introduce
introduce
Recently, there has been a lot of debate about the level of security that Layer 2 on Ethereum provides for applications and users. This brings up some issues with sidechains and rollups, and how different scaling solutions interact with the Ethereum mainchain. Next, let us understand what is Layer2 and is it safe?
first level title
Why is Layer2 needed?
This problem has been in the blockchain field since the beginning, and it is called the "Blockchain or Scalability Trilemma" (Blockchain or Scalability Trilemma), which states that the blockchain can only have the following three characteristics: Two, because security, scalability, and decentralization are mutually exclusive.
So Ethereum needs scalability solutions to help large, decentralized layer 1 networks like ETH1.0 scale without fundamentally compromising decentralization or security.
first level title
How does the scaling solution work?
The solution is actually quite elegant. By enabling off-main-chain transactions, Layer 2 enables developers to make trade-offs between speed/cost and security.
Use the following analogy with money storage:
Today, Ethereum transfers are inefficient, and Layer 2 optimizes the system by allowing various applications to choose their own combination of speed and security. In a realistic analogy, airlines allow passengers to choose between cost and comfort (economy, business, first class), thereby always operating the profit-maximizing solution.
In short, Layer 2 does not force developers to make certain trade-offs, but allows them to choose, thus optimizing the entire system.
first level title
Each extension solution does not, by itself, provide users with this option. Rather, it offers various combinations of speed, cost, and safety (similar to a flight offering economy, business, and first class). Developers can then choose their preferred solution based on the purpose of their application. There are currently four most widely used solutions: 1) sidechains, 2) plasma, 3) optimistic rollups, 4) zk rollups.
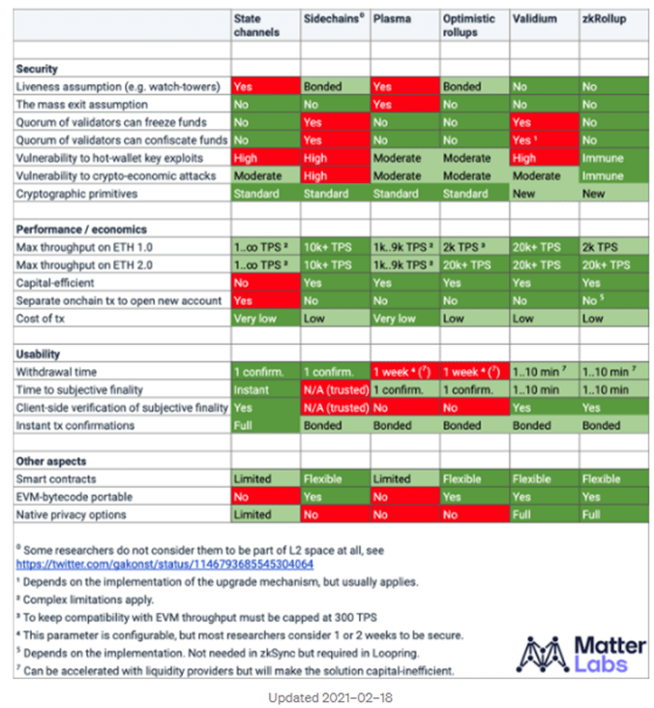
This table from Matter Labs gives us a good look at how these solutions stack up and the options developers have when building their projects.
first level title
Unraveling the Secrets of the Security Debate