This article comes fromBlockSecThis article comes from
On August 12, according to user feedback in the DAO Maker Telegram group, the project was suspected of being hacked, and USDC worth $7 million was withdrawn to an unknown address by hackers. After analysis, the BlockSec team found that the incident was caused by the leakage of the private key or by insiders.
secondary title
attack process
According to our transaction analysis system (https://tx.blocksecteam.com), we found that the attack process is very simple.
0x26aa86261c834e837f6be93b2d589724ed5ae644bc8f4b8af2207e6bd70828f9
The hash of the attack transaction is:
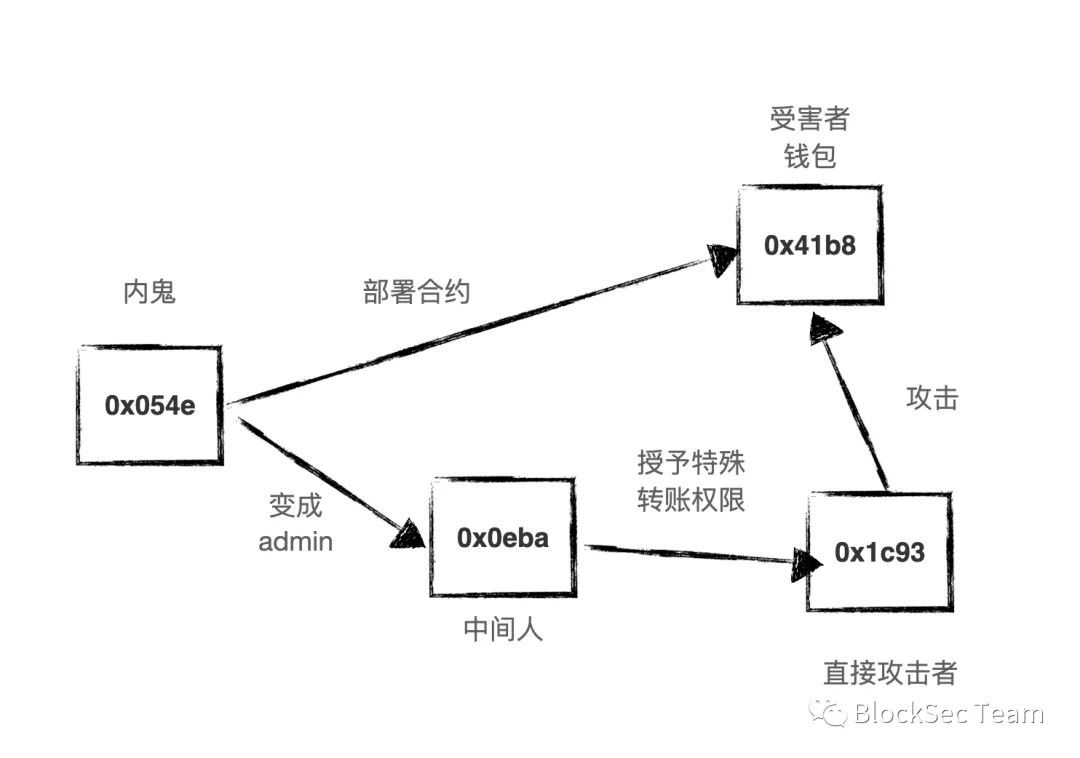
Addresses involved:
0x41b856701bb8c24cece2af10651bfafebb57cf49: victim wallet;
0x1c93290202424902a5e708b95f4ba23a3f2f3cee: XXX, attacker contract;
0x0eba461d9829c4e464a68d4857350476cfb6f559: man in the middle;
0x054e71d5f096a0761dba7dbe5cec5e2bf898971c: Victim contract creator (also attacker).
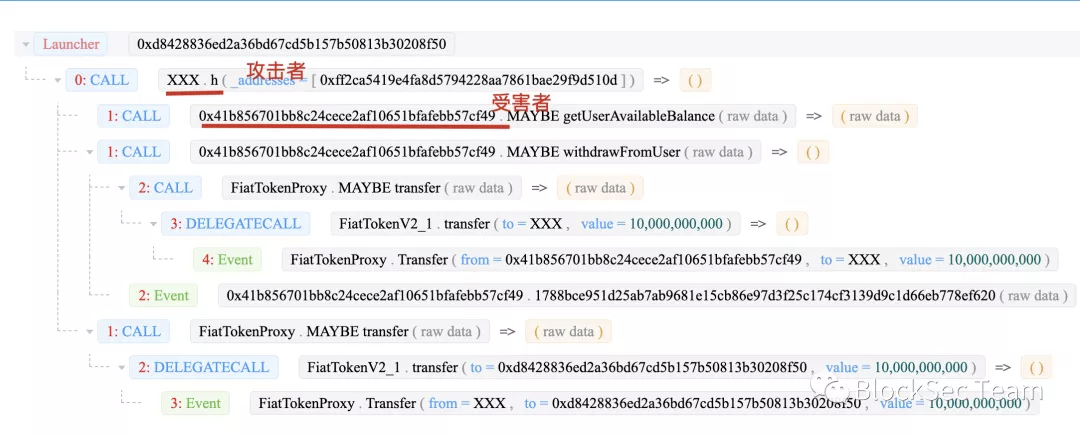
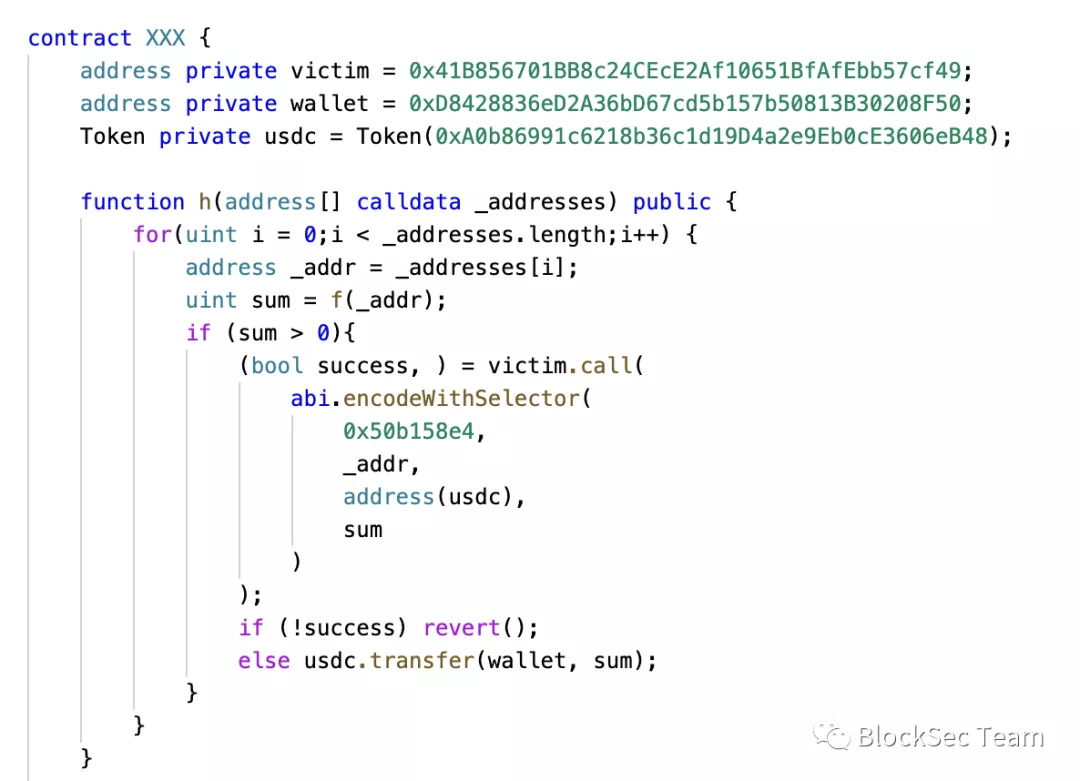
The attacker XXX (0x1c93290202424902a5e708b95f4ba23a3f2f3cee) calls the function of the victim wallet contract (0x41b856701bb8c24cece2af10651bfafebb57cf49) to query the user balance, and then calls withdrawFromUser to transfer the money to his own account. The attack is complete. Since the transfer operation is a privileged operation, it is usually necessary to verify the identity of the caller. Through analysis, we found that the attacker does have the appropriate authority to transfer the balance in the victim's wallet.
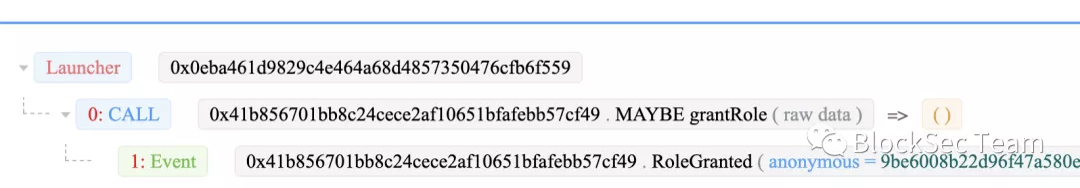
The question here becomes why would an attacker have the appropriate permissions? Through further analysis we found another transaction. This transaction gives the attacker the authority to transfer money. The transaction trace is as follows: 0x2fba930502d27f9c9a2f2b9337a0149534dda7527029645752b2a6507ca6b0d6.
0x0eba461d9829c4e464a68d4857350476cfb6f559 calls the grantRole function of the victim contract to grant the attacker 0x1c93 the authority to transfer funds. But if you can call grantRole to grant permissions to other accounts, then 0x0eba4 must have admin permissions. So who granted his admin privileges?
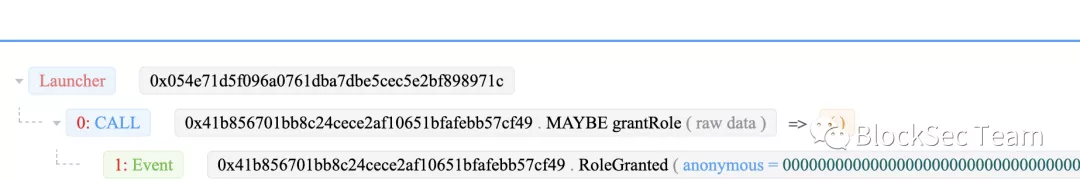
Continuing to track, we found that its admin permission was completed by another transaction: 0x41b856701bb8c24cece2af10651bfafebb57cf49.
Account 0x054e71d5f096a0761dba7dbe5cec5e2bf898971c sets account 0x0eba461d9829c4e464a68d4857350476cfb6f559 as the admin of the victim contract.
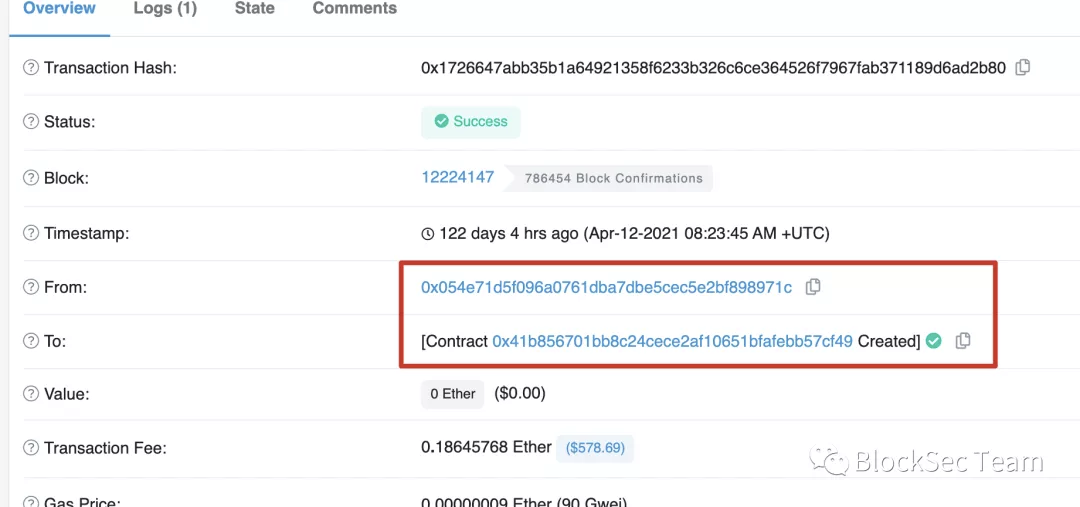
However, we found that the victim contract was created by 0x054e71d5f096a0761dba7dbe5cec5e2bf898971c.
secondary title
other
other
secondary title
at last
at last[Virtual Money Printing Machine] Popsicle Finance Double Spending Attack Analysisandand[Achilles' heel] In-depth analysis of key steps of Poly Network attack