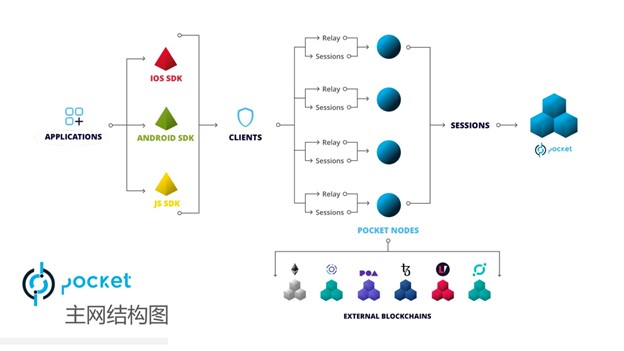
4. Basic operation mode of Pocket
1 If you want to register the decentralized infrastructure, the Application must stake the project's native token POKT in the network.
2 The number of relays approved each time is determined by the number of tokens pledged by the application in the network.
3 If you want to register the decentralized infrastructure, the Validator verifier must stake the project's native token POKT in the network.
4 In the subsequent Stake, the Application program is paired with the Validator verifier, during which interactive services are performed.
5 To provide a decentralized infrastructure, Validators will receive POKT proportional to the number of relays served per request.
To put it simply, Pocket can become a decentralized Node Provider. Even if some important nodes have problems, it will not affect the overall network operation. In this regard, it is better than Ethereum, which is deeply dependent on AWS. Much more advanced.

secondary title
1 Session Security:
How does POKT ensure security?
P(A Ç B)= P(A)P(B|A)
The probability of choosing at random without replacement is:
1/( allvals (allvals-1)(allvals-2)...*(allvals-valspersession))
Therefore, the probability of selecting any validator combination in any given Session in Pocket Network is:
2 Application Security
This means that the more validators there are in the network, the higher the level of randomization and security. The deterministic but unpredictable randomness property of Hash seed data in the session generation process ensures that no malicious participant can determine the pairing with Application and Validator, which is a common security mechanism of Pocket.
3 Validator Security
Validators do not receive POKT rewards for the services they provide when they violate protocol rules, which are enforced by validators by reporting work to the network to be validated. Examples of rule violations include:
Overservicing an Application
Incorrect App/Validator Pairing
Incorrect Relay Chain
Non-Unique Proof of Relays
Invalid Merkle Root / Proof pairings
Invalid Application Authentication Token
A minority Validator in Client-Side Validation
Invalid Servicer in Proof
Below minimum Relay count
secondary title
5. POKT Token Economic Model
POKT's innovative token economic model is very cleverly designed, and the cutting-edge token economic model redefines the payment method for applications facing blockchain infrastructure. Pocket Network has designed a unique economic model based on its token POKT, which is based on DAO, creating a decentralized trustless two-sided market between nodes and developers in its ecology, benefiting all participants .
In the Pocket ecosystem, developers and nodes have an indispensable rigid demand for token holding.
[Developers] POKT tokens are needed to implement API requests to obtain decentralized API request services with higher efficiency and lower cost.
[Node] It is necessary to hold a certain amount of POKT tokens to provide node services, and obtain POKT rewards by providing and implementing developers' API requests.

Since each side of the market has its own unique incentives, the bids on both sides are also different. The total supply will be limited through a burn mechanism established by a DAO that controls token policy. The final total supply of POKT will be determined by DAO.
There are two different types of stake functions in Pocket: StakeApp() and StakeNode(). Both stake functions use POKT.
1 Application Pledge
Decentralized applications pay for services by staking POKT in advance. When they call the Stakeapp() function, the minimum staking period is 21 days. By incurring a minimal staking lock-up period, the application forgoes, as an opportunity cost, the potential to spend its resources (POKT in this case) on other alternatives. In addition, the application pays through dilution, that is, each time a relay is serviced and verified by the network, a specific amount of POKT is rewarded to the relevant service node in the next block reward.
2 Node Staking
When an application unstakes, it loses the right to continue using the relay unless the stake is reinstated.
Like the application, when the node calls the StakeNode() function, the minimum lock period is 21 days. The minimum pledge amount required to become a service node at startup is 15,000 POKT (but the official tip is preferably greater than 15,000, such as 15,100). In addition, a sufficient amount of pledge will allow the node to participate in the PoS consensus as a verification node. Not all nodes are validators, but all validators are service nodes. To become a validator node, you must be among the first 5,000 nodes on the network (as per DAO parameter voting changes). Validator nodes can get 1% of the block reward for submitting blocks.
Total supply: 650,000,000 pokt
Minting rate: 0.01POKT/ 1 successful relay
Block rewards: Node operators get 89%, block creators get 1%, and the remaining 10% goes to the Pocket DAO Foundation
Block time: 10 minutes
Minimum pledge amount for full nodes: 15,000POKT
Applied minimum pledge amount: 1POKT
Minimum unbonding period (applications and full nodes): 21 days
BaseRelay Per POKT: 1.67 relays per session
Number of nodes per session: 5 nodes
Maximum number of blockchains available for staking: 15
Session Duration: 6 blocks (60 minutes)
When applications stake POKT, the ratio of Maxrelays they have access to is locked for the entire duration of the stake. Due to the oracle problem, the protocol itself cannot infer external factors that may affect the market price of POKT. Among them, the market price fluctuation of POKT may affect the price that the application must pay for the relay. Therefore, POKT will allow the market to find a $USDPerRelay target to ensure that the actual price borne by the application is within a relatively stable and acceptable range. The DAO will achieve the goal by adjusting the variables in the protocol throttling formula.
MaxRelays=StabilityAdjustment+(ParticipationRate*BaseThroughput)
POKT uses the following formula to calculate the number of relays the application is entitled to use per session.
BaseThroughtput=BaseRelaysPerPOKT*StakedPOKT
1 BaseThroughput: BaseThroughput determines the baseline of the relay service that the application can receive for each pledged POKT, which is determined by the following formula:
BaseRelaysPerPOKT=BaseRelaysPerPOKTumerator/BaseRelaysPerPOKTDenominator
2 Stability Adjustment
Among them, BaseRelaysPerPOKT is a uint64, managed by Pocket DAO, which describes the number of relay services that the application can receive for every 1 POKT pledged.
3 Participation Rate: participation rate
Participation Rate=(appStakedPOKT+nodeStakedPOKT)/TotalPOKT
secondary title

6. Pocket Team Introduction & Pocket Community Overview
1.Michael P O'Rourke, co-founder & CEO, Michael graduated from the University of South Florida with a major in international affairs studies. After graduation, he engaged in IT development. He is also a legendary little superman. He took the lead in creating Pocket Network in April 2017, and also created the blockchain development company Nonce+1 Labs and has served as CEO until now.
2. Luis C. de Leon, CTO, graduated from Santo Domingo Institute of Technology. Luis has a bachelor's degree in systems engineering and a minor in information technology. After years of professional training in multiple positions, he is already a mature full-time Stack tech gurus. He has served as front-end development, full-stack software development, infrastructure architect and other positions in many companies. April 2016 - April 2017, he met Michael at TimeSet, reunited at Eleven Systems, and finally started a business together. Luis joined Pocket Network in February 2018.
4. Andrew Nguyen, director of blockchain & protocol development, graduated from the University of South Florida with a major in computer science in 2018. Although he is young, he has very rich experience in the blockchain industry. In 2017, he worked as a block at Nonce+1 Labs Chain engineer, and later served as core development members of BitcoinLatina Foundation/Artpiece.io, and accumulated a lot of relevant professional capabilities.
secondary title

7. Pocket ecology and partners & top of Web3Index
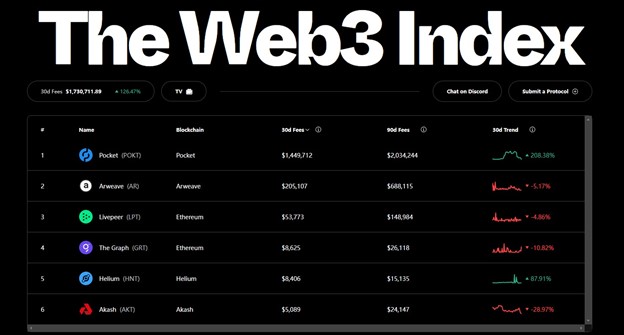
On November 16, 2021, Pocket Network, a blockchain data ecosystem for Web3 applications, was recently included in the prestigious Web3Index website along with other middleware service protocols Arweave, the Graph, Livepeer, Akash, and Hemium. Pocket topped the revenue charts as soon as it joined. Over the past 30 days, Pocket Network’s network revenue reached $18.67 million, topping the Web3Index list and on par with the top 10 blockchains and DeFi protocols.
Over the past year, Pocket has experienced exponential growth in network revenue and usage, fueled by its strategy of aggressive expansion into new blockchain ecosystems and markets, and through increased usage and node revenue resulting in network effects. In the past 3 months alone, Pocket has added support for a range of blockchains such as Harmony, IoTeX, Solana, Avalanche, Algorand, Fuse, and Polygon, with many more networks in test. Because the Pocket Network is a protocol, not a sale, it can accomplish these feats faster than its SaaS counterparts, and at an order of magnitude lower cost. This is because Pocket Network encourages independent node operators to support each blockchain, which is also the main source of network revenue.
After each (API request) relay service and verified by the node, 0.01 POKT will be minted. In this way, the reward is directly proportional to the usage and consumption of the actual blockchain network of dApps. Over the past 90 days, Pocket Network node operators have served 4.69 billion relays, earning more than $23.14 million worth of POKT.
Glossary::
Attachment 1:
Application: Application
Application Authentication Token (AAT): Each Client needs an AAT to authorize the use of the allocated "throughput". AAT functions similar to JSON Web Token (JWT) and provides security guarantees for the use of services. AAT is generated after a client acquires and holds POKT for an application.
Block Hash: The hash value of the block SHA3-256.
1 Fails to produce min_signed_per_window amount of blocks over a signed_blocks_window
2 For Double Signing a Block
Jail: When a validator is Jailed, it will remain in the Stake validator list, but cannot become a block producer or participate in Sessions. There may be two reasons for being Jailed:
POKT: the native token of the project
Relay: Blockchain API requests and responses transmitted over the Pocket Network.
Relay Chain: A single database instance, usually a blockchain, provided by the Validators that make up the decentralized infrastructure of the Pocket Network.
Relay Evidence: Evidence of Relay completion, backed by digital signatures from application clients.
ServiceURI: The endpoint where the Validator hosts Pocket RPC. A static URI (or IP) assigned to the node that applications can use to send relays to the node instead of your blockchain node URL.
Session: A relationship between an application and the validators serving it at any point in time.
Each application will only have a single Session on each Relay Chain. This means that after an application is Staked, each Relay Chain will have a corresponding application Session until it is Unstaked.
Session Block: Some numbers of the block, let the Session start or end.
Validator: Validators are responsible for submitting new blocks in the blockchain. These validators participate in the consensus protocol by broadcasting votes containing cryptographic signatures signed by each validator's private key. Validators participate in services and consensus by Staking POKT in the protocol.
max_app_relays = base_throughput / (# of Vals in Session * # of relay_chains staked for)