
"DeFi platforms don't do evil, but they can't handle too many hackers."
After Uniswap was hacked and lost 1,278 ETH (worth about 220,000 U.S. dollars) on April 18, at 8:45 a.m. on April 19, the domestic DeFi lending protocol Lendf.Me was exposed to hackers. According to SlowMist Technology Anti-money Laundering (AML) system statistics show that the cumulative loss of Lendf.Me this time is about 24.7 million US dollars. The specific stolen currency and amount are:

After that, the attackers continued to exchange the stolen coins into ETH and other tokens through DEX platforms such as 1inch.exchange, ParaSwap, and Tokenlon.
image description
Image source: Lendf.Me official website
image description
Image source: Defipulse
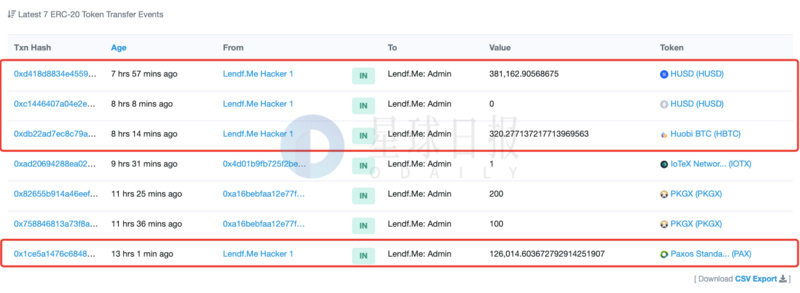
According to the monitoring of SlowMist’s anti-money laundering (AML) system, the Lendf.Me attackers are continuously transferring the PAX profited from the attack to ETH, with a total of nearly 587,000 PAX. The exchange platforms used include 1inch.exchange, ParaSwap, etc. . The attacker address is 0xa9bf70a420d364e923c74448d9d817d3f2a77822.
According to the analysis of the SlowMist security team, the hacker’s method of attacking Lendf.Me is similar to yesterday’s attack on Uniswap(Odaily Note: Hackers take advantage of the compatibility issues between Uniswap and ERC777, when conducting ETH-imBTC transactions,reentrancy attackreentrancy attack), all due to the lack of reentrancy attack protection in the DeFi contract, the attacker used multiple iterations in ERC777 to call the tokensToSend method function to achieve reentrancy attacks, and it is very likely that the same group of people did it.
The SlowMist security team analyzed the whole process of the Lendf.Me attack in detail:
The attacker first deposited 0.00021593 imBTCs, but successfully withdrew 0.00043188 imBTCs from Lendf.Me, and the withdrawn amount was almost double the amount deposited.
So how did the attacker get doubled balance from a short transaction?
By analyzing the transaction process, the SlowMist security team found that the attacker made two calls to the supply() function on Lendf.Me, but these two calls are independent, not called again in the previous supply() function supply() function.
image description
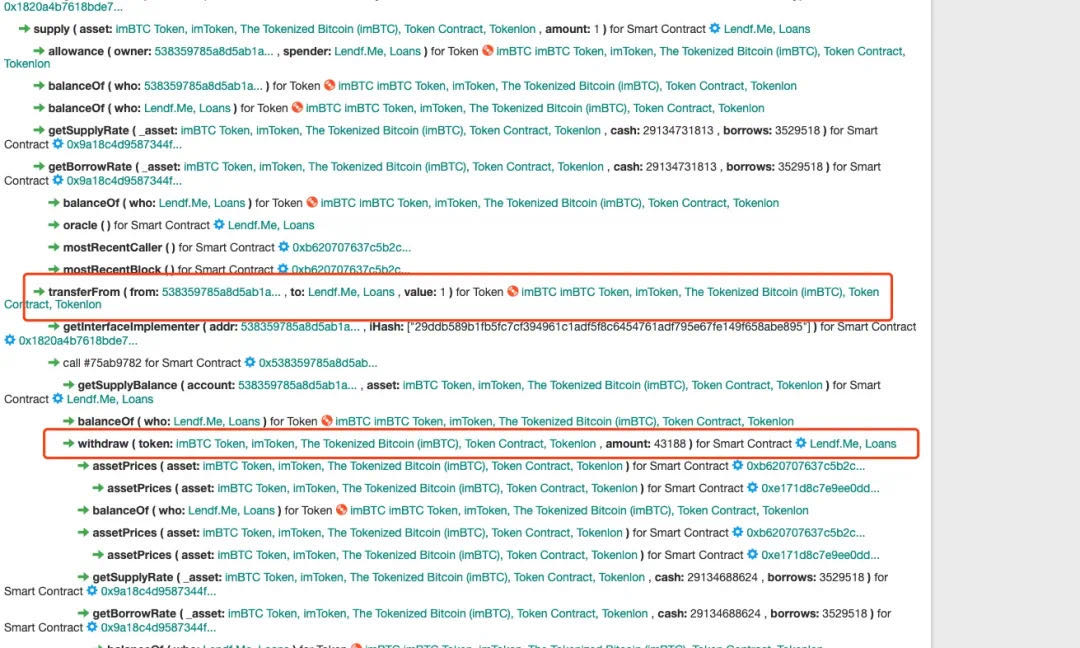
text
text
The attack on the Lendf.Me protocol also made everyone question the code auditor of dForce. Public information shows that the Lendf.me protocol forked the Compound v1 code, and Compound v1 was audited by the company trail of bits.
Image source: twitter
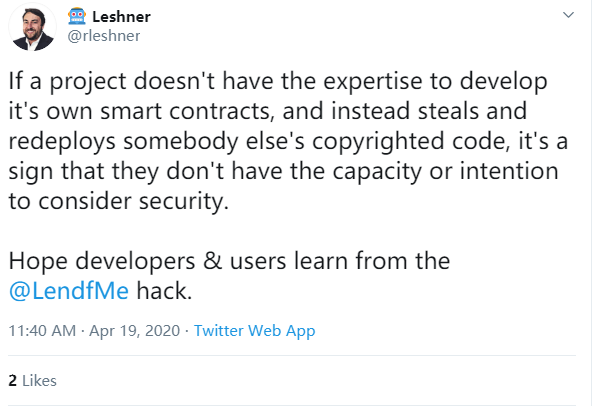
Image source: twitter
We hereby suggest that DeFi developers should develop independently when designing products, establish their own risk control mechanism, and improve risk control capabilities.
secondary title
What thoughts have been brought to us by the two consecutive DeFi attacks?
From the bZx attack incident at the beginning of this year to the Uniswap and dForce attack incidents, it shows that hackers have grasped the key points of DeFi’s systemic risk control loopholes, and made full use of the composability of DeFi to attack DeFi one after another.
Bowen Wang, head of DDEX operations, once reflected on the impact of the bZx incident at the "Vigor" cloud summit held by Odaily, "The concept of Lego is because all the building blocks are produced by the Lego family, and the quality is very good. But the quality of many parts in DeFi varies. Qi. What happened on bZx shows that when you don’t know the foundation very well, the higher you build, the more dangerous it is.”
Using the barrel theory to explain the biggest problem of DeFi Lego, the security of the DeFi system depends on the shortest piece of wood, so as long as there is a problem with one module of DeFi Lego, it may drag down the entire ecology. This requires DeFi developers to continuously improve and update at the code level. Instead of pursuing the high combination of DeFi products one by one, they should also pay attention to the compatibility of different DeFi products in terms of security.
In addition, the development of DeFi insurance can also alleviate the losses caused by hacker attacks to the DeFi platform to a certain extent. The DeFi insurance agreement Nexus Mutual has set a successful demonstration for the industry by compensating users who suffered losses in the bZx attack. However, DeFi insurance products are still in a very early stage of development. The product model and operation method are not yet mature, and there is also a lack of a unified risk pricing system and compensation protection mechanism. Most insurance platforms are more likely to have certain protection properties and hedge against currency price fluctuations. Risky derivatives, or only to B's platform services.
latest progress
latest progress
postpostIt said that hackers used the compatibility issues between ERC 777 and DeFi smart contracts to achieve re-entry attacks, and Lendf.Me lost about 25 million US dollars. Currently, the team is working on the following actions:
Top security companies have been contacted for a more comprehensive security assessment of Lendf.Me;
Working with partners to develop a solution to recapitalize the system, despite this attack, we will not stop;
We are working with major exchanges, OTC platforms, and relevant law enforcement to investigate the situation, stop the transfer of stolen funds, and track down the hackers.
In addition, the team will provide a more detailed update on the official blog on April 20 at 11:59 pm Beijing time.
Recommended reading:
Recommended reading:Reference article:
Reference article:"Slow Mist: DeFi Platform Lendf.Me Hacked Details Analysis and Defense Suggestions"