
In the Internet computer, the computer is driven by a set of protocols (ICP), which allow the network to expand to millions of nodes, and can provide Canister (container) with scalable and unlimited computing power. Chain lock technology is the core of the Internet computer protocol.
So what are the advantages of chain lock technology? How does the chain lock protocol work? What are the innovations of chain lock technology? Regarding the technical details of the chain lock protocol, Jan Camenisch, vice president of cryptography research at DFINITY, unveiled the mystery for us in his speech "New Chain Lock Technology for Internet Computers". Welcome to continue reading the full text of the speech organized by Odaily, enjoy~
Hello everyone, I'm Jan Camenisch from DFINITY, and this talk is about chain key technology. In the Internet computer, the computer is driven by a set of protocols (ICP), which allow the network to expand to millions of nodes, and can provide Canister (container) with scalable and unlimited computing power.
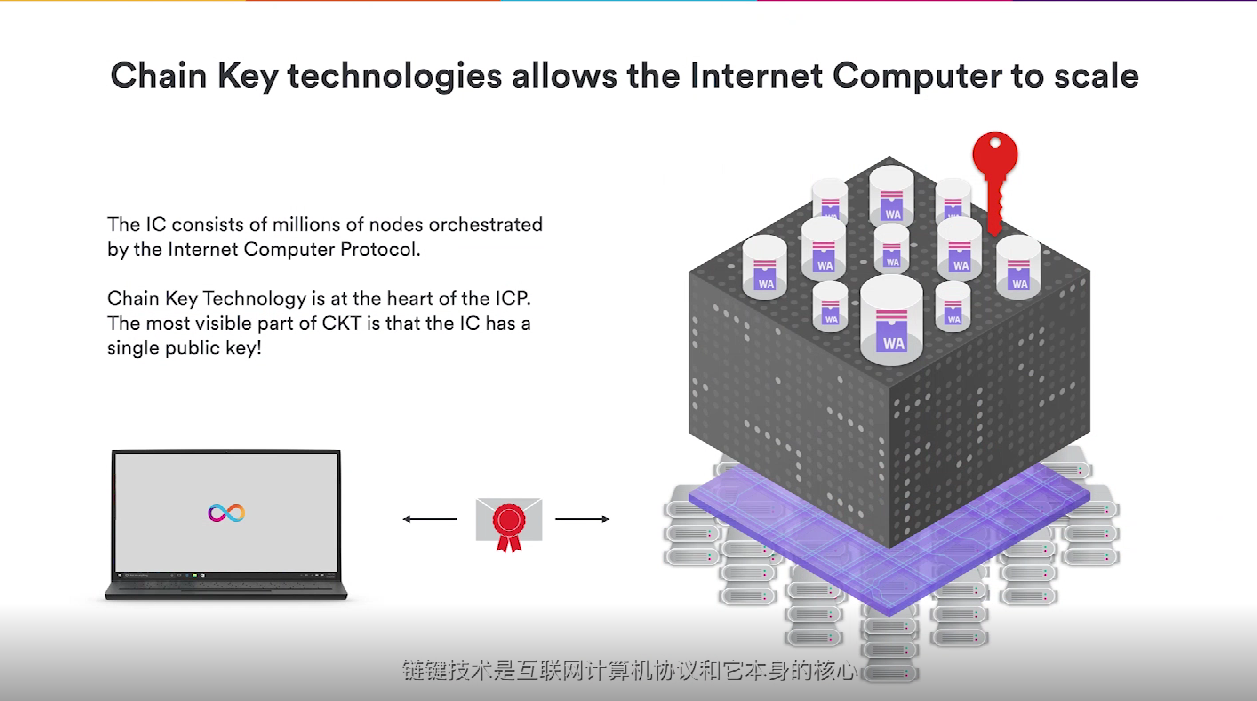
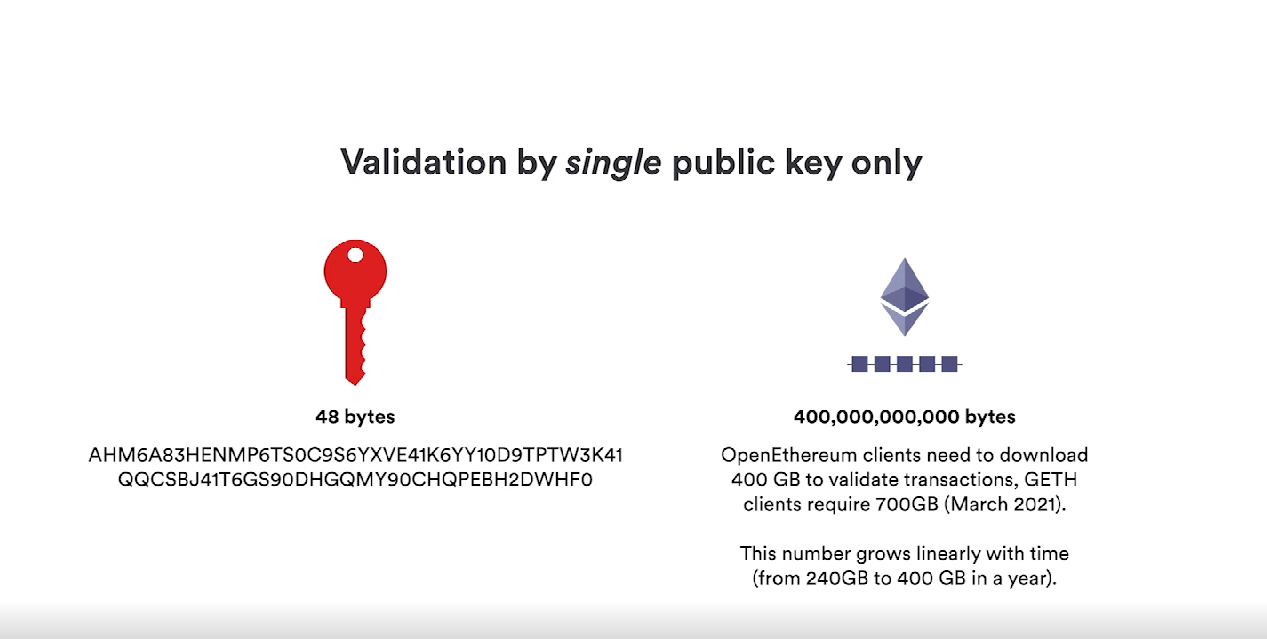
Chain lock technology is the core of the Internet computer protocol. In fact, this set of protocols is a special edge cryptosystem developed by us. The most obvious part of the chain lock technology is that Internet computers have a single public key with which information sent from interested computers about that single public key can be verified, which is a huge advantage for Internet computers. Therefore, if you want to enter an Internet computer, you only need a 48-byte public key to verify all messages. In contrast, the Ethereum client needs to download at least 400GB of data to achieve the same effect.
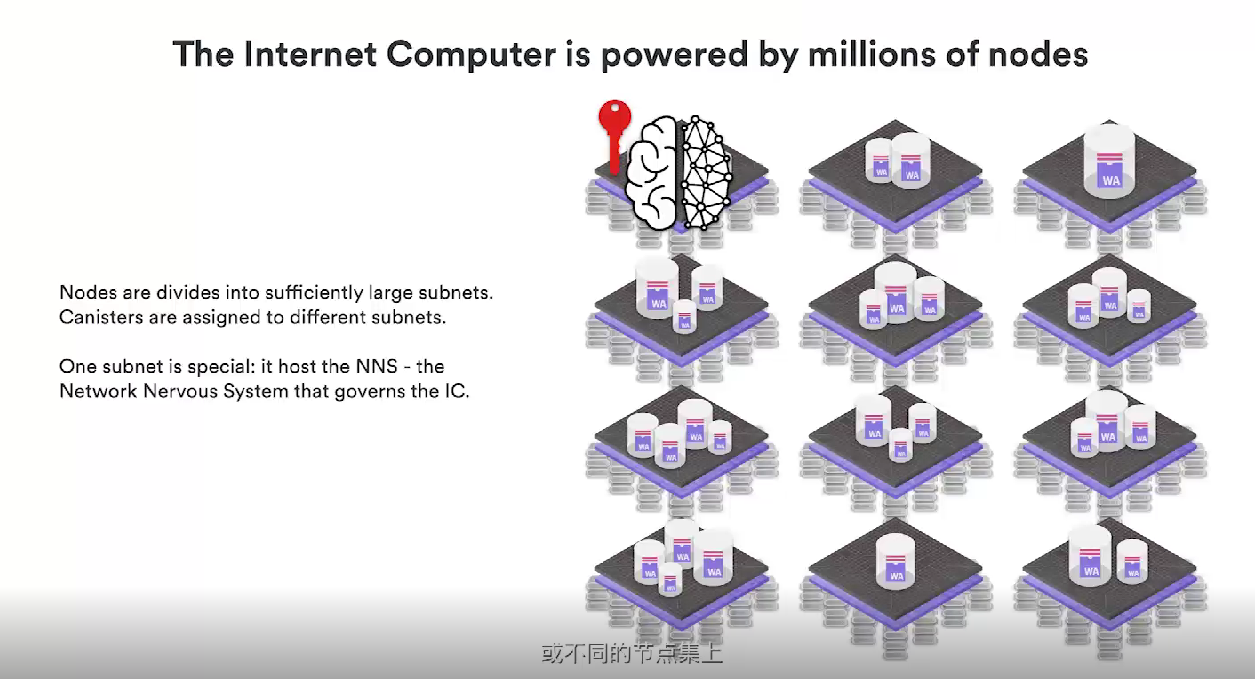
Now let's further explain the chain lock technology. In order to expand the Internet computer, not all nodes actually run in the same Canister (container), but we must distribute the Canister on different nodes, or in different subnets (composed of multiple nodes), we call this series of subnetworks Network Neurons (NNS). One of these subnets is special because it controls and dominates the other subnets.
And what I mean by single public key, is actually the public key that manages all other subnets, and is used to generate all other subnets that provide keys. We generate public keys, generate container certificates, and other major parts of this subnet.
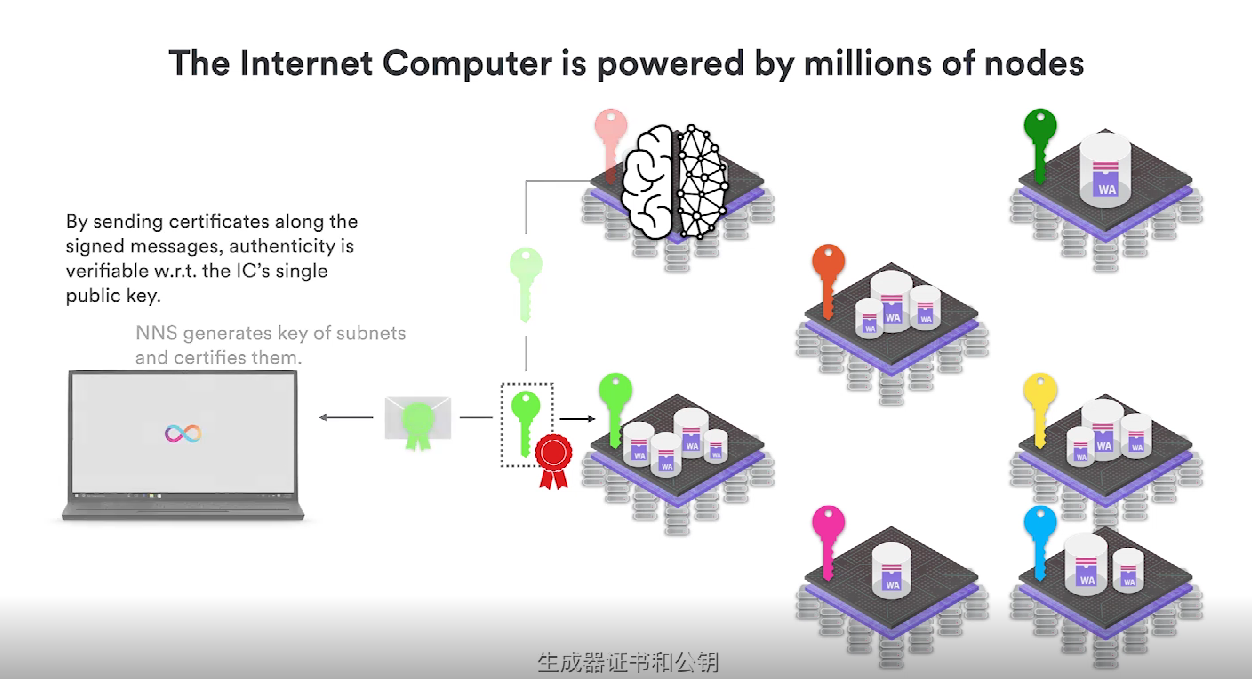 Like the chain lock technology, NNS can start from scratch. Now when users interact with NNS, NNS uses their Canister (container) to perform calculations and receive results from the calculations. They can sign on the subnet of these results to verify this. Regarding the subnet public key, the subnet public key can be verified using the certificate obtained by the subnet from NNS, which is like two parts of the chain lock technology. The first part is what we just said, higher-level subnets can generate private keys for other subnets; the second part is how the subnets that receive private keys from NNS manage these private keys.
Like the chain lock technology, NNS can start from scratch. Now when users interact with NNS, NNS uses their Canister (container) to perform calculations and receive results from the calculations. They can sign on the subnet of these results to verify this. Regarding the subnet public key, the subnet public key can be verified using the certificate obtained by the subnet from NNS, which is like two parts of the chain lock technology. The first part is what we just said, higher-level subnets can generate private keys for other subnets; the second part is how the subnets that receive private keys from NNS manage these private keys.
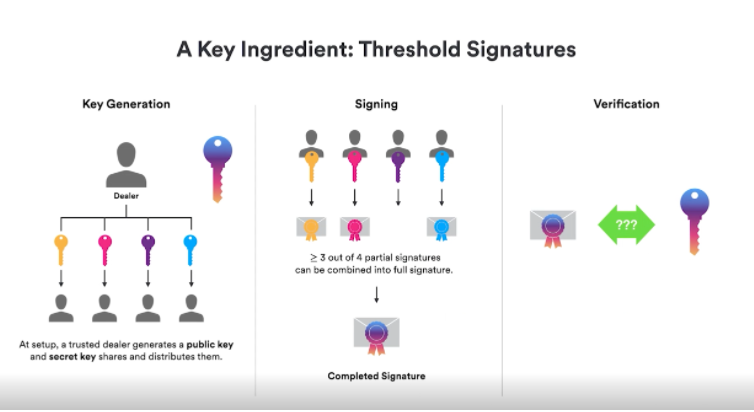
Nodes can crash and need to be replaced; nodes can also be compromised and need to be culled. In both cases, the private key received by the subnet needs to be re-shared among the new set of nodes, so in order to maintain the key information received by the subnet, we use Threshold Signature (threshold signature), this special signature It's actually an algorithm that sounds like a set of algorithms that have to work together. First of all, we have an algorithm for generating private keys, which is like having a trusted dealer continuously generate public keys and private keys, and then distribute them to different participants. When most participants agree to sign, these partial signatures can be Combined into a full signature relative to the original public key, and verified.
How to implement the above process in the chain lock technology? One way: you need a non-interactive key generation algorithm The standard key generation algorithm for threshold signature schemes requires a trusted old reseller with computers on the Internet, which is unlikely to be possible because we don't want to trust anyone party.
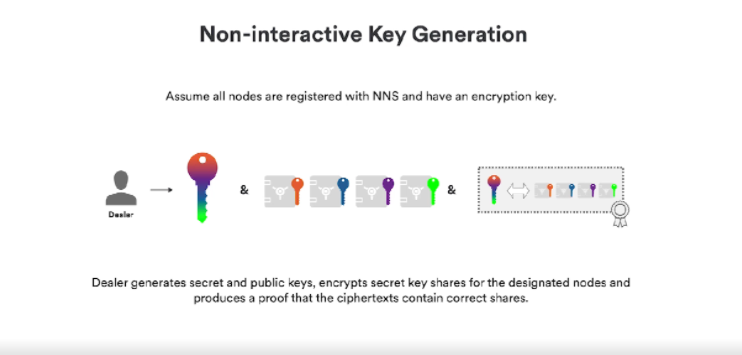
To solve this problem, we propose some new efficient cryptography. It allows two things: First, it allows the dealer to directly generate these keys without interaction, the dealer generates the key and the public key, but the difference is that the keys are written for each party, in our example here Clues are data, and non-interactive encrypted graphical proofs are also generated. In fact, matching the generated public key as well, we actually start a non-interactive proof where either party can verify that the share is correct.
The second part is the mathematical nature of the sharing scheme, that is, two different shares can be combined into one share, and if you have two or more dealers, the receiving transaction pair can do a mathematical homomorphic operation, which we call For public key merging, where different public keys become a single public key, they can also do the same on keys, resulting in a new kind of sharing, a combined sharing.
As we already know, all sharing is correct because of these proofs of neural knowledge, this homomorphic combination will actually ensure that as long as one dealer is doing it right, then I have not revealed this key, the overall combination The keys of will also be secure, since they contain sufficient randomness. The nice property of this homomorphic operation is that it will ensure that as long as the single share is done correctly, i.e. the key is randomly generated and not leaked anywhere, then the combined key and public key are generated. So this allows the internet to start new subnets, to generate keys for the subnets. To be more precise, each node of NNS will do such sharing and pass the information to new nodes.
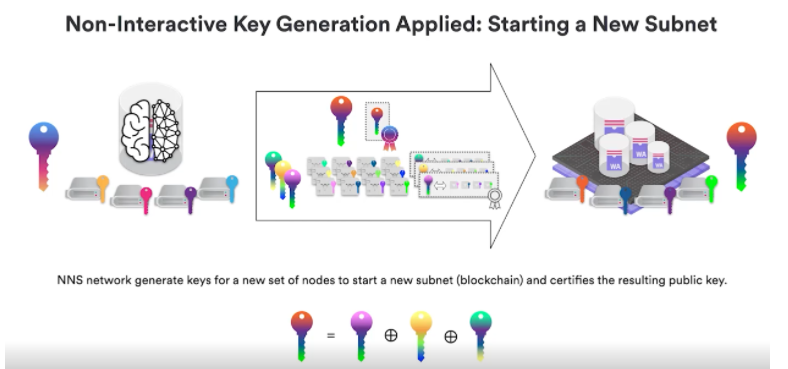
Now we talk about the second part. Nodes must maintain the key information they originally received from NNS. Now because they cannot be contacted specifically, they will also be transmitted in an encrypted manner. We need a second encrypted graph tool, but not to generate For new keys, they need to prove that their key encryption information is consistent with the shared key, and then provide it to all other nodes, and once a certain threshold is reached, all nodes can re-share a new key.
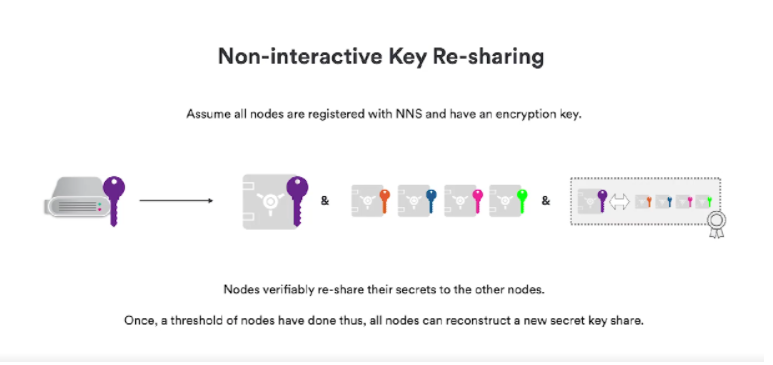
Let's take a look at how to use a non-interactive method to recover the lost key in the subnet. For example, we have four nodes in our example, one of them crashed, lost all state, lost all key information, because we are using three out of four key sharing schemes, the remaining nodes can still operate , at this time NNS will assign new nodes to the subnet, and store them into four nodes again. But if it's two nodes that are lost, it's a disaster.
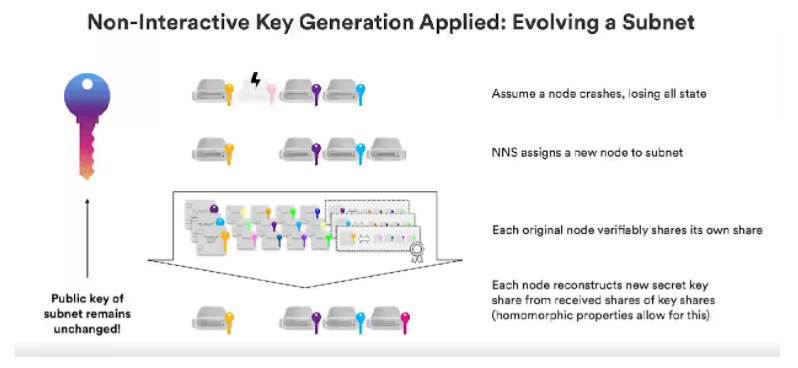
The other party also noticed that it was like a key that he shared, for this and the original record, we guaranteed the secrecy of the new set of nodes, the four nodes adopted the free sharing technology with non-attractive characteristics. After this, each of the four new nodes will have a key share corresponding to the public key, which is how we can replace those nodes from the subnet that have crashed and keep it going.
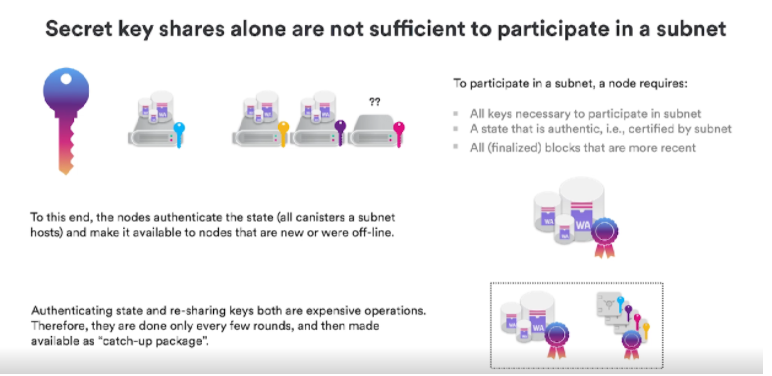
For those nodes whose key information is not yet qualified to join, if they want to join a subnet, they need to be specific: first, all private keys must agree to join the subnet; the subnet verifies and authorizes its status; contains all recent blocks state. Since individual nodes are not trustworthy, the nodes have to verify the latest state together, then we set a joint state i.e. the new node, we will be sure that the state received is actually the true state, the correct state to start with.
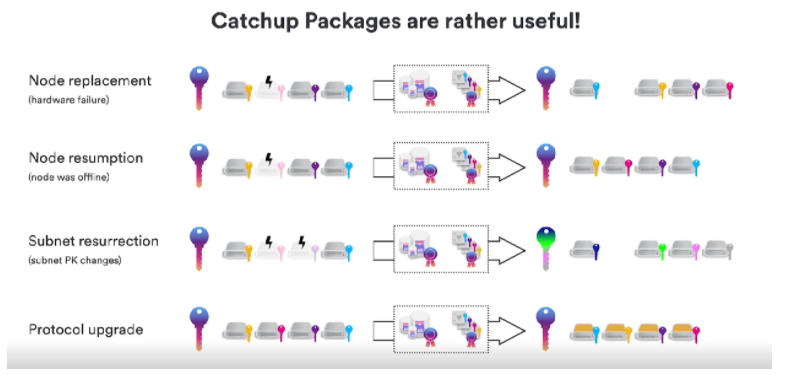
These operations are very expensive, we can't do them every round, we need to do them within a specified time interval, during this interval we generate the authentication status, put these two together, we call it a Catchup package. It allows nodes to keep up with other nodes, and operate with them, this Catchup package is actually very powerful, because not only do they not allow us to replace, but they also allow to recover nodes, so if the node did not crash but may be offline for other reasons, If the time is too long, to catch up with the previous node, you can download the latest catchup package, then decompress and resume operation.
In catastrophic cases, more than a third of the nodes would crash or lose their state, and even then we were able to recover the subnet. As long as we still have a Catchup packet, NNS can take that Catchup packet, just add a new shared key, because the previous one is no longer valid, and start from the original Catch-up packet, create a new subnet. Also, and probably most importantly, Catch-up packets also allow us to upgrade the protocol, since Catch-up packets define the explicit state of a subnet. We can say that after a certain Catch-up package, all new nodes will download the new protocol version, and run the new protocol version from this Catch-up package, non-interactive dkg and key re-sharing, or just change the technology. elements.
The core of the chain lock technology is the consensus protocol, which coordinates the difference consensus of all protocols. Its main task is to collect and evaluate messages from users and get them executed, but it also has to coordinate non-interactive organization and re-sharing between all the different nodes to ensure that computations are done correctly. Even if some problem occurs, such as a hard disk failure or some other glitch, the problem with some part of this container will not affect the command execution; but still involves the recovery and synchronization of its coordinated state, and thus coordinates all upgrades from the given lost The state starts. Another interesting feature is that the consensus protocol actually also provides recovery randomness applications, we will have a technical discussion on all these details shortly, and we will publish the specifications on this as well.
In short, chain lock technology enables Internet computers to have a single public key, which can be used to verify computers connected to the network; chain lock technology also allows NNS to add new subnets and expand the network forever; if too many nodes fail , the chain lock technology can reactivate a subnet; the chain lock technology can also replace the collapsed node; finally, the chain lock technology can also update the IC protocol, fix bugs, and add new functions.