On May 8, the decentralized computing platform DFINITY, together with 36Kr and Odaily, jointly held the "DFINITY Internet Computer Mainnet Launch Conference". This conference focuses on the technology and development of Internet computers, and is committed to discussing technology and applications, opportunities and challenges, business and ecology with decentralized builders.(Click to watch the exciting content)
At the press conference, DFINITY founder and chief scientist Dominic Williams and technical engineer Joachim Breitner jointly delivered a keynote speech on "Internet Identity: The End of the Username and Password Era".

The following is the full text of the speech, organized by Odaily:
The following is the full text of the speech, organized by Odaily:
Dominic Williams: Hi everyone, I'm here today with Joachim Breitner to talk about what internet identity is and what it's used for. We all know that Internet identities are used for Internet services such as registration, login, and hosting. These Internet services are built on multiple contracts, which require end-to-end cryptographic security. Indeed, internet identities are often tied to internet-stored histories. At DFINITY we've been working on it for a while and I'm so excited to have a product like this that I had the opportunity to show you today.
I started using a brand new cryptographic primitive a few weeks ago. Internet Computer supports this primitive, which is called an authentication variable, which in turn relies on keychain technology. First, imagine yourself in a new world where you can securely authenticate yourself to an online service without touching usernames and passwords, without touching cryptographic key material, just using your device. In this world, you can log into an Internet service without being tracked within it.
Then imagine an alternate new world where everything happens much more easily, and you can easily use any kind of authentication system today. So, the advantage of the Internet is like a phone number. It's just that these phone numbers are numbers you remember, and it doesn't matter if someone finds a number associated with you. Because these numbers are not sensitive information to me, nor does it involve security, but the online service sees something completely different. You can use these numbers on different devices. Then log in on any of those devices, and they can log in without even going through you.
Next to my colleague Joachim Breitner, let's see how DFINITY works.
Joachim Breitner: First, log in with multiple devices. Here's one of those devices: a fairly standard Android phone that's three years old. I'll use it to log into my internet identity. So this is the login home page, and initially we offered an option. I'm going to register as a new user and name him Pixel. I hit register, and now it interacts with the device, presenting me with logs and options to work with. I can use the screen lock, which means I can't just use my fingerprint on the back to check the internet.
Dominic Williams: The biometric device's fingerprint sensor that unlocks the phone has a secure TPM chip built into it that can be used to generate a key pair.
Joachim Breitner: The next thing I have to do is, confirm that I want to register. I have to click a second time. Yes, it takes two touches to complete the registration. I know this might take a while because it's doing some proof of work to get some information. Anyway, it's true that registration is a little bit slower at the moment, but this will allow us to prevent someone from using registration to manipulate us.
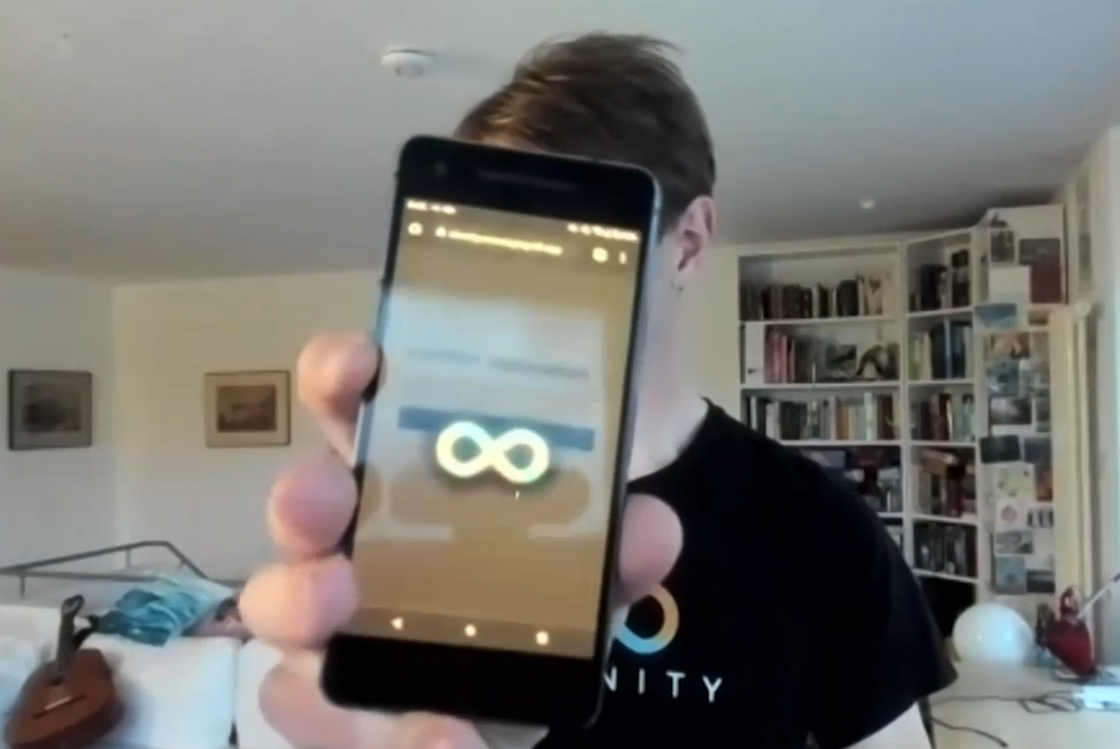
After the registration is completed, the system will automatically prompt me that I now have a user number on my Internet identity, which is also a sign of my Internet identity. I should choose remember password mode so they can use my device to log in again anytime. But I don't have to keep it secret, it's not a password. Once the number is noted down, I can proceed.
On the main view page, I can see that I only have one device so far, it's a bit boring, let's add another device here. In addition, I also have a security token in the form of a USB shield. Token is everywhere, I try to log in there. Below I will share my screen, you can see the Firefox browser.
After registering a new device, I can add another new device. To do this, I need to click the button that must enter the user number, and then the dialog box for binding the device will pop up again. In order to allow this device to be used, I need to click on the USB shield. After clicking on the USB shield it was trying to link to my account and then a link popped up so I could use it on more than one terminal.
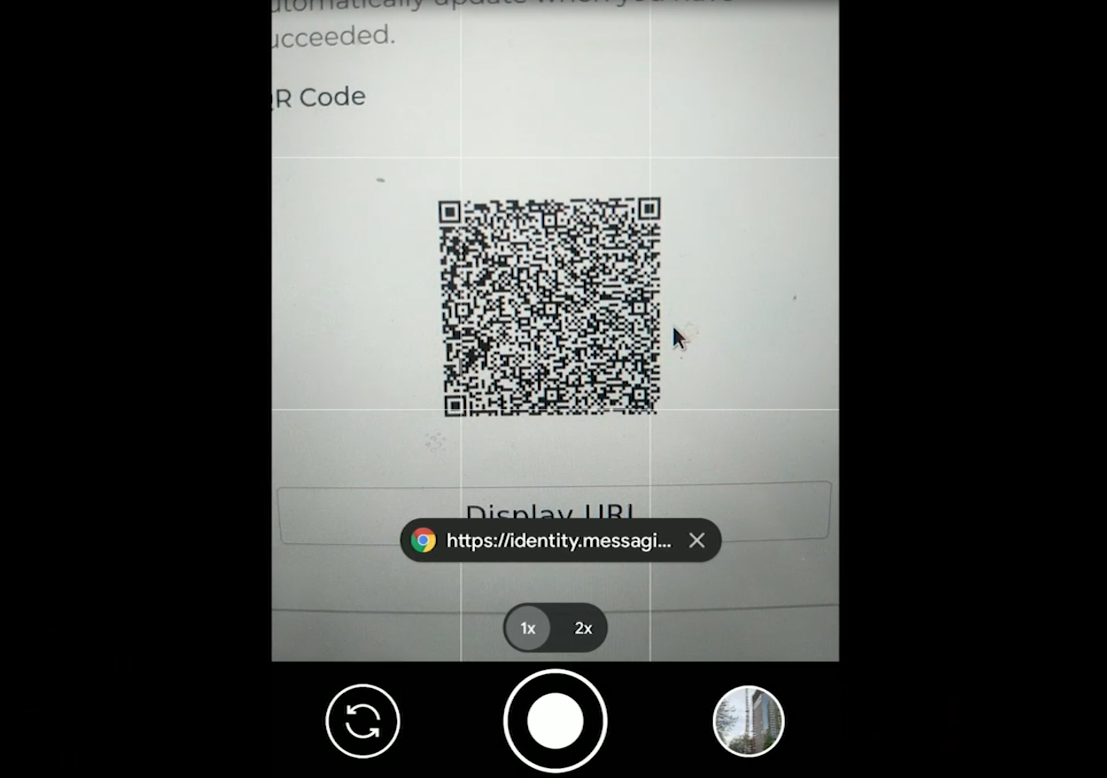
I now stop sharing my screen and use my camera to show what I'm doing. I'm turning on my phone's camera and I've got a QR code and I'm now on the screen to log in with my identity. I can log in and need to confirm with my fingerprint. It's worth noting that I wasn't asked by the system if I really wanted to link a new device.
We'll then see in the background if the browser loaded the information correctly. We look at the laptop screen after login. It knows my number, I can say look and look, I don't need a password or anything, I just need to click on my USB shield. I successfully logged in on both devices. Now, this is me adding my internet identity to both devices. I can add more devices as well as manage and delete. Previously, none of these devices could simultaneously log into relevant Internet services with an Internet identity.
Dominic Williams: Wow, that's pretty cool. You can imagine a scenario where someone might use an ID on their phone to log into a service, or a fingerprint sensor on a laptop to log into a service. Of course I will tell you that they can log into various services from any device. Because they've already done the authentication, it gives you a very flexible experience, and the authenticators associated with who you are.
You can add new authenticators, or delete authenticators. Thereafter, you register and log in to any Internet service. Use whatever equipment you want as long as you like. So your device is now actually acting as an authenticator. You never need to touch the password or key material of any kind. You only need to interact with your own device, which is absolutely revolutionary. Not only in terms of improving the usability of online authentication, but also in terms of security.
So we think people are going to see a lot more of that, and it's an amazing demonstration. Two advanced applied cryptography forces make this possible behind the scenes. We achieve this with the help of authentication variables, and also complete the technical optimization. So remember, you are seeing this innovation for the first time today, a brand new crypto project launched by the DIFINITY Foundation. I'm sure you'll have lots of questions and I really look forward to speaking with you soon. Thank you so much!