This article comes fromThe BlockEtc., original author: Celia Wan
Odaily Translator |
![]()
Odaily Translator |
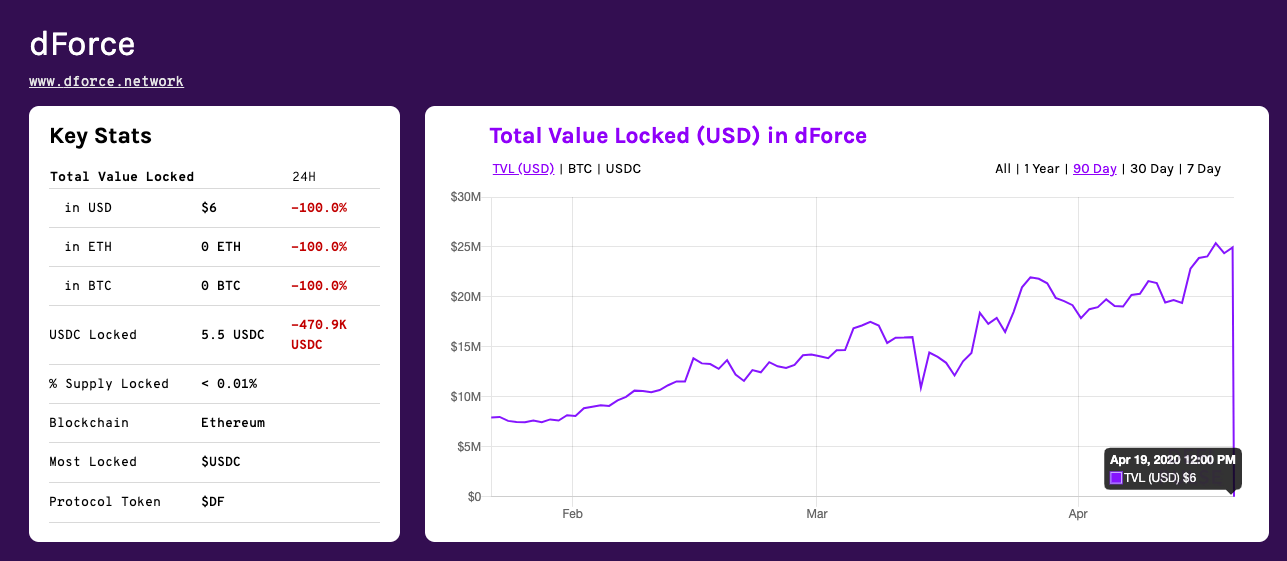
It shows that in the past 24 hours, the dollar value of dForce locked assets fell by 100% to 6 US dollars, while the total value of the previous locked positions exceeded 24.9 million US dollars.
In the dForce Telegram channel, dForce founder Yang Mindao said that the team is still investigating this issue and recommends that all users stop depositing assets to the lending agreement Lendf.Me. According to reports, the Lendf.Me team confirmed that it was attacked at block height 9899681 at 8:45 Beijing time.
While the details of the attack have not been revealed, it is worth noting that in January, Lendf.Me integrated with imBTC, an Ethereum token pegged to BTC. On April 18, imBTC's liquidity pool on the Uniswap decentralized exchange was attacked, resulting in a loss of tokens worth approximately $300,000.
On the afternoon of April 18, Tokenlon sent a message saying that the imBTC pool on Uniswap had been hacked and had been exhausted. According to PeckShield, the specific attack method of Uniswap in this incident is: Hackers take advantage of the compatibility issues between Uniswap and ERC777, and use multiple iterations in ERC777 to call tokensToSend to achieve re-entry attacks when conducting ETH-imBTC transactions. The loss of this attack was limited to the ETH-imBTC liquidity pool on Uniswap, and other DeFi protocols and BTC custody were not affected. PeckShield believes that since the bZx attack at the beginning of the year, this is another attack carried out by hackers using DeFi systemic risk control vulnerabilities.some userson twitterGuess Lendf.Me suffered a similar attack becauseTransaction RecordIt shows that the hacker repeatedly called the withdrawal function of Lendf.Me to withdraw imBTC by far exceeding the amount of tokens he had previously deposited in the lending agreement. It is reported that this attack method is not new. In 2016, the famous DAO hacker used a similar mechanism, leading to the theft of $60 million in ether.ConsenSys audit of Uniswap last year
This vulnerability is also discussed in depth.According to the analysis of the SlowMist security team, the attack on Lendf.Me is similar to the attack on Uniswap yesterday, and it is very likely that it was done by the same group.According to statistics from the Anti-Money Laundering (AML) system of SlowMist Technology,
In this regard, on April 19th, the Tokenlon team releasedannouncementannouncement
, Tokenlon discovered that Lendf.Me had a large number of abnormal lending behaviors this morning. To ensure the safety of user assets, Tokenlon decided to temporarily suspend the Lendf.Me USDT deposit and interest function. Other affected functions include imBTC transfer function and imBTC decentralized financial management function. BTC custody is not affected, and Tokenlon transactions in other currencies are also unaffected, and can be exchanged normally.According to the data, before the attack, Lendf.Me, which was launched in September last year, became one of the seven DeFi markets of DeFi Pulse because of the value of locked assets. However, according toPreviously reported by The Block
, the lending protocol Compound accused Lendf.Me of stealing its copyrighted code. After The Block contacted dForce, the Lendf.Me team added notes about Compound to their website and GitHub page. "Lendf.Me includes the following modules: money market contracts (based on Compound V1), interest rate models, Oracles, liquidators, liquidation monitoring, market dashboards and front-end UI & UE." Lendf.Me emphasizes that all codes of the project (unless otherwise stated) are open source and licensed under the MIT license.
At the time, Yang Mindao said Compound had never previously contacted dForce about potential copyright infringement. Compound CEO Robert Leshner also confirmed to The Block that Compound had not contacted dForce, claiming he had just been made aware of the situation. "In fact, we just got word about LendF.Me. It's new to us, and we're evaluating our legal options," Leshner noted. "All Compound code is available for review, inspection, and audit, but that doesn't Doesn't mean you're free to steal or redistribute. In fact, all of our code is copyrighted, eg 'rights reserved'."
But Yang Mindao believes that the concept of copyright is contrary to the open source concept represented by the cryptocurrency movement, and what really makes cryptocurrency shine is its open source advantages. “If Compound really wants to pivot their open finance business toward pursuing closed finance and old-school patent monopolies, I think they’re going to face an uphill battle and need to fight for their own survival.”
He said, “The issue of using Compound code was raised early in the Lendf.Me development process, but it was not considered a serious issue because many lending protocols already use a similar model. The assessment at the time was that, Almost all projects use a similar model or almost the same model. As far as the lending protocol is concerned, there is no monopoly on the market, and the money market module itself is not a complete product." However, experts say that the reality is more favorable for Compound, Because while the Compound website says its protocol is open source, that doesn't mean the company can't enforce ownership claims on the works it produces.