Editor's Note: This article comes fromBabbitt Information (ID: bitcoin8btc), Compilation: Overnight Porridge, released with authorization.
Editor's Note: This article comes from
Babbitt Information (ID: bitcoin8btc)wrote。
, Compilation: Overnight Porridge, released with authorization.
Beijing time on September 14th, the DeFi lending protocol bZx was attacked again, and this attack caused a total loss of about 8 million US dollars. According to bZx co-founder Kyle Kistner initially said: "This seems to be an oracle machine Manipulative attacks."
Immediately after the attack was discovered, the bZx team suspended the agreement using the admin key. It is reported that the attack transaction used flash loans and Synthetix, "but it will not affect the Synthetix system, although it does involve sUSD," bZx on twitter
wrote
The bZx official mentioned in the latest security report:
“Due to a token duplication event, the protocol insurance fund has temporarily accrued a debt. In addition to the protocol cash flow, the insurance fund will be backed by the token pool.”
Here is the timeline of the security incident:
The bZx team noticed an abnormal change in the protocol lock value (TVL);
After the fix is determined, the minting and burning of iToken is suspended (borrowing and trading are not affected);
A new version of the affected iToken contract is deployed and the balance is corrected;
The team sends the patch code to Peckshield and Certik for review;
iToken casting and burning recovery;
secondary title
Attack Technical Details
Every ERC20 token has a transferFrom() function that is responsible for transferring tokens. You can call this function to create an iToken and pass it to yourself, allowing you to artificially increase your balance.
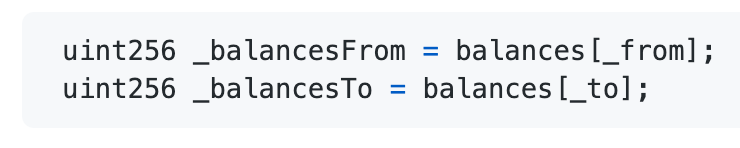
The transfer function was called with the same _from and _to addresses;
So
Call Immediately _internalTransferFrom with the same parameters;
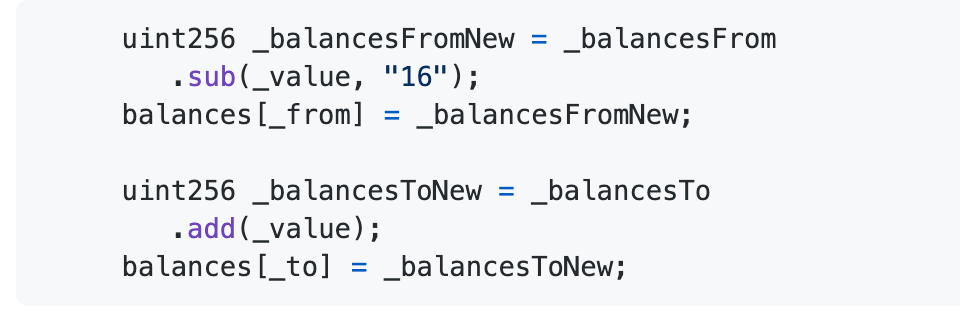
The following line of code is at fault:
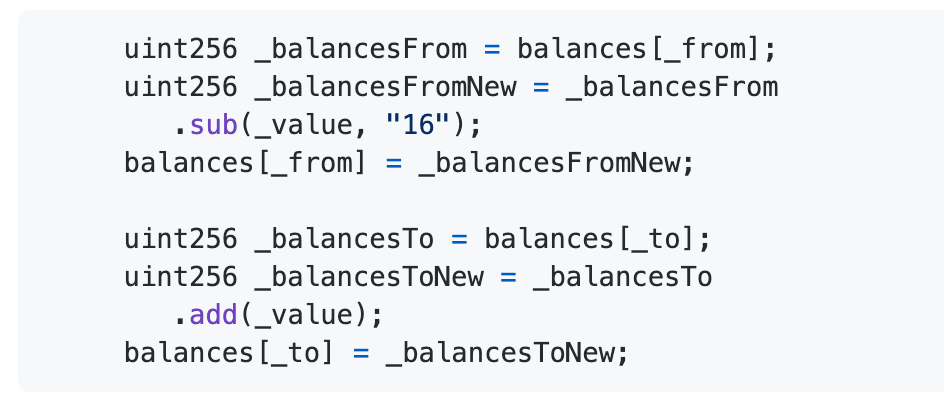
So
The above problem results in decreasing the balance of _balancesFrom, and increasing the balance of _balancesTo, and finally the most important part is saving _balancesFromNew and _balancesToNew. The attacker can then effectively artificially increase his own balance.
Then, here is the patch code:
219,199.66 LINK
4,502.70 ETH
1,756,351.27 USDT
1,412,048.48 USDC
667,988.62 DAI
secondary title
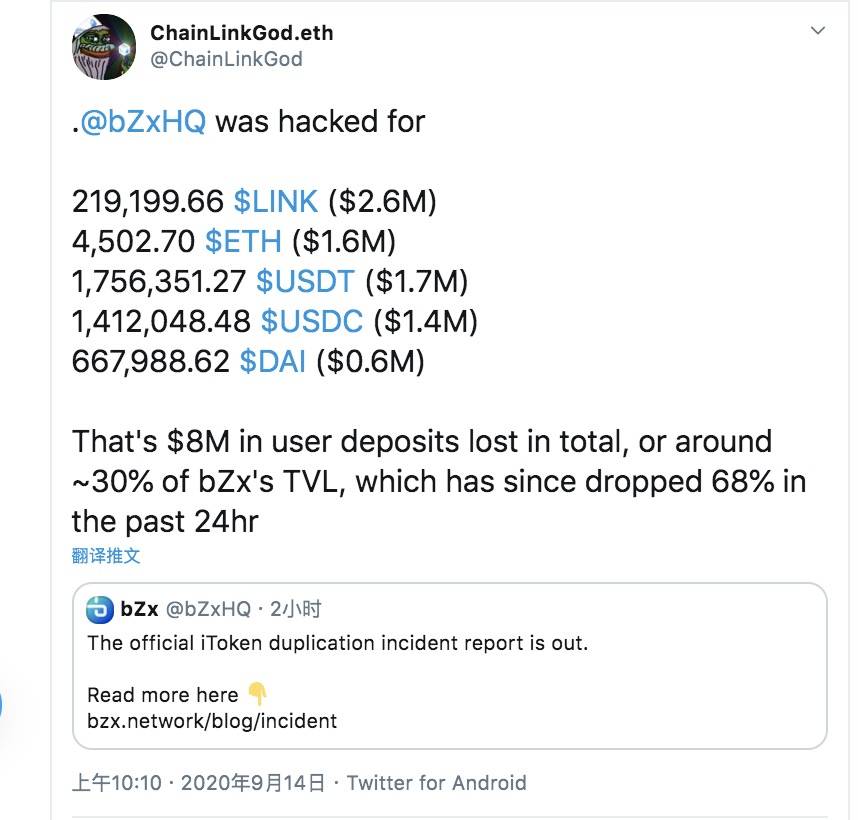
Security incident creates nearly $8 million in debt
Although the bZx code vulnerability was quickly resolved, this security incident did cause a lot of losses to the protocol. According to official information, this incident led to the following debts:
At current market prices, these lost tokens are worth $8 million.
secondary title
Auditing is not a panacea